Technology Mapping for Vlsi Circuits Exploiting Boolean Properties and Operations
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-
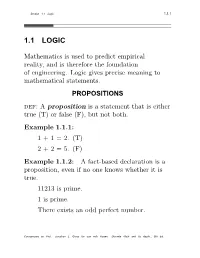
1.1 Logic 1.1.1
Section 1.1 Logic 1.1.1 1.1 LOGIC Mathematics is used to predict empirical reality, and is therefore the foundation of engineering. Logic gives precise meaning to mathematical statements. PROPOSITIONS def: A proposition is a statement that is either true (T) or false (F), but not both. Example 1.1.1: 1+1=2.(T) 2+2=5.(F) Example 1.1.2: A fact-based declaration is a proposition, even if no one knows whether it is true. 11213 is prime. 1isprime. There exists an odd perfect number. Coursenotes by Prof. Jonathan L. Gross for use with Rosen: Discrete Math and Its Applic., 5th Ed. Chapter 1 FOUNDATIONS 1.1.2 Example 1.1.3: Logical analysis of rhetoric begins with the modeling of fact-based natural language declarations by propositions. Portland is the capital of Oregon. Columbia University was founded in 1754 by Romulus and Remus. If 2+2 = 5, then you are the pope. (a conditional fact-based declaration). Example 1.1.4: A statement cannot be true or false unless it is declarative. This excludes commands and questions. Go directly to jail. What time is it? Example 1.1.5: Declarations about semantic tokens of non-constant value are NOT proposi- tions. x+2=5. Coursenotes by Prof. Jonathan L. Gross for use with Rosen: Discrete Math and Its Applic., 5th Ed. Section 1.1 Logic 1.1.3 TRUTH TABLES def: The boolean domain is the set {T,F}. Either of its elements is called a boolean value. An n-tuple (p1,...,pn)ofboolean values is called a boolean n-tuple. -

Exclusive Or from Wikipedia, the Free Encyclopedia
New features Log in / create account Article Discussion Read Edit View history Exclusive or From Wikipedia, the free encyclopedia "XOR" redirects here. For other uses, see XOR (disambiguation), XOR gate. Navigation "Either or" redirects here. For Kierkegaard's philosophical work, see Either/Or. Main page The logical operation exclusive disjunction, also called exclusive or (symbolized XOR, EOR, Contents EXOR, ⊻ or ⊕, pronounced either / ks / or /z /), is a type of logical disjunction on two Featured content operands that results in a value of true if exactly one of the operands has a value of true.[1] A Current events simple way to state this is "one or the other but not both." Random article Donate Put differently, exclusive disjunction is a logical operation on two logical values, typically the values of two propositions, that produces a value of true only in cases where the truth value of the operands differ. Interaction Contents About Wikipedia Venn diagram of Community portal 1 Truth table Recent changes 2 Equivalencies, elimination, and introduction but not is Contact Wikipedia 3 Relation to modern algebra Help 4 Exclusive “or” in natural language 5 Alternative symbols Toolbox 6 Properties 6.1 Associativity and commutativity What links here 6.2 Other properties Related changes 7 Computer science Upload file 7.1 Bitwise operation Special pages 8 See also Permanent link 9 Notes Cite this page 10 External links 4, 2010 November Print/export Truth table on [edit] archived The truth table of (also written as or ) is as follows: Venn diagram of Create a book 08-17094 Download as PDF No. -

