Download This PDF File
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Citizen's Charter
CITIZEN’S CHARTER APRIL 2019 VISION Tarlac State University is envisioned to be a premiere University in the Asia-Pacific. MISSION Tarlac State University commits to promote and sustain the offering of quality and relevant programs in higher and advanced education ensuring equitable access to education for people empowerment, professional development, and global competitiveness. Towards this end, TSU shall: 1. Provide high quality instruction through qualified, competent and adequately trained faculty members and support staff. 2. Be a premiere research institution by enhancing research undertakings in the fields of technology and sciences and strengthening collaboration with local and international institutions. 3. Be a champion in community development by strengthening partnership with public and private organizations and individuals. i CORE VALUES E - xcellence and Enhanced Competence Q - uality U - nity I - ntegrity and Involvement T - rust in God, Transparency and True Commitment Y - earning for Global Competitiveness SERVICE PLEDGE Pursuant to its mandated mission, the Tarlac State University as a premier institution in the Province of Tarlac, in particular, and in the region, in general shall: • Continue the curricular offerings of the graduate school, colleges of engineering, architecture and fine arts, technology, education, computer studies, business and accountancy, arts and social sciences, public administration, human kinetics, law, nursing, science and information technology related courses. • Offer other courses that the Board of Regents may deem necessary. • Continue to develop TSU into a regional center of excellence in engineering, technological, business and teacher education, research and extension in order to produce graduates who are globally competitive. • In an environment valuing freedom, excellence and equity, TSU shall provide and maintain relevant instruction, research, extension and production programs effectively to develop responsible members of the society imbued with critical and creative thinking. -

CHER Hongkong 2018 the IAFOR Conference for Higher Education Research – Hong Kong 2018
CHER HongKong2018 Draft Schedule CHER HongKong 2018 The IAFOR Conference for Higher Education Research – Hong Kong 2018 Friday, October 19 - Sunday, October 21, 2018 Lingnan University, Hong Kong Final Draft Schedule Please Check & Confirm Please check that all information pertaining to you is correct and notify us at [email protected] if there is any error. Please notify us of any corrections by Thursday, September 27 17:00 (GMT+8). Final Schedule After minor changes have been made to the schedule we will send you a link to the final schedule. The final schedule will contain session information and a detailed day-to-day presentation schedule (including room allocations and session chairs). This will be available on Monday, October 8. The International Academic Forum 1 CHER HongKong2018 Draft Schedule Friday at a Glance October 19, 2018 09:15-10:00 Conference Registration & Coffee 10:00-10:10 Opening Announcements Kiyoshi Mana, Director of Events, IAFOR 10:10-10:20 Welcome Address Joseph Haldane, IAFOR, Japan 10:20-10:50 Welcome Address Joshua Ka Ho Mok, Lingnan University, Hong Kong 10:50-11:35 Keynote Presentation I Innovation and Entrepreneurship at a Liberal Arts University? The Experience of Lingnan University Leonard K Cheng, Lingnan University, Hong Kong 11:35-12:20 Keynote Presentation II Innovation, Entrepreneurship and the Shift to the East Anthony Welch, University of Sydney, Australia 12:20-12:35 IAFOR Documentary Photography Award | 2018 Winners Screening 12:35-12:45 Conference Photograph 12:45-14:00 Lunch -
