Xilinx XAPP1137 Linux Operating System Software Debugging
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Kernel Panic
Kernel Panic Connect, Inc. 1701 Quincy Avenue, Suites 5 & 6, Naperville, IL 60540 Ph: (630) 717-7200 Fax: (630) 717-7243 www.connectrf.com Table of Contents SCO Kernel Patches for Panics on Pentium Systems…………………………………..1 Kernel Panic Debug Methodologies..............................................................................3 SCO Kernel Patches for Panics on Pentium Systems SCO Kernel Patches for Panics on Pentium Systems Web Links http://www.sco.com/cgi-bin/ssl_reference?104530 http://www.sco.com/cgi-bin/ssl_reference?105532 Pentium System Panics with Trap Type 6; no dump is saved to /dev/swap. Keywords panic trap kernel invalid opcode pentium querytlb querytbl 386 mpx unix v4 dump swap double type6 no patch /etc/conf/pack.d/kernel/locore.o image locore Release SCO UNIX System V/386 Release 3.2 Operating System Version 4.0, 4.1 and 4.2 SCO Open Desktop Release 2.0 and 3.0 SCO Open Server System Release 2.0 and 3.0 Problem My system panics with a Trap Type 6, but no memory dump gets written. Cause There is a flaw in the kernel querytlb() routine that allows the Pentium to execute a 386-specific instruction which causes it to panic with an invalid opcode. querytlb() is only called when your system is panicking. The fault causes the system to double- panic and it thus fails to write a panic dump to disk. This means that the panic trap type 6 is concealing another type of panic which will show itself after the following patch has been applied. Solution You can apply the following patch, as root, to: /etc/conf/pack.d/kernel/locore.o Use the procedure that follows. -

Ben Livshits 1 Basic Instrumentation
Runtime monitoring CO444H Ben Livshits 1 Basic Instrumentation • Insert additional code into the program • This code is designed to record important events as they occur at runtime • Some examples • A particular function is being hit or a statement is being hit • This leads to function-level or line-level coverage • Each allocation to measure overall memory allocation 2 Levels of Instrumentation • Native code • Instrument machine code • Tools like LLVM are often used for rewriting • Bytecode • Common for languages such as Java and C# • A variety of tools are available for each bytecode format • JoeQ is in this category as well, although it’s a lot more general • Source code • Common for languages like JavaScript • Often the easiest option – parse the code and add more statements 3 Runtime Code Monitoring •Three major examples of monitoring • Purify/Valgrind • Detecting data races • Detecting memory leaks 4 5 Memory Error Detection Purify • C and C++ are not type-safe • The type system and the runtime fail to enforce type safety • What are some of the examples? • Possible to read and write outside of your intended data structures • Write beyond loop bounds • Or object bounds • Or overwrite the code pointer, etc. 6 Track Each Byte of Memory • Three states for every byte of tracker memory • Unallocated: cannot be read or written • Allocated but not initialized: cannot be read • Allocated and initialized: all operations are allowed 7 Instrumentation for Purify • Check the state of each byte at every access • Binary instrumentation: • Add -

Memory Leak Or Dangling Pointer
Modern C++ for Computer Vision and Image Processing Igor Bogoslavskyi Outline Using pointers Pointers are polymorphic Pointer “this” Using const with pointers Stack and Heap Memory leaks and dangling pointers Memory leak Dangling pointer RAII 2 Using pointers in real world Using pointers for classes Pointers can point to objects of custom classes: 1 std::vector<int> vector_int; 2 std::vector<int >* vec_ptr = &vector_int; 3 MyClass obj; 4 MyClass* obj_ptr = &obj; Call object functions from pointer with -> 1 MyClass obj; 2 obj.MyFunc(); 3 MyClass* obj_ptr = &obj; 4 obj_ptr->MyFunc(); obj->Func() (*obj).Func() ↔ 4 Pointers are polymorphic Pointers are just like references, but have additional useful properties: Can be reassigned Can point to ‘‘nothing’’ (nullptr) Can be stored in a vector or an array Use pointers for polymorphism 1 Derived derived; 2 Base* ptr = &derived; Example: for implementing strategy store a pointer to the strategy interface and initialize it with nullptr and check if it is set before calling its methods 5 1 #include <iostream > 2 #include <vector > 3 using std::cout; 4 struct AbstractShape { 5 virtual void Print() const = 0; 6 }; 7 struct Square : public AbstractShape { 8 void Print() const override { cout << "Square\n";} 9 }; 10 struct Triangle : public AbstractShape { 11 void Print() const override { cout << "Triangle\n";} 12 }; 13 int main() { 14 std::vector<AbstractShape*> shapes; 15 Square square; 16 Triangle triangle; 17 shapes.push_back(&square); 18 shapes.push_back(&triangle); 19 for (const auto* shape : shapes) { shape->Print(); } 20 return 0; 21 } 6 this pointer Every object of a class or a struct holds a pointer to itself This pointer is called this Allows the objects to: Return a reference to themselves: return *this; Create copies of themselves within a function Explicitly show that a member belongs to the current object: this->x(); 7 Using const with pointers Pointers can point to a const variable: 1 // Cannot change value , can reassign pointer. -