Boolean.Py Documentation Release 3.2
boolean.py Documentation Release 3.2 Sebastian Krämer Aug 06, 2018 Contents 1 User Guide 1 1.1 Introduction...............................................1 1.2 Installation................................................2 1.3 Creating boolean expressions......................................2 1.4 Evaluation of expressions........................................2 1.5 Equality of expressions..........................................3 1.6 Analyzing a boolean expression.....................................4 1.7 Using boolean.py to define your own boolean algebra.........................5 2 Concepts and Definitions 7 2.1 Basic Definitions.............................................7 2.2 Laws...................................................9 3 Development Guide 13 3.1 Testing.................................................. 13 3.2 Classes Hierarchy............................................ 14 3.3 Class creation............................................... 14 3.4 Class initialization............................................ 14 3.5 Ordering................................................. 14 3.6 Parsing.................................................. 15 4 Acknowledgments 17 i ii CHAPTER 1 User Guide This document provides an introduction on boolean.py usage. It requires that you are already familiar with Python and know a little bit about boolean algebra. All definitions and laws are stated in Concepts and Definitions. Contents • User Guide – Introduction – Installation – Creating boolean expressions – Evaluation of expressions – Equality -

Further Improvements in the Boolean Domain
Further Improvements in the Boolean Domain Further Improvements in the Boolean Domain Edited by Bernd Steinbach Further Improvements in the Boolean Domain Edited by Bernd Steinbach This book first published 2018 Cambridge Scholars Publishing Lady Stephenson Library, Newcastle upon Tyne, NE6 2PA, UK British Library Cataloguing in Publication Data A catalogue record for this book is available from the British Library Copyright © 2018 by Bernd Steinbach and contributors All rights for this book reserved. No part of this book may be reproduced, stored in a retrieval system, or transmitted, in any form or by any means, electronic, mechanical, photocopying, recording or otherwise, without the prior permission of the copyright owner. ISBN (10): 1-5275-0371-2 ISBN (13): 978-1-5275-0371-7 Contents List of Figures ............................................ xi List of Tables .............................................. xv Foreword ................................................... xix Preface ..................................................... xxiii Acknowledgments . .xxxiii List of Abbreviations . .xxxvii I Extensions in Theory and Computations 1 1 Models, Methods, and Techniques ................... 3 1.1 NP-Problems and Boolean Equations . 3 1.1.1 Classes of Hard Problems . 3 1.1.2 Boolean Functions and Equations . 4 1.1.3 Boolean Equations and Ternary Vectors . 5 1.1.4 NP-Complete Problems . 9 1.1.5 Boolean Equations - a Unifying Instrument . 24 1.2 Number of Variables of Index Generation Functions . 25 1.2.1 Background . 25 1.2.2 An Index Generation Unit . 26 1.2.3 Notation . 27 1.2.4 Expected Number of Variables . 29 1.2.5 Distribution of the Expected Number . 31 1.2.6 Expected Number of Balanced Columns . 38 1.2.7 Found Results . -