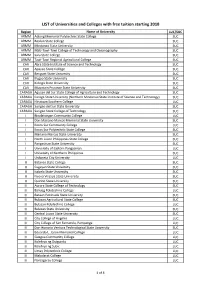
LIST of Universities and Colleges with Free Tuition Starting 2018
LIST of Universities and Colleges with free tuition starting 2018 Region Name of University LUC/SUC ARMM Adiong Memorial Polytechnic State College SUC ARMM Basilan State College SUC ARMM Mindanao State University SUC ARMM MSU-Tawi-Tawi College of Technology and Oceanography SUC ARMM Sulu State College SUC ARMM Tawi-Tawi Regional Agricultural College SUC CAR Abra State Institute of Science and Technology SUC CAR Apayao State College SUC CAR Benguet State University SUC CAR Ifugao State University SUC CAR Kalinga State University SUC CAR Mountain Province State University SUC CARAGA Agusan del Sur State College of Agriculture and Technology SUC CARAGA Caraga State University (Northern Mindanao State Institute of Science and Technology) SUC CARAGA Hinatuan Southern College LUC CARAGA Surigao del Sur State University SUC CARAGA Surigao State College of Technology SUC I Binalatongan Community College LUC I Don Mariano Marcos Memorial State University SUC I Ilocos Sur Community College LUC I Ilocos Sur Polytechnic State College SUC I Mariano Marcos State University SUC I North Luzon Philippines State College SUC I Pangasinan State University SUC I University of Eastern Pangasinan LUC I University of Northern Philippines SUC I Urdaneta City University LUC II Batanes State College SUC II Cagayan State University SUC II Isabela State University SUC II Nueva Vizcaya State University SUC II Quirino State University SUC III Aurora State College of Technology SUC III Baliuag Polytechnic College LUC III Bataan Peninsula State University SUC III Bulacan Agricultural State College SUC III Bulacan Polytechnic College LUC III Bulacan State University SUC III Central Luzon State University SUC III City College of Angeles LUC III City College of San Fernando, Pampanga LUC III Don Honorio Ventura Technological State University SUC III Eduardo L. -
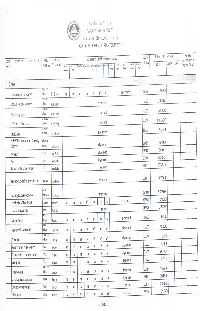
APP-2015-NEW.Pdf
Pages 1 of 103 ANNUAL PROCUREMENT PLAN FOR 2015 For Common-Use Supplies and Equipment INSTRUCTIONS IN FILLING OUT THE ANNUAL PROCUREMENT PLAN (APP) FORM: 1. Select the appropriate worksheet depending on the nearest Regional/Provincial Depot in your area. 2. For Sub - Depots please refer to the following (Arranged/ Classified according to commmonality of freight cost): a. Bukidnon, Puerto Princesa Palawan, Biliran, Borongan, Misamis Occidental (Oroquieta) and Southern Leyte (Maasin)- Region XIII b. Misamis Oriental, Bacolod, Calbayog, Bontoc and Northern Samar (Catarman)- Regions VI, VII, VIII, X, & XI c. Surigao Del Norte - Surigao Del Norte d. Zamboanga Sibugay- Zamboanga Sibugay e. Camiguin - Camiguin 3. Indicate the agency’s monthly requirement per item in the APP form. The form will automatically compute for the Total Quarterly requirement, Total Amount per item and the Grand Total. 4. APPs are considered incorrect if: a) form used is other than the prescribed format downloaded at philgeps.gov.ph and; b) correct format is used but fields were deleted and/or inserted in Portion A of the APP. The agency will be informed through e-mail if the submission is incorrect. 5. For Other Items not available from the Procurement Service but regularly purchased from other sources, agency must specify/indicate the item name under each category and unit price based on their last purchase of the item/s. These items will be evaluated by the Procurement Service and may be considered Common Supplies or Equipment (CSE). Items will be added to the electronic catalogue / virtual store as soon as it is procured and made available by the Procurement Service. -

