On Fast Multiplication of a Matrix by Its Transpose
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Introduction to Linear Bialgebra
View metadata, citation and similar papers at core.ac.uk brought to you by CORE provided by University of New Mexico University of New Mexico UNM Digital Repository Mathematics and Statistics Faculty and Staff Publications Academic Department Resources 2005 INTRODUCTION TO LINEAR BIALGEBRA Florentin Smarandache University of New Mexico, [email protected] W.B. Vasantha Kandasamy K. Ilanthenral Follow this and additional works at: https://digitalrepository.unm.edu/math_fsp Part of the Algebra Commons, Analysis Commons, Discrete Mathematics and Combinatorics Commons, and the Other Mathematics Commons Recommended Citation Smarandache, Florentin; W.B. Vasantha Kandasamy; and K. Ilanthenral. "INTRODUCTION TO LINEAR BIALGEBRA." (2005). https://digitalrepository.unm.edu/math_fsp/232 This Book is brought to you for free and open access by the Academic Department Resources at UNM Digital Repository. It has been accepted for inclusion in Mathematics and Statistics Faculty and Staff Publications by an authorized administrator of UNM Digital Repository. For more information, please contact [email protected], [email protected], [email protected]. INTRODUCTION TO LINEAR BIALGEBRA W. B. Vasantha Kandasamy Department of Mathematics Indian Institute of Technology, Madras Chennai – 600036, India e-mail: [email protected] web: http://mat.iitm.ac.in/~wbv Florentin Smarandache Department of Mathematics University of New Mexico Gallup, NM 87301, USA e-mail: [email protected] K. Ilanthenral Editor, Maths Tiger, Quarterly Journal Flat No.11, Mayura Park, 16, Kazhikundram Main Road, Tharamani, Chennai – 600 113, India e-mail: [email protected] HEXIS Phoenix, Arizona 2005 1 This book can be ordered in a paper bound reprint from: Books on Demand ProQuest Information & Learning (University of Microfilm International) 300 N. -

21. Orthonormal Bases
21. Orthonormal Bases The canonical/standard basis 011 001 001 B C B C B C B0C B1C B0C e1 = B.C ; e2 = B.C ; : : : ; en = B.C B.C B.C B.C @.A @.A @.A 0 0 1 has many useful properties. • Each of the standard basis vectors has unit length: q p T jjeijj = ei ei = ei ei = 1: • The standard basis vectors are orthogonal (in other words, at right angles or perpendicular). T ei ej = ei ej = 0 when i 6= j This is summarized by ( 1 i = j eT e = δ = ; i j ij 0 i 6= j where δij is the Kronecker delta. Notice that the Kronecker delta gives the entries of the identity matrix. Given column vectors v and w, we have seen that the dot product v w is the same as the matrix multiplication vT w. This is the inner product on n T R . We can also form the outer product vw , which gives a square matrix. 1 The outer product on the standard basis vectors is interesting. Set T Π1 = e1e1 011 B C B0C = B.C 1 0 ::: 0 B.C @.A 0 01 0 ::: 01 B C B0 0 ::: 0C = B. .C B. .C @. .A 0 0 ::: 0 . T Πn = enen 001 B C B0C = B.C 0 0 ::: 1 B.C @.A 1 00 0 ::: 01 B C B0 0 ::: 0C = B. .C B. .C @. .A 0 0 ::: 1 In short, Πi is the diagonal square matrix with a 1 in the ith diagonal position and zeros everywhere else. -