Spectral Methods for Boolean and Multiple-Valued Input Logic Functions
Portland State University PDXScholar Dissertations and Theses Dissertations and Theses 1991 Spectral Methods for Boolean and Multiple-Valued Input Logic Functions Bogdan Jaroslaw Falkowski Portland State University Let us know how access to this document benefits ouy . Follow this and additional works at: http://pdxscholar.library.pdx.edu/open_access_etds Recommended Citation Falkowski, Bogdan Jaroslaw, "Spectral Methods for Boolean and Multiple-Valued Input Logic Functions" (1991). Dissertations and Theses. Paper 1152. 10.15760/etd.1151 This Dissertation is brought to you for free and open access. It has been accepted for inclusion in Dissertations and Theses by an authorized administrator of PDXScholar. For more information, please contact [email protected]. SPECTRAL METHODS FOR BOOLEAN AND MULTIPLE-VALUED INPUT LOGIC F&-ICTIONS by BOGDAN JAROSLAW FALKOWSKI A disseitation submitted in partial fulfillment ofthe requirements for the degree of DOcrOR OF PHILOSOPHY in ELECTRICAL AND COMPUTER ENGINEERING Portland State University 1991 AN ABSTRACT OF THE DISSERTATION OF Bogdan Jaroslaw Falkowski for the Doctor of Philosophy in Electrical and Computer Engineering presented May 2, 1991. Title: Spectra! Methods for Boolean and Multiple-Valued Input Logic Functions. Jack12. Riley ,/ ; .~ / E. Balogh Spectral techniques in digital logic design have been known for more than thirty years. They have been used for Boolean function classification, disjoint decomposition, parallel and serial linear decomposition, spectral translation synthesis (extraction of 2 linear pre- and post-filters), multiplexer synthesis, prime implicant extraction by spectral summation, threshold logic synthesis, estimation of logic complexity, testing, and state assignment. This dissertation resolves many important issues concerning the efficient applica tion of spectral methods used in the computer-aided design of digital circuits. -
UCLA Electronic Theses and Dissertations
UCLA UCLA Electronic Theses and Dissertations Title Modeling, Learning and Reasoning with Structured Bayesian Networks Permalink https://escholarship.org/uc/item/7ns0f906 Author Shen, Yujia Publication Date 2020 Peer reviewed|Thesis/dissertation eScholarship.org Powered by the California Digital Library University of California UNIVERSITY OF CALIFORNIA Los Angeles Modeling, Learning and Reasoning with Structured Bayesian Networks A dissertation submitted in partial satisfaction of the requirements for the degree Doctor of Philosophy in Computer Science by Yujia Shen 2020 © Copyright by Yujia Shen 2020 ABSTRACT OF THE DISSERTATION Modeling, Learning and Reasoning with Structured Bayesian Networks by Yujia Shen Doctor of Philosophy in Computer Science University of California, Los Angeles, 2020 Professor Adnan Youssef Darwiche, Chair Probabilistic graphical models, e.g. Bayesian Networks, have been traditionally intro- duced to model and reason with uncertainty. A graph structure is crafted to capture knowl- edge of conditional independence relationships among random variables, which can enhance the computational complexity of reasoning. To generate such a graph, one sometimes has to provide vast and detailed knowledge about how variables interacts, which may not be readily available. In some cases, although a graph structure can be obtained from available knowledge, it can be too dense to be useful computationally. In this dissertation, we propose a new type of probabilistic graphical models called a Structured Bayesian network (SBN) that requires less detailed knowledge about conditional independences. The new model can also leverage other types of knowledge, including logical constraints and conditional indepen- dencies that are not visible in the graph structure. Using SBNs, different types of knowledge act in harmony to facilitate reasoning and learning from a stochastic world. -

1.1 Logic 1.1.1
Section 1.1 Logic 1.1.1 1.1 LOGIC Mathematics is used to predict empirical reality, and is therefore the foundation of engineering. Logic gives precise meaning to mathematical statements. PROPOSITIONS def: A proposition is a statement that is either true (T) or false (F), but not both. Example 1.1.1: 1 + 1 = 2. (T) 2 + 2 = 5. (F) Example 1.1.2: A fact-based declaration is a proposition, even if no one knows whether it is true. 11213 is prime. 1 is prime. There exists an odd perfect number. Coursenotes by Prof. Jonathan L. Gross for use with Rosen: Discrete Math and Its Applic., 5th Ed. Chapter 1 FOUNDATIONS 1.1.2 Example 1.1.3: Logical analysis of rhetoric begins with the modeling of fact-based natural language declarations by propositions. Portland is the capital of Oregon. Columbia University was founded in 1754 by Romulus and Remus. If 2+2 = 5, then you are the pope. (a conditional fact-based declaration). Example 1.1.4: A statement cannot be true or false unless it is declarative. This excludes commands and questions. Go directly to jail. What time is it? Example 1.1.5: Declarations about semantic tokens of non-constant value are NOT proposi- tions. x + 2 = 5. Coursenotes by Prof. Jonathan L. Gross for use with Rosen: Discrete Math and Its Applic., 5th Ed. Section 1.1 Logic 1.1.3 TRUTH TABLES def: The boolean domain is the set {T,F }. Either of its elements is called a boolean value. An n-tuple (p1, . -

