1. Introduction 1.1 the Background 1.2
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Technical Study Desktop Internationalization
Technical Study Desktop Internationalization NIC CH A E L T S T U D Y [This page intentionally left blank] X/Open Technical Study Desktop Internationalisation X/Open Company Ltd. December 1995, X/Open Company Limited All rights reserved. No part of this publication may be reproduced, stored in a retrieval system, or transmitted, in any form or by any means, electronic, mechanical, photocopying, recording or otherwise, without the prior permission of the copyright owners. X/Open Technical Study Desktop Internationalisation X/Open Document Number: E501 Published by X/Open Company Ltd., U.K. Any comments relating to the material contained in this document may be submitted to X/Open at: X/Open Company Limited Apex Plaza Forbury Road Reading Berkshire, RG1 1AX United Kingdom or by Electronic Mail to: [email protected] ii X/Open Technical Study (1995) Contents Chapter 1 Internationalisation.............................................................................. 1 1.1 Introduction ................................................................................................. 1 1.2 Character Sets and Encodings.................................................................. 2 1.3 The C Programming Language................................................................ 5 1.4 Internationalisation Support in POSIX .................................................. 6 1.5 Internationalisation Support in the X/Open CAE............................... 7 1.5.1 XPG4 Facilities......................................................................................... -

Videotex in Education: Current Developmentsin Screen Design
DOCUMENT .RESUME. ED 234 739 IR 010. 804 AUTHOR Kerr, Stephen-_T. TITLE Videotex in Education: Current Developmentsin Screen Design,. Data Structure, and Access Control. PUB DATE 15 Apr 83 37p.; Paper presented at the AnnualMeeting of the NOTE t American- Educational Research Association(Montrealc Canada; April 11-15, 1983). PUB TYPE Speeches/Conference Papers'(150) Information Analyses (070) -- Viewpoints (120) EDRS' PRICE MF01/PCO2 Plus Postage. DESCRIPTORS *Computer Graphics; Computer Science;*Design Requirements; Display Systems; Graphic Arts; Information Networks; *Information Retrieval; *Instructional Waterials;, Policy Formation;Privacy; *Videotex IDENTIFIERS *Access to Information; Electronic Publishing; Interactive Systems ABSTRACT This-four-section paper begins with a brief description of videotex and the pathsits development,has followed during its short lifespan. Thesecond_ section examines hoW videotex systems should present anddisplay information, and how such i'nformation should be internally organized sothat it is maximally useful for thefreader/user. Theanalysis, which draws heavily on work done during several videotex fieldtrials in the United States, Canada,' and other countries, incorpor4esinsights from.human factors studies of, video display terminals,research on typography and graphic display, and work on thedesign of interactive systems and computer help facilities. Thethird section addresses some, significant policy_issues that affectinstructional uses of videotex, including questions of equity, privacy, andsecrecy._ Finally, several possible future scenarios for the development ofvideotexas an instructional medium are discussed,, and the suggestionis made that. the convergence of videotex withother emerging technologies may result in novel arrangements for electronicpublishing and new qpportunities for. improvedinstructional design. Fifty-six references are listed. (LMM) *k***********************************v*************************w******, * Reproductions supplied by EDRS are the bestthat, can be made . -

Communications
50 Communications How Long the Wait until We Can Call It Television Jerry BORRELL: Congressional Research sharing service that provides more than Service, Library of Congress, Washington, 100 different (nonbibliographic) data bases D.C* to about 5,000 users. The Warner and American Express joint project, QUBE This brief article will review videotex (also Columbus-based), utilizes cable and teletext. There is little need to define broadcast with a limited interactive capa terminology because new hybrid systems bility. It does not allow for on-demand are being devised almost constantly (hats provision of information; rather, it uses a off to OCLC's latest buzzword-Viewtel). polling technique. Antiope, the French Ylost useful of all would be an examination teletext system, used at KSL in St. Louis of the types of technology being used for last year and undergoing further tests in information provision. The basic require Los Angeles at KNXT in the coming year, ment for all systems is a data base-i.e., is only part of a complex data transmission data stored so as to allow its retrieval and system known as DIDon. Antiope is also display on a television screen. The interac at an experimental stage in France, with tions between the computer and the tele 2,500 terminals scheduled for use in 1981. vision screens are means to distinguish CEEFAX and Oracle, broadcast teletext technologies. In teletext and videotex a by the BBC and IBC in Britain, have an device known as a decoder uses data en estimated 100,000 users currently. Two coded onto the lines of a broadcast signal thousand adapted television sets are being (whatever the medium of transmission) to sold every month. -