Multivector Differentiation and Linear Algebra 0.5Cm 17Th Santaló
Multivector differentiation and Linear Algebra 17th Santalo´ Summer School 2016, Santander Joan Lasenby Signal Processing Group, Engineering Department, Cambridge, UK and Trinity College Cambridge [email protected], www-sigproc.eng.cam.ac.uk/ s jl 23 August 2016 1 / 78 Examples of differentiation wrt multivectors. Linear Algebra: matrices and tensors as linear functions mapping between elements of the algebra. Functional Differentiation: very briefly... Summary Overview The Multivector Derivative. 2 / 78 Linear Algebra: matrices and tensors as linear functions mapping between elements of the algebra. Functional Differentiation: very briefly... Summary Overview The Multivector Derivative. Examples of differentiation wrt multivectors. 3 / 78 Functional Differentiation: very briefly... Summary Overview The Multivector Derivative. Examples of differentiation wrt multivectors. Linear Algebra: matrices and tensors as linear functions mapping between elements of the algebra. 4 / 78 Summary Overview The Multivector Derivative. Examples of differentiation wrt multivectors. Linear Algebra: matrices and tensors as linear functions mapping between elements of the algebra. Functional Differentiation: very briefly... 5 / 78 Overview The Multivector Derivative. Examples of differentiation wrt multivectors. Linear Algebra: matrices and tensors as linear functions mapping between elements of the algebra. Functional Differentiation: very briefly... Summary 6 / 78 We now want to generalise this idea to enable us to find the derivative of F(X), in the A ‘direction’ – where X is a general mixed grade multivector (so F(X) is a general multivector valued function of X). Let us use ∗ to denote taking the scalar part, ie P ∗ Q ≡ hPQi. Then, provided A has same grades as X, it makes sense to define: F(X + tA) − F(X) A ∗ ¶XF(X) = lim t!0 t The Multivector Derivative Recall our definition of the directional derivative in the a direction F(x + ea) − F(x) a·r F(x) = lim e!0 e 7 / 78 Let us use ∗ to denote taking the scalar part, ie P ∗ Q ≡ hPQi. -

Algebra of Linear Transformations and Matrices Math 130 Linear Algebra
Then the two compositions are 0 −1 1 0 0 1 BA = = 1 0 0 −1 1 0 Algebra of linear transformations and 1 0 0 −1 0 −1 AB = = matrices 0 −1 1 0 −1 0 Math 130 Linear Algebra D Joyce, Fall 2013 The products aren't the same. You can perform these on physical objects. Take We've looked at the operations of addition and a book. First rotate it 90◦ then flip it over. Start scalar multiplication on linear transformations and again but flip first then rotate 90◦. The book ends used them to define addition and scalar multipli- up in different orientations. cation on matrices. For a given basis β on V and another basis γ on W , we have an isomorphism Matrix multiplication is associative. Al- γ ' φβ : Hom(V; W ) ! Mm×n of vector spaces which though it's not commutative, it is associative. assigns to a linear transformation T : V ! W its That's because it corresponds to composition of γ standard matrix [T ]β. functions, and that's associative. Given any three We also have matrix multiplication which corre- functions f, g, and h, we'll show (f ◦ g) ◦ h = sponds to composition of linear transformations. If f ◦ (g ◦ h) by showing the two sides have the same A is the standard matrix for a transformation S, values for all x. and B is the standard matrix for a transformation T , then we defined multiplication of matrices so ((f ◦ g) ◦ h)(x) = (f ◦ g)(h(x)) = f(g(h(x))) that the product AB is be the standard matrix for S ◦ T . -

The Classical Matrix Groups 1 Groups
The Classical Matrix Groups CDs 270, Spring 2010/2011 The notes provide a brief review of matrix groups. The primary goal is to motivate the lan- guage and symbols used to represent rotations (SO(2) and SO(3)) and spatial displacements (SE(2) and SE(3)). 1 Groups A group, G, is a mathematical structure with the following characteristics and properties: i. the group consists of a set of elements {gj} which can be indexed. The indices j may form a finite, countably infinite, or continous (uncountably infinite) set. ii. An associative binary group operation, denoted by 0 ∗0 , termed the group product. The product of two group elements is also a group element: ∀ gi, gj ∈ G gi ∗ gj = gk, where gk ∈ G. iii. A unique group identify element, e, with the property that: e ∗ gj = gj for all gj ∈ G. −1 iv. For every gj ∈ G, there must exist an inverse element, gj , such that −1 gj ∗ gj = e. Simple examples of groups include the integers, Z, with addition as the group operation, and the real numbers mod zero, R − {0}, with multiplication as the group operation. 1.1 The General Linear Group, GL(N) The set of all N × N invertible matrices with the group operation of matrix multiplication forms the General Linear Group of dimension N. This group is denoted by the symbol GL(N), or GL(N, K) where K is a field, such as R, C, etc. Generally, we will only consider the cases where K = R or K = C, which are respectively denoted by GL(N, R) and GL(N, C). -

