Department of Electronics And
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Liberty Latin America Completes Split-Off from Liberty Global
Liberty Latin America Completes Split-Off from Liberty Global Newly listed company well-positioned to leverage world-class technology, innovation and scale Value creation strategy to stem from both organic and inorganic opportunities Denver, Colorado – January 2, 2018 Liberty Latin America Ltd. (NASDAQ: LILA and LILAK, OTC Link: LILAB) (“Liberty Latin America”), a leading telecommunications company with operations in Chile, Puerto Rico, the Caribbean and other parts of Latin America, today announced the completion of its previously announced split-off from Liberty Global plc (“Liberty Global”) and its launch as an independent, publicly-traded company. Following the successful completion of the split-off, Liberty Latin America Class A and Class C common shares are now trading on the NASDAQ Global Select Market under the symbols “LILA” and “LILAK,” respectively, and the Class B common shares are quoted on the OTC Markets under the symbol “LILAB”. Mike Fries, Executive Chairman of Liberty Latin America and CEO of Liberty Global, commented, “The split-off of our Latin American and Caribbean operations from Liberty Global will ensure that this new company will have access to the capital and resources necessary to achieve superior financial and strategic growth. I have tremendous confidence in Balan Nair’s leadership as well as the world-class board of directors and management team we have put in place. As Liberty Latin America charts its own course going forward, it will continue to benefit from its Liberty Global heritage and will have access to key shared services and expertise across products, technology, procurement and more. The launch of Liberty Latin America is an exciting moment for all shareholders and a clear confirmation of the opportunity for value creation in the Latin American and Caribbean region.” Balan Nair, President and Chief Executive Officer of Liberty Latin America, stated, “Today marks an important milestone for Liberty Latin America as we begin the path forward as an independent company focused squarely on the region. -

BGP Interconnection in the Region of Latin America and the Caribbean
BGP Interconnection in the Region of Latin America and the Caribbean Author: Augusto Mathurín Coordination/Revision: Guillermo Cicileo Edition and Design: Maria Gayo, Carolina Badano, Martín Mañana Project: Strengthening Regional Internet Infrastructure Department: Internet Infrastructure R&D Contents Contents 2 Introduction 4 Methodology 4 Stated Objectives 4 Data Sources 4 Data Processing 6 Generated Datasets 8 Data by Country 10 Argentina 10 Aruba 12 Bolivia 13 Brazil 15 Belize 17 Chile 19 Colombia 21 Costa Rica 23 Cuba 25 Dominican Republic 27 Ecuador 29 French Guiana 31 Guatemala 32 Guyana 34 Honduras 36 Haiti 38 Mexico 40 Nicaragua 42 Panama 44 2 Peru 46 Paraguay 48 Suriname 50 El Salvador 52 Trinidad and Tobago 54 Uruguay 56 Venezuela 58 Regional Data Analysis 60 Connection to the Other Regions 62 Conclusions and Future Work 65 3 Introduction Internet development and the quality of user connectivity depend on the existence of good communications infrastructure and proper connectivity between countries. In Latin America, there are still some deficiencies in this regard which result in many people experiencing high latencies in their connections. The main reason for these latencies is the lack of local interconnection between different network operators, which means that traffic between nearby countries must often use distant Internet exchange points, located in the United States or Europe. The deployment of various Internet exchange points (IXPs) has helped improve this situation, although the actual status of connectivity between countries and networks remains a mystery. To find answers to these unknowns, some time ago LACNIC created Simón1, a project that seeks to generate information by measuring latency levels between countries and in this way estimate traffic volumes. -

