A Robust Durability Process for Military Ground
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Lynuxworks Lynxsecure Embedded Hypervisor and Separation
Operating systems: RTOS and tools Software LynuxWorks, Inc. 855 Embedded Way • San Jose, CA 95138 800-255-5969 www.lynuxworks.com LynxSecure Embedded Hypervisor and Separation Kernel With the introduction of the new LynxSecure separation kernel and embedded hypervisor, LynuxWorks once again raises the bar when it comes to superior embedded software security and safety. LynxSecure has been built from the ground up as a real-time separa- tion kernel able to run different operating systems and applications in their own secure partitions. The LynxSecure separation kernel is a virtual machine monitor that is certifi able to (a) Common Criteria EAL 7 (Evaluated Assurance Level 7) security certifi cation, a level of certifi cation unattained by any known operating system to date; and (b) DO-178B Level A, the highest level of FAA certifi cation for safety-critical avionics applications. LynxSecure conforms to the Multiple Independent Levels of Security/ Safety (MILS) architecture. The embedded hypervisor component of LynxSecure allows multiple “guest” operating systems to run in their own secure partitions. These can be run in either paravirtual- ized or fully virtualized modes, helping preserve legacy applications and operating systems in systems that now have a security require- FEATURES ment. Guest operating systems include the LynxOS family, Linux and › Optimal security and safety – the only operating system designed to Windows. support CC EAL 7 and DO-178B Level A › Real time – time-space partitioned RTOS for superior determinism and performance -

Cloud Computing Bible Is a Wide-Ranging and Complete Reference
A thorough, down-to-earth look Barrie Sosinsky Cloud Computing Barrie Sosinsky is a veteran computer book writer at cloud computing specializing in network systems, databases, design, development, The chance to lower IT costs makes cloud computing a and testing. Among his 35 technical books have been Wiley’s Networking hot topic, and it’s getting hotter all the time. If you want Bible and many others on operating a terra firma take on everything you should know about systems, Web topics, storage, and the cloud, this book is it. Starting with a clear definition of application software. He has written nearly 500 articles for computer what cloud computing is, why it is, and its pros and cons, magazines and Web sites. Cloud Cloud Computing Bible is a wide-ranging and complete reference. You’ll get thoroughly up to speed on cloud platforms, infrastructure, services and applications, security, and much more. Computing • Learn what cloud computing is and what it is not • Assess the value of cloud computing, including licensing models, ROI, and more • Understand abstraction, partitioning, virtualization, capacity planning, and various programming solutions • See how to use Google®, Amazon®, and Microsoft® Web services effectively ® ™ • Explore cloud communication methods — IM, Twitter , Google Buzz , Explore the cloud with Facebook®, and others • Discover how cloud services are changing mobile phones — and vice versa this complete guide Understand all platforms and technologies www.wiley.com/compbooks Shelving Category: Use Google, Amazon, or -

(DBATU Iope) Question Bank (MCQ) Cloud Computing Elective II
Diploma in Computer Engineering (DBATU IoPE) Question Bank (MCQ) Cloud Computing Elective II (DCE3204A) Summer 2020 Exam (To be held in October 2020 - Online) Prepared by Prof. S.M. Sabale Head of Computer Engineering Institute of Petrochemical Engineering, Lonere Id 1 Question Following are the features of cloud computing: (CO1) A Reliability B Centralized computing C Location dependency D No need of internet connection Answer Marks 2 Unit I Id 2 Question Which is the property that enables a system to continue operating properly in the event of the failure of some of its components? (CO1) A Availability B Fault-tolerance C Scalability D System Security Answer Marks 2 Unit I Id 3 Question A _____________ is a contract between a network service provider and a customer that specifies, usually in measurable terms (QoS), what services the network service provider will furnish (CO1) A service-level agreement B service-level specifications C document D agreement Answer Marks 2 Unit I Id 4 Question The degree to which a system, subsystem, or equipment is in a specified operable and committable state at the start of a mission, when the mission is called for at an unknown time is called as _________ (CO1) A reliability B Scalability C Availability D system resilience Answer Marks 2 Unit I Id 5 Question Google Apps is an example of (CO1) A IaaS B SaaS C PaaS D Both PaaS and SaaS Answer Marks 2 Unit I Id 6 Question Separation of a personal computer desktop environment from a physical machine through the client server model of computing is known as __________. -