Effective and Efficient Memory Protection Using Dynamic Tainting
1 Effective and Efficient Memory Protection Using Dynamic Tainting Ioannis Doudalis, Student Member, IEEE, James Clause, Member, IEEE, Guru Venkataramani, Member, IEEE, Milos Prvulovic, Senior Member, IEEE, and Alessandro Orso, Member, IEEE, ! Abstract—Programs written in languages allowing direct access to pointer p or a pointer derived from p and 2) if the access memory through pointers often contain memory-related faults, which occurs during the interval when p is valid, (i.e. between the cause non-deterministic failures and security vulnerabilities. We present allocation and deallocation of m). All other accesses to m are a new dynamic tainting technique to detect illegal memory accesses. illegal memory accesses (IMAs), where a pointer is used to When memory is allocated, at runtime, we taint both the memory and the corresponding pointer using the same taint mark. Taint marks access memory outside the bounds of the memory area with are then propagated and checked every time a memory address m which it was originally associated, or outside the time period is accessed through a pointer p; if the associated taint marks differ, during which the pointer is valid. an illegal access is reported. To allow always-on checking using a IMAs are especially relevant for several reasons. First, they low-overhead, hardware-assisted implementation, we make several key are caused by typical programming errors, such as array-out- technical decisions. We use a configurable, low number of reusable taint of-bounds accesses and stale pointer dereferences, and are thus marks instead of a unique mark for each allocated area of memory, reducing the performance overhead without losing the ability to target widespread and common. -
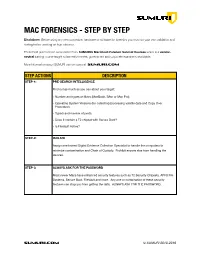
SUMURI Macintosh Forensics Best Practices
! MAC FORENSICS - STEP BY STEP Disclaimer: Before using any new procedure, hardware or software for forensics you must do your own validation and testing before working on true evidence. These best practices are summarized from SUMURI’s Macintosh Forensic Survival Courses which is a vendor- neutral training course taught to law enforcement, government and corporate examiners worldwide. More information about SUMURI can be found at SUMURI.com STEP ACTIONS DESCRIPTION STEP-1: PRE-SEARCH INTELLIGENCE Find out as much as you can about your target: • Number and types of Macs (MacBook, iMac or Mac Pro). • Operating System Versions (for collecting/processing volatile data and Copy Over Procedure). • Type/s and number of ports. • Does it contain a T2 chipset with Secure Boot? • Is FileVault Active? STEP-2: ISOLATE Assign one trained Digital Evidence Collection Specialist to handle the computers to minimize contamination and Chain of Custody. Prohibit anyone else from handling the devices. STEP-3: ALWAYS ASK FOR THE PASSWORD Most newer Macs have enhanced security features such as T2 Security Chipsets, APFS File Systems, Secure Boot, FileVault and more. Any one or combination of these security features can stop you from getting the data. ALWAYS ASK FOR THE PASSWORD. SUMURI.com © SUMURI 2010-2019 ! STEP ACTIONS DESCRIPTION STEP-4: IF COMPUTER IS ON - SCREEN SAVER PASSWORD ACTIVE Options are: • Ask for the Password - Confirm password and proceed to Step-6. • Restart to Image RAM - Connect a RAM Imaging Utility to the Mac such as RECON IMAGER. Conduct a soft-restart (do not power off if possible and image the RAM). -