LUH Clears 6 Kms Altitude Flight
www.aeromag.in n January - February 2019 | Vol 13 | Issue 1 LUH Clears 6 KMs Altitude Flight World’s Largest Importer, in association with Yet Indian Armed Forces Society of Indian Aerospace Technologies & Industries Need to be Better Equipped - Page 14 Official Media Partner Feb 20 - 24, 2019. Yelahanka Air Force Station, Bangalore Advertise with AEROMAG Show Dailies 1 Total Air and Missile Defense Sky Capture BARAK 8 - Naval-based BARAK 8 - Land-based ARROW 2 - Anti-Ballistic ARROW 3 - Anti-Ballistic Air & Missile Defense Air & Missile Defense Missile Defense Missile Defense Full Spectrum of Integrated, Networked Meet us at AERO INDIA 2019 Air and Missile Defense Solutions to Defeat Hall B: B2.1, B2.2 Threats at Any Range and Altitude IAI offers a comprehensive range of Air and Missile Defense Systems for land and naval applications. From VSHORAD to long-range, to theater and exo-atmospheric systems against ballistic missiles. Our unique solutions, based on lessons derived from vast operational experience, incorporate state-of-the-art technology and full networking for the most effective System of Systems. The result: IAI’s solutions. www.iai.co.il • [email protected] 2 Total Air and Missile Defense Advertise with Official Show Dailies of AEROMAG AEROMAG OFFICIAL MEDIA PARTNER Sky Capture BARAK 8 - Naval-based BARAK 8 - Land-based ARROW 2 - Anti-Ballistic ARROW 3 - Anti-Ballistic Air & Missile Defense Air & Missile Defense Missile Defense Missile Defense Full Spectrum of Integrated, Networked Meet us at AERO INDIA 2019 AERO INDIA 2019 Air and Missile Defense Solutions to Defeat Hall B: B2.1, B2.2 Threats at Any Range and Altitude 20-24 FEBRUARY, BENGALURU IAI offers a comprehensive range of Air and Missile Defense Systems for land and naval applications. -

Ministry of Defence
21 STANDING COMMITTEE ON DEFENCE (2015-2016) (SIXTEENTH LOK SABHA) MINISTRY OF DEFENCE DEMANDS FOR GRANTS (2016-17) MINISTRY OF DEFENCE (MISCELLANEOUS) (DEMAND NO. 20) TWENTY-FIRST REPORT LOK SABHA SECRETARIAT NEW DELHI May, 2016/ Vaisakha, 1938 (Saka) 1 TWENTY-FIRST REPORT STANDING COMMITTEE ON DEFENCE (2015-2016) (SIXTEENTH LOK SABHA) MINISTRY OF DEFENCE DEMANDS FOR GRANTS (2016-2017) (MISCELLANEOUS) (DEMAND NO. 20) Presented to Lok Sabha on 03.05.2016 Laid in Rajya Sabha on 03.05.2016 LOK SABHA SECRETARIAT NEW DELHI May, 2016/ Vaisakha, 1938 (Saka) 2 CONTENTS Composition of the Committee (2015-16)………………………………………. Introduction ………………….……………………………………………………… PART - I Chapter I Ordnance Factory Board……………………...……………….….. Chapter II Defence Research and Development Organization …………… Chapter III Ex- Servicemen Contributory Health Scheme …………………. Chapter IV Directorate General Quality Assurance ……. …………………. Chapter V National Cadet Corps …………………………..…………………. PART – II OBSERVATIONS/RECOMMENDATIONS........................................... ANNEXURE ………………………………………………………….……... APPENDICES Minutes of the sitting of the Committee on Defence held on 4.4.2016, 5.4.2016, 6.04.2016 and 29.04.2016…………………………………………………………… 3 COMPOSITION OF THE STANDING COMMITTEE ON DEFENCE (2015-16) Maj Gen B C Khanduri, AVSM (Retd) - Chairperson Members Lok Sabha 2. Shri Suresh C. Angadi 3. Shri Shrirang Appa Barne 4. Shri Dharambir 5. Shri Thupstan Chhewang 6. Col Sonaram Choudhary(Retd) 7. Shri H.D. Devegowda 8. Shri Sher Singh Ghubaya 9. Shri G. Hari 10. Shri Ramesh Jigajinagi 11. Dr. Murli Manohar Joshi 12. Km. Shobha Karandlaje 13. Shri Vinod Khanna 14. Dr. Mriganka Mahato 15. Shri Tapas Paul 16. Shri Ch. Malla Reddy 17. Shri Rajeev Satav 18. Smt. Mala Rajya Lakshmi Shah 19. Capt Amarinder Singh(Retd) 20. -