High-Assurance Separation Kernels: a Survey on Formal Methods
1 High-Assurance Separation Kernels: A Survey on Formal Methods Yongwang Zhao, Beihang University, China David Sanan´ , Nanyang Technological University, Singapore Fuyuan Zhang, Nanyang Technological University, Singapore Yang Liu, Nanyang Technological University, Singapore Separation kernels provide temporal/spatial separation and controlled information flow to their hosted applications. They are introduced to decouple the analysis of applications in partitions from the analysis of the kernel itself. More than 20 implementations of separation kernels have been developed and widely applied in critical domains, e.g., avionics/aerospace, military/defense, and medical devices. Formal methods are mandated by the security/safety certification of separation kernels and have been carried out since this concept emerged. However, this field lacks a survey to systematically study, compare, and analyze related work. On the other hand, high-assurance separation kernels by formal methods still face big challenges. In this paper, an analytical framework is first proposed to clarify the functionalities, implementations, properties and stan- dards, and formal methods application of separation kernels. Based on the proposed analytical framework, a taxonomy is designed according to formal methods application, functionalities, and properties of separation kernels. Research works in the literature are then categorized and overviewed by the taxonomy. In accordance with the analytical framework, a compre- hensive analysis and discussion of related work are presented. -

Unit-1 Cloud Computing Virtualization Concepts
Unit-1 Cloud Computing Virtualization Concepts AVINAV PATHAK Assistant Professor Shobhit Institute of Engineering & Technology (Deemed-to-be-University), Meerut, India Virtualization Concept Virtualization is a technique, which allows to share single physical instance of an application or resource among multiple organizations or tenants (customers). It does so by assigning a logical name to a physical resource and providing a pointer to that physical resource on demand. Virtualization Concept Creating a virtual machine over existing operating system and hardware is referred as Hardware Virtualization. Virtual Machines provide an environment that is logically separated from the underlying hardware. The machine on which the virtual machine is created is known as host machine and virtual machine is referred as a guest machine. This virtual machine is managed by a software or firmware, which is known as hypervisor. Hypervisor The hypervisor is a firmware or low-level program that acts as a Virtual Machine Manager. There are two types of hypervisor: Type 1 hypervisor executes on bare system. LynxSecure, RTS Hypervisor, Oracle VM, Sun xVM Server, VirtualLogic VLX are examples of Type 1 hypervisor. The following diagram shows the Type 1 hypervisor. Virtualization Concept The type1 hypervisor does not have any host operating system because they are installed on a bare system. Type 2 hypervisor is a software interface that emulates the devices with which a system normally interacts. Containers, KVM, Microsoft Hyper V, VMWare Fusion, Virtual Server 2005 R2, Windows Virtual PC and VMWare workstation 6.0 are examples of Type 2 hypervisor. The following diagram shows the Type 2 hypervisor. Types of Hardware Virtualization Here are the three types of hardware virtualization: 1. -

Continuing to Secure the Internet of Things
Safety & Security for the Connected World Continuing to secure the Internet of Things Connected embedded devices l Everything in our embedded world is becoming connected to – The Internet – Other connected devices – Personal devices l The information provided by these devices and the control of the devices is still vulnerable to cyber attacks – Cloud exploits – Embedded device compromise (e.g. Target attack) 2 Securing connected embedded devices l Security as an afterthought will have the same result as anti-virus and network security for protecting PCs l In the embedded world we have the opportunity to build security into our connected devices l Lynx Software Technologies continues to provide real-time products with built-in security 3 Security Technologies l LynxOS 7.0 offers military-grade security built into the RTOS Process 1 Process 2 l Connected embedded devices CPU CPU can be protected from Quota 1 Quota 2 Identification & Roles & traditional cyber attacks Authentication Capabilities Access Control Lists Residual – Network infiltration Information File System Audit Log Protection – Denial of Service attacks Device Hardware – Memory scraping – Password and authentication attacks • e.g. Root Escalation or “Rooting” the system 4 Security Technologies l LynxSecure offers isolation, separation and virtualization for multi-domain systems – Real-time performance and small footprint for real embedded deployments – Consolidation of hardware for efficient use of multi-core systems – Secure separation of networks, devices, operating systems -
Cloud Computing MCQ.Xlsx
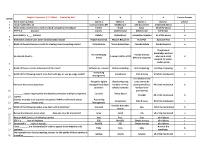
Chapter 1 Question 1, 2, 3 Mark Created by Atul a b c d Correct Answer SR.NO 1 Write down question Option a Option b Option c Option d a/b/c/d 2 Cloud model relies on communication API Middleware web documents embedded device a 3 What widely used service is built on cloud-computing technology? Twitter Skype Gmail All of the above d 4 HTTP is a ______ protocol stateful unidirectional bidirectional full dulpex b websocket is a____ Protocol stateful bidirectional connection oriented all of the above d 5 6 Websocket protocol uses which communication model Publish-Subscribe Request Response Push-Pull Exclusive Pair a Which of these techniques is vital for creating cloud-computing centers Virtualization Transubstantiation Cannibalization Insubordination a 7 The group of knowledge workers An overhanging A cloud that sits An internal cloud is… A career risk for a CIO who use a social d threat behind a corporate network for water- cooler gossip 8 Which of these is not an antecedent of the cloud? Software as a service Utility computing Grid computing Desktop computing d 9 Accounting Which of the following subject area deals with pay-as-you-go usage model? Compliance Data Privacy All of the mentioned a 10 Management The low barrier to Except for tightly Cloud computing entry cannot be Point out the correct statement managed SaaS cloud vendors run very accompanied by a All of the mentioned b providers reliable networks low barrier to 11 provisioning ________ captive requires that the cloud accommodate multiple compliance Licensed Policy-based Variable All of the mentioned b 12 regimes. -

