Noncombatant Persons
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

The Relationship Between International Humanitarian Law and the International Criminal Tribunals Hortensia D
Volume 88 Number 861 March 2006 The relationship between international humanitarian law and the international criminal tribunals Hortensia D. T. Gutierrez Posse Hortensia D. T. Gutierrez Posse is Professor of Public International Law, University of Buenos Aires Abstract International humanitarian law is the branch of customary and treaty-based international positive law whose purposes are to limit the methods and means of warfare and to protect the victims of armed conflicts. Grave breaches of its rules constitute war crimes for which individuals may be held directly accountable and which it is up to sovereign states to prosecute. However, should a state not wish to, or not be in a position to, prosecute, the crimes can be tried by international criminal tribunals instituted by treaty or by binding decision of the United Nations Security Council. This brief description of the current legal and political situation reflects the state of the law at the dawn of the twenty-first century. It does not, however, describe the work of a single day or the fruit of a single endeavour. Quite the contrary, it is the outcome of the international community’s growing awareness, in the face of the horrors of war and the indescribable suffering inflicted on humanity throughout the ages, that there must be limits to violence and that those limits must be established by the law and those responsible punished so as to discourage future perpetrators from exceeding them. Short historical overview International humanitarian law has played a decisive role in this development, as both the laws and customs of war and the rules for the protection of victims fall 65 H. -

Law of Armed Conflict
Lesson 1 THE LAW OF ARMED CONFLICT Basic knowledge International Committee of the Red Cross Unit for Relations with Armed and Security Forces 19 Avenue de la Paix 1202 Geneva, Switzerland T +41 22 734 60 01 F +41 22 733 20 57 E-mail: [email protected] www.icrc.org Original: English – June 2002 INTRODUCTION TO THE LAW OF ARMED CONFLICT BASIC KNOWLEDGE LESSON 1 [ Slide 2] AIM [ Slide 3] The aim of this lesson is to introduce the topic to the class, covering the following main points: 1. Background: setting the scene. 2. The need for compliance. 3. How the law evolved and its main components. 4. When does the law apply? 5. The basic principles of the law. INTRODUCTION TO THE LAW OF ARMED CONFLICT 1. BACKGROUND: SETTING THE SCENE Today we begin a series of lectures on the law of armed conflict, which is also known as the law of war, international humanitarian law, or simply IHL. To begin, I’d like to take a guess at what you’re thinking right now. Some of you are probably thinking that this is an ideal opportunity to catch up on some well-earned rest. “Thank goodness I’m not on the assault course or on manoeuvres. This is absolutely marvellous. I can switch off and let this instructor ramble on for 45 minutes. I know all about the Geneva Conventions anyway – the law is part of my culture and our military traditions. I really don't need to listen to all this legal ‘mumbo jumbo’.” The more sceptical and cynical among you might well be thinking along the lines of a very famous orator of ancient Rome – Cicero. -

Combatant Status and Computer Network Attack
Combatant Status and Computer Network Attack * SEAN WATTS Introduction .......................................................................................... 392 I. State Capacity for Computer Network Attacks ......................... 397 A. Anatomy of a Computer Network Attack ....................... 399 1. CNA Intelligence Operations ............................... 399 2. CNA Acquisition and Weapon Design ................. 401 3. CNA Execution .................................................... 403 B. State Computer Network Attack Capabilites and Staffing ............................................................................ 405 C. United States’ Government Organization for Computer Network Attack .............................................. 407 II. The Geneva Tradition and Combatant Immunity ...................... 411 A. The “Current” Legal Framework..................................... 412 1. Civilian Status ...................................................... 414 2. Combatant Status .................................................. 415 3. Legal Implications of Status ................................. 420 B. Existing Legal Assessments and Scholarship.................. 424 C. Implications for Existing Computer Network Attack Organization .................................................................... 427 III. Departing from the Geneva Combatant Status Regime ............ 430 A. Interpretive Considerations ............................................. 431 * Assistant Professor, Creighton University Law School; Professor, -
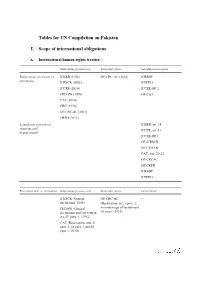
Tables for UN Compilation on Pakistan I. Scope of International
Tables for UN Compilation on Pakistan I. Scope of international obligations1 A. International human rights treaties2 Status during previous cycle Action after review Not ratified/not accepted Ratification, accession or ICERD (1966) OP -CRC-AC (2016) ICRMW succession ICESCR (2008) ICPPED ICCPR (2010) ICCPR-OP 2 CEDAW (1996) OP-CAT CAT (2010) CRC (1990) OP-CRC-SC (2011) CRPD (2011) Complaints procedures, – – ICERD, art. 14 inquiries and ICCPR, art. 41 urgent action3 ICCPR-OP 1 OP-ICESCR OP-CEDAW CAT, arts. 20-22 OP-CRC-IC OP-CRPD ICRMW ICPPED Reservations and / or declarations Status during previous cycle Action after review Current Status ICESCR (General OP -CRC-AC – declaration, 2008) (Declaration, art. 3 para. 2, CEDAW (General minimum age of recruitment declaration and reservation 16 years, (2016) art. 29, para. 1, 1996) CAT (Reservation, arts. 8 para. 2, 28 para. 1 and 30 para. 1. 2010) ICCPR (General reservation, 2008) B. Other main relevant international instruments Status during previous cycle Action after review Not ratified Ratification, accession or Convention on the – Rome Statute of the succession Prevention and Punishment International Criminal Court of the Crime of Genocide Geneva Conventions of 12 Palermo Protocol5 August 19494 Additional Protocols I, II and III to the 1949 Geneva Conventions6 ILO fundamental – Conventions on refugees conventions7 and stateless persons8 – – Convention against Discrimination in Education – – ILO Conventions Nos. 169 and 1899 II. Cooperation with human rights mechanisms and bodies A. Cooperation -

