Whitepaper Long En.Pdf
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

A Generalization of the Minisum and Minimax Voting Methods
A Generalization of the Minisum and Minimax Voting Methods Shankar N. Sivarajan Undergraduate, Department of Physics Indian Institute of Science Bangalore 560 012, India [email protected] Faculty Advisor: Prof. Y. Narahari Deparment of Computer Science and Automation Revised Version: December 4, 2017 Abstract In this paper, we propose a family of approval voting-schemes for electing committees based on the preferences of voters. In our schemes, we calcu- late the vector of distances of the possible committees from each of the ballots and, for a given p-norm, choose the one that minimizes the magni- tude of the distance vector under that norm. The minisum and minimax methods suggested by previous authors and analyzed extensively in the literature naturally appear as special cases corresponding to p = 1 and p = 1; respectively. Supported by examples, we suggest that using a small value of p; such as 2 or 3, provides a good compromise between the minisum and minimax voting methods with regard to the weightage given to approvals and disapprovals. For large but finite p; our method reduces to finding the committee that covers the maximum number of voters, and this is far superior to the minimax method which is prone to ties. We also discuss extensions of our methods to ternary voting. 1 Introduction In this paper, we consider the problem of selecting a committee of k members out of n candidates based on preferences expressed by m voters. The most common way of conducting this election is to allow each voter to select his favorite candidate and vote for him/her, and we select the k candidates with the most number of votes. -

1 Introduction 2 Condorcet and Borda Tallies
1 Introduction General introduction goes here. 2 Condorcet and Borda Tallies 2.1 Definitions We are primarily interested in comparing the behaviors of two information aggregation methods, namely the Condorcet and Borda tallies. This interest is motivated by both historical and practical concerns: the relative merits of the two methods have been argued since the 18th century, and, although variations on the Borda tally are much more common in practice, there is a significant body of theoretical evidence that the Condorcet tally is in many cases superior. To begin, we provide formal definitions of both of these methods, and of a generalized information aggregation problem. An information aggregation problem, often referred to simply as a voting problem, is a problem which involves taking information from a number of disparate sources, and using this information to produce a single output. Problems of this type arise in numerous domains. In political science, they are common, occurring whenever voters cast votes which are used to decide 1 the outcome of some issue. Although less directly, they also occur in fields as diverse as control theory and cognitive science. Wherever there is a system which must coalesce information from its subsystems, there is potentially the need to balance conflicting information about a single topic. In any such circumstance, if there is not reason to trust any single source more than the others, the problem can be phrased as one of information aggregation. 2.1.1 Information Aggregation Problems To facilitate the formalization of these problems, we only consider cases in which a finite number of information sources (which shall henceforth be re- ferred to as voters) provide information regarding some contested issue. -