UNIT – I – Cloud Computing – SCSA7023 Unit – I
SCHOOL OF COMPUTING DEPARTMENT OF COMPUTER SCIENCE AND ENGINEERING UNIT – I – Cloud Computing – SCSA7023 Unit – I Understanding Cloud Computing Topics: Introduction -History of Cloud Computing-Cloud computing architecture-NIST architectural Framework-Types of Cloud-Service Based - Location Based-Merits and Demerits of Cloud Computing-Difference: Cloud and Web 2.0-Key challenges in cloud computing-Major cloud players-Cloud deployment model-Virtualization in cloud computing-Types of virtualization-Parallelization in cloud computing-Cloud resource management-Dynamic resource allocation-Optimal allocation of cloud models-Web services-Key Concepts 1.1. Introduction to Cloud Computing Cloud computing is the on-demand availability of computer system resources, especially data storage (cloud storage) and computing power, without direct active management by the user. The term is generally used to describe data centers available to many users over the Internet. Large clouds, predominant today, often have functions distributed over multiple locations from central servers. If the connection to the user is relatively close, it may be designated an edge server. 1.2 History of Cloud computing Cloud computing has as its antecedents both client/server computing and peer-to-peer distributed computing. It’s all a matter of how centralized storage facilitates collaboration and how multiple computers work together to increase computing power. During the 1960s, the initial concepts of time-sharing became popularized via RJE (Remote Job Entry) this terminology was mostly associated with large vendors such as IBM and DEC. Full- time-sharing solutions were available by the early 1970s on such platforms as Multics (on GE hardware), Cambridge CTSS, and the earliest UNIX ports (on DEC hardware). -

Curtiss-Wright Debuts Support for Lynxsecure Hypervisor Operating Environment on Its Intel®-Based SBC and Small Form Factor Systems
NEWS RELEASE FOR IMMEDIATE RELEASE Contact: John Wranovics M: 925.640.6402 [email protected] Curtiss-Wright Debuts Support for LynxSecure Hypervisor Operating Environment on its Intel®-based SBC and Small Form Factor Systems Expanded collaboration with Lynx Software Technologies brings secure hypervisor technology to rugged deployed modules and LRUs ASHBURN, Va. – January 30, 2017 – Curtiss-Wright’s Defense Solutions division today announced support for the LynxSecure separation kernel hypervisor, a real-time secure virtualization platform capable of leveraging multi-core CPU hardware virtualization features on Curtiss-Wright’s Intel-based single board computer (SBC) and Parvus® DuraCOR® small form factor processor product families. The expanded collaboration between Curtiss-Wright and Lynx Software Technologies, Inc., a world leader in the embedded safety and security software market, enables customers to deploy Curtiss-Wright hardware with LynxSecure hypervisor technology to satisfy high assurance computing requirements on in support of the NIST, NSA Common Criteria, and NERC CIP evaluation processes used to regulate military and industrial computing environments. The first Curtiss-Wright products pre-validated for LynxSecure support are the rugged DuraCOR 80-41 tactical mission computer subsystem and the VPX3-1257 3U OpenVPX SBC, both based on quad-core, Intel Core i7 processors. Curtiss-Wright and Lynx Software Technologies anticipate availability of additional pre-validated SBCs and subsystems in the near future. The use -