Noncombatant Immunity and War-Profiteering
In Oxford Handbook of Ethics of War / Published 2017 / doi:10.1093/oxfordhb/9780199943418.001.0001 Noncombatant Immunity and War-Profiteering Saba Bazargan Department of Philosophy UC San Diego Abstract The principle of noncombatant immunity prohibits warring parties from intentionally targeting noncombatants. I explicate the moral version of this view and its criticisms by reductive individualists; they argue that certain civilians on the unjust side are morally liable to be lethally targeted to forestall substantial contributions to that war. I then argue that reductivists are mistaken in thinking that causally contributing to an unjust war is a necessary condition for moral liability. Certain noncontributing civilians—notably, war-profiteers— can be morally liable to be lethally targeted. Thus, the principle of noncombatant immunity is mistaken as a moral (though not necessarily as a legal) doctrine, not just because some civilians contribute substantially, but because some unjustly enriched civilians culpably fail to discharge their restitutionary duties to those whose victimization made the unjust enrichment possible. Consequently, the moral criterion for lethal liability in war is even broader than reductive individualists have argued. 1 In Oxford Handbook of Ethics of War / Published 2017 / doi:10.1093/oxfordhb/9780199943418.001.0001 1. Background 1.1. Noncombatant Immunity and the Combatant’s Privilege in International Law In Article 155 of what came to be known as the ‘Lieber Code’, written in 1866, Francis Lieber wrote ‘[a]ll enemies in regular war are divided into two general classes—that is to say, into combatants and noncombatants’. As a legal matter, this distinction does not map perfectly onto the distinction between members and nonmembers of an armed force. -

The Geneva Conventions and Public International
Volume 91 Number 875 September 2009 REPORTS AND DOCUMENTS The Geneva Conventions and Public International Law British Foreign and Commonwealth Office Conference commemorating the 60th Anniversary of the 1949 Geneva Conventions, London, 9 July 2009 Address by Theodor Meron, Judge and former President of the International Criminal Tribunal for the former Yugoslavia, Professor of International Law and holder of the Charles L. Denison Chair at New York University Law School With sixty years of hindsight, it seems particularly appropriate to reflect on the trajectory of international humanitarian law (IHL) as shaped by the 1949 Geneva Conventions. The near universal acceptance of the Conventions and their secure integration into the international system can sometimes lead us to underestimate the significance of their impact. It is this transformative impact on public inter- national law which will be the focus of this note. To start, I will briefly review the historical context from which the 1949 Conventions materialized. Calamitous events and atrocities have always driven the development of IHL. In 1863, the American Civil War gave rise to the Lieber Code. This ultimately gave birth to the branch of IHL commonly known as the Hague Law, which governs the conduct of hostilities. One hundred and fifty years ago, the battle of Solferino – immortalized in Henry Dunant’s moving memoir of suffering and bloodshed – inspired the Red Cross Movement. Thence began the other branch of IHL, the Geneva Law, which – starting with the first Geneva Convention in 1864 – has provided for the protection of victims of war, the sick, the wounded, prisoners and civilians. -

