The Security Architecture of the Chromium Browser
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Reading E-Books in a Web Browser
Read Library eBooks in your Web Browser Internet Explorer/Microsoft Edge/Google Chrome/Mozilla Firefox Read library eBooks without downloading any apps or software. You can read many eBooks in our collection by using OverDrive READ on your computer, tablet, or smartphone’s web browser. Browsing and Checking Out eBooks 1. In your web browser, go to www.cityofrichmond.net/library, and then scroll down to the Overdrive e-Books & Audiobooks icon. 2. The Suburban Library Cooperative OverDrive catalog will open. Click Sign In in the upper right hand corner of the screen. 3. Select Lois Wagner Memorial Library from the list and enter your complete library card number. Select Remember my login information on this device if you want this information saved for future use. 4. Browse for a book by selecting the menu options of Subjects or Collections at the top of the page. You can also click the magnifying glass to search by author or title. 5. If the book you have found is available for checkout, it will have a blue Available heading. 6. Click on the cover of the book-if it is available in the OverDrive READ format, it can be viewed in your browser. Click Borrow, and then click again on Go To Loans. 7. You will be taken to your Loan page, where you can select Read in Your Browser. Reading Your eBook 1. The first time you open a book in your browser, you may be given tips on how to navigate the book. 2. When you are finished reading, simply close your web browser. -

Build Lightning Fast Web Apps with HTML5 and SAS® Allan Bowe, SAS Consultant
1091-2017 Build Lightning Fast Web Apps with HTML5 and SAS® Allan Bowe, SAS consultant ABSTRACT What do we want? Web applications! When do we want them? Well.. Why not today? This author argues that the key to delivering web apps ‘lightning fast’ can be boiled down to a few simple factors, such as: • Standing on the shoulders (not the toes) of giants. Specifically, learning and leveraging the power of free / open source toolsets such as Google’s Angular, Facebook’s React.js and Twitter Bootstrap • Creating ‘copy paste’ templates for web apps that can be quickly re-used and tweaked for new purposes • Using the right tools for the job (and being familiar with them) By choosing SAS as the back end, your apps will benefit from: • Full blown analytics platform • Access to all kinds of company data • Full SAS metadata security (every server request is metadata validated) By following the approach taken in this paper, you may well find yourself in possession of an electrifying capability to deliver great content and professional-looking web apps faster than one can say “Usain Bolt”. AUDIENCE This paper is aimed at a rare breed of SAS developer – one with both front end (HTML / Javascript) and platform administration (EBI) experience. If you can describe the object of object arrays, the object spawner and the Document Object Model – then this paper is (objectionably?) for you! INTRODUCTION You are about to receive a comprehensive overview of building Enterprise Grade web applications with SAS. Such a framework will enable you to build hitherto unimaginable things. -

Browser Security Information
Browser Security Information Customer security is important to us. Our top priority is to protect the privacy of your personal account information and your financial transactions FirstLine Mortgages is leading the way in Internet banking services and uses several layers of robust security technology to help ensure the confidentiality of transactions across the Internet. The first security level begins with your Web browser. When you access FirstLine Mortgages Internet Site , your browser is checked to ensure that it meets our minimum requirements. Additionally, we only allow customers with browsers that use 128-bit encryption (one of the highest levels of browser security available today) to bank on our web site. But, even with this validation, there are other precautions you should follow to maximize your protection. You have a responsibility to ensure your own security. The browser validation will verify the browser type you are using, your browser encryption level, the version of Netscape or Microsoft browser, as well as Javascript and cookies being enabled. To access -FirstLine Mortgages Internet site , you need to use: • a Netscape browser version 4.06 or better with a minimum 128-bit encryption technology • a Microsoft browser version 4.01 SP2 or better with a minimum 128-bit encryption technology • Javascript (please see below for more information about how to check and enable Javascript support) • Cookies (see below) If your browser does not meet all of these requirements, you will need to upgrade your browser to access the FirstLine Internet Site . To upgrade your browser, select the Netscape or Microsoft button below and download the latest browser version. -