ANNUAL PROCUREMENT PLAN for 2014 for Common-Use Supplies and Equipment
ANNUAL PROCUREMENT PLAN FOR 2014 For Common-Use Supplies and Equipment Department/Bureau/Office: TARLAC STATE UNIVERSITY Region: III Address: Romulo Boulevard, San Vicente, Tarlac City Unit of PS Price Item & Specifications Measur MONTH Catalogue as of e (07.11.13) TOTAL COST Mar Jun Sep Oct Nov Dec TOTAL COMMON ELECTRICAL SUPPLIES 1 BALLAST, 18 watts piece 0 67.77 - 2 BALLAST, 36 watts piece 0 - 3 BATTERY, size AA, alkaline, 2 pcs./packet 104 53 84 53 294 20.42 6,003.48 packet 4 4. BATTERY, size AAA, alkaline, 2 pcs./packet 77 48 68 48 241 15.31 3,689.71 packet 5 BATTERY, size D, alkaline, 2 pcs./packet 5 2 7 76.00 532.00 packet 6 FLUORESCENT LIGHTING FIXTURE, 1 x 20W set 0 316.68 - 7 FLUORESCENT LIGHTING FIXTURE, 1 x 40W set 25 25 25 25 100 369.46 36,946.00 8 FLUORESCENT LAMP, tubular, 18 watts piece 50 50 50 50 200 35.89 7,178.00 9 FLUORESCENT LAMP, tubular, 36 watts piece 10 10 20 36.95 739.00 10 COMPACT FLUORESCENT LIGHT, 18 watts piece 0 102.29 - 11 FUSE, 30 amperes piece 0 12.67 - 12 FUSE, 60 amperes piece 0 25.33 - 13 STARTER, 4‐40 watts piece 30 20 30 20 100 3.55 355.00 14 TAPE, electrical roll 13 10 13 10 46 19.53 898.38 0 - COMMON COMPUTER SUPPLIES/CONSUMABLES 0 - 1 COMPUTER CONTINUOUS FORMS, 1 ply, 11" x 9‐1/2", 2000 sheets/box box 84 7 30 3 124 452.35 56,091.40 2 . -

Tarlac State University Student Manual
TARLAC STATE UNIVERSITY STUDENT MANUAL 1 TARLAC STATE UNIVERSITY STUDENT MANUAL 2 TARLAC STATE UNIVERSITY STUDENT MANUAL Republic of the Philippines TARLAC STATE UNIVERSITY Tarlac City STUDENT MANUAL 2017 3 TARLAC STATE UNIVERSITY STUDENT MANUAL 4 TARLAC STATE UNIVERSITY STUDENT MANUAL i TABLE OF CONTENTS History of the Tarlac State University 1 Philosophy 2 Vision 2 Mission 2 Core Values 3 Philosophy Statement 3 University Logo 4 Part I: GENERAL PROVISIONS 5 Chapter 1: Preliminary Matters 6 Chapter 2: Declaration of Principles 7 Chapter 3: Students’ Rights and Obligations 7 Part II: ADMISSION AND REGISTRATION 11 Chapter 1: Admission 12 A. New Freshmen Students 12 B. Transferees 13 C. Foreign Students 14 D. Cross-enrollees 15 E. Special/Audit Students/Refresher Course Students 15 Chapter 2: Registration 15 A. Academic Load 16 B. Cross-Enrolment 17 C. Changing/Adding/Dropping of Subjects 17 D. Shifting from One Course to Another 18 E. Withdrawal of Registration 18 F. Pre-requisite Subject/s 18 G. Validation of Subject/s 19 Chapter 3: Validation/Accreditation 19 Chapter 4: Attendance and Related Matters 20 A. Attendance 20 B. Leave of Absence 21 Chapter 5: Examinations 21 Chapter 6: Grading System 22 Chapter 7: Retention Policies 22 Chapter 8: Academic Scholarship 23 5 TARLAC STATE UNIVERSITY STUDENT MANUAL ii Chapter 9: Transfer Credentials 24 Chapter 10: Graduation 24 Chapter 11: Graduation with Honors 25 Chapter 12: Recognition, Baccalaureate, and Graduation Program 26 Chapter 13: Transcript of Records, Form 137A, and Certifications 27 Part III: FEES AND PAYMENTS 28 Chapter 1: Fees and Payment 29 Part IV: STUDENT SERVICES AND FACILITIES 30 Chapter 1: Library Management and Services 31 Chapter 2: Medical Services Unit 33 A. -

Ÿþc M O 9 S 2 0 1 9 S U C L E V E L O F 1 0 6 S U