Rome Statute of the International Criminal Court
Rome Statute of the International Criminal Court The text of the Rome Statute reproduced herein was originally circulated as document A/CONF.183/9 of 17 July 1998 and corrected by procès-verbaux of 10 November 1998, 12 July 1999, 30 November 1999, 8 May 2000, 17 January 2001 and 16 January 2002. The amendments to article 8 reproduce the text contained in depositary notification C.N.651.2010 Treaties-6, while the amendments regarding articles 8 bis, 15 bis and 15 ter replicate the text contained in depositary notification C.N.651.2010 Treaties-8; both depositary communications are dated 29 November 2010. The table of contents is not part of the text of the Rome Statute adopted by the United Nations Diplomatic Conference of Plenipotentiaries on the Establishment of an International Criminal Court on 17 July 1998. It has been included in this publication for ease of reference. Done at Rome on 17 July 1998, in force on 1 July 2002, United Nations, Treaty Series, vol. 2187, No. 38544, Depositary: Secretary-General of the United Nations, http://treaties.un.org. Rome Statute of the International Criminal Court Published by the International Criminal Court ISBN No. 92-9227-232-2 ICC-PIOS-LT-03-002/15_Eng Copyright © International Criminal Court 2011 All rights reserved International Criminal Court | Po Box 19519 | 2500 CM | The Hague | The Netherlands | www.icc-cpi.int Rome Statute of the International Criminal Court Table of Contents PREAMBLE 1 PART 1. ESTABLISHMENT OF THE COURT 2 Article 1 The Court 2 Article 2 Relationship of the Court with the United Nations 2 Article 3 Seat of the Court 2 Article 4 Legal status and powers of the Court 2 PART 2. -

Geneva Conventions of 12 August 1949
THE GENEVA CONVENTIONS OF 12 AUGUST 1949 AUGUST 12 OF CONVENTIONS THE GENEVA THE GENEVA CONVENTIONS OF 12 AUGUST 1949 0173/002 05.2010 10,000 ICRC Mission The International Committee of the Red Cross (ICRC) is an impartial, neutral and independent organization whose exclusively humanitarian mission is to protect the lives and dignity of victims of armed conflict and other situations of violence and to provide them with assistance. The ICRC also endeavours to prevent suffering by promoting and strengthening humanitarian law and universal humanitarian principles. Established in 1863, the ICRC is at the origin of the Geneva Conventions and the International Red Cross and Red Crescent Movement. It directs and coordinates the international activities conducted by the Movement in armed conflicts and other situations of violence. THE GENEVA CONVENTIONS OF 12 AUGUST 1949 THE GENEVA CONVENTIONS OF 1949 1 Contents Preliminary remarks .......................................................................................................... 19 GENEVA CONVENTION FOR THE AMELIORATION OF THE CONDITION OF THE WOUNDED AND SICK IN ARMED FORCES IN THE FIELD OF 12 AUGUST 1949 CHAPTER I General Provisions ....................................................................................................... 35 Article 1 Respect for the Convention ..................................................................... 35 Article 2 Application of the Convention ................................................................ 35 Article 3 Conflicts not of an international -

How the United States Use of Double-Tap Drone Strikes Violates IHL Principles of Distinction and Proportionality
Seton Hall University eRepository @ Seton Hall Law School Student Scholarship Seton Hall Law 2021 Transparency into Darkness: How the United States Use of Double-Tap Drone Strikes Violates IHL Principles of Distinction and Proportionality John Bonino Follow this and additional works at: https://scholarship.shu.edu/student_scholarship Part of the Law Commons Recommended Citation Bonino, John, "Transparency into Darkness: How the United States Use of Double-Tap Drone Strikes Violates IHL Principles of Distinction and Proportionality" (2021). Law School Student Scholarship. 1125. https://scholarship.shu.edu/student_scholarship/1125 INTRODUCTION .......................................................................................................................... 1 I. PRELIMINARY STATEMENT ............................................................................................. 2 II. PRINCIPLE OF DISTINCTION............................................................................................. 4 A. Distinguishing Combatants and Non-combatants ................................................................ 6 i. Medical Personnel ............................................................................................................ 7 ii. Protecting Civilians .......................................................................................................... 9 B. Overcoming the Mens Rea Requirement ........................................................................... 11 III. MILITARY NECESSITY AND THE IHL ...................................................................... -

