Grid and Cloud Computing Subject Code
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Lynuxworks Lynxsecure Embedded Hypervisor and Separation
Operating systems: RTOS and tools Software LynuxWorks, Inc. 855 Embedded Way • San Jose, CA 95138 800-255-5969 www.lynuxworks.com LynxSecure Embedded Hypervisor and Separation Kernel With the introduction of the new LynxSecure separation kernel and embedded hypervisor, LynuxWorks once again raises the bar when it comes to superior embedded software security and safety. LynxSecure has been built from the ground up as a real-time separa- tion kernel able to run different operating systems and applications in their own secure partitions. The LynxSecure separation kernel is a virtual machine monitor that is certifi able to (a) Common Criteria EAL 7 (Evaluated Assurance Level 7) security certifi cation, a level of certifi cation unattained by any known operating system to date; and (b) DO-178B Level A, the highest level of FAA certifi cation for safety-critical avionics applications. LynxSecure conforms to the Multiple Independent Levels of Security/ Safety (MILS) architecture. The embedded hypervisor component of LynxSecure allows multiple “guest” operating systems to run in their own secure partitions. These can be run in either paravirtual- ized or fully virtualized modes, helping preserve legacy applications and operating systems in systems that now have a security require- FEATURES ment. Guest operating systems include the LynxOS family, Linux and › Optimal security and safety – the only operating system designed to Windows. support CC EAL 7 and DO-178B Level A › Real time – time-space partitioned RTOS for superior determinism and performance -

Cloud Computing Bible Is a Wide-Ranging and Complete Reference
A thorough, down-to-earth look Barrie Sosinsky Cloud Computing Barrie Sosinsky is a veteran computer book writer at cloud computing specializing in network systems, databases, design, development, The chance to lower IT costs makes cloud computing a and testing. Among his 35 technical books have been Wiley’s Networking hot topic, and it’s getting hotter all the time. If you want Bible and many others on operating a terra firma take on everything you should know about systems, Web topics, storage, and the cloud, this book is it. Starting with a clear definition of application software. He has written nearly 500 articles for computer what cloud computing is, why it is, and its pros and cons, magazines and Web sites. Cloud Cloud Computing Bible is a wide-ranging and complete reference. You’ll get thoroughly up to speed on cloud platforms, infrastructure, services and applications, security, and much more. Computing • Learn what cloud computing is and what it is not • Assess the value of cloud computing, including licensing models, ROI, and more • Understand abstraction, partitioning, virtualization, capacity planning, and various programming solutions • See how to use Google®, Amazon®, and Microsoft® Web services effectively ® ™ • Explore cloud communication methods — IM, Twitter , Google Buzz , Explore the cloud with Facebook®, and others • Discover how cloud services are changing mobile phones — and vice versa this complete guide Understand all platforms and technologies www.wiley.com/compbooks Shelving Category: Use Google, Amazon, or -

Developing Applications Using Platform-As-A-Service
Whitepaper Developing Applications using Platform-as-a-Service A Paradigm Shift in Application Development WOLF Frameworks Developing Applications using Platform-as-a-Service Contents Abstract ......................................................................................................................................................................3 Traditional Application Development ........................................................................................................................3 Client/Server Architecture ..........................................................................................................................................5 Service Oriented Architecture (SOA) ..........................................................................................................................5 Web Application development ...................................................................................................................................6 Advantages of Web Based Applications .....................................................................................................................7 Why Platform-as-a-Service? .......................................................................................................................................8 Difference between traditional application development and PaaS application development ................................8 Platform-as-a-Service Benefits ...................................................................................................................................9 -

