Border Control
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

U.S. Customs and Border Protection * Volume 4, Issue 3
U.S. Customs and Border Protection H Volume 4, Issue 3 SPECIAL 9 / 11 EDITION In Memoriam H H H In honor of CBP employees who have died in the line of duty 2011 Hector R. Clark Eduardo Rojas Jr. 2010 Charles F. Collins II Michael V. Gallagher Brian A. Terry Mark F. Van Doren John R. Zykas 2009 Nathaniel A. Afolayan Cruz C. McGuire Trena R. McLaughlin Robert W. Rosas Jr. 2008 Luis A. Aguilar Jarod Dittman 2007 Julio E. Baray Eric Cabral Richard Goldstein Ramon Nevarez Jr. Robert Smith Clinton B. Thrasher David J. Tourscher 2006 Nicholas D. Greenig David N. Webb 2004 Travis Attaway George DeBates Jeremy Wilson 2003 James P. Epling H H H For a historic listing honoring federal personnel who gave their lives while securing U.S. borders, please visit CBP.gov Vol 4, Issue 3 CONTENTS H FEATURES VOL 4, ISSUE 3 4 A Day Like No Other SEPTEMBER 11, 2011 In the difficult hours and days after the SECRETARY OF HOMELAND SECURITY Sept. 11 attacks, confusion and fear Janet Napolitano turned to commitment and resolve as COMMISSIONER, the agencies that eventually would form 4 U.S. CUSTOMS AND BORDER PROTECTION CBP responded to protect America. Alan D. Bersin ASSISTANT COMMISSIONER, 16 Collective Memory OFFICE OF PUBLIC AFFAIRS Melanie Roe CBP employees look back on the day that united an agency… and a nation. EDITOR Laurel Smith 16 CONTRIBUTING EDITORS 41 Attacks Redefine Eric Blum Border Security Susan Holliday Marcy Mason CBP responds to challenge by coming Jay Mayfield together to build layers of security Jason McCammack extending around the globe, upgrading its ability to keep dangerous people PRODUCTION MANAGER Tracie Parker and things out of the homeland. -

Before You Go... Stop! Essential Information for New Zealanders
Essential information for New Zealanders travelling overseas. LOG ON BEFORE YOU TAKE OFF safetravel.govt.nz New Zealanders love to experience the thrill of travel. But sometimes travel brings nasty surprises like medical bills, natural disasters and crime. If you plan ahead, you can reduce these risks. Make sure you are prepared to tackle anything unexpected that comes your way. Whenever you travel, check our latest travel advice, register your details and remember to get travel insurance. Important messages for New Zealand passport holders.................................................................................4 Contents Before you go Safe travel matters!............................................................................7 Log on before you take off..................................................................7 Tips for safe travel..................................................................9 Your passport..........................................................................13 How do I get a passport in New Zealand?.....................................13 How do I get a passport overseas?.................................................14 Tips for keeping your passport secure..........................................14 How do I get a visa for another country?.......................................15 Online authorisation needed for travellers to the United States of America.......................................................15 Aviation security.....................................................................15 -