HIGII ,‘ Republic of the Philippines 01.N on High C/) OFFICE OF THE PRESIDENT 0 COMMISSION ON HIGHER EDUCATION foFFIcIAL. e RELEASE 13 CHED Central Office Cl CHED Memorandum Order RECORDS SECTION No. 09 tzy Series of 2019 e., U.r. GO\ Subject : SUC LEVEL OF 106 STATE UNIVERSITIES AND COLLEGES In accordance with the pertinent provisions of Republic Act (RA) No. 7722, otherwise known as the "Higher Education Act of 1994" and Republic Act (RA) No. 8292, otherwise known as the "Higher Education Modernization Act of 1997", pursuant to Joint Circular No. 1, s. 2016, otherwise known as the "FY 2016 Levelling Instrument for SUCs and Guidelines for the Implementation Thereof," and National Evaluation Committee (NEC) Resolution Nos. 1 and 2, s. 2019, the Commission on Higher Education (CHED) hereby issues the following: I. List of SUCs with their corresponding levels pursuant to CM° 12, s. 2018 titled "2016 SUC Levelling Results, SUC Levelling Benefits and SUC Levelling Appeal Procedures" effective August 20, 2018: No. Region State University / College SUC LEVEL 1 I Ilocos Sur Polytechnic State College III 2 I Mariano Marcos State University IV 3 I North Luzon Philippines State College I 4 I Pangasinan State University IV 5 II Batanes State College I 6 II Cagayan State University III 7 II Isabela State University IV 8 ll Nueva Vizcaya State University IV 9 II Quirino State University II 10 III Aurora State College of Technology II 11 III Bataan Peninsula State University III 12 III Bulacan Agricultural State College III 13 III Central Luzon State -

2020 Annual Report
2020 ANNUAL REPORT UNIVERSITY RESEARCH OFFICE Email: [email protected] Tel: 606- 8190 Address: TSU Villa Lucinda Extension Campus 2 LIST OF DIAGRAMS Number Diagram Title Page Number Diagram 1 TSU Framework for Research 4 Diagram 2 URO Organizational Chart 5 Diagram 3. Integration of ICT and GAD to the Research Agenda 7 LIST OF TABLES Number Table Title Page Number Table 1 List of Research Proposals submitted during the 10 CRPC Table 2 List of Presented Research Proposals during the 21 University- wide Colloquium List of On- going Research Proposals with Total Line- Table 3 23 item Budget (LIB) Table 4 List of Research Publication Incentives 27 Table 5 List of Research Presentation Incentives 27 Table 6 List of Research Citation Incentives 28 Approved matrix guide on the Turnitin ASI % Table 7 applicable to all articles/ researches submitted by 39 students or researchers of the Tarlac State University Table 8 List of Updated Office Forms Table 9 PBB Accomplishments per College 49 Table 10 PBB Accomplishments Per Faculty Member 49 Table 11 Summary of Research Accomplishments per College 51 Table 12 Research Accomplishments of the Faculty 51 Researchers in the CAFA Table 13 Research Accomplishments of the Faculty 52 Researchers in the CASS Table 14 Research Accomplishments of the Faculty 53 Researchers in the CBA Table 15 Research Accomplishments of the Faculty 54 Researchers in the CCS Table 16 Research Accomplishments of the Faculty 54 Researchers in the CCJE Table 17 Research Accomplishments of the Faculty 55 Researchers in the CET Table 18 Research Accomplishments of the Faculty 56 Researchers in the CPAG Table 19 Research Accomplishments of the Faculty 56 Researchers in the COS Table 20 Research Accomplishments of the Faculty 57 Researchers in the CTE UNIVERSITY RESEARCH OFFICE Email: [email protected] Tel: 606- 8190 Address: TSU Villa Lucinda Extension Campus 3 INTRODUCTION The University Research Office is composed of five (5) units namely: 1. -

Manual on Rules and Regulations of the TSU IP Policy
