Openoffice / Opendocument and MS Office 2007 / Open XML Security
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Administering CRM 2015 for Online and On- Premises
Administering CRM 2015 for online and on- premises Version 7.1.1 This document is provided "as-is". Information and views expressed in this document, including URL and other Internet Web site references, may change without notice. Some examples depicted herein are provided for illustration only and are fictitious. No real association or connection is intended or should be inferred. This document does not provide you with any legal rights to any intellectual property in any Microsoft product. You may copy and use this document for your internal, reference purposes. The videos and eBooks might be in English only. Also, if you click the links, you may be redirected to a U.S. website whose content is in English. © 2015 Microsoft. All rights reserved. Microsoft, Active Directory, Azure, Bing, Excel, Internet Explorer, Microsoft Dynamics, Outlook, SharePoint, SQL Server, Windows, and Windows Server are trademarks of the Microsoft group of companies. All other trademarks are property of their respective owners. Contents Administering CRM 2015 ................................................................................................................. 9 What's new for administrators and customizers in Microsoft Dynamics CRM 2015 and CRM Online ........................................................................................................................................ 9 Getting started ............................................................................................................................ 22 64-bit supported -

The Microsoft Office Specialist
ii MCAS Office 2007 Exam Prep: Exams for Microsoft® ASSOCIATE PUBLISHER Dave Dusthimer Office 2007 ACQUISITIONS EDITOR Copyright © 2009 by Pearson Certification Betsy Brown All rights reserved. No part of this book shall be reproduced, stored in a retrieval system, or DEVELOPMENT EDITOR transmitted by any means, electronic, mechanical, photocopying, recording, or otherwise, Andrew Cupp without written permission from the publisher. No patent liability is assumed with respect to the use of the information contained herein. Although every precaution has been taken in the MANAGING EDITOR preparation of this book, the publisher and author assume no responsibility for errors or omis- Patrick Kanouse sions. Nor is any liability assumed for damages resulting from the use of the information contained herein. SENIOR PROJECT EDITOR Tonya Simpson ISBN-13: 978-0-7897-3774-8 ISBN-10: 0-7897-3774-4 COPY EDITOR Barbara Hacha Library of Congress Cataloging-in-Publication Data: Gilster, Ron. INDEXER Ken Johnson MCAS Office 2007 exam prep : exams for Microsoft Office 2007. p. cm. PROOFREADER Matthew Purcell Includes bibliographical references and index. ISBN-13: 978-0-7897-3774-8 (pbk.) TECHNICAL EDITORS Pawan K. Bhardwaj ISBN-10: 0-7897-3774-4 (pbk.) Christopher A. Crayton 1. Microsoft Office—Examinations—Study guides. 2. Business—Computer programs— PUBLISHING COORDINATOR Examinations—Study guides. 3. Word processing—Examinations—Study guides. Vanessa Evans 4. Electronic spreadsheets—Examinations—Study guides. 5. Integrated software— Examinations—Study guides. I. Title. II. Title: Microsoft certified application specialist MULTIMEDIA DEVELOPER Office 2007 exam prep. Dan Scherf HF5548.4.M525G54 2009 BOOK DESIGNER 005.5076—dc22 Gary Adair 2009020166 COMPOSITOR Printed in the United States of America Louisa Adair First Printing: June 2009 Trademarks All terms mentioned in this book that are known to be trademarks or service marks have been appropriately capitalized. -

Microsoft ® Office 2016 Transition
Microsoft ® Office 2016 Transition Course Length: 7 hours Click here to view the current class schedule! Overview: You've used Microsoft® Office 2007 or Office 2010 to create various types of business materials, from documents in Word to spreadsheets in Excel® to presentations in PowerPoint®. Perhaps you use Outlook® to manage your calendar, contacts, and email; or Access® to manage inventory and trouble tickets. However you use Office, the fact is the Office suite of applications is the de-facto standard for business productivity software. Each new release of Office builds upon the successes of the previous generations. This course builds upon the foundational Microsoft Office 2007/2010 knowledge and skills you’ve already acquired. It focuses on the enhanced features you’ll want to leverage to improve the way you manage, organize, present, and distribute your company’s data and information. You’ll explore a variety of enhancements, from Word’s ability to edit PDF files to the new Flash Fill functionality in Excel that dramatically increases the speed at which you can add data to a spreadsheet. You’ll discover how the cloud has been deeply integrated into your Office experience and how collaborating with colleagues has never been easier. This Microsoft® Office 2016: Transition from Office 2007/2010 course will help you bridge the gap from the version you already know and love, to the latest release of Microsoft’s flagship productivity suite. Course Objectives: In this course, you will explore the new features available in Office 2016 applications. You will: • Identify new and enhanced features that are common across all applications in Office 2016. -