Public Strategies for the Information Society in the Member States of the European Union
Public Strategies for the Information Society in the Member States of the European Union A report prepared by Isabelle Chatrie and Paul Wraight, LL&A An ESIS report Information Society Activity Centre DG Information Society This version includes two additional contributions from the EFTA/EEA countries Norway and Iceland (November 2000) September 2000 The ESIS Project The Information Society Project Office (ISPO) at the European Commission set up a survey of European Information Society Projects and Actions in the 15 EU Member States called ESIS. This project ran for a period of two years between February 1997 and January 1999. It was further extended to 25 CEEC and Mediterranean countries and a continuation phase for Member States was implemented in 2000 with a narrower scope. This report on Public Strategies for the Information Society in the Member States of the European Union has been produced to provide up-to-date and relevant information that would support the existing reports and database on the web site. ESIS holds information on a broad range of commercial and publicly funded Information Society application projects in Europe. It aims to provide a tool for benchmarking, knowledge, communication, partnership and the promotion of best practice examples. Furthermore, it can serve as a navigation tool for all key actors and help in the promotion of the Information Society in Europe. More precisely, ESIS combines four categories of information: · An inventory of projects, which is the core of ESIS. Projects must use ICT in an innovative, interactive way and provide remote access. They may concern a large number of social and economic sectors and be initiated by national, regional, public and private organisations, or through partnerships set up between public and private groups. -

The French Videotex System Minitel: a Successful Implementation of a National Information Technology Infrastructure Author(S): William L
The French Videotex System Minitel: A Successful Implementation of a National Information Technology Infrastructure Author(s): William L. Cats-Baril and Tawfik Jelassi Source: MIS Quarterly, Vol. 18, No. 1 (Mar., 1994), pp. 1-20 Published by: Management Information Systems Research Center, University of Minnesota Stable URL: http://www.jstor.org/stable/249607 Accessed: 04/01/2010 13:20 Your use of the JSTOR archive indicates your acceptance of JSTOR's Terms and Conditions of Use, available at http://www.jstor.org/page/info/about/policies/terms.jsp. JSTOR's Terms and Conditions of Use provides, in part, that unless you have obtained prior permission, you may not download an entire issue of a journal or multiple copies of articles, and you may use content in the JSTOR archive only for your personal, non-commercial use. Please contact the publisher regarding any further use of this work. Publisher contact information may be obtained at http://www.jstor.org/action/showPublisher?publisherCode=misrc. Each copy of any part of a JSTOR transmission must contain the same copyright notice that appears on the screen or printed page of such transmission. JSTOR is a not-for-profit service that helps scholars, researchers, and students discover, use, and build upon a wide range of content in a trusted digital archive. We use information technology and tools to increase productivity and facilitate new forms of scholarship. For more information about JSTOR, please contact [email protected]. Management Information Systems Research Center, University of Minnesota is collaborating with JSTOR to digitize, preserve and extend access to MIS Quarterly. -

