Interdisciplinary Approaches to Cyber Security for Organisations
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Kent Academic Repository Kent Academic Repository Full Text Document (Pdf)
View metadata, citation and similar papers at core.ac.uk brought to you by CORE provided by Kent Academic Repository Kent Academic Repository Full text document (pdf) Citation for published version Vadean, Florin and Randazzo, Teresa and Piracha, Matloob (2017) Remittances, Labour Supply and Activity of Household Members Left-Behind. Journal of Development Studies . ISSN 0022-0388. DOI https://doi.org/10.1080/00220388.2017.1404031 Link to record in KAR http://kar.kent.ac.uk/64218/ Document Version Author's Accepted Manuscript Copyright & reuse Content in the Kent Academic Repository is made available for research purposes. Unless otherwise stated all content is protected by copyright and in the absence of an open licence (eg Creative Commons), permissions for further reuse of content should be sought from the publisher, author or other copyright holder. Versions of research The version in the Kent Academic Repository may differ from the final published version. Users are advised to check http://kar.kent.ac.uk for the status of the paper. Users should always cite the published version of record. Enquiries For any further enquiries regarding the licence status of this document, please contact: [email protected] If you believe this document infringes copyright then please contact the KAR admin team with the take-down information provided at http://kar.kent.ac.uk/contact.html Remittances, Labour Supply and Activity of Household Members Left-Behind† Florin Vadean PSSRU, University of Kent, Canterbury, UK Teresa Randazzo Department -

Cv Cantore.Pdf
Cristiano Cantore Research Hub E-mail: [email protected] Bank of England E-mail: [email protected] Threadneedle Street Web: http://www.cristianocantore.com London EC2R 8AH Phone: +44 (0)2034614469 Fields of Business Cycle Theory, Monetary and Fiscal Policy, Applied Macroeconomics Interest Current Research Advisor, Research Hub, Bank of England. 07/2021 to date Employment Reader in Economics (Part-Time), University of Surrey, Guildford. 08/2018 to date Other Centre for Macroeconomics (LSE), Euro Area Business Cycle Network, Central Bank Affiliations Research Association and Centre for International Macroeconomics (Surrey). Education Ph.D. in Economics University of Kent, (passed without corrections). 2011 Dissertation Examiners: Prof. M. Ellison (Oxford), Dr. K.Shibayama (Kent). M.Sc. in Economics, Pompeu Fabra University, Barcelona. 2005 B.A. in Economics and Statistics, L. Bocconi University, Milan. 2004 Previous Senior Research Economist, Research Hub, Bank of England. 09/2018 to 06/2021 Positions Senior Lecturer in Economics, University of Surrey, Guildford. 04/2013 to 07/2018 Visiting Professor, University of California San Diego. 02/2014 to 07/2014 Visiting Research Fellow, Banco de España, Madrid. 04/2012 to 08/2012 Lecturer in Economics, University of Surrey, Guildford. 09/2009 to 03/2013 Visiting Professor, University of Cagliari. 01/2012 to 02/2012 Intern, European Central Bank, Economics DG. 08/2008 to 10/2008 Intern, OECD, Economic Department, Country desk 1. 07/2007 to 09/2007 Publications (2021) Workers, Capitalists, and the Government: Fiscal Policy and Income (Re)Distribution, joint with Lukas Freund (University of Cambridge). Journal of Monetary Economics, 119, 58-74. -

Oxford Brookes University Access and Participation Plan
Oxford Brookes University Access and Participation Plan 2020-21 to 2024-25 1. Assessment of performance Unless stated otherwise, the analyses in this report draw on data from UK-domiciled, undergraduate students studying full-time or sandwich courses at Oxford Brookes University and at our Associate College Partnerships. Where possible we have referenced national higher education data sources supplemented with internal data. Unless otherwise stated the data sources by life cycle stage are as follows: ● Applicant data are from UCAS end of cycle reports, from UCAS Undergraduate reports by sex, area background, and ethnic group, or from purchased UCAS EXACT data. ● Entrant, Continuation, Attainment and Progression data are from the OfS Access and Participation data resources. ● National data, including that from HESA, UCAS and TEF metrics, were used for sector benchmarks. ● Regional population data is derived from the Local Authority. Additional analysis has been undertaken on the relative performance of Oxford Brookes students registered through the University’s Associate College Partnerships. This analysis has shown some gaps in performance against the data for the average of ACPs, which has led to the initiation of discussions with college partners to pinpoint where gaps are significant and to work with partners to better understand the data and to develop action plans to address differences in access, success and progression. Summary of performance Underrepresented Access Success - Continuation Success - Attainment Progression group -