Tutorial on Debugging, Memory Leaks and Profiling
High Performance Computing for Science and Engineering I Tutorial on debugging, memory leaks and profiling Michalis Chatzimanolakis Computational Science & Engineering Laboratory OUTLINE - Approaches to debug your code •Using assertions •Using a debugger •Memory sanitation •Using a profiler Assertions in C++ An assertion is a logical statement that will cause your code to abort execution, if it is false. Example: Assertions can affect performance, Assertions perform checks that make sure that as they are essentially ‘if’ statements. some conditions are met. However, it is good practice to add assertions in a code. A simple compilation flag can ignore all assertions, so it is generally a good idea to use them. It is useful to combine assertions with the std functions isinf and isnan They can also be used with screen output. Compiler warnings Compiler warnings are compilation flags that you can (should) add to your Makefiles. Enabling warnings makes the compiler check for several issues in your source file, such as: • Forgetting to initialize a variable • Not using a declared variable • Using a function before declaring it • Having screen/file output with incorrect format (for example, treating doubles as integers) Generally, you should add warnings and try to fix all of them, before proceeding with further debugging your code. Note that different compilers may produce different warnings. The most common compiler warning flags are listed below: -Wall : enables several construction/declaration warnings -Wextra : more warnings than Wall including warnings for unused variables -Werror: will treat all warnings as errors -Wpedantic: warnings related to the use of non standard C++ extensions Using a debugger What is a debugger? A debugger is a program. -

Linux Kernal II 9.1 Architecture
Page 1 of 7 Linux Kernal II 9.1 Architecture: The Linux kernel is a Unix-like operating system kernel used by a variety of operating systems based on it, which are usually in the form of Linux distributions. The Linux kernel is a prominent example of free and open source software. Programming language The Linux kernel is written in the version of the C programming language supported by GCC (which has introduced a number of extensions and changes to standard C), together with a number of short sections of code written in the assembly language (in GCC's "AT&T-style" syntax) of the target architecture. Because of the extensions to C it supports, GCC was for a long time the only compiler capable of correctly building the Linux kernel. Compiler compatibility GCC is the default compiler for the Linux kernel source. In 2004, Intel claimed to have modified the kernel so that its C compiler also was capable of compiling it. There was another such reported success in 2009 with a modified 2.6.22 version of the kernel. Since 2010, effort has been underway to build the Linux kernel with Clang, an alternative compiler for the C language; as of 12 April 2014, the official kernel could almost be compiled by Clang. The project dedicated to this effort is named LLVMLinxu after the LLVM compiler infrastructure upon which Clang is built. LLVMLinux does not aim to fork either the Linux kernel or the LLVM, therefore it is a meta-project composed of patches that are eventually submitted to the upstream projects. -

Oracle VM Virtualbox User Manual
Oracle VM VirtualBox R User Manual Version 5.0.16 c 2004-2016 Oracle Corporation http://www.virtualbox.org Contents 1 First steps 11 1.1 Why is virtualization useful?............................. 12 1.2 Some terminology................................... 12 1.3 Features overview................................... 13 1.4 Supported host operating systems.......................... 15 1.5 Installing VirtualBox and extension packs...................... 16 1.6 Starting VirtualBox.................................. 17 1.7 Creating your first virtual machine......................... 18 1.8 Running your virtual machine............................ 21 1.8.1 Starting a new VM for the first time.................... 21 1.8.2 Capturing and releasing keyboard and mouse.............. 22 1.8.3 Typing special characters.......................... 23 1.8.4 Changing removable media......................... 24 1.8.5 Resizing the machine’s window...................... 24 1.8.6 Saving the state of the machine...................... 25 1.9 Using VM groups................................... 26 1.10 Snapshots....................................... 26 1.10.1 Taking, restoring and deleting snapshots................. 27 1.10.2 Snapshot contents.............................. 28 1.11 Virtual machine configuration............................ 29 1.12 Removing virtual machines.............................. 30 1.13 Cloning virtual machines............................... 30 1.14 Importing and exporting virtual machines..................... 31 1.15 Global Settings................................... -

Memory Vulnerability Diagnosis for Binary Program
ITM Web of Conferences 7 03004 , (2016) DOI: 10.1051/itmconf/20160703004 ITA 2016 Memory Vulnerability Diagnosis for Binary Program Feng-Yi TANG, Chao FENG and Chao-Jing TANG College of Electronic Science and Engineering National University of Defense Technology Changsha, China Abstract. Vulnerability diagnosis is important for program security analysis. It is a further step to understand the vulnerability after it is detected, as well as a preparatory step for vulnerability repair or exploitation. This paper mainly analyses the inner theories of major memory vulnerabilities and the threats of them. And then suggests some methods to diagnose several types of memory vulnerabilities for the binary programs, which is a difficult task due to the lack of source code. The diagnosis methods target at buffer overflow, use after free (UAF) and format string vulnerabilities. We carried out some tests on the Linux platform to validate the effectiveness of the diagnosis methods. It is proved that the methods can judge the type of the vulnerability given a binary program. 1 Introduction (or both) the memory area. These headers can contain some information like size, used or not, and etc. Memory vulnerabilities are difficult to detect and diagnose Therefore, we can monitor the allocator so as to especially for those do not crash the program. Due to its determine the base address and the size of the allocation importance, vulnerability diagnosis problem has been areas. Then, check all STORE and LOAD accesses in intensively studied. Researchers have proposed different memory to see which one is outside the allocated area. techniques to diagnose memory vulnerabilities. -