First Look 2007 Microsoft Office System Ebook
A02L622655.fm Page iii Friday, May 19, 2006 3:23 PM PUBLISHED BY Microsoft Press A Division of Microsoft Corporation One Microsoft Way Redmond, Washington 98052-6399 Copyright © 2006 by Microsoft Corporation All rights reserved. No part of the contents of this book may be reproduced or transmitted in any form or by any means without the written permission of the publisher. Library of Congress Control Number 2005939242 ISBN-13: 978-0-7356-2265-4 ISBN-10: 0-7356-2265-5 Printed and bound in the United States of America. 1 2 3 4 5 6 7 8 9 QWE 1 0 9 8 7 6 Distributed in Canada by H.B. Fenn and Company Ltd. A CIP catalogue record for this book is available from the British Library. Microsoft Press books are available through booksellers and distributors worldwide. For further information about international editions, contact your local Microsoft Corporation office or contact Microsoft Press Inter- national directly at fax (425) 936-7329. Visit our Web site at www.microsoft.com/mspress. Send comments to [email protected]. Microsoft, ActiveX, Excel, InfoPath, Microsoft Press, MSDN, OneNote, Outlook, PivotChart, PivotTable, PowerPoint, SharePoint, Visio, Windows, Windows Mobile, and Windows Vista are either registered trade- marks or trademarks of Microsoft Corporation in the United States and/or other countries. Other product and company names mentioned herein may be the trademarks of their respective owners. The example companies, organizations, products, domain names, e-mail addresses, logos, people, places, and events depicted herein are fictitious. No association with any real company, organization, product, domain name, e-mail address, logo, person, place, or event is intended or should be inferred. -

EXAM MS-900: Microsoft 365 Fundamentals
WWW.AGUIDETOCLOUD.COM A Guide To Cloud To Guide A MS900: Course Course Introduction MS900: WWW.AGUIDETOCLOUD.COM A Guide To Cloud To Guide A Susanth Sutheesh Susanth A Guide To Cloud WWW.AGUIDETOCLOUD.COM WWW.AGUIDETOCLOUD.COM Study areas Weights Understand cloud concepts 15-20% Understand core Microsoft 365 services and concepts 30-35% Understand security, compliance, privacy, and trust in Microsoft 365 25-30% Understand Microsoft 365 pricing and support 20-25% WWW.AGUIDETOCLOUD.COM WWW.AGUIDETOCLOUD.COM aka.ms/Microsoft365Exams A Guide To Cloud aka.ms/ModernDesktopExams WWW.AGUIDETOCLOUD.COM A Guide To Cloud To Guide A A Guide To Cloud WWW.AGUIDETOCLOUD.COM WWW.AGUIDETOCLOUD.COM Next Video How to schedule MS900 Exam? WWW.AGUIDETOCLOUD.COM A Guide To Cloud To Guide A How to schedule MS900 Exam? Exam? MS900 schedule to How 1 WWW.AGUIDETOCLOUD.COM Visit the WWW.AGUIDETOCLOUD.COM Exam page Select your country 2 Schedule the exam 3 A Guide To Cloud Go to exam page WWW.AGUIDETOCLOUD.COM A Guide To Cloud To Guide A A Guide To Cloud WWW.AGUIDETOCLOUD.COM WWW.AGUIDETOCLOUD.COM Select “At my home or office ” Click “Run pre- check” A Guide To Cloud WWW.AGUIDETOCLOUD.COM WWW.AGUIDETOCLOUD.COM Check Check internet Check microphone speed webcam A Guide To Cloud WWW.AGUIDETOCLOUD.COM WWW.AGUIDETOCLOUD.COM Check Check internet Check microphone speed webcam WWW.AGUIDETOCLOUD.COM A Guide To Cloud To Guide A A Guide To Cloud WWW.AGUIDETOCLOUD.COM WWW.AGUIDETOCLOUD.COM Read the online exam policies. Click Next after you agree to all policies. -

User Guide Windows 7 and Microsoft Office 2007
User Guide Windows 7 and Microsoft Office 2007 Villanova UNIT Training© Table of Contents GLOSSARY OF WINDOWS 7 TERMS ......................................................................................................................................... 3 GLOSSARY OF MICROSOFT OFFICE 2007 TERMS .................................................................................................................... 3 WINDOWS 7: (Enterprise Version) CLIENT OPERATING SYSTEM ............................................................................................ 4 Background: ........................................................................................................................................................................ 4 Process: ............................................................................................................................................................................... 5 Types of Operating Systems:............................................................................................................................................... 5 Windows 7 Operating System: ............................................................................................................................................ 5 Windows 7’s New Interface: ............................................................................................................................................... 6 New/Updated Features: .................................................................................................................................................... -