The New and the Old: the University of Kent at Canterbury” Krishan Kumar
1 For: Jill Pellew and Miles Taylor (eds.), The Utopian Universities: A Global History of the New Campuses of the 1960s “The New and the Old: The University of Kent at Canterbury” Krishan Kumar Foundations and New Formations1 It all began with a name. A new university was to be founded in the county of Kent.2 Where to put it? In the end, the overwhelming preference was for the ancient cathedral city of Canterbury. But that choice of site was by no means uncontested. There was no lack of alternatives. Ashford, Dover, and Folkestone all put in bids. The Isle of Thanet in East Kent was for some time a strong contender, and its large seaside town of Margate, with its many holiday homes, undoubtedly seemed a better prospect than Canterbury for the provision of student accommodation, in the early years at least. Ramsgate too, with a large disused airport, was another strongly- urged site in Thanet. But as far back as 1947, Canterbury had been proposed as the site of a new university in the county. That proposal got nowhere, but the idea that Canterbury – rather than say Maidstone, the county capital, or anywhere else in Kent – should be the place where and when a new university was founded had caught the imagination of many in the county. Thanet might, from a practical point of view, have been the better site. But it lacked the cultural significance and the wealth of historical associations of the city of Canterbury. Moreover the University of Thanet, or the University of Margate or Ramsgate, did not have quite the same ring to it as the University of Kent or the University of Canterbury.3 That at least was the strong opinion of the two bodies that brought the University into being, the Steering Committee of Kent County Council and the group of the great and the good in the county that came together as “Sponsors of the University of Kent”- most prominent among them being its chairman, Lord Cornwallis, Lord Lieutenant of Kent and former chairman of Kent County Council.4 2 Canterbury having been chosen as the site, what to call the new foundation? That proved trickier. -

University of Kent Accommodation Living Cost Loan Maximum Amounts for 2019/20
The UK’s European university STUDENT FINANCE/ THE COSTS INVOLVED AND HOW TO APPLY Loans Support availableWhat support is available? Extra support Introduction We will cover: • the costs involved • funding your studies • applying for financial support • Repayment • managing your money What makes up your student finance? Tuition Fee Loan Additional Living cost loan support Student Finance Scholarships and Bursaries Costs and financial support available Tuition fee loan • Available from the UK government to cover Kent’s tuition fee the cost of fees 2020/21 • All UK (home) students are eligible to apply TBC for the full loan • The loan is paid directly to the university, 2019/20 not to you £9,250 Living cost loan (maintenance loan) for new UK and EU • Available from the UK government to help entrants with living costs • The amount you get depends on where you live and study • The loan is paid into your bank account each term Costs and financial support available Living costs Your living costs include accommodation, food, travel, socialising, and clubs and societies Living cost loan • Available from the government to help with living costs • All full-time students who have resided in the UK for a continuous length of five years are eligible to apply for the loan • All eligible students are entitled to some of the loan, the rest is assessed on household income (means tested) • The loan is paid to you each term Living costs Estimated living costs Cost for a typical academic Weekly cost (first year) year From To From To Accommodation* £119.14 £193.41 £4,646.46 £7,542.99 Books and materials £15.00 £20.00 £585 £780 Food £40.00 £70.00 £1,560 £2,730 Clothes/Laundry £15.00 £45.00 £585 £1,755 Personal items £5.00 £10.00 £195 £390 Socialising (inc. -

College and University Acceptances
COLLEGE AND UNIVERSITY ACCEPTANCES 2016 -2020 UNITED KINGDOM • University of Bristol • High Point University • Aberystwyth University • University of Cardiff • Hofstra University • Arts University Bournemouth • University of Central Lancashire • Ithaca College • Aston University • University of East Anglia • Lesley University • Bath Spa University • University of East London • Long Island University - CW Post • Birkbeck University of London • University of Dundee • Loyola Marymount University • Bornemouth University • University of Edinburgh • Loyola University Chicago • Bristol, UWE • University of Essex • Loyola University Maryland • Brunel University London • University of Exeter • Lynn University • Cardiff University • University of Glasgow • Marist College • City and Guilds of London Art School • University of Gloucestershire • McGill University • City University of London • University of Greenwich • Miami University • Durham University • University of Kent • Michigan State University • Goldsmiths, University of London • University of Lancaster • Missouri Western State University • Greenwich School of Management • University of Leeds • New York Institute of Technology • Keele University • University of Lincoln • New York University • King’s College London • University of Liverpool • Northeastern University • Imperial College London • University of Loughborough • Oxford College of Emory University • Imperial College London - Faculty of Medicine • University of Manchester • Pennsylvania State University • International School for Screen -
Choosing Course Modules at the University of Kent
Choosing Course Modules at the University of Kent Once you have been accepted by SPU, we will send your application to the University of Kent. At Kent, your application will be reviewed and approved by the different faculties (departments) and you will be accepted to a faculty according to your major or general area of study. Kent must have your course selections before they are able to accept you. You may view Kent’s online module catalog here: http://www.kent.ac.uk/courses/modulecatalogue/ How to choose Modules: When you click on a module title, a page will open with many details about the course. You must make sure to follow these guidelines: 1) Location: Choose Canterbury. You will not be taking courses at the Medway campus. 2) Term: Must say "Autumn". You can't take courses that say "Autumn and Spring" as these are yearlong courses. Obviously you won't choose "Spring" either! 3) Level: There are three levels of courses 1,2,3. "Certificate" are first level courses and are a good way to explore a new area of study. "Intermediate" and "higher" are upper division courses. You may select from any level. 4) Credits: You MUST take a total of 60 credits. Modules are either 15 or 30 credits each depending on the intensity of the course. So, you might end up with four 15-credit modules, two 30-credit, etc. If you see this: “Credits (ECTS): 30 (15)” the course is worth 30 credits not 15. The number in parenthesis is not applicable to you. -