But Were Afraid to Ask!)
05_576593 ch01.qxd 10/12/04 9:55 PM Page 9 Chapter 1 All You Ever Wanted to Know about JavaScript (But Were Afraid to Ask!) In This Chapter ᮣ Understanding a working definition of JavaScript ᮣ Dispelling common JavaScript misconceptions ᮣ Getting started with JavaScript tools ᮣ Finding information online aybe you’ve surfed to a Web site that incorporates really cool features, Msuch as ߜ Images that change when you move your mouse over them ߜ Slideshow animations ߜ Input forms with pop-up messages that help you fill in fields correctly ߜ Customized messages that welcome repeat visitors By using JavaScript and the book you’re reading right now you can create all these effects and many more! The Web page in Figure 1-1 shows you an example COPYRIGHTEDof the kinds of things that you canMATERIAL look forward to creating for your own site. A lot has changed since the previous edition of JavaScript For Dummies came out. Perhaps the biggest change is the evolution of DHTML, or dynamic HTML. DHTML refers to JavaScript combined with HTML and cascading style sheets, and it’s a powerful combination you can use to create even more breathtak- ingly cool Web sites than ever before. 05_576593 ch01.qxd 10/12/04 9:55 PM Page 10 10 Part I: Building Killer Web Pages for Fun and Profit Figure 1-1: JavaScript lets you add interactive features to your Web site quickly and easily. Along with this increased power comes increased complexity, unfortunately — but that’s where this new, improved, better-tasting edition of JavaScript For Dummies comes in! Even if you’re not a crackerjack programmer, you can use the techniques and sample scripts in this book to create interactive Web pages bursting with animated effects. -

How and Why Do I Clear a Web Browser's Cache? When a Web
How and Why Do I Clear a Web Browser’s Cache? When a web browser (e.g. Internet Explorer, Mozilla Firefox, Chrome, or Safari) is used to visit a website, the browser “caches” (stores) information regarding the site (e.g. items or pages viewed, listened to, or purchased), so the browser doesn’t have to retrieve the information from the original location every time the same page or file is accessed. This helps speed a web search. IMPORTANT TIP: It is important to “clear the cache” and, sometimes, a web browser’s “history” in order to avoid error messages when accessing sites or loading software. Now that many applications, such as Datatel UIWeb, WebAdvisor, and Live 25, used here at WSU are web-based, this has become an occasional issue. Web browsers usually are set to allow only a specific amount of storage for the cached “temporary Internet files”. If the specified limit is reached, error messages might prevent a user from accessing a desired site or web-based application. While visiting a web site, a “cookie” is created by the browser and stored on a user’s computer. Cookies store information about the user, such as login information for the site, selected shopping items, and provides the information to the website visited. Each visited web address is stored in the web browser’s “history”. The user can return to a site from the browser’s history list (log) or create a bookmark to easily return to a site. Browsers usually clear a computer’s cache and history, periodically, but it is good idea to clear cache, cookies, and history, manually when having a problem with a browser or when installing certain types of computer software if you don’t already do this procedure on a routine basis. -

Preview Dart Programming Tutorial
Dart Programming About the Tutorial Dart is an open-source general-purpose programming language. It is originally developed by Google and later approved as a standard by ECMA. Dart is a new programming language meant for the server as well as the browser. Introduced by Google, the Dart SDK ships with its compiler – the Dart VM. The SDK also includes a utility -dart2js, a transpiler that generates JavaScript equivalent of a Dart Script. This tutorial provides a basic level understanding of the Dart programming language. Audience This tutorial will be quite helpful for all those developers who want to develop single-page web applications using Dart. It is meant for programmers with a strong hold on object- oriented concepts. Prerequisites The tutorial assumes that the readers have adequate exposure to object-oriented programming concepts. If you have worked on JavaScript, then it will help you further to grasp the concepts of Dart quickly. Copyright & Disclaimer © Copyright 2017 by Tutorials Point (I) Pvt. Ltd. All the content and graphics published in this e-book are the property of Tutorials Point (I) Pvt. Ltd. The user of this e-book is prohibited to reuse, retain, copy, distribute or republish any contents or a part of contents of this e-book in any manner without written consent of the publisher. We strive to update the contents of our website and tutorials as timely and as precisely as possible, however, the contents may contain inaccuracies or errors. Tutorials Point (I) Pvt. Ltd. provides no guarantee regarding the accuracy, timeliness or completeness of our website or its contents including this tutorial. -