Vtr Finance Bv
VTR FINANCE B.V. Annual Report December 31, 2018 VTR FINANCE B.V. Boeing Avenue 53 1119 PE Schiphol-Rijk The Netherlands VTR FINANCE B.V. TABLE OF CONTENTS Page Number Forward-looking Statements 2 Business 4 Management and Governance 13 Independent Auditors’ Report 15 Consolidated Balance Sheets as of December 31, 2018 and 2017 16 Consolidated Statements of Operations for the Years Ended December 31, 2018, 2017 and 2016 18 Consolidated Statements of Comprehensive Earnings (Loss) for the Years Ended December 31, 2018, 2017 and 2016 19 Consolidated Statements of Owner’s Deficit for the Years Ended December 31, 2018, 2017 and 2016 20 Consolidated Statements of Cash Flows for the Years Ended December 31, 2018, 2017 and 2016 21 Notes to Consolidated Financial Statements 23 Management’s Discussion and Analysis of Financial Condition and Results of Operations 46 1 FORWARD-LOOKING STATEMENTS Certain statements in this annual report constitute forward-looking statements. To the extent that statements in this annual report are not recitations of historical fact, such statements constitute forward-looking statements, which, by definition, involve risks and uncertainties that could cause actual results to differ materially from those expressed or implied by such statements. In particular, statements under Business and Management’s Discussion and Analysis of Financial Condition and Results of Operations may contain forward-looking statements, including our business, product, service offering, foreign currency and finance strategies in 2019; our property -

Engineering the Motivo Way Praveen Penmetsa’S U.S.-Based Team Develops Unique Mobility Solutions
MOBILITY ENGINEERINGTM ENGLISH QUARTERLY Vol : 5 Issue : 2 April - June 2018 Free Distribution Engineering the Motivo Way Praveen Penmetsa’s U.S.-based team develops unique mobility solutions New-age stationary power Developing Mazda’s drones for SpCCI engine passenger transport ready for production ME Altair Ad 0618.qxp_Mobility FP 3/29/18 2:49 PM Page 1 CONTENTS Features 30 Roadmap for future Indian 46 Developing an alternative engine passenger drone sector concept COMMERCIAL VEHICLE PROPULSION AEROSPACE AUTONOMY Ricardo’s CryoPower engine leverages two unique combustion techniques for reduced emissions and fuel consumption—liquid nitrogen and split combustion. 32 Internet of Vehicles: connected Long-haul trucking and stationary power generation will vehicles & data - driven solutions be the first beneficiaries of the technologies. AUTOMOTIVE CONNECTIVITY 49 Spark of genius AUTOMOTIVE PROPULSION 34 Development and verification of Mazda’s Skyactiv-X—the nexus of gasoline and diesel electronic braking system ECU tech—remains on track for 2019 production. We test-drive software for commercial vehicle recent prototypes to check development status. COMMERCIAL VEHICLE CHASSIS 52 Plain bearings for aerospace 42 Engineering the Motivo Way applications AEROSPACE MATERIALS AUTOMOTIVE ENGINEERING Broad capabilities, unparalleled project diversity and an innovative culture have put this thriving California “idea factory” in high demand. Cover Sway Motorsports’ three- wheeled electric motorcycle leans into a curve thanks to a suspension design developed -
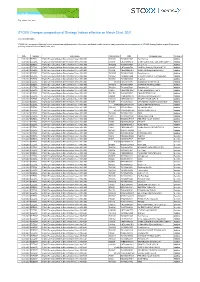
STOXX Changes Composition of Strategy Indices Effective on March 22Nd, 2021
Zug, March 13th, 2021 STOXX Changes composition of Strategy Indices effective on March 22nd, 2021 Dear Sir and Madam, STOXX Ltd., the operator of Qontigo’s index business and a global provider of innovative and tradable index concepts, today announced the new composition of STOXX Strategy Indices as part of the regular quarterly review effective on March 22nd, 2021 Date Symbol Index name Internal Key ISIN Company name Changes 12.03.2021 EDEDSL STOXX Emerging Markets Diversification Select 100 USD TW01UK TW0001722007 Twn Fertilizer Addition 12.03.2021 EDEDSL STOXX Emerging Markets Diversification Select 100 USD CN0010 CNE1000002H1 CHINA CONSTRUCTION BANK CORP H Addition 12.03.2021 EDEDSL STOXX Emerging Markets Diversification Select 100 USD TW02MD TW0002301009 Liteon Tech Addition 12.03.2021 EDEDSL STOXX Emerging Markets Diversification Select 100 USD CN249E CNE000000T59 YANTAI CHANGYU PION.WINE 'B' Addition 12.03.2021 EDEDSL STOXX Emerging Markets Diversification Select 100 USD CN1I6O CNE100000HF9 CHINA MINSHENG BANKING H Addition 12.03.2021 EDEDSL STOXX Emerging Markets Diversification Select 100 USD TW025W TW0002015005 Feng Hsin Iron Addition 12.03.2021 EDEDSL STOXX Emerging Markets Diversification Select 100 USD TW505Z TW0006412000 CHICONY POWER TECHNOLOGY Addition 12.03.2021 EDEDSL STOXX Emerging Markets Diversification Select 100 USD TW0751 TW0004938006 Pegatron Addition 12.03.2021 EDEDSL STOXX Emerging Markets Diversification Select 100 USD 691316 HK0270001396 Guangdong Investment Ltd. Addition 12.03.2021 EDEDSL STOXX Emerging Markets -