Autism, Creativity and Aesthetics
Open Research Online The Open University’s repository of research publications and other research outputs Autism, Creativity and Aesthetics Journal Item How to cite: Roth, Ilona (2018). Autism, Creativity and Aesthetics. Qualitative Research in Psychology, 17(4) pp. 498–508. For guidance on citations see FAQs. c 2018 Taylor Francis https://creativecommons.org/licenses/by-nc-nd/4.0/ Version: Accepted Manuscript Link(s) to article on publisher’s website: http://dx.doi.org/doi:10.1080/14780887.2018.1442763 Copyright and Moral Rights for the articles on this site are retained by the individual authors and/or other copyright owners. For more information on Open Research Online’s data policy on reuse of materials please consult the policies page. oro.open.ac.uk 1 Autism, Creativity and Aesthetics Ilona Roth Affiliation Dr Ilona Roth, BA (Hons), DPhil, BA (Hons) Hum (Open), CPsychol, AFBPsS Senior Lecturer in Psychology, School of Life, Health and Chemical Sciences, The Open University Contact details School of Life, Health and Chemical Sciences, STEM Faculty, The Open University, Walton Hall, Milton Keynes, MK 7 6AA, United Kingdom [email protected] Biographical note Ilona Roth is Senior Lecturer in Psychology, School of Life Health and Chemical Sciences, The Open University. With background in cognitive psychology, she has teaching and research specialisms in autism. Roth’s longstanding personal and professional interest in the arts led her recently to complete a degree in Humanities and Romance languages. She is author of film, multi-media and written material on autism, including Roth et.al. (2010) ‘The Autism Spectrum in the 21st Century: Exploring Psychology, Biology and Practice’. -

Christian Siegel
June 2021 CHRISTIAN SIEGEL School of Economics, University of Kent, Canterbury, CT2 7FS, United Kingdom; Email: [email protected] Current Appointments Since Oct 2017 Senior Lecturer, and from October 2021 Reader, in Economics, University of Kent, UK Since Dec 2019 CEPR Research Affiliate (Macroeconomics and Growth programme) Since Feb 2020 Deputy Director of Macroeconomics, Growth and History Centre, University of Kent Since Nov 2019 Co-lead of Centre for Productivity and Workplace Performance, University of Kent Since Oct 2019 Fellow of the Global Labor Organization (GLO) Since Nov 2018 Fellow of the Research Centre for Education and the Labour Market (ROA), Maastricht Education Aug 2009–Dec 2012 PhD in Economics, London School of Economics and Political Science (LSE), UK Sep 2007–Jul 2009 MRes in Economics, LSE Sep 2005–May 2006 Visiting Graduate Student in Economics, University of Toronto, Canada Oct 2002–Feb 2007 Diplom Economics (Volkswirtschaftslehre), University of Mannheim, Germany Former Academic Work Experience Oct 2016–Sep 2017 Lecturer in Economics, University of Kent Sep 2012–Sep 2016 Lecturer in Economics, University of Exeter, UK Sep 2011–Aug 2012 Fellow, Department of Economics, LSE Jun 2008–Dec 2010 Occasional Research Assistant at the Centre for Economic Performance, LSE Oct 2008–Jun 2011 Graduate Teaching Assistant, LSE Jun 2006–Aug 2007 Research Assistant, Mannheim Research Institute for the Economics of Ageing (MEA) Oct 2005–Apr 2006 Teaching Assistant, University of Toronto Oct 2003–Jul 2005 Student Teaching Assistant, University of Mannheim Teaching Qualifications Since January 2016 Fellow of the Higher Education Academy December 2015 ASPIRE Fellowship, University of Exeter November 2015 Postgraduate Certificate of Academic Practice (PCAP), University of Exeter Publications in Journals (peer-reviewed) ‘Make Yourselves Scarce: The Effect of Demographic Change on the Relative Wages and Employment Rates of Experienced Workers’ (with Michael Böhm), March 2021, International Economic Review, forthcoming. -