Discrete Mathematics
Discrete Mathematics Haluk Bingol February 21, 2012 ii Contents I Preliminaries 1 1 Preliminaries 3 1.1 Motivation............................. 3 1.2 Ondefinitions........................... 3 1.3 Similarstatements ........................ 5 1.4 SetofNumbers .......................... 6 II Basics 7 2 Logic 9 2.1 Motivation............................. 9 2.2 Foundations ............................ 10 2.2.1 Well-formedformula . 10 2.2.2 LogicalAxioms . .. 11 2.2.3 RulesofInference. 11 2.2.4 Equality .......................... 12 2.3 PropositionalLogic . 12 2.3.1 CompoundPropositions . 12 2.3.2 Application ........................ 15 2.4 PropositionalEquivalence . 16 3 Sets, Relations, and Functions 21 3.1 Set................................. 21 3.1.1 Sets ............................ 21 3.1.2 SetOperations ...................... 24 3.2 Relation .............................. 26 3.2.1 CompositionofRelations. 27 iii iv CONTENTS 3.3 Functions ............................. 28 3.4 Problems.............................. 33 4 Relations on a Set 37 4.1 RelationsonaSet......................... 37 4.2 ObservationsontheMatrixofaRelation . 38 4.3 ClosureofRelations . .. .. 39 4.4 CompatibilityRelation . 39 4.4.1 Application of Compatibility Relation . 41 4.5 EquivalenceRelation . 42 4.5.1 Applications of Equivalence Relations . 43 4.6 Problems.............................. 45 5 Partial Ordering, Lattice 47 5.1 PartialOrdering.......................... 47 5.2 HasseDiagram .......................... 48 5.3 Lattice............................... 50 5.4 -

Updates and Boolean Universals
Updates and Boolean Universals Fausto Carcassi1,* and Giorgio Sbardolini1,* 1Institute for Logic, Language and Computation; Universiteit van Amsterdam *Co-first authors. Abstract Languages across the world have simple lexical terms that convey Boolean opera- tors, such as conjunction and disjunction. Of the many logically possible operators of this kind, only three are in fact attested: and, or, nor. Moreover, there are patterns in the way they co-occur in lexical inventories, e.g. nor is not observed by itself. In this paper, we develop a proposal to explain the occurrence of lexical inventories in natural language based on previous work in update semantics. We present a bilat- eral extension of standard update semantics, which allows to calculate how linguistic information can be accepted in a context but also rejected. Boolean operators are en- coded as particular forms of update, on the basis of which we define a cognitively plausible measure of conceptual simplicity. We show that the attested operators are conceptually simpler than the remaining Booleans. Moreover, we show that the pat- terns in co-occurrence of Boolean operators can be explained by balancing conceptual simplicity and simplicity of using the language. Our perspective reveals a way that formal and cognitive constraints on dynamic aspects of the use of sentences may have contributed to shaping language evolution. 1 Introduction English and expresses Boolean conjunction: the compound ‘p and q’ is true just in case p and q are both true. Assuming two truth values, True and False, there are 16 Boolean truth functions of two arguments, like conjunction. However, only few of them are expressed in natural language by lexical primitives. -