Matrix Multiplication. Diagonal Matrices. Inverse Matrix. Matrices
MATH 304 Linear Algebra Lecture 4: Matrix multiplication. Diagonal matrices. Inverse matrix. Matrices Definition. An m-by-n matrix is a rectangular array of numbers that has m rows and n columns: a11 a12 ... a1n a21 a22 ... a2n . .. . am1 am2 ... amn Notation: A = (aij )1≤i≤n, 1≤j≤m or simply A = (aij ) if the dimensions are known. Matrix algebra: linear operations Addition: two matrices of the same dimensions can be added by adding their corresponding entries. Scalar multiplication: to multiply a matrix A by a scalar r, one multiplies each entry of A by r. Zero matrix O: all entries are zeros. Negative: −A is defined as (−1)A. Subtraction: A − B is defined as A + (−B). As far as the linear operations are concerned, the m×n matrices can be regarded as mn-dimensional vectors. Properties of linear operations (A + B) + C = A + (B + C) A + B = B + A A + O = O + A = A A + (−A) = (−A) + A = O r(sA) = (rs)A r(A + B) = rA + rB (r + s)A = rA + sA 1A = A 0A = O Dot product Definition. The dot product of n-dimensional vectors x = (x1, x2,..., xn) and y = (y1, y2,..., yn) is a scalar n x · y = x1y1 + x2y2 + ··· + xnyn = xk yk . Xk=1 The dot product is also called the scalar product. Matrix multiplication The product of matrices A and B is defined if the number of columns in A matches the number of rows in B. Definition. Let A = (aik ) be an m×n matrix and B = (bkj ) be an n×p matrix. -

Linear Transformations and Determinants Matrix Multiplication As a Linear Transformation
Linear transformations and determinants Math 40, Introduction to Linear Algebra Monday, February 13, 2012 Matrix multiplication as a linear transformation Primary example of a = matrix linear transformation ⇒ multiplication Given an m n matrix A, × define T (x)=Ax for x Rn. ∈ Then T is a linear transformation. Astounding! Matrix multiplication defines a linear transformation. This new perspective gives a dynamic view of a matrix (it transforms vectors into other vectors) and is a key to building math models to physical systems that evolve over time (so-called dynamical systems). A linear transformation as matrix multiplication Theorem. Every linear transformation T : Rn Rm can be → represented by an m n matrix A so that x Rn, × ∀ ∈ T (x)=Ax. More astounding! Question Given T, how do we find A? Consider standard basis vectors for Rn: Transformation T is 1 0 0 0 completely determined by its . e1 = . ,...,en = . action on basis vectors. 0 0 0 1 Compute T (e1),T(e2),...,T(en). Standard matrix of a linear transformation Question Given T, how do we find A? Consider standard basis vectors for Rn: Transformation T is 1 0 0 0 completely determined by its . e1 = . ,...,en = . action on basis vectors. 0 0 0 1 Compute T (e1),T(e2),...,T(en). Then || | is called the T (e ) T (e ) T (e ) 1 2 ··· n standard matrix for T. || | denoted [T ] Standard matrix for an example Example x 3 2 x T : R R and T y = → y z 1 0 0 1 0 0 T 0 = T 1 = T 0 = 0 1 0 0 0 1 100 2 A = What is T 5 ? 010 − 12 2 2 100 2 A 5 = 5 = ⇒ − 010− 5 12 12 − Composition T : Rn Rm is a linear transformation with standard matrix A Suppose → S : Rm Rp is a linear transformation with standard matrix B. -