Runway to Recovery
Runway to Recovery The United States Framework for Airlines and Airports to Mitigate the Public Health Risks of Coronavirus Guidance Jointly Issued by the U.S. Departments of Transportation, Homeland Security, and Health and Human Services Version 1.1 | December 2020 CONTENTS – 03 Overview 07 Principles 09 Air Transportation Stakeholder Roles and Responsibilities 11 A Risk-Based Approach for COVID-19 Outbreak Mitigation Planning 14 Public Health Risk Mitigation in the Passenger Air Transportation System 49 Future Areas of Research and Evaluation for Public Health Risk Mitigations 51 Implementation Challenges Specific to International Travel 53 Appendix A: Key Partners and Decision-Makers OVERVIEW A safe, secure, efficient, and resilient air transportation system is essential to our Nation’s physical, economic, and social health. The Coronavirus Disease 2019 (COVID-19) public health emergency has demonstrated that protecting public health in the air transportation system is just as critical as aviation safety and security to the confidence of the flying public. Government, aviation, and public health leaders have been working together—and must continue to do so—to meaningfully reduce the public health risk and restore passenger, aviation workforce (including aircrew), and public confidence in air travel. The U.S. Government continues to assess the evolving situation and the effectiveness of actions and recommendations implemented to date. This updated guidance reflects this continual assessment and updated information. Although there are some updates and adjustments throughout, the key additions and changes in this document include new information on: » Passenger and Aviation Workforce Education » Contact Tracing » Mask Use, specifically the need to accommodate those who cannot wear masks » Passenger Testing This document provides the U.S. -
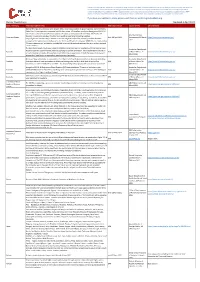
Border Restrictions Updated 6 April 2021
Please note, although we endeavour to provide you with the most up to date information derived from various third parties an d sources, we cannot be held accountable for any inaccuracies or changes to this information. Inclusion of company information in this matrix does no t imply any business relationship between the supplier and WFP / Logistics Cluster, and is used solely as a determinant of services, and capacities. Logistics Cluster /WFP maintain complete impartiality and are not in a position to endorse, comment on any company's suitability as a reputable serv ice provider. If you have any updates to share, please email them to: [email protected] Border Restrictions Updated 6 April 2021 State / Territory Restrictions (Other Info) Restriction Period Source of Info URL / Remarks State of Emergency is extended until 18 April 2021. Color-coded system to guide response. Current level is Code Blue. All entry permits suspended until further notice. All travellers must provide negative COVID-19 test results within 72 hours before arrival and are subject to full quarantine of 14 days. Moreover, the American Samoa traveller is required to disclose if he/she had a positive result prior to testing negative. American Samoa Until 18 April 2021 Government, 19 March https://www.americansamoa.gov/ Cargo flights into the Territory to deliver or retrieve cargo or mail will be allowed, provided that each 2021 occupant of the plane must furnish proof to the Director of Health of a negative COVID-19 test results within 72 hours before arrival, and further provided tht no one will disembark withouth the prior written approval of the Governor. -

International Boundary Cities: the Debate of Transfrontier Planning in Two Border Regions
Volume 31 Issue 3 Summer 1991 Summer 2020 International Boundary Cities: The Debate of Transfrontier Planning in Two Border Regions Lawrence A. Herzog Recommended Citation Lawrence A. Herzog, International Boundary Cities: The Debate of Transfrontier Planning in Two Border Regions, 31 Nat. Resources J. 587 (2020). Available at: https://digitalrepository.unm.edu/nrj/vol31/iss3/6 This Article is brought to you for free and open access by the Law Journals at UNM Digital Repository. It has been accepted for inclusion in Natural Resources Journal by an authorized editor of UNM Digital Repository. For more information, please contact [email protected], [email protected], [email protected]. LAWRENCE A. HERZOG* International Boundary Cities: The Debate on Transfrontier Planning in Two Border Regions** ABSTRACT For the first time in modern history, large-scale cities are evolving along the borders of nation-states. The settlement pattern is one in which urban residents on either side of the boundary are enmeshed in a singularfunctional region, or "transfrontiermetropolis." Eco- logical resources are shared within these common transboundary living spaces. Environmental problems such as sewage contamina- tion, hazardous waste spillage, or air pollution are also shared. While cooperative transborderplanning has been proposed as a means for resolving these problems, it is not clear that such an approachworks. This article examines the transfrontierpolicy debate for two important boundary regions: Western Europe and the U.S.- Mexico border. Western Europe'srecord of transfrontiercooperation is critically reviewed. While the volume of transfrontierplanning projects has mushroomed there during the past decade, many struc- tural obstacles to long term cooperation remain. -