Using Microsoft Office 2007 Introduction to Outlook Handout INFORMATION TECHNOLOGY SERVICES California State University, Los Angeles Version 1.2 Spring 2009
Using Microsoft Office 2007 Introduction to Outlook Handout INFORMATION TECHNOLOGY SERVICES California State University, Los Angeles Version 1.2 Spring 2009 Contents Starting Outlook............................................................................................................................ 2 Using the Outlook Interface ......................................................................................................... 3 Using the Navigation Pane .......................................................................................................... 4 Configuring the Navigation Pane ............................................................................................. 5 Adding an Item to the Navigation Pane ................................................................................... 6 Using the Toolbars....................................................................................................................... 6 The Standard Toolbar ............................................................................................................... 6 The Web Toolbar ..................................................................................................................... 7 Using Outlook E-mail Features ................................................................................................... 7 Checking E-mail Messages ......................................................................................................... 7 Reading E-mail Messages .......................................................................................................... -

Office Productivity Catalog
The Industry’s Best-Value Learning Membership Featuring: Office Productivity Office Productivity Catalog Overview The Office Productivity catalog includes online career certification training in Microsoft Office 2016, Microsoft Office 2013, Microsoft Office 365 and more. Featured Certifications • Microsoft Office 2016: New Features • Microsoft Project • • Microsoft Office Excel • Microsoft Office 365 - For End Users • • Microsoft Office Outlook • Microsoft Office Word • and more! • Additional Membership Catalogs • Project Management • IT Service Management • Cyber Security • • IT Networking • Business Skills • Cloud Management • • Software Development • CareerAcademy.com Inc. | [email protected] | 1-800-538-9193 (U.S.) | 1-781-453-3900 (Int.) The Industry’s Best-Value Learning Membership Featuring: Office Productivity Office Productivity Catalog Office 365 Training 2013 Edition • Microsoft Office 365 - For End Users • Transition to Office 2013 from Office • Microsoft Office 365 - Administration 2007/2010 • Microsoft Office 365 - SharePoint for • Microsoft Office 2013 Lync Essentials End Users • Microsoft Project 2013 Basic • Microsoft Office 365 - Web Apps • Microsoft Project 2013 Advanced • Microsoft Office 2013 Access Basic Microsoft Office Training • Microsoft Office 2013 Access Intermediate 2016 Edition • Microsoft Office 2013 Access Advanced • Microsoft Office 2016: New Features • Microsoft Office 2013 Excel Basic • Microsoft Office 2016 Excel Basic • Microsoft Office 2013 Excel • Microsoft Office 2016 Excel Intermediate Intermediate -