Medieval and Early Modern Studies Summer Festival
#MEMSFest19 MEDIEVAL AND EARLY MODERN STUDIES SUMMER FESTIVAL 14 - 15 June 2019 University of Kent, Canterbury 1 #MEMSFest19 #MEMSFest19 Welcome! Hello, and a very warm welcome to the University of Kent for the 2019 MEMS Summer Festival. We are delighted to welcome both new and returning attendees to the Festival, which promises to be full of stimulating papers and workshops. Should you have any questions or need assistance during the Festival, please do not hesitate to speak to a member of the organising committee. This is the University of Kent’s fifth annual MEMS Summer Festival. This two-day event celebrates Medieval and Early Modern history, with speakers’ topics ranging from 800 - 1850. These include politics, religion, economics, art, drama, literature, material culture, from countries spanning the globe. MEMS Fest is an informal space where postgraduate students, early career researchers, and academics can share their ideas in a friendly community. Undergraduate students in their final year of study are also welcome at the conference to network with other academics in their field of research. Travel Bursary Awards This year, the MEMS Festival offered travel bursaries for speakers selected to present papers at the Festival. These awards would not be possible without the generous support of the Centre for Medieval and Early Modern Studies, the School of History and the School of English, at the University of Kent, and the Consortium for the Humanities and the Arts South-East England (CHASE). Social Media We encourage you to connect with us and your fellow Festival-goers online during and beyond this year’s MEMS Fest. -

Trade Marks Group Trade Mark Group
Trade Marks Group Trade Mark Group Roberto Calamita Professional Experience Partner and Roberto joined the firm in 1985 and became a Partner in 1996. He handles both patent and trade mark matters and is Head of Group the Head of the firm’s Trade Marks Group. Email [email protected] Tel +44 (0)20 7632 7200 Roberto has substantial trade mark experience and has a client base covering a range of commercial areas, including chemistry, pharmaceuticals, engineering, lighting, clothing Education and fashion, publishing and media, telecommunications MA, University of Oxford, Natural Sciences (Chemistry), 1985 and financial services. He is listed in the “Managing Intellectual Property Guide to the World’s Leading Trade Mark Professional Qualifications Practitioners”. European Patent Attorney, 1991 UK Registered Trade Mark Attorney, 1991 In relation to patent matters, Roberto prosecutes patent UK Registered Patent Attorney, 1992 applications in all areas of chemistry, with particular Professional Representative before OHIM, 1995 emphasis on materials, polymers and alloys. Membership of Professional Bodies Fellow of the Chartered Institute of Patent Attorneys Institute of Trade Mark Attorneys European Communities Trademark Association International Trademark Association European Patent Institute Michael Butler Professional Experience Partner Mike Butler joined the firm in 1973 and qualified as a patent Email [email protected] attorney in 1977, winning the Gill Prize. He became a Partner in 1980. Having lived in Oxfordshire since 1982, he was one Tel +44 (0)20 7632 7200 of the founders of the Oxford office in 2002 and is based there principally, working for SME’s and universities in the region in addition to his other national and international clients. -
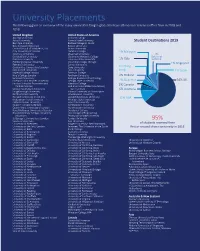
University Placements the Following Gives an Overview of the Many Universities Tanglin Graduates Have Attended Or Received Offers from in 2018 and 2019
University Placements The following gives an overview of the many universities Tanglin graduates have attended or received offers from in 2018 and 2019. United Kingdom United States of America Abertay University Amherst College Aston University Arizona State University Student Destinations 2019 Bath Spa University Berklee College of Music Bournemouth University Boston University Central School of St Martin’s, UAL Brown University City, University of London Carleton College 1% Malaysia Coventry University Chapman University 7% De Montfort University Claremont McKenna College National Durham University Colorado State University 1% Italy Service Edinburgh Napier University Columbia College, Chicago Falmouth University Cornell University 1% Singapore Goldsmiths, University of London Duke University 1% Hong Heriot-Watt University Elon University Kong 1% Spain Imperial College London Emerson College King’s College London Fordham University 2% Holland Lancaster University Georgia Institute of Technology Liverpool John Moores University Georgia State University 4% Gap Year 64% UK London School of Economics and Hamilton College Political Science Hult International Business School, 2% Canada London South Bank University San Francisco 6% Australia Loughborough University Indiana University at Bloomington Northumbria University John Hopkins University Norwich University of the Arts Loyola Marymount University 11% USA Nottingham Trent University Michigan State University Oxford Brookes University New York University Queen’s University Belfast Northeastern