CBP Has Improved Southwest Border Technology, but Significant Challenges Remain
CBP Has Improved Southwest Border Technology, but Significant Challenges Remain February 23, 2021 OIG-21-21 OFFICE OF INSPECTOR GENERAL Department of Homeland Security Washington, DC 20528 / www.oig.dhs.gov February 2, 2021 MEMORANDUM FOR: Troy A. Miller Senior Official Performing the Duties of the Commissioner U.S. Customs and Border Protection FROM: Joseph V. Cuffari, Ph.D. Digitally signed by JOSEPH V JOSEPH V CUFFARI Inspector General Date: 2021.02.22 CUFFARI 15:16:43 -05'00' SUBJECT: CBP Has Improved Southwest Border Technology, but Significant Challenges Remain Attached for your action is our final report, CBP Has Improved Southwest Border Technology, but Significant Challenges Remain. We incorporated the formal comments provided by your office. The report contains three recommendations aimed at improving border security technology and situational awareness of the southwest border. Your office concurred with all three recommendations. Based on information provided in your response to the draft report, we consider all three recommendations resolved and open. Once your office has fully implemented the recommendations, please submit a formal closeout letter to us within 30 days so that we may close the recommendations. The memorandum should be accompanied by evidence of completion of agreed-upon corrective actions. Please send your response or closure request to [email protected]. Consistent with our responsibility under the Inspector General Act, we will provide copies of our report to congressional committees with oversight and appropriation responsibility over the Department of Homeland Security. We will post the report on our website for public dissemination. Please call me with any questions, or your staff may contact Thomas Kait, Acting Assistant Inspector General for Audits, at (202) 981-6000. -

CERN to Cross Border Into France
CCEJan/FebArchive11 23/1/06 16:45 Page 11 CERN COURIER ARCHIVE: 1963 A look back to CERN Courier vol. 3, January 1963 LOOKING AHEAD CERN to cross border into France The 23rd session of CERN Council was held on 19 December 1962, under the presidency THE ORGANIZATION of Mr Jean Willems (Belgium). The president CERN in a nutshell opened the session by a tribute to the memory of Prof. Niels Bohr, one of the The European Organization for Nuclear founders of CERN, who died on 18 November. Research (CERN) came into being in 1954 Commenting on the progress report of the as a cooperative enterprise among Organization, Prof. V F Weisskopf, the Director- European governments in order to regain a general, stated that “1962 was a decisive year first-rank position in nuclear science. At for CERN…which now has a healthy scientific present it is supported by 13 Member programme exploiting reasonably well the States, with contributions according to their opportunities of the two accelerators, within national revenues: Austria (1.92 %), the limits of our present state of development”. Belgium (3.78), Denmark (2.05), Federal In a statement concerning the programme Republic of Germany (22.47), France and budget, however, Prof. Weisskopf issued (18.34), Greece (0.60), Italy (10.65), a warning, pointing out that the success of our The size of the new experimental hall in the Netherlands (3.87), Norway (1.46), Spain laboratory does not mean that its facilities are East area of the PS can be seen in this aerial (3.36), Sweden (4.18), Switzerland (3.15), fully exploited. -

Complaint Mechanisms in Border Management and Expulsion Operations in Europe
COMPLAINT MECHANISMS IN BORDER MANAGEMENT AND EXPULSION OPERATIONS IN EUROPE EFFECTIVE REMEDIES FOR VICTIMS OF HUMAN RIGHTS VIOLATIONS? Sergio Carrera and Marco Stefan COMPLAINT MECHANISMS IN BORDER MANAGEMENT AND EXPULSION OPERATIONS IN EUROPE EFFECTIVE REMEDIES FOR VICTIMS OF HUMAN RIGHTS VIOLATIONS? SERGIO CARRERA AND MARCO STEFAN CENTRE FOR EUROPEAN POLICY STUDIES (CEPS) BRUSSELS The Centre for European Policy Studies (CEPS) is an independent policy research institute in Brussels. Its mission is to produce sound policy research leading to constructive solutions to the challenges facing Europe. The views expressed in this book are entirely those of the authors and should not be attributed to CEPS or any other institution with which they are associated or to the European Union. Prof. Sergio Carrera is Senior Research Fellow and Head of Justice and Home Affairs Programme at CEPS, Brussels. He is also Part-Time Professor at the Migration Policy Centre (MPC) in the European University Institute (EUI) in Florence (Italy) and Visiting Professor at the Paris School of International Affairs (PSIA) in Sciences Po, Paris (France). Dr. Marco Stefan is Research Fellow in the Justice and Home Affairs Programme at CEPS. Cover illustration by LeStudio / Shutterstock.com. Cover design Margaita Minkova. ISBN 978-94-6138-677-9 © Copyright 2018, CEPS All rights reserved. No part of this publication may be reproduced, stored in a retrieval system or transmitted in any form or by any means – electronic, mechanical, photocopying, recording or otherwise – without the prior permission of the Centre for European Policy Studies. Centre for European Policy Studies Place du Congrès 1, B-1000 Brussels Tel: (32.2) 229.39.11 E-mail: [email protected] Internet: www.ceps.eu Contents Preface ..................................................................................................................................................... -