A Categorial Semantic Representation of Quantum Event Structures
Found Phys DOI 10.1007/s10701-013-9733-5 A Categorial Semantic Representation of Quantum Event Structures Elias Zafiris · Vassilios Karakostas Received: 23 May 2012 / Accepted: 16 July 2013 © Springer Science+Business Media New York 2013 Abstract The overwhelming majority of the attempts in exploring the problems re- lated to quantum logical structures and their interpretation have been based on an underlying set-theoretic syntactic language. We propose a transition in the involved syntactic language to tackle these problems from the set-theoretic to the category- theoretic mode, together with a study of the consequent semantic transition in the logical interpretation of quantum event structures. In the present work, this is real- ized by representing categorically the global structure of a quantum algebra of events (or propositions) in terms of sheaves of local Boolean frames forming Boolean lo- calization functors. The category of sheaves is a topos providing the possibility of applying the powerful logical classification methodology of topos theory with refer- ence to the quantum world. In particular, we show that the topos-theoretic represen- tation scheme of quantum event algebras by means of Boolean localization functors incorporates an object of truth values, which constitutes the appropriate tool for the definition of quantum truth-value assignments to propositions describing the behav- ior of quantum systems. Effectively, this scheme induces a revised realist account of truth in the quantum domain of discourse. We also include an Appendix, where we compare our topos-theoretic representation scheme of quantum event algebras with other categorial and topos-theoretic approaches. Keywords Quantum event structures · Boolean algebras · Topos subobject classifier · Kochen-Specker theorem · Quantum truth values · Adjoint functors · Sheaves · Grothendieck topos · Realist account E. -

Boolean Functions and Degree of Approximation
Lecture 9: Boolean functions and degree of approximation Rajat Mittal IIT Kanpur A Boolean function is a function from the domain f0; 1gn to Boolean domain f0; 1g for some n. In other words, f : f0; 1gn ! f0; 1g is called a Boolean function. We will look at larger range, i.e., f : f0; 1gn ! R. In these notes, all such functions will be called Boolean functions. The domain can be switched to f : n 1−x {−1; 1g ! R by the simple linear transform 2 (we will mostly use this domain for Boolean functions). These functions are of fundamental importance in many areas of computer science like chip/circuit design, logic, cryptography and complexity theory. As a student of computer science, you must already be familiar with gates like AND, OR and NOT . A familiar result is that any Boolean function can be computed using NAND gate (it is universal). Our focus will be on the representation of Boolean functions as polynomials. We will first see that every Boolean function can be represented as a polynomial. Then, we will define various measures of complexity of such functions. It turns out that one very important measure, approximate degree, can be modeled as a linear program. Finally, we will derive an explicit lower bound on the approximate degree of OR function using linear programming techniques. You might have seen Boolean functions defined from f0; 1gn to f0; 1g. For the equivalence between these two representations, map 0 with 1 and 1 with −1. Exercise 1. Why don't we identify 1 with 1 and 0 with −1? 1 Representing Boolean functions The easiest way to specify a Boolean function is by its truth table. -

Categorical Foundations of Quantum Logics and Their Truth Values Structures
Categorical Foundations of Quantum Logics and Their Truth Values Structures ELIAS ZAFIRIS University of Athens Institute of Mathematics Panepistimiopolis, 15784 Athens Greece Abstract We introduce a foundational sheaf theoretical scheme for the com- prehension of quantum event structures, in terms of localization sys- tems consisting of Boolean coordinatization coverings induced by mea- surement. The scheme is based on the existence of a categorical ad- junction between presheaves of Boolean event algebras and Quantum event algebras. On the basis of this adjoint correspondence we prove the existence of an object of truth values in the category of quantum logics, characterized as subobject classifier. This classifying object plays the equivalent role that the two-valued Boolean truth values object plays in classical event structures. We construct the object of quantum truth values explicitly and argue that it constitutes the appropriate choice for the valuation of propositions describing the be- havior of quantum systems. arXiv:quant-ph/0402174v1 24 Feb 2004 0E-mail : ezafi[email protected] 1 1 Prologue The notion of the logic of a physical theory has been introduced in 1936 by von Neumann and G. Birkhoff in a paper entitled The Logic of Quantum Mechanics. For classical theories the appropriate logic is a Boolean algebra; but for quantum theories a non-Boolean logical structure is necessary, which can be an orthocomplemented lattice, or a partial Boolean algebra, or some other structure of a related form. The logic of a physical theory reflects the structure of the propositions describing the behavior of a physical system in the domain of the corresponding theory.