Grid and Cloud Computing Subject Code
MOTHER TERESA WOMEN’S UNIVERSITY DIRECTORATE OF DISTANCE EDUCATION KODAIKANAL – 624 102 M.Sc. COMPUTER SCIENCE (P.G.) MATERIAL FOR GRID AND CLOUD COMPUTING SUBJECT CODE Compiled by Dr. K.Kavitha GRID AND CLOUD COMPUTING UNIT I : Concepts and Architectures: Introduction - Parallel and Distributed Computing- Cluster computing – Grid Computing-anatomy and physiology of Grid – Review of web services – OGSA – WSRF. UNIT II : GRID Monitoring : Grid Monitoring Architecture (GMA) – An overview of Grid Monitoring systems – Grid ICE – JAMM – MDs – Network Weather Service – R – GMA – other Monitoring systems Ganglia and Grid Mon UNIT III: Grid Security and Resource Management: Grid Security – A Brief security primer – PRI – X509 Certificates – Grid security – Grid Scheduling and Resource management –Scheduling paradigms – Working principles of scheduling – A review of condor, SGE, PBS and LSF – Grid scheduling with QoS UNIT IV: Examining the Value Proposition : Defining Cloud Computing, Assessing the Value Proposition, Understanding Cloud Architecture, Understanding Services and Applications by Type. UNIT V : Using Platforms : Understanding Abstraction and Virtualization, Capacity, Planning, Exploring Platform as a Service, Using Google Web Services, Using Amazon Web Services, Using Microsoft Cloud Services. TEXT BOOKS 1.The Grid : Core Technologies – Maozhen Li, Mark Baker, - John Wiley & Sum 2005 2. Cloud Computing Bible – Barrie Sosinky – Wiley Publishing Inc, 2011 REFERENCE BOOKS 1. Grid Computing – Josy Joseph & Craig Fellenstein – Pearson Education, 2004 2. The Little Book of Cloud Computing – A New Street Executive Summary 3. Lars Nielson – 2011 Edition UNIT I CONCEPTS AND ARCHITECTURE Introduction Grid computing is a group of computers physically connected (over a network or with Internet) to perform a dedicated tasks together, such as analyzing e-commerce data and solve a complex problem. -

Towards Full Virtualization of Embedded Real-Time Systems
A thesis submitted to the Faculty of Computer Science, Electrical Engineering and Mathematics of the University of Paderborn in partial fulfillment of the requirements for the degree of Dr. rer. nat. submitted by Dipl.-Inform. Timo Kerstan Paderborn, 21. März 2011 TOWARDSFULLVIRTUALIZATIONOF EMBEDDEDREAL-TIMESYSTEMS Supervisor________________________________________________ Prof. Dr. rer. nat. Franz Josef Rammig Referees________________________________________________ Prof. Dr. rer. nat. Franz Josef Rammig Prof. Dr. rer. nat. Marco Platzner Timo Kerstan: Towards full virtualization of embedded real-time systems– © University of Paderborn, 21. März 2011 ABSTRACT The growing complexity and the need for high level functional- ity in embedded hard real-time systems lead to conflicting goals for the design of the underlying system software. Adding the re- quired high level functionality endangers the properties of being small, robust, efficient, safe and secure typically stated for em- bedded real-time operating systems. On the other side, the capa- bility of handling hard real-time loads in a general purpose OS is often not compatible due to strong non determinisms in gen- eral purpose OSes. Top of the line cars already house more than 70 interconnected embedded control units (ECUs). The question is how to cope with this additional complexity. Will the next generation of cars house even more ECUs or will there be pow- erful general purpose ECUs executing more than one dedicated task to reduce the number of ECUs, as the growing number of ECUs is not adequately manageable any more? When looking towards the direction of using more powerful ECUs, the con- flicting goals of general purpose OSes and real-time OSes arise again. -

Cloud Computing 1. Is a Paradigm of Distribut
Practice Questions for TYBSc(Computer Science) –Sem 6 Subject : Cloud Computing 1. ________________ is a paradigm of distributed computing to provide the customers on- demand, utility based computing service. a) Remote Sensing b) Remote Invocation c) Cloud Computing d) Private Computing 2. These cloud services are of the form of utility computing i.e. the _________ uses these services pay-as-you-go model. a) Cloud providers b) Clients c) End users d) Cloud users 3. Which of the following is not a type of cloud? a) Private b) Public c) Protected d) Hybrid 4. Most of the cloud architectures are built on this type of architecture. a) skeleton b) grid c) linear d) template 5. Saas stands for? a) Software as a service b) System Software and services c) Software as a system d) System as a service 6. Hadoop is an example of _________ a) Saas b) PaaS c) IaaS d) Xaas 7. Grid and cloud platforms are regarded as a) Parallelized services b) Innovative services c) Utility services d) Software services 8. Utility computing focuses on a a) Business model b) Scalable model c) Cloud model d) Data model 9. A ________________________is a collection of independent computers that appears to its users as a single coherent system. a) distributed system b) parallel system c) operating system d) standalone system 10. A paradigm of multiple autonomous computers, having a private memory, communicating through a computer network is known as a) distributed system b) cloud computing c) centralized computing d) parallel computing 11. Which of these is not an example of Web2.0 application a) GoogleMaps b) Flickr c) de.li.cious d) vCloud 12.