Stable Voting
Stable Voting Wesley H. Hollidayy and Eric Pacuitz y University of California, Berkeley ([email protected]) z University of Maryland ([email protected]) September 12, 2021 Abstract In this paper, we propose a new single-winner voting system using ranked ballots: Stable Voting. The motivating principle of Stable Voting is that if a candidate A would win without another candidate B in the election, and A beats B in a head-to-head majority comparison, then A should still win in the election with B included (unless there is another candidate A0 who has the same kind of claim to winning, in which case a tiebreaker may choose between A and A0). We call this principle Stability for Winners (with Tiebreaking). Stable Voting satisfies this principle while also having a remarkable ability to avoid tied outcomes in elections even with small numbers of voters. 1 Introduction Voting reform efforts in the United States have achieved significant recent successes in replacing Plurality Voting with Instant Runoff Voting (IRV) for major political elections, including the 2018 San Francisco Mayoral Election and the 2021 New York City Mayoral Election. It is striking, by contrast, that Condorcet voting methods are not currently used in any political elections.1 Condorcet methods use the same ranked ballots as IRV but replace the counting of first-place votes with head- to-head comparisons of candidates: do more voters prefer candidate A to candidate B or prefer B to A? If there is a candidate A who beats every other candidate in such a head-to-head majority comparison, this so-called Condorcet winner wins the election. -
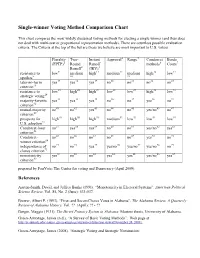
Single-Winner Voting Method Comparison Chart
Single-winner Voting Method Comparison Chart This chart compares the most widely discussed voting methods for electing a single winner (and thus does not deal with multi-seat or proportional representation methods). There are countless possible evaluation criteria. The Criteria at the top of the list are those we believe are most important to U.S. voters. Plurality Two- Instant Approval4 Range5 Condorcet Borda (FPTP)1 Round Runoff methods6 Count7 Runoff2 (IRV)3 resistance to low9 medium high11 medium12 medium high14 low15 spoilers8 10 13 later-no-harm yes17 yes18 yes19 no20 no21 no22 no23 criterion16 resistance to low25 high26 high27 low28 low29 high30 low31 strategic voting24 majority-favorite yes33 yes34 yes35 no36 no37 yes38 no39 criterion32 mutual-majority no41 no42 yes43 no44 no45 yes/no 46 no47 criterion40 prospects for high49 high50 high51 medium52 low53 low54 low55 U.S. adoption48 Condorcet-loser no57 yes58 yes59 no60 no61 yes/no 62 yes63 criterion56 Condorcet- no65 no66 no67 no68 no69 yes70 no71 winner criterion64 independence of no73 no74 yes75 yes/no 76 yes/no 77 yes/no 78 no79 clones criterion72 81 82 83 84 85 86 87 monotonicity yes no no yes yes yes/no yes criterion80 prepared by FairVote: The Center for voting and Democracy (April 2009). References Austen-Smith, David, and Jeffrey Banks (1991). “Monotonicity in Electoral Systems”. American Political Science Review, Vol. 85, No. 2 (June): 531-537. Brewer, Albert P. (1993). “First- and Secon-Choice Votes in Alabama”. The Alabama Review, A Quarterly Review of Alabama History, Vol. ?? (April): ?? - ?? Burgin, Maggie (1931). The Direct Primary System in Alabama. -

Chapter 9:Social Choice: the Impossible Dream
Chapter 9:Social Choice: The Impossible Dream September 18, 2013 Chapter 9:Social Choice: The Impossible Dream Last Time Last time we talked about Voting systems Majority Rule Condorcet's Method Plurality Borda Count Sequential Pairwise Voting Chapter 9:Social Choice: The Impossible Dream Condorcet's Method Definition A ballot consisting of such a rank ordering of candidates is called a preference list ballot because it is a statement of the preferences of the individual who is voting. Description of Condorcet's Method With the voting system known as Condorcet's method, a candidate is a winner precisely when he or she would, on the basis of the ballots cast, defeat every other candidate in a one-on-one contest using majority rule. Chapter 9:Social Choice: The Impossible Dream Example Consider the following set of preference lists: Number of Voters(9) Rank 3 1 1 1 1 1 1 First A A B B C C D Second D C C C B D B Third C B D A D B C Fourth B D A D A A A Winner: C Chapter 9:Social Choice: The Impossible Dream Pros and Cons of Condorcet's Method Pro: Takes all preferences into account. Con: Condorcet's Voting Paradox With three or more candidates, there are elections in which Condorcet's method yields no winners. In particular, the following ballots constitute an election in which Condorcet's method yields no winner. Chapter 9:Social Choice: The Impossible Dream Plurality Voting Plurality Voting Each voter pick their top choice. Chapter 9:Social Choice: The Impossible Dream Example Consider the following set of preference lists: Number of Voters(9) Rank 3 1 1 1 1 1 1 First A A B B C C D Second D B C C B D C Third B C D A D B B Fourth C D A D A A A Winner: A Chapter 9:Social Choice: The Impossible Dream Pros and Cons of Plurality Voting May's Theorem Among all two-candidate voting systems that never result in a tie, majority rule is the only one that treats all voters equally, treats both candidates equally, and is monotone. -