(DBATU Iope) Question Bank (MCQ) Cloud Computing Elective II
Diploma in Computer Engineering (DBATU IoPE) Question Bank (MCQ) Cloud Computing Elective II (DCE3204A) Summer 2020 Exam (To be held in October 2020 - Online) Prepared by Prof. S.M. Sabale Head of Computer Engineering Institute of Petrochemical Engineering, Lonere Id 1 Question Following are the features of cloud computing: (CO1) A Reliability B Centralized computing C Location dependency D No need of internet connection Answer Marks 2 Unit I Id 2 Question Which is the property that enables a system to continue operating properly in the event of the failure of some of its components? (CO1) A Availability B Fault-tolerance C Scalability D System Security Answer Marks 2 Unit I Id 3 Question A _____________ is a contract between a network service provider and a customer that specifies, usually in measurable terms (QoS), what services the network service provider will furnish (CO1) A service-level agreement B service-level specifications C document D agreement Answer Marks 2 Unit I Id 4 Question The degree to which a system, subsystem, or equipment is in a specified operable and committable state at the start of a mission, when the mission is called for at an unknown time is called as _________ (CO1) A reliability B Scalability C Availability D system resilience Answer Marks 2 Unit I Id 5 Question Google Apps is an example of (CO1) A IaaS B SaaS C PaaS D Both PaaS and SaaS Answer Marks 2 Unit I Id 6 Question Separation of a personal computer desktop environment from a physical machine through the client server model of computing is known as __________. -

High-Assurance Separation Kernels: a Survey on Formal Methods
1 High-Assurance Separation Kernels: A Survey on Formal Methods Yongwang Zhao, Beihang University, China David Sanan´ , Nanyang Technological University, Singapore Fuyuan Zhang, Nanyang Technological University, Singapore Yang Liu, Nanyang Technological University, Singapore Separation kernels provide temporal/spatial separation and controlled information flow to their hosted applications. They are introduced to decouple the analysis of applications in partitions from the analysis of the kernel itself. More than 20 implementations of separation kernels have been developed and widely applied in critical domains, e.g., avionics/aerospace, military/defense, and medical devices. Formal methods are mandated by the security/safety certification of separation kernels and have been carried out since this concept emerged. However, this field lacks a survey to systematically study, compare, and analyze related work. On the other hand, high-assurance separation kernels by formal methods still face big challenges. In this paper, an analytical framework is first proposed to clarify the functionalities, implementations, properties and stan- dards, and formal methods application of separation kernels. Based on the proposed analytical framework, a taxonomy is designed according to formal methods application, functionalities, and properties of separation kernels. Research works in the literature are then categorized and overviewed by the taxonomy. In accordance with the analytical framework, a compre- hensive analysis and discussion of related work are presented. -

Cloud Computing in India: Challenges, Progress and Future
4 XII December 2016 www.ijraset.com Volume 4 Issue XII, December 2016 IC Value: 13.98 ISSN: 2321-9653 International Journal for Research in Applied Science & Engineering Technology (IJRASET) Cloud Computing in India: Challenges, Progress and Future Shraddha Kulkarni Computer Engineering – Third Year, LDRP-Institute of Research and Technology, KSV University, Gandhinagar, Gujarat Abstract— Cloud Computing is one of the emerging fields of Technologies in today's time. In the recent times, it has taken the usage of Internet to an all together different level. The concept of 'pay-for-what-you-use' makes it completely affordable and flexible. India, due to its huge and strong IT Industry has been one of the major markests for all the Cloud providers. This paper presents the current scenario of Cloud services in India, the steps taken for its advancement in the main working sector and where it stands compared to other countries. It also highlights the major points that hinder India from using this Technology which majorly includes the Privacy and Security issues. Citing the advantages, even the government has been taking steps to utilize the benefits of the Cloud in the country. Keywords— Gartner Report, Data privacy, Cybercrime, Internet connectivity, Meghraj, ERP. I. INTRODUCTION Cloud is an acronym of the phrase: Common, Location-independent, Online Utility that is available on Demand. Cloud Computing environment provides internet based platform which are used for computer Technology. Cloud computing collects all the computing resources and manages them automatically. With the advancement of Internet, the Concept of getting everything online arose. Realizing this need, the big companies like Amazon, Google and Microsoft came up with a model called “Cloud Computing”, which can be termed as a highly innovative concept of utilizing different Hardware and software services independent of any platform at reasonable rates without any kind of risk involved. -