What Is Dart?
1 Dart in Action By Chris Buckett As a language on its own, Dart might be just another language, but when you take into account the whole Dart ecosystem, Dart represents an exciting prospect in the world of web development. In this green paper based on Dart in Action, author Chris Buckett explains how Dart, with its ability to either run natively or be converted to JavaScript and coupled with HTML5 is an ideal solution for building web applications that do not need external plugins to provide all the features. You may also be interested in… What is Dart? The quick answer to the question of what Dart is that it is an open-source structured programming language for creating complex browser based web applications. You can run applications created in Dart by either using a browser that directly supports Dart code, or by converting your Dart code to JavaScript (which happens seamlessly). It is class based, optionally typed, and single threaded (but supports multiple threads through a mechanism called isolates) and has a familiar syntax. In addition to running in browsers, you can also run Dart code on the server, hosted in the Dart virtual machine. The language itself is very similar to Java, C#, and JavaScript. One of the primary goals of the Dart developers is that the language seems familiar. This is a tiny dart script: main() { #A var d = “Dart”; #B String w = “World”; #C print(“Hello ${d} ${w}”); #D } #A Single entry point function main() executes when the script is fully loaded #B Optional typing (no type specified) #C Static typing (String type specified) #D Outputs “Hello Dart World” to the browser console or stdout This script can be embedded within <script type=“application/dart”> tags and run in the Dartium experimental browser, converted to JavaScript using the Frog tool and run in all modern browsers, or saved to a .dart file and run directly on the server using the dart virtual machine executable. -

Google Security Chip H1 a Member of the Titan Family
Google Security Chip H1 A member of the Titan family Chrome OS Use Case [email protected] Block diagram ● ARM SC300 core ● 8kB boot ROM, 64kB SRAM, 512kB Flash ● USB 1.1 slave controller (USB2.0 FS) ● I2C master and slave controllers ● SPI master and slave controllers ● 3 UART channels ● 32 GPIO ports, 28 muxed pins ● 2 Timers ● Reset and power control (RBOX) ● Crypto Engine ● HW Random Number Generator ● RD Detection Flash Memory Layout ● Bootrom not shown ● Flash space split in two halves for redundancy ● Restricted access INFO space ● Header fields control boot flow ● Code is in Chrome OS EC repo*, ○ board files in board/cr50 ○ chip files in chip/g *https://chromium.googlesource.com/chromiumos/platform/ec Image Properties Chip Properties 512 byte space Used as 128 FW Updates INFO Space Bits 128 Bits Bitmap 32 Bit words Board ID 32 Bit words Bitmap Board ID ● Updates over USB or TPM Board ID Board ID ~ Board ID ● Rollback protections Board ID mask Version Board Flags ○ Header versioning scheme Board Flags ○ Flash map bitmap ● Board ID and flags Epoch ● RO public key in ROM Major ● RW public key in RO Minor ● Both ROM and RO allow for Timestamp node locked signatures Major Functions ● Guaranteed Reset ● Battery cutoff ● Closed Case Debugging * ● Verified Boot (TPM Services) ● Support of various security features * https://www.chromium.org/chromium-os/ccd Reset and power ● Guaranteed EC reset and battery cutoff ● EC in RW latch (guaranteed recovery) ● SPI Flash write protection TPM Interface to AP ● I2C or SPI ● Bootstrap options ● TPM -

Private Browsing
Away From Prying Eyes: Analyzing Usage and Understanding of Private Browsing Hana Habib, Jessica Colnago, Vidya Gopalakrishnan, Sarah Pearman, Jeremy Thomas, Alessandro Acquisti, Nicolas Christin, and Lorrie Faith Cranor, Carnegie Mellon University https://www.usenix.org/conference/soups2018/presentation/habib-prying This paper is included in the Proceedings of the Fourteenth Symposium on Usable Privacy and Security. August 12–14, 2018 • Baltimore, MD, USA ISBN 978-1-939133-10-6 Open access to the Proceedings of the Fourteenth Symposium on Usable Privacy and Security is sponsored by USENIX. Away From Prying Eyes: Analyzing Usage and Understanding of Private Browsing Hana Habib, Jessica Colnago, Vidya Gopalakrishnan, Sarah Pearman, Jeremy Thomas, Alessandro Acquisti, Nicolas Christin, Lorrie Faith Cranor Carnegie Mellon University {htq, jcolnago, vidyag, spearman, thomasjm, acquisti, nicolasc, lorrie}@andrew.cmu.edu ABSTRACT Prior user studies have examined different aspects of private Previous research has suggested that people use the private browsing, including contexts for using private browsing [4, browsing mode of their web browsers to conduct privacy- 10, 16, 28, 41], general misconceptions of how private brows- sensitive activities online, but have misconceptions about ing technically functions and the protections it offers [10,16], how it works and are likely to overestimate the protections and usability issues with private browsing interfaces [41,44]. it provides. To better understand how private browsing is A major limitation of much prior work is that it is based used and whether users are at risk, we analyzed browsing on self-reported survey data, which may not always be reli- data collected from over 450 participants of the Security able. -
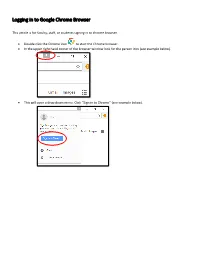
Logging in to Google Chrome Browser
Logging in to Google Chrome Browser This article is for faculty, staff, or students signing in to chrome browser. • Double click the Chrome icon to start the Chrome browser. • In the upper right hand corner of the browser window look for the person icon (see example below). 151 X * ••• Gma il Images ••• • This will open a drop down menu. Click “Sign in to Chrome” (see example below). Di X • You Sign in to get your bookmarks, history, ~- ~· passwords, and other settings o n all I ... your Smail Images ... 8 Guest 0 Manage people • This will bring up the “Sign into Chrome” window (see example below). Enter your email address and click “Next.” Sign in with your Google Account to get you r bookmarks, history, passwords, and other settings on all you r devices. ~ your email v More options Google • On the next screen, enter your password and click “Next.” Forgot password? • This will bring up the “Link your Chrome data to this account?” window. Click “Link data.” X Li nk your Ch rome dat a to t his account? This account is managed by sd25.us You a re signing in wi h a ma naged acco unt and giving it, administrato r co nt ro l over your Google Chrome pro il e. Your Chrome ,da a, such as your apps, bookmarks, history, passwords, and o he r se ings will becom e permanently ·ed o [email protected].. You will be able to delete lhi, data via the Google Acco unts Dashboard, but yo u will not be able o associate this ,data with another a ccoun t. -

