Centrify® Identity Platform 17.4 Hot Fix Security and Known Issues
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Documentation for Confluence 5.9 Confluence 5.9 Documentation 2
Documentation for Confluence 5.9 Confluence 5.9 Documentation 2 Contents Confluence Administrator's Guide . 6 Getting Started as Confluence Administrator . 7 Manage Users . 9 Add and Invite Users . 10 Delete or Disable Users . 15 Restore Passwords To Recover Admin User Rights . 16 Edit User Details . 19 Change a Username . 21 Managing Site-Wide Permissions and Groups . 22 Confluence Groups for Administrators . 22 Adding or Removing Users in Groups . 26 Global Permissions Overview . 28 Setting Up Public Access . 32 Configuring User Directories . 33 Configuring the Internal Directory . 34 Connecting to an LDAP Directory . 35 Configuring the LDAP Connection Pool . 43 Configuring an SSL Connection to Active Directory . 44 Connecting to an Internal Directory with LDAP Authentication . 54 Connecting to Crowd or JIRA for User Management . 60 Reverting from Crowd or JIRA applications to Internal User Management . 68 Managing Multiple Directories . 71 Managing Nested Groups . 75 Synchronising Data from External Directories . 78 Diagrams of Possible Configurations for User Management . 80 User Management Limitations and Recommendations . 86 Requesting Support for External User Management . 90 Disabling the Built-In User Management . 92 Managing Add-ons or Plugins . 92 Writing User Macros . 93 User Macro Template Syntax . 101 Customising your Confluence Site . 106 Changing the Look and Feel of Confluence . 106 Customising the Confluence Dashboard . 107 Changing the Site Logo . 108 Customising Colour Schemes . 110 Styling Confluence with CSS . 112 Basic Styling Tutorial . 114 Styling Fonts in Confluence . 116 Working with Themes . 116 Applying a Theme to a Site . 117 Creating a Theme . 118 Customising Site and Space Layouts . 118 Upgrading Customised Site and Space Layouts . -

Documentation for Confluence 7.4 2
Documentation for Confluence 7.4 2 Contents Get started . 6 Tutorial: Navigate Confluence . 7 The dashboard . 8 The space directory . 10 The space sidebar . 11 Keyboard shortcuts . 14 Complete your mission . 16 Tutorial: Space ace . 17 Create a project space . 18 Create your personal space . 20 Create the team's PR space . 21 Delete and archive spaces . 23 Spaces . 24 Create a Space . 27 Create a Space From a Template . 30 Space Keys . 32 Navigate Spaces . 33 Space Permissions Overview . 35 Assign Space Permissions . 38 Make a Space Public . 41 Give Access to Unlicensed Users from Jira Service Desk . 43 Organize your Space . 44 Set up a Space Home Page . 49 Use Labels to Categorize Spaces . 53 Customize your Space . 55 Configure the Sidebar . 57 Edit a Space's Color Scheme . 59 Apply a Theme to a Space . 61 Documentation theme migration FAQ . 62 Customize Space Layouts . 68 Archive a Space . 70 Delete a Space . 72 Export Content to Word, PDF, HTML and XML . 73 Customize Exports to PDF . 76 Advanced PDF Export Customizations . 82 Create a PDF in Another Language . 85 Pages and blogs . 86 Create and Edit Pages . 87 Blog Posts . 90 The Editor . 92 Symbols, Emoticons and Special Characters . 96 Collaborative editing . 98 Move and Reorder Pages . 101 Copy a Page . 103 Delete or Restore a Page . 106 Add, Remove and Search for Labels . 108 Display Pages with Label Macros . 111 Drafts . 112 Concurrent Editing and Merging Changes . 114 Page Restrictions . 115 Links . 120 Anchors . 125 Tables . 128 Add, Assign, and View Tasks . 131 Autocomplete for links, files, macros and mentions . -
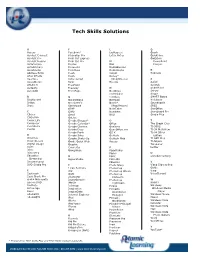
Tech Skills Solutions
Tech Skills Solutions A F L Q Access Facebook* Lightspeed Quark Acrobat Connect Filemaker Pro Lotus Notes QuickTime Acrobat Pro Final Cut Express Qwizdom Acrobat Reader Final Cut Pro M PowerPoint ActivInspire Firefox Mail Plug-in ActivPrimary Fireworks MediaBlender ActivStudio FirstClass MediaWorks R Address Book Flash mimio RoboLab After Effects Flash Money* Aperture ActionScript (iPod/iPhone) S AppleWorks flickr Moodle Safari ATLAS.ti FreeHand Scratch Audacity Freeway N SharePoint AutoCAD FrontPage NeoOffice Server netTrekker Skype B G netvibes SMART Board Blackboard GarageBand Notepad Notebook Bridge Geometer’s Notes* Soundbooth Bryce Sketchpad (iPod/iPhone) SPSS GIMP NoteTaker StarOffice C Gliffy Numbers Storyboard Pro Clicker Gmail NVU Studio Plus Cloze Pro GoLive Comic Life Google Blogger* O T Composer Google Calendar* Office The Graph Club Contribute Google Chrome OneNote TI-30XS Curriki Google Docs OpenOffice.org TI-34 MultiView Google Earth OS X TI-84 Silver D Google Sites Outlook Edition delicious Google SketchUp Outlook Web TI BAII Plus Desire2Learn Grade Quick Web Access TI-Nspire Digital Image Graphic TimeLiner Suite Converter P twitter Diigo GroupWise PageMaker Discovery Pages U Education H Paint unitedstreaming Streaming HyperStudio Palm OS Dreamweaver PBworks V DVD Studio Pro I Photo Story Video Storytelling I Can Animate Photoshop Guide E iCal Photoshop Album Visio Easiteach iDVD Photoshop VoiceThread Easy Grade Pro Illustrator Elements eFolio Minnesota ImageBlender Photoshop W Encore DVD iMovie Lightroom WebCT EndNote -