FOR an INFORMATION STRATEGY by Rene Mayer, Chairman Amoud De Kemp, Roberto Liscia, John Martyn, Jo
IMPACTll MID-TERM EVALUATION: FOR AN INFORMATION STRATEGY by Rene Mayer, Chairman Amoud de Kemp, Roberto Liscia, John Martyn, Joio Campos Rodrigues, Experts, Mogens Rasmussen, Rapporteur Report drawn up at the request of the Commission of the European Communities DGXIIIIE • IMPACTll MID-TERM EVALUATION: FOR AN INFORMATION STRATEGY by Rene Mayer, Chairman Amoud de Kemp, Roberto Liscia, John Martyn, Joio Campos Rodrigues, Experts, Mogens Rasmussen, Rapporteur Report drawn up at the request of the Commission of the European Communities DGXIIIIE - 1 - CONTENTS Page 5 I- A MUCH REDUCED PROGRAMME 6 1. Four correctly chosen action lines 9 2. A reduced budget applied to a field which is inherently contracting 11 3. Knowing the market: statistics and strategic studies 14 4. The LAB achieves an effective reconciliation of originally widely-differing legal approaches 15 5. But who is dealing with the other barriers? 22 6. Steering demand, increasing awareness, training, facilitating access : the role of ECHO, the NAPs and the focal points, etc. 28 7. Ensuring convergence between the vertical actions and the principal objectives 32 8. Improving awareness amongst senior national leaders 34 ll- IN A FAST-MOVING WORLD 34 1. Proliferation of products 37 2. The customer: a planetary entity a - the fall in the price of equipment b - limitless capacity c - planetary scope 42 3. From television to the computer, equipment is merging 43 4. From games to STI, from text to images: continuity of content 46 5. Links between methods 47 6. The concept of "meta-work" 49 7. Hyper-concentration of producers • -2- 53 m- THE ESSENTIALS OF A EUROPEAN STRATEGY 53 1. -

ETS 300 382 TELECOMMUNICATION February 1995 STANDARD
EUROPEAN ETS 300 382 TELECOMMUNICATION February 1995 STANDARD Source: ETSI TC-TE Reference: DE/TE-01016 ICS: 33.020, 33.040.40 Key words: Videotex, Man Machine Interface, VEMMI Terminal Equipment (TE); Videotex Enhanced Man Machine Interface service (VEMMI) ETSI European Telecommunications Standards Institute ETSI Secretariat Postal address: F-06921 Sophia Antipolis CEDEX - FRANCE Office address: 650 Route des Lucioles - Sophia Antipolis - Valbonne - FRANCE X.400: c=fr, a=atlas, p=etsi, s=secretariat - Internet: [email protected] Tel.: +33 92 94 42 00 - Fax: +33 93 65 47 16 Copyright Notification: No part may be reproduced except as authorized by written permission. The copyright and the foregoing restriction extend to reproduction in all media. New presentation - see History box © European Telecommunications Standards Institute 1995. All rights reserved. Page 2 ETS 300 382: February 1995 Whilst every care has been taken in the preparation and publication of this document, errors in content, typographical or otherwise, may occur. If you have comments concerning its accuracy, please write to "ETSI Editing and Committee Support Dept." at the address shown on the title page. Page 3 ETS 300 382: February 1995 Contents Foreword .......................................................................................................................................................9 1 Scope ................................................................................................................................................11 2 Normative -

Videotex/Teletext Presentation Level Protocol Syntax (North American PIPS) I
American Canadian National Adopted for Use by the Federal Government REFERENCE | NBS PUBLICATIONS r i(/. f 1 1 wS\3 No.121 1986 | North American PLPS i Government use. pederai d has been adopted l°'Fe " , Government are c0™e„,ation Level This standard within ,hc Federal ^^eUrie*■*.ca,ions available concerning 'ts . ds Publication . list the P . Processing Deta''S °n Processing Standards for a cornet the Standards Qf SSSCU-*- American <C !ri b Canadian National CL'UCX IJ A- Standards Standard Association .110-1983 T500-1983 NBS RESEARCH INFORMATION Videotex/Teletext CENTER Presentation Level Protocol Syntax North American PLPS Published in December, 1983 by American National Standards Institute, Inc. Canadian Standards Association 1430 Broadway 178 Rexdale Boulevard New York, NY 10018 Rexdale (Toronto), Ontario M9W 1R3 (Approved November 3, 1983) (Approved October 3, 1983) American National Standards and Canadian Standards Standards approved by the American National Standards Institute (ANSI) and the Canadian Standards Association (CSA) imply a consensus of those substantially concerned with their scope and provisions. These standards are intended as guides to aid the manufacturer, the consumer, and the general public. The existence of a standard does not in any respect preclude any of the above groups, whether they have approved the standard or not, from manufacturing, marketing, purchasing, or using products, processes, or procedures not conforming to the standard. These standards are subject to periodic review and users are cautioned to obtain the latest editions. In this standard, the words ''shall/' "should,” and "may" represent requirements, recommendations, and options, respectively, as specified in ANSI and CSA policy and style guides. -