BIZAV in EUROPE - TRENDING RNI NUMBER: DELENG/2008/24199 UPWARDPAGE 18 the Best-Selling Business Aircraft in History
SP’s AN SP GUIDE PUBLICATION r only) E y U d b SE a-ba I 100.00 (Ind ` Aviation Sharp Content for Sharp Audience www.sps-aviation.com vol 17 ISSUE 5 • may • 2014 LAST WORD SEEN HERE IS BOMBardier’s CHALLENGER 300 WHICH IS LIKELY TO Bizav in India, BE ONE OF THE MANY BUSINESS JETS DISPLAYED AT EBACE 2014 INSPIRE. ALSO: • IAF AND DASSAULT - A JOURNEY OF RELATIONSHIP • INDIA’S UAV PROGRAMMES - LONG FLIGHT EBACE • WE SUPPORT 2014: A Preview INDIA’S INDIGENOUS PROGRAMMES —Uday Yadav, ABACE PRESIDENT, Aerospace 2014: A Report GROUP, Eaton BIZAV IN EUROPE - TRENDING RNI NUMBER: DELENG/2008/24199 UPWARDPAGE 18 The best-selling business aircraft in history. King Air 250. The King Air 200 series has outsold every other line of business aircraft—including turboprops and jets. The King Air 250 builds on the legacy with an outstanding combination of systems redundancy, speed and fuel effi ciency. Not to mention luxury. Its larger cabin with leather club seating and premium appointments lets you conduct business comfortably and effi ciently. For more information, contact: Manju Singhal +91.99719.77666 | Sanjeev Choudhary +91.99582.00918 Visit us at Beechcraft.com ©2014 Beechcraft Corporation. All rights reserved. Beechcraft and King Air are the registered trademarks of Beechcraft Corporation. Beech140679 KA 250 SP Aviation India_March.indd 2 3/7/14 2:45 PM BAILEY LAUERMAN Beechcraft KA 250_SP Aviation India March Beech140679 Pub: SP Aviation India March Color: 4-color Size: Trim 210mm (w) x 267mm (h), Bleed 220mm (w) x 277mm (h) table of contents vol 17 ISSUE 5 • May • 2014 SP’s AN SP GUIDE PUBLICATION 100.00 (INDIA-BASED BUYER ONLY) BUYER 100.00 (INDIA-BASED ` Aviation Sharp Content for Sharp Audience www.sps-aviation.com VOL 17 ISSUE 5 • MAY • 2014 LAST WORD SEEN HERE IS BOMBARDIER’S CHALLENGER 300 WHICH IS LIKELY TO Bizav in India, BE ONE OF THE MANY BUSINESS JETS DISPLAYED AT EBACE 2014 INSPIRE. -