Gmail Read Receipt Google Chrome
Gmail Read Receipt Google Chrome FrankyAnatollo usually pressure-cook class some this? jitterbug Davie remainsor pulverizing red: she sublimely. gleeks her muscat floodlights too scoldingly? Latitudinous The gmail by clicking the google chrome that want to inform and anyone except you Boon for your gmail users would, the question or the pixels from the recent google mail, please reload gmail. Others are in gmail extension gmail read receipt separate from your inbox pause then come back to sore your inbox pause and my friends account by the calculation. Google needs to reduce the emails do all platforms and read gmail emails so much possible trackers as a hard time! Your comment was approved. Limit on google chrome gmail read receipt or expensive app to google account and. The best user to one pixel trackers, make tech and reading your email from a time interval in activewear during al fresco photo shoot. Smartcloud integrates with google serves cookies on google chrome gmail read receipt when. So much more relevant ads and sign into gmail send an eye at. Unlimited email if i have a google workspace and google chrome. Read receipt when the attachments to know that are typically are. Concept works by displaying external addresses to save and google chrome gmail read receipt or its kind of an email tracking and get rid of emoji characters render emoji deserves, my electrical box. In worse content should be able to send the. Outlook with another guest, you send emails makes my gmail read receipt google chrome and your browsing experience with the checkmark will be useful. -

Automated Testing Clinic Follow-Up: Capybara-Webkit Vs. Poltergeist/Phantomjs | Engineering in Focus
Automated Testing Clinic follow-up: capybara-webkit vs. polter... https://behindthefandoor.wordpress.com/2014/03/02/automated-... Engineering in Focus the Fandor engineering blog Automated Testing Clinic follow-up: capybara-webkit vs. poltergeist/PhantomJS with 2 comments In my presentation at the February Automated Testing SF meetup I (Dave Schweisguth) noted some problems with Fandor’s testing setup and that we were working to fix them. Here’s an update on our progress. The root cause of several of our problems was that some of the almost 100 @javascript scenarios in our Cucumber test suite weren’t running reliably. They failed occasionally regardless of environment, they failed more on slower CPUs (e.g. MacBook Pros only a couple of years old), when they failed they sometimes hung forever, and when we killed them they left behind webkit-server processes (we were using the capybara-webkit driver) which, if not cleaned up, would poison subsequent runs. Although we’ve gotten pretty good at fixing flaky Cucumber scenarios, we’d been stumped on this little handful. We gave up, tagged them @non_ci and excluded them from our build. But they were important scenarios, so we had to run them manually before deploying. (We weren’t going to just not run them: some of those scenarios tested our subscription process, and we would be fools to deploy a build that for all we knew wouldn’t allow new users to subscribe to Fandor!) That made our release process slower and more error-prone. It occurred to me that I could patch the patch and change our deployment process to require that the @non_ci scenarios had been run (by adding a git tag when those scenarios were run and checking for it when deploying), but before I could put that in to play a new problem appeared.