Videotex in Europe Conference Proce!Edings
ORGANISED BY THE COMMISSION OF THE EUROPEAN COMMUNITIES Videotex in Europe Conference ProcE!edings Edited by Carlo Vernimb and William Skyvington With a preface by Georges Anderla Learned Information Oxford and New York Videotex in Europe I ' ; v· : -;:· Proceedings of th~ • ~ideotex 1n Europe ~ Conference Luxembourg 19-20 July 1979 Organ1sed by the COMMISSION OF THE EUROPEAN COMMUNITIES Edited by Carlo Vernimb and William Skyvington ' ~ ~ ~ With a preface by Georges Anderla (Learned Information 1980 Oxford and New York ', \\ ·J Videotex in Europe © ECSC, EEC, EAEC, Brussels and Luxembourg, 1980 All rights reserved ISBN 0 904933 22 9 Published by Learned Information (Europe) Ltd. Learned Information Besselsleigh Road The Anderson House Abingdon Stokes Road Oxford OX1 3 6 EF Medford, N.J. 08055 England U.S.A. (~co:Y) - tYI · (. :;r.,{ IV Contents Page PREFACE Mr. G. Anderla, Director - Information Management (CEC Directorate General XIII) v1i EDITORS' NOTE 1x OPENING OF THE CONFERENCE Mr. R.K. Appleyard, D1rector General- Sc1ent1f1c and Techn1callnformat1on and Information Management (CEC Directorate General XIII) INTRODUCTION TO THE STUDIES Mr. C. Vern1mb, Co-ordmator - New Information Technologies (CEC Directorate General XIII) 3 TERMINOLOGY 5 LECTURE: "Videotex Development in the Community" Mr. M. Kohn, (Telesystemes, Pans) 7 TEXT: "Videotex/Euronet Compatibility" [summanzed extracts from the study report] (Telesystemes, Pans) 22 LECTURE: "Videotex Development outside the Community" Mr. R. Woolfe (Butler, Cox & Partners, London) 44 DISCUSSION - Session No. 1 51 LECTURE: "Videotex Market in the Community" Mr. H.D. Scholz (Pactel, Frankfurt) 63 TEXT: "Videotex Market and Display Study" [summaned extracts from the study report] (PA Management Consultants, Frankfurt) 75 LECTURE: "Market for Videotex Business Terminals" Mr. -
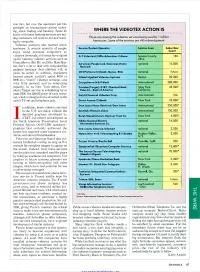
WHERE the VIDEOTEX ACTION IS Price-The Rest of the Industry Will
vice mix, but now the operators put the spotlight on transactions-airline ticket- ing, stock trading and banking. Some 40 WHERE THE VIDEOTEX ACTION IS banks with home banking services are bet- ting customers will want to do their bank- These are among the videotex services being used by 1 million ing by computer. Americans. Some of the services are still in develcpment. Videotex pioneers also learned about hardware: A certain minority of people Service/System Operator Service Area Subscribe enjoy using personal computers as Count videotex terminals, and many have signed A -T Videotext/Tiffin Advertiser-Tribune Seneca County, 150 up for national videotex services such as Ohio Mrs. Mass CompuServe. But Mr. and Mar- American People Link/American Home national 16,000 ket don't want to deal with computerlike Network gadgets (perhaps their children will, in years to come). In addition, marketers CNt Partners/Citibank, Nynex, RCA national future learned people wouldn't spend $600 or Citiret/Applied Videotex Systems Boston 20,000 $900 on a "dumb" videotex terminal-one with little memory and no computing CompuServe/H & R Block international 280,000 capacity. In its New York debut, Cov- Coridea (Target)/AT&T, Chemical Bank, New York, 45,000- idea's Target service is subsidizing by at Time Inc., Bank of America California least $100 the $49.95 price of each termi- Del 3hi/General Videotex Corp. international NA nal, which is designed to be attached to the user's TV set and telephone jack. Direct Access/Citibank New York 22,000' Dow Jones News-Retrieval/Dow Jones international 250,000' n addition, home videotex services in the U.S. -