How to Choose a Winner: the Mathematics of Social Choice
Snapshots of modern mathematics № 9/2015 from Oberwolfach How to choose a winner: the mathematics of social choice Victoria Powers Suppose a group of individuals wish to choose among several options, for example electing one of several candidates to a political office or choosing the best contestant in a skating competition. The group might ask: what is the best method for choosing a winner, in the sense that it best reflects the individual pref- erences of the group members? We will see some examples showing that many voting methods in use around the world can lead to paradoxes and bad out- comes, and we will look at a mathematical model of group decision making. We will discuss Arrow’s im- possibility theorem, which says that if there are more than two choices, there is, in a very precise sense, no good method for choosing a winner. This snapshot is an introduction to social choice theory, the study of collective decision processes and procedures. Examples of such situations include • voting and election, • events where a winner is chosen by judges, such as figure skating, • ranking of sports teams by experts, • groups of friends deciding on a restaurant to visit or a movie to see. Let’s start with two examples, one from real life and the other made up. 1 Example 1. In the 1998 election for governor of Minnesota, there were three candidates: Norm Coleman, a Republican; Skip Humphrey, a Democrat; and independent candidate Jesse Ventura. Ventura had never held elected office and was, in fact, a professional wrestler. The voting method used was what is called plurality: each voter chooses one candidate, and the candidate with the highest number of votes wins. -

Instructor's Manual
The Mathematics of Voting and Elections: A Hands-On Approach Instructor’s Manual Jonathan K. Hodge Grand Valley State University January 6, 2011 Contents Preface ix 1 What’s So Good about Majority Rule? 1 Chapter Summary . 1 Learning Objectives . 2 Teaching Notes . 2 Reading Quiz Questions . 3 Questions for Class Discussion . 6 Discussion of Selected Questions . 7 Supplementary Questions . 10 2 Perot, Nader, and Other Inconveniences 13 Chapter Summary . 13 Learning Objectives . 14 Teaching Notes . 14 Reading Quiz Questions . 15 Questions for Class Discussion . 17 Discussion of Selected Questions . 18 Supplementary Questions . 21 3 Back into the Ring 23 Chapter Summary . 23 Learning Objectives . 24 Teaching Notes . 24 v vi CONTENTS Reading Quiz Questions . 25 Questions for Class Discussion . 27 Discussion of Selected Questions . 29 Supplementary Questions . 36 Appendix A: Why Sequential Pairwise Voting Is Monotone, and Instant Runoff Is Not . 37 4 Trouble in Democracy 39 Chapter Summary . 39 Typographical Error . 40 Learning Objectives . 40 Teaching Notes . 40 Reading Quiz Questions . 41 Questions for Class Discussion . 42 Discussion of Selected Questions . 43 Supplementary Questions . 49 5 Explaining the Impossible 51 Chapter Summary . 51 Error in Question 5.26 . 52 Learning Objectives . 52 Teaching Notes . 53 Reading Quiz Questions . 54 Questions for Class Discussion . 54 Discussion of Selected Questions . 55 Supplementary Questions . 59 6 One Person, One Vote? 61 Chapter Summary . 61 Learning Objectives . 62 Teaching Notes . 62 Reading Quiz Questions . 63 Questions for Class Discussion . 65 Discussion of Selected Questions . 65 CONTENTS vii Supplementary Questions . 71 7 Calculating Corruption 73 Chapter Summary . 73 Learning Objectives . 73 Teaching Notes . -