Working with 3D Rotations
Working With 3D Rotations Stan Melax Graphics Software Engineer, Intel Human Brain is wired for Spatial Computation Which shape is the same: a) b) c) “I don’t need to ask A childhood IQ test question for directions” Translations Rotations Agenda ● Rotations and Matrices (hopefully review) ● Combining Rotations ● Matrix and Axis Angle ● Challenges of deep Space (of Rotations) ● Quaternions ● Applications Terminology Clarification Preferred usages of various terms: Linear Angular Object Pose Position (point) Orientation A change in Pose Translation (vector) Rotation Rate of change Linear Velocity Spin also: Direction specifies 2 DOF, Orientation specifies all 3 angular DOF. Rotations Trickier than Translations Translations Rotations a then b == b then a x then y != y then x (non-commutative) ● Programming with rotations also more challenging! 2D Rotation θ Rotate [1 0] by θ about origin 1,1 [ cos(θ) sin(θ) ] θ θ sin cos θ 1,0 2D Rotation θ Rotate [0 1] by θ about origin -1,1 0,1 sin θ [-sin(θ) cos(θ)] θ θ cos 2D Rotation of an arbitrary point Rotate about origin by θ = cos θ + sin θ 2D Rotation of an arbitrary point 푥 Rotate 푦 about origin by θ 푥′, 푦′ 푥′ = 푥 cos θ − 푦 sin θ 푦′ = 푥 sin θ + 푦 cos θ 푦 푥 2D Rotation Matrix 푥 Rotate 푦 about origin by θ 푥′, 푦′ 푥′ = 푥 cos θ − 푦 sin θ 푦′ = 푥 sin θ + 푦 cos θ 푦 푥′ cos θ − sin θ 푥 푥 = 푦′ sin θ cos θ 푦 cos θ − sin θ Matrix is rotation by θ sin θ cos θ 2D Orientation 풚 Yellow grid placed over first grid but at angle of θ cos θ − sin θ sin θ cos θ 풙 Columns of the matrix are the directions of the axes. -
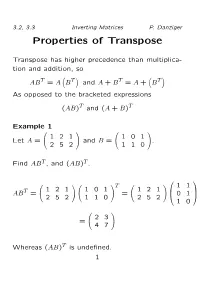
Properties of Transpose
3.2, 3.3 Inverting Matrices P. Danziger Properties of Transpose Transpose has higher precedence than multiplica- tion and addition, so T T T T AB = A B and A + B = A + B As opposed to the bracketed expressions (AB)T and (A + B)T Example 1 1 2 1 1 0 1 Let A = ! and B = !. 2 5 2 1 1 0 Find ABT , and (AB)T . T 1 1 1 2 1 1 0 1 1 2 1 0 1 ABT = ! ! = ! 0 1 2 5 2 1 1 0 2 5 2 B C @ 1 0 A 2 3 = ! 4 7 Whereas (AB)T is undefined. 1 3.2, 3.3 Inverting Matrices P. Danziger Theorem 2 (Properties of Transpose) Given ma- trices A and B so that the operations can be pre- formed 1. (AT )T = A 2. (A + B)T = AT + BT and (A B)T = AT BT − − 3. (kA)T = kAT 4. (AB)T = BT AT 2 3.2, 3.3 Inverting Matrices P. Danziger Matrix Algebra Theorem 3 (Algebraic Properties of Matrix Multiplication) 1. (k + `)A = kA + `A (Distributivity of scalar multiplication I) 2. k(A + B) = kA + kB (Distributivity of scalar multiplication II) 3. A(B + C) = AB + AC (Distributivity of matrix multiplication) 4. A(BC) = (AB)C (Associativity of matrix mul- tiplication) 5. A + B = B + A (Commutativity of matrix ad- dition) 6. (A + B) + C = A + (B + C) (Associativity of matrix addition) 7. k(AB) = A(kB) (Commutativity of Scalar Mul- tiplication) 3 3.2, 3.3 Inverting Matrices P. Danziger The matrix 0 is the identity of matrix addition. -