International Register of Coded Character Sets to Be Used with Escape Sequences for Information Interchange in Data Processing
INTERNATIONAL REGISTER OF CODED CHARACTER SETS TO BE USED WITH ESCAPE SEQUENCES 1 Introduction 1.1 General This document is the ISO International Register of Coded Character Sets To Be Used With Escape Sequences for information interchange in data processing. It is compiled in accordance with the provisions of ISO/IEC 2022, "Code Extension Technique" and of ISO 2375 "Procedure for Registration of Escape Sequences". This International Register contains coded character sets which have been registered in accordance with procedures given in ISO 2375. Its purpose is to identify widely used coded character sets and associate with each a unique escape sequence by means of which it can be designated according to ISO/IEC 2022 and ISO/IEC 4873. The publication of this International Register should promote compatibility in international information interchange and avoid duplication of effort in developing application-oriented coded character sets. Registration provides an identification for a coded character set but implies nothing about its status; it may or may not be part of a standard of an international, national or a corporate body. However, if such a standard is published subsequently to the registration, it would be appropriate for the escape sequence identifying the character set to be specified in the standard. If it is desired to register a set, application should be made to the Registration Authority through an appropriate Sponsoring Authority as specified in ISO 2375. Any character set can be a candidate for registration if it meets the requirements of ISO 2375. The Registration Authority ascertains that the proposals received are formally in accordance with this International Standard, technically in accordance with ISO/IEC 2022, and, where applicable, with ISO/IEC 646 and ISO/IEC 4873, and meet the presentation practice of the Registration Authority. -

Lof Ormatiestromen En Gegevensbanken M De Parlementaire Werkzaamheden
loformatiestromen en gegevensbanken m de parlementaire werkzaamheden door Louis V ANVEL THOVEN Voorzitter van de Vlaamse Raad "Een paar eeuwen geleden kon een wetenschapsmens nog beweren dat hij een ruime kennis had van zijn vak. De dag van heden is het zelfs voor specialisten in een bepaalde discipline niet meer mogelijk de evolutie op de voet te volgen. Wanneer een arts b.v. alle ontwikkelingen op medisch gebied zou willen kennen, dan zou 1 procent van deze informatie hem 5 uur lectuur per dag kosten. Gelukkig bestaat ook voor hem de computer. .. ". Zo luidt de inleiding van een artikel dat mij onder de titel "Kennis is nu nog meer macht" in een presentatienummer van EOS, een magazine voor wetenschap en technologie, onder ogen viel. Uiteraard maakte ik hierbij de associatie met de allegorie van F-16's en tweedekkers, die ik destijds heb gemaakt om het hemels brede verschil inzake toegang tot de informatie tussen de uitvoerende en de wet gevende macht aan de kaak te stellen. Bedenk daarbij dat de uitvoerende zowel als de wetgevende macht regelgevend moeten optreden in de brede waaier van materies die Staat, volk en burger aanbelangen. Vergeleken bij de arts, zou een politiek mandataris met 24 uur lectuur per dag nog tekort schieten. Als oplossing voor het probleem van de toegang tot de informatie en de daaruit voortvloeiende kenniswerving, wordt de computer steevast als een "deus ex ma china" naar voren geschoven. Met hem wordt de mens van een zwaar juk bevrijd en krijgt hij moeiteloos toegang tot de tuin van kennis en wetenschappen.