Kenya - Somalia Border Tel.: +254 20 4222000 Email: [email protected] Sources: UNHCR, Global Insight Digital Mapping © 1998 Europa Technologies Ltd
Geographic Information Systems and Mapping Unit UNHCR Regional Support Hub in Nairobi Kenya - Somalia Border Tel.: +254 20 4222000 Email: [email protected] Sources: UNHCR, Global Insight digital mapping © 1998 Europa Technologies Ltd. Overview Map The boundaries and names shown and the designations used on this map do not imply official endorsement or acceptance by the United Nations. KEN_Somalia_Border_A3PC.WOR DambelDambel Daro Daro WarsaWarsa BurBur AminoAmino !!! !!! !!! ((( ((( !!! ((( ((( ((( !!! ((( ((( ((( !!! ((( ((( ((( MalkamariMalkamari ((( DoloDolo BayBay ((( WalgindaWalginda MalkamariMalkamari DoloDolo BayBay ((( ((( WalgindaWalginda ((( ((( DolloDollo AdoAdo ((( GayuGayu DodoDodo ChilagoChilagoChilago HullowHullow ((( DolloDollo AdoAdo DolloDollo AdoAdo !! ElgayElgayElgay SodigaSodigaSodiga ((( DoolowDoolow ElgayElgayElgay SodigaSodigaSodiga ((( AdiliAdiliAdili DoolowDoolow AdiliAdiliAdili ((( ((( ((( ((( ((( ((( ArdaArdaArda Garbicha GarbichaGarbicha ((( ((( DebureDebure ((( DidagemboDidagembo ((( DebureDebure DidagemboDidagembo ((( FiyakoFiyakoFiyako FiyakoFiyakoFiyako ((( FiyakoFiyakoFiyako ((( FiyakoFiyakoFiyako ((( ((( FiyakoFiyakoFiyako ((( ((( ((( ((( ((( ((( JimaJimaJimaJima Sidamo SidamoSidamoSidamo ((( !!! ((( ((( OdaOda JimaJimaJimaJima Sidamo SidamoSidamoSidamo ((( LulisLulisLulis RhamuRhamu DintoDinto !!! ((( OdaOda LuuqLuuq RhamuRhamu DintoDinto ((( LuuqLuuq HareriHareri ((( MelkaMelka SuftuSuftu HareriHareri !!! ((( DoloDolo Bella!Bella!Bella! ((( DoloDolo ETHIOPIAETHIOPIA !!! BellaBellaBella -