Manual on Rules and Regulations of the TSU IP Policy The primary purpose of this IRR is to provide protection and incentives to encourage both the discovery and development of new knowledge and its transfer for public benefit. A secondary purpose is to enhance the generation of revenue for the University and creators. Revenues accruing to the University as a result of the commercialization of intellectual property covered in this manual will be for the purposes of advancing the University’s mission. The University is guided by the following objectives: 1. To ensure that the mission of the University is advanced; 2. To optimize the environment and incentives for research and for the creation of new knowledge at the University; 3. To bring the results of research and scholarship into practical use for the public benefit as quickly and effectively as possible; 4. To protect the interests/rights of faculty, staff, and students through their investment in research and scholarship. Introduction and Brief History The Board of Regents on its Special Meeting on July 30, 2007 at CHED Central Office, Pasig City, passed Resolution No.62, s.2007 approving the “Policies on Intellectual Property of the Tarlac State University”. By virtue of the TSU administrative order No. 20, s.2007 dated August 7, 2007, the “Office of the Intellectual Property” of TSU was established effective August 8, 2007 under the Office of the President then it was later placed under the Office of the Vice-President for Research, Extension, and Planning. The establishment of the Intellectual Property policy of the University is intended to strengthen current protection of the reputation of the name “Tarlac State University” and their variations and appendages. -

The Philippines Are a Chain of More Than 7,000 Tropical Islands with a Fast Growing Economy, an Educated Population and a Strong Attachment to Democracy
1 Philippines Media and telecoms landscape guide August 2012 1 2 Index Page Introduction..................................................................................................... 3 Media overview................................................................................................13 Radio overview................................................................................................22 Radio networks..........……………………..........................................................32 List of radio stations by province................……………………………………42 List of internet radio stations........................................................................138 Television overview........................................................................................141 Television networks………………………………………………………………..149 List of TV stations by region..........................................................................155 Print overview..................................................................................................168 Newspapers………………………………………………………………………….174 News agencies.................................................................................................183 Online media…….............................................................................................188 Traditional and informal channels of communication.................................193 Media resources..............................................................................................195 Telecoms overview.........................................................................................209 -

Adversity Quotient, Leadership Style and Performance of Secondary School Heads and Commitment to Organizational Values Of