Unit-1 Cloud Computing Virtualization Concepts
Unit-1 Cloud Computing Virtualization Concepts AVINAV PATHAK Assistant Professor Shobhit Institute of Engineering & Technology (Deemed-to-be-University), Meerut, India Virtualization Concept Virtualization is a technique, which allows to share single physical instance of an application or resource among multiple organizations or tenants (customers). It does so by assigning a logical name to a physical resource and providing a pointer to that physical resource on demand. Virtualization Concept Creating a virtual machine over existing operating system and hardware is referred as Hardware Virtualization. Virtual Machines provide an environment that is logically separated from the underlying hardware. The machine on which the virtual machine is created is known as host machine and virtual machine is referred as a guest machine. This virtual machine is managed by a software or firmware, which is known as hypervisor. Hypervisor The hypervisor is a firmware or low-level program that acts as a Virtual Machine Manager. There are two types of hypervisor: Type 1 hypervisor executes on bare system. LynxSecure, RTS Hypervisor, Oracle VM, Sun xVM Server, VirtualLogic VLX are examples of Type 1 hypervisor. The following diagram shows the Type 1 hypervisor. Virtualization Concept The type1 hypervisor does not have any host operating system because they are installed on a bare system. Type 2 hypervisor is a software interface that emulates the devices with which a system normally interacts. Containers, KVM, Microsoft Hyper V, VMWare Fusion, Virtual Server 2005 R2, Windows Virtual PC and VMWare workstation 6.0 are examples of Type 2 hypervisor. The following diagram shows the Type 2 hypervisor. Types of Hardware Virtualization Here are the three types of hardware virtualization: 1. -

Cloud Computing: a Detailed Relationship to Grid and Cluster Computing
International Journal of Future Computer and Communication, Vol. 4, No. 2, April 2015 Cloud Computing: A Detailed Relationship to Grid and Cluster Computing Ikechukwu Nwobodo premises and distributed computing perception, by providing Abstract—Cloud computing continues to maintain a rapid to users pool of computing resources in utility consumption growth while constituting a viable alternative to conventional forms accessible via internet on demand. The process of computing. Cloud computing is an emerging business cloud resource distribution and allocation makes it easier for computing model that enable users access to IT resources via enterprises to access and use cloud computing resources such internet infrastructure at any PC connected node across the globe without hardware constraints. Cloud computing concept as network, storage, and application servers without is a development trend based on several successful researches in requirement for huge upfront investment on infrastructure computing areas such as virtualization, grid computing, cluster provided, thereby strengthening or allowing concentration on computing and distributed computing. Cloud, cluster and grid other business critical development. Cloud computing computing share some common features towards achieving resources are dynamically accessed or requested on demand utility or service oriented computing although marginal without prior reservation and in essence helps to eliminate differences exist on their processes and approaches in many ways. This paper will be exploring the evolutionary issues of resource over-provisioning resulting to improved relationships in terms of features and component of cloud utilization of resources [2], [3]. computing technological innovation in comparison to cluster and grid computing. II. THREE MODELS OF COMPUTING Index Terms—Cloud computing, grid computing, cluster computing, utility computing. -

Continuing to Secure the Internet of Things
Safety & Security for the Connected World Continuing to secure the Internet of Things Connected embedded devices l Everything in our embedded world is becoming connected to – The Internet – Other connected devices – Personal devices l The information provided by these devices and the control of the devices is still vulnerable to cyber attacks – Cloud exploits – Embedded device compromise (e.g. Target attack) 2 Securing connected embedded devices l Security as an afterthought will have the same result as anti-virus and network security for protecting PCs l In the embedded world we have the opportunity to build security into our connected devices l Lynx Software Technologies continues to provide real-time products with built-in security 3 Security Technologies l LynxOS 7.0 offers military-grade security built into the RTOS Process 1 Process 2 l Connected embedded devices CPU CPU can be protected from Quota 1 Quota 2 Identification & Roles & traditional cyber attacks Authentication Capabilities Access Control Lists Residual – Network infiltration Information File System Audit Log Protection – Denial of Service attacks Device Hardware – Memory scraping – Password and authentication attacks • e.g. Root Escalation or “Rooting” the system 4 Security Technologies l LynxSecure offers isolation, separation and virtualization for multi-domain systems – Real-time performance and small footprint for real embedded deployments – Consolidation of hardware for efficient use of multi-core systems – Secure separation of networks, devices, operating systems -