Professor Teaches Microsoft Office 2003 & 2007, Windows, Web
PROFESSOR TEACHES MICROSOFT OFFICE 2003 & 2007, WINDOWS, WEB & GRAPHICS Professor Teaches® provides realistic, interactive, and complete training for Office, Windows, Web Design and Graphics. Users may build their skills with 50+ tutorials and learn everything they will need, from beginning to advanced topics. Each interactive tutorial is organized for fast and easy learning with practical exercises that build skills quickly and effectively. Features: Thousands of learning topics 5 to 10 Hours of Training per Course Beginner to Advanced Topics Self-Paced Learning Objectives Introductions & Summaries Interactive Exercises Professional Voice Narration Realistic Simulation of Software End-of-Chapter Quiz Questions Checkmarks for Completed Topics Glossary, Index & Search Professor Answers for Instant Training User will interact to perform the correct action during each exercise for better learning and retention. Professor Teaches Office is a complete multimedia-training Microsoft application. It offers instruction from beginning to advanced features of each Microsoft Office software program, Microsoft Windows, and several popular Web-creation programs. It offers a comprehensive set of training programs which include hundreds of practical exercises designed to build essential skills quickly and effectively. Step-by-step interactive instructions make learning easy. Plus, with the included Professor Answers reference feature you can browse all these courses by topic or keyword to quickly access training topics just when you need them. Refresh your memory, brush up your skills, or learn new tips with Professor Answers. Users will discover how these powerful, self-paced training programs will improve their computer skills, increase their efficiency, and enhance their productivity. Professor Answers allows you to browse through all the training topics in every Professor Teaches tutorial, or you can search using keywords for just the training you need, right when you need it. -
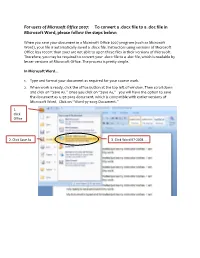
To Convert a .Docx File to a .Doc File in Microsoft Word, Please Follow the Steps Below
For users of Microsoft Office 2007: To convert a .docx file to a .doc file in Microsoft Word, please follow the steps below: When you save your document in a Microsoft Office 2007 program (such as Microsoft Word), your file is automatically saved a .docx file. Instructors using versions of Microsoft Office less recent than 2007 are not able to open these files in their versions of Microsoft. Therefore, you may be required to convert your .docx file to a .doc file, which is readable by lesser versions of Microsoft Office. The process is pretty simple. In Microsoft Word… 1. Type and format your document as required for your course work. 2. When work is ready, click the office button at the top left of window. Then scroll down and click on “Save As.” Once you click on “Save As,” you will have the option to save the document as a, 97‐2003 document, which is compatible with earlier versions of Microsoft Word. Click on “Word 97‐2003 Document.” 1. Click Office 2. Click Save As 3. Click Word 97‐2003…. 3. In the “Save As” Dialog box, click the dropdown arrow to the right of the “Save in” option to select the appropriate place to store your file. Then in the “File Name” box at the bottom of the dialog box, type an appropriate title for your work, being sure to include your name somewhere in the title (this is helpful for your instructor to keep up with whose work is whose). 4. Your file is now saved. The saved file name should now appear in the left corner in the blue strip at the very top of the screen. -

Microsoft Office 2007 Training Manual
Microsoft Office 2007 Microsoft Office 2007 Training Manual COPYRIGHT Copyright ©2007 by EZ-REF Courseware, Ladera Ranch, CA http://www.ezref.com/ All rights reserved. This publication, including the student manual, instructor's guide and exercise files, or any part thereof, may not be reproduced or transmitted in any form or by any means, electronic or mechanical, without prior written permission of EZ-REF Courseware. TRADEMARKS EZ-REF is a trademark of EZ-REF Courseware. All other products or brand names mentioned are trademarks or registered trademarks of their respective holders. DISCLAIMER While EZ-REF Courseware has taken care to ensure the accuracy and quality of these materials, all material is provided without any warranty whatsoever, including, but not limited to, the implied warranties of merchantability or fitness for a particular purpose. Any persons or businesses mentioned in the text of this manual are strictly fictitious. Any resemblances to existing or deceased persons, or existing or defunct businesses, is entirely coincidental. Product Code: OFFICE 2007 7.08 ©2007 EZ-REF Courseware Page ii Microsoft Office 2007 TABLE OF CONTENTS HOW TO USE THIS MANUAL ..................................................................................................................... VII RUNNING MICROSOFT WORD ................................................................................................................... 2 THE WORD SCREEN ................................................................................................................................... -

Skillchoice Desktop Catalog
OFFICE OF THE CHANCELLOR DesktopDesktop Available Now! SkillSoft offers the most comprehensive and compelling Systemwide e-learning content for desktop computer skills training. Professional SkillChoice Desktop provides learners with comprehensive Development coverage of relevant desktop technologies and skills, [email protected] including more than 400 interactive courses and over 450 Access this content at online books from the OfficeEssentials™ Collection by https://ds.calstate. Books24x7®. Content focuses on Microsoft Office (Mac and edu/?svc=skillsoft PC), Microsoft Windows, Apple OS X, e-mail, internet skills and browsers (including Internet Explorer and Apple Safari), computing fundamentals, and various Adobe products. The courses in this catalog are available at no charge to all CSU faculty and staff. The table of contents is fully searchable. Click the topic heading of interest to reach the course listing in the catalog. Find out more about the course, such as a full description, target audience, expected course duration, course number, and lesson objectives by clicking on the course name. 2 SkillChoice Desktop Catalog Microsoft Office 2013: Power User Excel 6 Course List Microsoft Office 2013: SharePoint for Power Users 6 DESKTOP COMPUTER SKILLS 5 Microsoft Office 2010 7 Adobe 5 Microsoft Office 2010: New Features 7 Microsoft Office 2010 New Features for Users Adobe Flash CS5 5 Migrating from Office 2003 7 Adobe Photoshop CS5 5 Microsoft Office 2010: Beginning Word 7 Adobe Dreamweaver CS5 5 Microsoft SharePoint 2010: New Features