SUPER Current Affairs MCQ PDF 6Th March 2021
SUPER Current Affairs MCQ PDF 6th March 2021 By Dream Big Institution: (SUPER Current Affairs) © Q. NPCI has launched the RuPay SoftPoS in collaboration with which company for merchants? A) PayPal India C) Paytm B) SBI Payments D) HDFC Bank Answer: B National Payments Corporation of India (NPCI) and SBI Payments have partnered to launch “RuPay SoftPoS” for Indian merchants. RuPay SoftPoS will enable merchants to use their near-field communication (NFC)- enabled smartphones as point of sale (PoS) terminals and accept payment up to Rs 5,000 through a simple tap and pay mechanism. SBI Cards & Payment Services Ltd: CEO: Ashwini Kumar Tewari Headquarters: Gurugram Founded: 1998 Revenue: 7,286.84 crores INR (US$1.0 billion, 2018–2019) Parent organizations: State Bank of India, The Carlyle Group Chairpersons: Dinesh Kumar Khara, Rajnish Kumar NPCI in Nems: NPCI Partners SBI Payments to launch “RuPay SoftPoS” for Merchants Central Bank of India ties up with NPCI to launche ‘RuPay Select’ Contactless Debit Card NPCI imposes 30% cap on transaction volumes via UPI for third party apps About NPCI: Page 1 Follow us: Official Site, Telegram, Facebook, Instagram, Instamojo Headquarters location: Mumbai Founded: 2008 Type of business: Section 8 Company Founders: Reserve Bank of India, Indian Banks' Association About RuPay: Owner: National Payments Corporation of India Introduced: 8 May 2014; 6 years ago Tagline: ONE LIFE. ONE RuPay Q. As per the State of India’s Environment 2021 Report, the COVID-19 pandemic will leave ___ million children with health impacts. a) 325 c) 375 b) 350 d) 400 Answer: C As per the State of India’s Environment 2021 Report, the ongoing COVID-19 pandemic will leave around 375 million children with long term health impacts. -

Ready Awarded It to Operators by the End of 2016, Whereas Mexico Has Already Allocated 90 Mhz of That Band to Those in Charge of Deploying the Shared Network
TABLE OF CONTENTS TABLE OF CONTENTS ............................................................................................................ 2 EXECUTIVE SUMMARY ........................................................................................................... 3 INTRODUCTION ...................................................................................................................... 6 ITU MOBILE SPECTRUM SUGGESTIONS .............................................................................. 8 ITU RECOMMENDATIONS: SPECTRUM ALLOCATION FOR THE DEVELOPMENT OF IMT AND IMT-ADVANCED TECHNOLOGIES .............................................................................. 9 LATIN AMERICA SPECTRUM OVERVIEW ............................................................................ 10 FUTURE OF THE RADIO SPECTRUM IN LATIN AMERICA ................................................... 12 CHALLENGES TO AWARD THE RADIO SPECTRUM ............................................................ 15 CONCLUSION ........................................................................................................................ 16 APPENDIX A: LATIN AMERICA MARKETS PROFILES ......................................................... 18 ARGENTINA ....................................................................................................................... 18 BOLIVIA ............................................................................................................................. 18 BRAZIL .............................................................................................................................. -

VTR Finance 2020 Annual Bank Report
VTR FINANCE N.V. Annual Report December 31, 2020 VTR FINANCE N.V. Boeing Avenue 53 1119 PE Schiphol-Rijk The Netherlands VTR FINANCE N.V. TABLE OF CONTENTS Page Number Forward-looking Statements....................................................................................................................................... 2 Business...................................................................................................................................................................... 4 Management and Governance..................................................................................................................................... 16 Management’s Discussion and Analysis of Financial Condition and Results of Operations..................................... 18 Consolidated Financial Statements Independent Auditors’ Report............................................................................................................................... 33 Consolidated Balance Sheets as of December 31, 2020 and 2019......................................................................... 34 Consolidated Statements of Operations for the Years Ended December 31, 2020, 2019 and 2018...................... 36 Consolidated Statements of Comprehensive Earnings (Loss) for the Years Ended December 31, 2020, 2019 and 2018.............................................................................................................................................................. 37 Consolidated Statements of Owner’s Equity (Deficit) -

VTR Finance Q4 2017 Bank Report
VTR FINANCE B.V. Annual Report December 31, 2017 VTR FINANCE B.V. Boeing Avenue 53 1119 PE Schiphol-Rijk The Netherlands VTR FINANCE B.V. TABLE OF CONTENTS Page Number Forward-looking Statements....................................................................................................................................... 2 Business ...................................................................................................................................................................... 4 Management and Governance .................................................................................................................................... 13 Independent Auditors’ Report..................................................................................................................................... 15 Consolidated Balance Sheets as of December 31, 2017 and 2016............................................................................. 16 Consolidated Statements of Operations for the Years Ended December 31, 2017, 2016 and 2015........................... 18 Consolidated Statements of Comprehensive Earnings (Loss) for the Years Ended December 31, 2017, 2016 and 2015......................................................................................................................................................................... 19 Consolidated Statements of Owner’s Deficit for the Years Ended December 31, 2017, 2016 and 2015................... 20 Consolidated Statements of Cash Flows for the Years Ended December