A Robust Durability Process for Military Ground
2010 NDIA GROUND VEHICLE SYSTEMS ENGINEERING AND TECHNOLOGY SYMPOSIUM VEHICLE ELECTRONICS & ARCHITECTURE (VEA) MINI-SYMPOSIUM AUGUST 17-19 DEARBORN, MICHIGAN Software Virtualization in Ground Combat Vehicles Daniel McDowell John Norcross BAE Systems BAE Systems U.S. Combat Systems U.S. Combat Systems Minneapolis, MN Minneapolis, MN ABSTRACT Increased complexity of ground combat vehicles drives the need to support software applications from a broad variety of sources and seamlessly integrate them into a vehicle system. Traditionally, hosting GOTS and COTS applications required burdening a vehicle’s computing infrastructure with dedicated hardware tailored to specific processors and operating systems, heavily impacting the vehicles space, weight and power systems. Alternatively, porting the applications to the vehicles native computer systems is often cost prohibitive and error prone. Advancements in commercially developed software virtualization capabilities bring an entirely new approach for dealing with this challenge. Virtualization allows real-time and non-real-time applications running on different operating systems to operate seamlessly alongside each other on the same hardware. The benefits include reduced software porting costs and reduced qualification efforts. Additionally, elimination of specialized computing environments can produce significant gains in space, weight, power and cooling demands. INTRODUCTION The traditional approach used to consolidate and install all Ground combat vehicles are becoming increasingly more of -

Hype Cycle for Cloud Computing, 2011
Research Publication Date: 27 July 2011 ID Number: G00214915 Hype Cycle for Cloud Computing, 2011 David Mitchell Smith While clearly maturing, cloud computing continues to be the most hyped subject in IT today. We look at the different aspects of the topic and where they are on Gartner's Hype Cycle for Cloud Computing, 2011. © 2011 Gartner, Inc. and/or its affiliates. All rights reserved. Gartner is a registered trademark of Gartner, Inc. or its affiliates. This publication may not be reproduced or distributed in any form without Gartner's prior written permission. The information contained in this publication has been obtained from sources believed to be reliable. Gartner disclaims all warranties as to the accuracy, completeness or adequacy of such information and shall have no liability for errors, omissions or inadequacies in such information. This publication consists of the opinions of Gartner's research organization and should not be construed as statements of fact. The opinions expressed herein are subject to change without notice. Although Gartner research may include a discussion of related legal issues, Gartner does not provide legal advice or services and its research should not be construed or used as such. Gartner is a public company, and its shareholders may include firms and funds that have financial interests in entities covered in Gartner research. Gartner's Board of Directors may include senior managers of these firms or funds. Gartner research is produced independently by its research organization without input or influence from these firms, funds or their managers. For further information on the independence and integrity of Gartner research, see "Guiding Principles on Independence and Objectivity" on its website, http://www.gartner.com/technology/about/ombudsman/omb_guide2.jsp TABLE OF CONTENTS Analysis ...................................................................................................................................... -
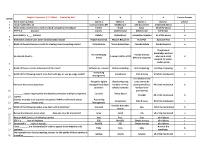
Cloud Computing MCQ.Xlsx
Chapter 1 Question 1, 2, 3 Mark Created by Atul a b c d Correct Answer SR.NO 1 Write down question Option a Option b Option c Option d a/b/c/d 2 Cloud model relies on communication API Middleware web documents embedded device a 3 What widely used service is built on cloud-computing technology? Twitter Skype Gmail All of the above d 4 HTTP is a ______ protocol stateful unidirectional bidirectional full dulpex b websocket is a____ Protocol stateful bidirectional connection oriented all of the above d 5 6 Websocket protocol uses which communication model Publish-Subscribe Request Response Push-Pull Exclusive Pair a Which of these techniques is vital for creating cloud-computing centers Virtualization Transubstantiation Cannibalization Insubordination a 7 The group of knowledge workers An overhanging A cloud that sits An internal cloud is… A career risk for a CIO who use a social d threat behind a corporate network for water- cooler gossip 8 Which of these is not an antecedent of the cloud? Software as a service Utility computing Grid computing Desktop computing d 9 Accounting Which of the following subject area deals with pay-as-you-go usage model? Compliance Data Privacy All of the mentioned a 10 Management The low barrier to Except for tightly Cloud computing entry cannot be Point out the correct statement managed SaaS cloud vendors run very accompanied by a All of the mentioned b providers reliable networks low barrier to 11 provisioning ________ captive requires that the cloud accommodate multiple compliance Licensed Policy-based Variable All of the mentioned b 12 regimes.