16 the Transpose
The Transpose Learning Goals: to expose some properties of the transpose We would like to see what happens with our factorization if we get zeroes in the pivot positions and have to employ row exchanges. To do this we need to look at permutation matrices. But to study these effectively, we need to know something about the transpose. So the transpose of a matrix is what you get by swapping rows for columns. In symbols, T ⎡2 −1⎤ T ⎡ 2 0 4⎤ ⎢ ⎥ A ij = Aji. By example, ⎢ ⎥ = 0 3 . ⎣−1 3 5⎦ ⎢ ⎥ ⎣⎢4 5 ⎦⎥ Let’s take a look at how the transpose interacts with algebra: T T T T • (A + B) = A + B . This is simple in symbols because (A + B) ij = (A + B)ji = Aji + Bji = Y T T T A ij + B ij = (A + B )ij. In practical terms, it just doesn’t matter if we add first and then flip or flip first and then add • (AB)T = BTAT. We can do this in symbols, but it really doesn’t help explain why this is n true: (AB)T = (AB) = T T = (BTAT) . To get a better idea of what is ij ji ∑a jkbki = ∑b ika kj ij k =1 really going on, look at what happens if B is a single column b. Then Ab is a combination of the columns of A. If we transpose this, we get a row which is a combination of the rows of AT. In other words, (Ab)T = bTAT. Then we get the whole picture of (AB)T by placing several columns side-by-side, which is putting a whole bunch of rows on top of each other in BT. -
Eigenvalues and Eigenvectors
Section 5.1 Eigenvalues and Eigenvectors At this point in the class, we understand that the operation of matrix multiplication is very different from scalar multiplication. Matrix multiplication is an operation that finds the product of a pair of matrices, whereas scalar multiplication finds the product of a scalar with a matrix. More to the point, scalar multiplication of a scalar k with a matrix X is an easy operation to perform; indeed there's a simple algorithm: multiply each entry of X by the scalar k. Matrix multiplication on the other hand cannot be expressed using a simple algorithm. Indeed, the operation is extremely complex: to multiply a pair of n×n matrices, it takes about n2 operations, a hugely inefficient process. Thus it is surprising that, for any square matrix A, certain matrix multiplications \collapse" (in a sense) into scalar multiplication. As an example, consider the matrices ( ) ( ) ( ) 3 2 −4 10 A = ; w = ; x = : 3 4 −1 15 The product Aw is not particularly interesting: ( ) −14 Aw = ; −16 indeed, there appears to be very little connection between A, w, and Aw. On the other hand, an we see an interesting phenomenon when we calculate Ax: ( ) ( ) 60 10 Ax = = 6 = 6x: 90 15 Forgetting the calculation in the middle, we have Ax = 6x; in a sense, the matrix multiplication Ax collapsed into scalar multiplication 6x. We will see below that the phenomenon described here is more common than one might think. Identifying products like Ax = 6x will allow us to extract a great deal of useful information about A; accordingly, the rest of the section will be devoted to this phenomenon, which we give a name in the next definition. -

Sophomoric Matrix Multiplication
Sophomoric Matrix Multiplication Carl C. Cowen IUPUI (Indiana University Purdue University Indianapolis) September 12, 2016, Taylor University Linear algebra students learn, for m × n matrices A, B, and C, matrix addition is A + B = C if and only if aij + bij = cij. Expect matrix multiplication is AB = C if and only if aijbij = cij, But, the professor says \No! It is much more complicated than that!" Linear algebra students learn, for m × n matrices A, B, and C, matrix addition is A + B = C if and only if aij + bij = cij. Expect matrix multiplication is AB = C if and only if aijbij = cij, But, the professor says \No! It is much more complicated than that!" Today, I want to explain why this kind of multiplication not only is sensible but also is very practical,very interesting, and has many applications in mathematics and related subjects. Linear algebra students learn, for m × n matrices A, B, and C, matrix addition is A + B = C if and only if aij + bij = cij. Expect matrix multiplication is AB = C if and only if aijbij = cij, But, the professor says \No! It is much more complicated than that!" Today, I want to explain why this kind of multiplication not only is sensible but also is very practical, very interesting, and has many applications in mathematics and related subjects. Definition If A and B are m × n matrices, the Schur (or Hadamard or naive or sophomoric) product of A and B is the m × n matrix C = A•B with cij = aijbij. These ideas go back more than a century to Moutard (1894), who didn't even notice he had proved anything(!), Hadamard (1899), and Schur (1911).