A Proposal for Proportional Representation in the California Legislature
Loyola of Los Angeles Law Review Volume 44 Number 2 Winter 2011 - Symposium: Rebooting California: Initiatives, Conventions & Article 2 Government Reform 1-1-2011 Approximating Democracy: A Proposal for Proportional Representation in the California Legislature Allan Ides Loyola Law School Los Angeles, [email protected] Follow this and additional works at: https://digitalcommons.lmu.edu/llr Part of the Law Commons Recommended Citation Allan Ides, Approximating Democracy: A Proposal for Proportional Representation in the California Legislature , 44 Loy. L.A. L. Rev. 437 (2011). Available at: https://digitalcommons.lmu.edu/llr/vol44/iss2/2 This Symposium is brought to you for free and open access by the Law Reviews at Digital Commons @ Loyola Marymount University and Loyola Law School. It has been accepted for inclusion in Loyola of Los Angeles Law Review by an authorized administrator of Digital Commons@Loyola Marymount University and Loyola Law School. For more information, please contact [email protected]. APPROXIMATING DEMOCRACY: A PROPOSAL FOR PROPORTIONAL REPRESENTATION IN THE CALIFORNIA LEGISLATURE Allan Ides* The State of California elects a bicameral legislature through a first- past-the-post electoral system. Beginning in 2012, the election of California state legislators will be through an open primary, two-round system. Neither of these electoral systems provides for proportional representation in the legislature. Accordingly, neither system leads to a truly representative democracy. The author recommends that the state adopt a proportional representation electoral system—specifically, a mixed-member system—as a more democratic alternative to the plurality/majority systems now in place or projected to be implemented in 2012. -

Selecting the Runoff Pair
Selecting the runoff pair James Green-Armytage New Jersey State Treasury Trenton, NJ 08625 [email protected] T. Nicolaus Tideman Department of Economics, Virginia Polytechnic Institute and State University Blacksburg, VA 24061 [email protected] This version: May 9, 2019 Accepted for publication in Public Choice on May 27, 2019 Abstract: Although two-round voting procedures are common, the theoretical voting literature rarely discusses any such rules beyond the traditional plurality runoff rule. Therefore, using four criteria in conjunction with two data-generating processes, we define and evaluate nine “runoff pair selection rules” that comprise two rounds of voting, two candidates in the second round, and a single final winner. The four criteria are: social utility from the expected runoff winner (UEW), social utility from the expected runoff loser (UEL), representativeness of the runoff pair (Rep), and resistance to strategy (RS). We examine three rules from each of three categories: plurality rules, utilitarian rules and Condorcet rules. We find that the utilitarian rules provide relatively high UEW and UEL, but low Rep and RS. Conversely, the plurality rules provide high Rep and RS, but low UEW and UEL. Finally, the Condorcet rules provide high UEW, high RS, and a combination of UEL and Rep that depends which Condorcet rule is used. JEL Classification Codes: D71, D72 Keywords: Runoff election, two-round system, Condorcet, Hare, Borda, approval voting, single transferable vote, CPO-STV. We are grateful to those who commented on an earlier draft of this paper at the 2018 Public Choice Society conference. 2 1. Introduction Voting theory is concerned primarily with evaluating rules for choosing a single winner, based on a single round of voting. -

Midterm 2. Correction
University of Illinois at Urbana-Champaign Spring 2007 Math 181 Group F1 Midterm 2. Correction. 1. The table below shows chemical compounds which cannot be mixed without causing dangerous reactions. Draw the graph that would be used to facilitate the choice of disposal containers for these compounds ; what is the minimal number of containers needed ? 2 E A B C D E F A X X X B A 3 1 B X X X X C X X D X X X 1 2 E X X C D F X X F 1 Answer. The graph is above ; a vertex-coloring of this graph will at least use three colors since the graph contains a triangle, and the coloring above shows that 3 colors is enough. So the chromatic number of the graph is 3, which means that the minimal number of containers needed is 3. 2. (a) In designing a security system for its accounts, a bank asks each customer to choose a ve-digit number, all the digits to be distinct and nonzero. How many choices can a customer make ? Answer. There are 9 × 8 × 7 × 6 × 5 = 15120 possible choices. (b) A restaurant oers 4 soups, 10 entrees and 8 desserts. How many dierent choices for a meal can a customer make if one selection is made from each category ? If 3 of the desserts are pie and the customer will never order pie, how many dierent meals can the customer choose ? Answer. If one selection is made from each category, there are 4 × 10 × 8 = 320 dierent choices ; if the customer never orders pie, he has only 5 desserts to choose from and thus can make 4 × 10 × 5 = 200 dierent choices. -