A Statistical Approach for Identifying Memory Leaks in Cloud Applications
A STATISTICAL APPROACH FOR IDENTIFYING MEMORY LEAKS IN CLOUD APPLICATIONS Vladimir Sorˇ and Satish Narayana Srirama Institute of Computer Science, University of Tartu, J. Liivi 2, Tartu, Estonia Keywords: Troubleshooting, JavaTM Virtual Machine, Byte code instrumentation, Cloud computing, Tools. Abstract: This position paper describes the attempt to automate the statistical approach for memory leak detection in JavaTM applications. Proposed system extends the basic statistical memory leak detection method with further intelligence to pinpoint the source of the memory leak in the source code. As the method adds only small overhead in runtime it is designed to be used in production systems and will help detecting memory leaks in production environments without constraint to the source of the leak. Architecture of the proposed approach is intended to use in cloud applications. 1 INTRODUCTION in production under very specific circumstances (of- ten hardly specifiable) can be very hard to find and fix Memory leaks can be a major problem in distributed in development and test environments. applications, depleting their performance, even if they This is the area we think we can improve by de- run on platforms with automatic memory manage- veloping the solution that uses efficient statistical al- ment like Java Virtual Machine. Finding memory gorithm to detect memory leaks in advance, imposes leaks is coveredby many researches and there are sev- low overhead in production system and would help eral tools and methodologies to find memory leaks. tracking down the source of the leak. The rest of the However, these tools are incorporated in profilers and paper is organized as follows. -

Linux Crash HOWTO
Linux Crash HOWTO Norman Patten [email protected] 2002−01−30 Revision History Revision 1.0 2002−01−30 Revised by: NM Initial release. This document describes the installation and usage of the LKCD (Linux Kernel Crash Dump) package. Linux Crash HOWTO Table of Contents 1. Introduction.....................................................................................................................................................1 1.1. Copyright and License......................................................................................................................1 2. How LKCD Works.........................................................................................................................................2 2.1. What You Need.................................................................................................................................2 3. Installation of lkcd..........................................................................................................................................3 3.1. Installing From Source Code............................................................................................................3 3.2. Building and Installing LKCD Utilities............................................................................................3 3.3. What Gets Installed...........................................................................................................................3 3.4. Installing LKCD Utilities From RPM..............................................................................................3 -

Embedded Linux Conference Europe 2019
Embedded Linux Conference Europe 2019 Linux kernel debugging: going beyond printk messages Embedded Labworks By Sergio Prado. São Paulo, October 2019 ® Copyright Embedded Labworks 2004-2019. All rights reserved. Embedded Labworks ABOUT THIS DOCUMENT ✗ This document is available under Creative Commons BY- SA 4.0. https://creativecommons.org/licenses/by-sa/4.0/ ✗ The source code of this document is available at: https://e-labworks.com/talks/elce2019 Embedded Labworks $ WHOAMI ✗ Embedded software developer for more than 20 years. ✗ Principal Engineer of Embedded Labworks, a company specialized in the development of software projects and BSPs for embedded systems. https://e-labworks.com/en/ ✗ Active in the embedded systems community in Brazil, creator of the website Embarcados and blogger (Portuguese language). https://sergioprado.org ✗ Contributor of several open source projects, including Buildroot, Yocto Project and the Linux kernel. Embedded Labworks THIS TALK IS NOT ABOUT... ✗ printk and all related functions and features (pr_ and dev_ family of functions, dynamic debug, etc). ✗ Static analysis tools and fuzzing (sparse, smatch, coccinelle, coverity, trinity, syzkaller, syzbot, etc). ✗ User space debugging. ✗ This is also not a tutorial! We will talk about a lot of tools and techniches and have fun with some demos! Embedded Labworks DEBUGGING STEP-BY-STEP 1. Understand the problem. 2. Reproduce the problem. 3. Identify the source of the problem. 4. Fix the problem. 5. Fixed? If so, celebrate! If not, go back to step 1. Embedded Labworks TYPES OF PROBLEMS ✗ We can consider as the top 5 types of problems in software: ✗ Crash. ✗ Lockup. ✗ Logic/implementation error. ✗ Resource leak. ✗ Performance.