Fm 6-27 Mctp 11-10C the Commander's Handbook on the Law of Land Warfare
FM 6-27 MCTP 11-10C THE COMMANDER'S HANDBOOK ON THE LAW OF LAND WARFARE AUGUST 2019 DISTRIBUTION RESTRICTION: Approved for public release; distribution is unlimited. This publication supersedes FM 27-10/MCTP 11-10C, dated 18 July 1956. HEADQUARTERS, DEPARTMENT OF THE ARMY HEADQUARTERS, UNITED STATES MARINE CORPS Foreword The lessons of protracted conflict confirm that adherence to the law of armed conflict (LOAC) by the land forces, both in intern ational and non-international armed conflict, must serve as the standard that we train to and apply across the entire range of military operations. Adhering to LOAC enhances the legitimacy of our operations and supports the moral framework of our armed forces. We have learned th at we deviate from these norms to our detriment and risk undercutting both domesti c and international support for our operations. LOAC has been and remains a vital guide for all military operations conducted by the U.S. Governm ent. This fi eld manual provides a general description of the law of land warfare for Soldiers and Marines, delineated as statements of doctrine and practice, to gui de the land forces in conducting di sci plined military operations in accordance with the rule of law. The Department of Defense Law of War Manual (June 20 15, updated December 2016) is the authoritative statement on the law of war for the Department of Defense. In the event of a conflict or discrepancy regarding the legal standards addressed in this publication and th e DOD Law of War Manual, the latter takes precedence. -

Al-Qaeda & Taliban Unlawful Combatant
AL-QAEDA & TALIBAN UNLAWFUL COMBATANT DETAINEES,..., 55 A.F. L. Rev. 1 55 A.F. L. Rev. 1 Air Force Law Review 2004 Article AL-QAEDA & TALIBAN UNLAWFUL COMBATANT DETAINEES, UNLAWFUL BELLIGERENCY, AND THE INTERNATIONAL LAWS OF ARMED CONFLICT Lieutenant Colonel (s) Joseph P. “Dutch” Bialkea1 Copyright © 2004 by Lieutenant Colonel (s) Joseph P. “Dutch” Bialke I. INTRODUCTION International Obligations & Responsibilities and the International Rule of Law The United States (U.S.) is currently detaining several hundred al-Qaeda and Taliban unlawful enemy combatants from more than 40 countries at a multi-million dollar maximum-security detention facility at the U.S. Naval Base in Guantanamo Bay, Cuba. These enemy detainees were captured while engaged in hostilities against the U.S. and its allies during the post-September 11, 2001 international armed conflict centered primarily in Afghanistan. The conflict now involves an ongoing concerted international campaign in collective self-defense against a common stateless enemy dispersed throughout the world. Domestic and international human rights organizations and other groups have criticized the U.S.,1 arguing that al-Qaeda and Taliban detainees in Cuba should be granted Geneva Convention III prisoner of war (POW)2status. They contend broadly that pursuant to the international laws of armed conflict (LOAC), combatants captured during armed conflict must be treated equally and conferred POWstatus. However, no such blanket obligation exists in international law. There is no legal or moral equivalence in LOAC between lawful combatants and unlawful combatants, or between lawful belligerency *2 and unlawful belligerency (also referred to as lawful combatantry and unlawful combatantry). -

Understanding Cyber Collateral Damage
Understanding Cyber Collateral Damage Sasha Romanosky* & Zachary Goldman** INTRODUCTION In conventional (kinetic) U.S. warfare, there exists a standard methodology for identifying and assessing collateral damage (i.e. accidental damage to civilian targets). Indeed, the U.S. Department of Defense (DoD) relies on a governing document that defines the policy regarding unlawful military targets (no-strike targets), and methods for estimating collateral damage from kinetic military operations.1 The definitions in this document are clear, and the harms against which it aims to protect are tangible because they relate to persons and property. The munitions in the military’s arsenal are defined and well-known, and their properties—blast radius, amount of force delivered, and the like—are well understood. While accidents of course do occur, the anticipated effects of a kinetic operation (collateral or otherwise), are generally straightforward to anticipate, assess, and manage. However, given the interconnectedness of cyber and cyber-physical systems, direct, indirect, and collateral effects can be much more difficult to predict, rendering ineffective traditional approaches to collateral damage estimation (CDE). Indeed, even the notion of clearly defining and considering “damage” within the cyber realm is challenging. For example, how does one estimate harms resulting from an outage of network connectivity caused when an attacker exploits a software vulnerability? How can one evaluate and weigh the collateral impact of a cyber intervention on incommensurable values, such as exposing the IP addresses of anonymous Tor users in order to arrest child pornographers, against international comity concerns that might be implicated by remotely searching foreign computers in contravention of traditional diplo- matic and law enforcement norms? We consider two main questions in this Article.