Math in Society
Math in Society Edition 1.1 Revision 3 Contents Voting Theory . 1 David Lippman Weighted Voting . 19 David Lippman Fair Division . 31 David Lippman Graph Theory . 49 David Lippman Scheduling . 79 David Lippman Growth Models . 95 David Lippman Finance . 111 David Lippman Statistics . 131 David Lippman, Jeff Eldridge, onlinestatbook.com Describing Data . 143 David Lippman, Jeff Eldridge, onlinestatbook.com Historical Counting Systems . 167 Lawrence Morales Solutions to Selected Exercises . 201 David Lippman Pierce College Ft Steilacoom Copyright © 2010 David Lippman This book was edited by David Lippman, Pierce College Ft Steilacoom Development of this book was supported, in part, by the Transition Math Project Statistics and Describing Data contain portions derived from works by: Jeff Eldridge, Edmonds Community College (used under CC-BY-SA license) www.onlinestatbook.com (used under public domain declaration) Historical Counting Systems derived from work by: Lawrence Morales, Seattle Central Community College (used under CC-BY-SA license) Front cover photo: Jan Tik, http://www.flickr.com/photos/jantik/, CC-BY 2.0 This text is licensed under a Creative Commons Attribution-Share Alike 3.0 United States License. To view a copy of this license, visit http://creativecommons.org/licenses/by-sa/3.0/us/ or send a letter to Creative Commons, 171 Second Street, Suite 300, San Francisco, California, 94105, USA. You are free: to Share — to copy, distribute, display, and perform the work to Remix — to make derivative works Under the following conditions: Attribution. You must attribute the work in the manner specified by the author or licensor (but not in any way that suggests that they endorse you or your use of the work). -

Arrow's Impossibility Theorem
Arrow’s Impossibility Theorem Some announcements • Final reflections due on Monday. • You now have all of the methods and so you can begin analyzing the results of your election. Today’s Goals • We will discuss various fairness criteria and how the different voting methods violate these criteria. Last Time We have so far discussed the following voting methods. • Plurality Method (Majority Method) • Borda Count Method • Plurality-with-Elimination Method (IRV) • Pairwise Comparison Method • Method of Least Worst Defeat • Ranked Pairs Method • Approval Voting Fairness Criteria The following fairness criteria were developed by Kenneth Arrow, an economist in the 1940s. Economists are often interested in voting theories because of their impact on game theory. The mathematician John Nash (the subject of A Beautiful Mind) won the Nobel Prize in economics for his contributions to game theory. The Majority Criterion A majority candidate should always be the winner. Note that this does not say that a candidate must have a majority to win, only that such a candidate should not lose. Plurality, IRV, Pairwise Comparison, LWD, and Ranked Pairs all satisfy the Majority Criterion. The Majority Criterion The Borda Count Method violates the Majority Criterion. Number of voters 6 2 3 1st A B C 2nd B C D 3rd C D B 4th D A A Even though A had a majority of votes it only has 29 points. B is the winner with 32 points. Moral: Borda Count punishes polarizing candidates. The Condorcet Criterion A Condorcet candidate should always be the winner. Recall that a Condorcet Candidate is one that beats all other candidates in a head-to-head (pairwise) comparison.