1 Republic of the Philippines University of St. La Salle Bacolod City APPROVAL SHEET This dissertation of Jessie B. Aquino, entitled “Adversity Quotient, Leadership Style and Performance of Secondary School Heads and Commitment to Organizational Values of Teachers in the Province of Tarlac”, which is prepared and submitted in partial fulfillment of the requirements for the degree Doctor of Education is hereby accepted. NIÑO B. CORPUZ, Ed. D., RGC Adviser DISSERTATION COMMITTEE NICANOR C. CAINGAT, Ph. D. Chairman ELENA A. HAMSILANI, Ph. D. MYRNA Q. MALLARI, DBA Member Member Accepted and approved in partial fulfillment of the requirements for the degree Doctor of Education. Comprehensive Examination passed. DR. MYRNA Q. MALLARI Academic Administrator Date: ____________________ 2 ADVERSITY QUOTIENT, LEADERSHIP STYLE AND PERFORMANCE OF SECONDARY SCHOOL HEADS AND COMMITMENT TO ORGANIZATIONAL VALUES OF TEACHERS IN THE PROVINCE OF TARLAC A Dissertation Presented to the Faculty of Graduate School University of St. La Salle Bacolod City In Partial Fulfillment of the Requirements for the Degree Doctor of Education JESSIE B. AQUINO 2013 ABSTRACT 3 Title: ADVERSITY QUOTIENT, LEADERSHIP STYLE AND PERFORMANCE OF SECONDARY SCHOOL HEADS AND COMMITMENT TO ORGANIZATIONAL VALUES OF TEACHERS IN THE PROVINCE OF TARLAC Researcher: Jessie B. Aquino Degree: Doctor of Education Institution: University of St. La Salle, Bacolod City This study was conducted to determine the relationship of adversity quotient, leadership style and performance of secondary school heads and commitment to organizational values of teachers in the Province of Tarlac. The following concerns were looked into: the school heads’ adversity quotient, leadership styles and performance, commitment of teachers to organizational values and the relationship among these variables; the influence of adversity quotient and leadership style to performance and commitment and; a model showing the nature of influence of adversity quotient and leadership to performance and commitment. -

Professional Regulation Commission BAGUIO REGIONAL OFFICE LICENSURE EXAMINATION for PROFESSIONAL TEACHERS SEPTEMBER 30, 2018
Professional Regulation Commission BAGUIO REGIONAL OFFICE LICENSURE EXAMINATION FOR PROFESSIONAL TEACHERS SEPTEMBER 30, 2018 BAGUIO TESTING ROOMCENTER / GROUP - ELEMENTARY NO.: 01 LEVEL PLACE OF EXAM : AGUINALDO ELEMENTARY SCHOOL ADDRESS : EVERLASTING ST., BAGUIO CITY BUILDING : ROOM / GROUP NO.: FLOOR : 01 Seat LAST NAME FIRST NAME MIDDLE NAME School Graduated From No. 1 ABACCO JOBELLE REBUCAS DON MARIANO MARCOS MEMORIAL STATE UNIVERSITY-AGOO 2 ABACO MARIA RELNA MENDOZA IFUGAO STATE UNIVERSITY (for. IFUGAO SCAF)-LAMUT 3 ABAD JAZEL JOYCE DELA CUADRA UNIVERSITY OF PANGASINAN 4 ABAD JENNY BESO NORTHWEST SAMAR STATE UNIVERSITY (FOR.TIBURCIO TANCINCO) 5 ABAD JULIE ANNE CABANAS TOMAS DEL ROSARIO ACADEMY 6 ABAD MARY JANE ARBIZO MAGSAYSAY MEMORIAL COLLEGE OF ZAMBALES 7 ABAD RUBY ANN JIMENEZ RAMON MAGSAYSAY TECHNOLOGICAL UNIVERSITY-IBA 8 ABADILLA NELVIE BIALBA RAMON MAGSAYSAY TECHNOLOGICAL UNIVERSITY-IBA 9 ABAGAT RIZZA DE VERA LYCEUM NORTHWESTERN UNIV-DAGUPAN CITY 10 ABALOS ELLA BITONIO SAINT MARY'S COLLEGE-ILOCOS SUR 11 ABALOS JOCELYN DELA CRUZ ADELPHI COLLEGE 12 ABALOS MILDRED FERRER MYSTICAL ROSE COLLEGE OF SCIENCE & TECHNOLOGY 13 ABALOS VANESSA ROSE BUYAGAO PANGASINAN STATE UNIVERSITY-URDANETA 14 ABAN FEBIE PUNASEN KING'S COLLEGE OF THE PHILIPPINES INC.- BENGUET (for E.L.C) 15 ABANDO LEANNE MAE DEL ROSARIO MOUNTAIN PROV. STATE POLYTECHNIC COLLEGE-BONTOC 16 ABANES CRISTINE VILLACACAN DON MARIANO MARCOS MEMORIAL STATE UNIVERSITY-AGOO 17 ABANSI GRIEL ATABAN KING'S COLLEGE OF THE PHILIPPINES INC.- BENGUET (for E.L.C) 18 ABARRA ALEXANDER ARIOLA PASS COLLEGE (PHIL. ACCOUNTANCY & SCIENCE SCH.) IMPORTANT REMINDERS: 1 PLEASE REPORT TO PRC BAGUIO REGIONAL OFFICE OR EMAIL US AT [email protected] IF THERE ARE ERRORS/DISCREPANCIES.