The Context and Risk of Organised Illegal Immigration to New Zealand
The Context and Risk of Organised Illegal Immigration to New Zealand: An Exploration in Policy Relevant Research Greg Talcott Centre for Strategic Studies Victoria University of Wellington, New Zealand. No.15/00 1 CENTRE FOR STRATEGIC STUDIES NEW ZEALAND Working Papers The Centre for Strategic Studies Working Paper series is designed to give a forum for scholars and specialists working on issues related directly to New Zealand’s security, broadly defined, and to the Asia- Pacific region. The Working Papers represent ‘work in progress’ and as such may be altered and expanded after feedback before being published elsewhere. The opinions expressed and conclusions drawn in the Working Papers are solely those of the writer. They do not necessarily represent the views of the Centre for Strategic Studies or any other organisation with which the writer may be affiliated. For further information or additional copies of the Working Papers please contact: The Centre for Strategic Studies Victoria University of Wellington PO Box 600 Wellington New Zealand. Tel: 64 4 463 5434 Fax: 64 4 463 5737 Email: [email protected] This paper is based on intelligence analysis written by the author for the New Zealand Customs Service. The opinions expressed in this paper are solely the author’s and do not necessarily reflect those of the New Zealand Customs Service or the Centre for Strategic Studies: New Zealand. Centre for Strategic Studies Victoria University of Wellington 2000 © Greg Talcott ISSN 1175-1339 Desktop Design: Synonne Rajanayagam 2 The Context and Risk of Organised Illegal Immigration to New Zealand: An Exploration in Policy Relevant Research Working Paper 15/00 Abstract “People smuggling,” or organized illegal immigration, is one of the new breed of transnational issues confronting states all over the developed world. -

Texas Border Security Monthly Brief
Texas Border Security June 2021 Strategic Intent The Texas Department of Public Safety (DPS) will work with its local and state partners to provide direct assistance to U.S. Customs and Border Protection to deter, detect and interdict smuggling along the Texas/Mexico border through the deployment of an integrated network of detection and communication technologies and an increase in ground, air and marine interdiction assets. DPS will work with its local and federal partners and the Border Prosecution Unit to degrade the smuggling infrastructure used by the cartel plaza bosses to smuggle drugs and people into Texas. The Texas Rangers will work with the Border Prosecution Unit and our federal partners to deter smuggling related corruption along the border by increasing the number of public corruption investigations, arrests and prosecutions. DPS will work with its local and federal partners to target transnational criminal activity including drug trafficking, labor trafficking, sex trafficking and money laundering in key Texas transshipment and trafficking centers and other impacted areas throughout the state. (I) DPS Deterrence and Detection Assets Deployed DPS enhances the level of detection coverage directly on the border through the deployment of motion detection cameras, day and night tactical boat patrols, helicopter patrols, and fixed wing aircraft patrols with FLIR and integrated communications technology. A. DPS Maritime Assets The State of Texas has deployed DPS and TPWD boats on the Rio Grande River to deter and detect smuggling activity. DPS Boats Assigned to the Border: Tactical Boats Deployed Pending Totals Shallow Water 6 -- 6 Extreme Shallow Jet 7 -- 7 Total 13 -- 13 1 B. -

Practical Guide to Cross-Border Donations
PRACTICAL GUIDE TO CROSS-BORDER DONATIONS 1 TO FACILITATE PHILANTHROPY WITHOUT BORDERS IN EUROPE Foreword Dear Sir, Madam, Founded almost 20 years ago, the Transnational Giving Europe (TGE) network was created to make cross-border philanthropy more accessible. Now active in 20 countries across Europe, including Switzerland via Swiss Philanthropy Foundation, the network, which consists of reputable foundations and associations, receives about 5’000 donations per year, which amounts to more than 10 million euros. Honoured to chair the Transnational Giving Europe network in 2018, Swiss Philanthropy Foundation would like to host an event to reflect the Swiss spirit as seen from Geneva, by inviting its European partners to an evening event during which both Donors and Heads of public interest organisations can assess the value of European Philanthropy. In fact, is there is a better place to speak about philanthropy without borders than in this city which is the hub of global governance bound by a spirit and open-minded culture towards others, with an ethical footprint and know-how. Our position as a leading Swiss hosting foundation, reinforced by our membership in the European cross-border network, gives us the opportunity to meet the committed donors, namely, Swiss individuals, expats, entrepreneurs and institutions. The cosmopolitan spirit that animates Geneva, the foundation’s headquarters, shows us just how much everyone wants to contribute and maintain ties with their country of origin or share with others the opportunities they might have had. We hope that this evening, as well as the concrete explanations provided in this publication, will serve you in your philanthropic endeavours and inspire you to donate on a European scale.