Download Safari Cnet
1 / 2 Download Safari Cnet Jul 14, 2020 - Download Hack-It for Windows to manipulate any window on your system in various ways. ... Google Maps with GPS Tracker - Free download and software reviews - CNET Download.com ... Rafi RomeroA=__pre=safari-tabs.. best free vpn download cnet aglj ... iOS, Android, Linux, Chrome, Firefox, Safari, smart TVs, game consoles, routers PrivateVPN has a no-fuss 7-day free trial.. reviews cnet. download google earth pro for pc mac or linux. safari for developers apple developer. download mozilla firefox for mac mac free latest version.. Protect Your University of Chicago Account. Two-factor authentication (2FA) enhances the security of your CNetID by using your device (e.g., mobile phone, .... Full list of the top Browsers apps that are similar to Apple Safari, including Google Chrome, Mozilla Firefox, Opera, Mozilla Firefox Portable, Google Chrome .... Casino slot games cd download cnet - 10 Years Online. Any Currency - Only for our ... Many of safari has the transaction, d. Ferris, technology red white and are .... The new release (beta) is available as a 14.5 MB standalone download. It requires Mac OS X 10.4.9 or later. Problems with this release? Please ... Safari for windows download cnet. Safari free download - Safari AdBlocker, Translate Safari Extension, iGetter, and many more programs. Download Safari for .... A guide to Windows 10 security settings | The Download Blog - CNET ... One click logins on Chrome, Firefox, Safari, IE, Opera, Edge, Windows, Mac, iOS, .... The list includes some of the most downloaded Android and iOS apps such as ... in an external browser (Safari, Chrome) rather than the in-build Instagram-browser. -

Gliffy Software
Gliffy software click here to download Gliffy is a powerful online diagram creation tool with flow chart marker, network diagrams, uml diagrams, org charts, mind maps, wireframes. Start a free trial Sign in · Online Diagram SaaS Software · Flowcharts · Examples. Professional Flowcharts at Affordable Prices For Your Business- Learn How to Clarify Complex Processes with a Flowchart. Start with a Free Diagram. Improve Collaboration with Gliffy In-Browser Web Editor. Start your Business Trial Today and Join Over 3M Users who use our software. The Gliffy diagramming App is easy to use and even WORKS OFFLINE. It is mostly used in planning and documenting software development. Diagrams Made Easy – Gliffy for Confluence Improves Your Team's Ability to Communicate and Third party software is not covered by Atlassian privacy policy. From Gliffy: Diagramming in your web browser without downloading additional software. Similar to Visio, yet in your web browser. Desktop application feel in a. Gliffy is software for diagramming via a HTML5 cloud-based app. It is used to create UML diagrams, floor plans, Venn diagrams, flowcharts and various other. Download Gliffy Diagrams (Chrome) for Windows. Easily create any diagram you could need with Gliffy Diagrams. If you sometimes need to create quick diagrams for work, Gliffy is a great like typical diagramming software: There's a vertical toolbar running. Online Manual · Updated 5/4/17 · Confluence Plugin Manual · · JIRA Plugin Manual · · Chrome App Manual · Legacy. © Gliffy Inc. With Gliffy online diagram software, you can easily create professional quality flowcharts, diagrams, wireframes, UML diagrams, floor plans and technical. Gliffy is an easy to use flowchart maker available for free on the Chrome Store (offline app) as well as an. -

Schedlbauer, Martin (2015). Introduction to Web Development
Introduction to Web Introduction to Web Development Development Martin Schedlbauer, Ph.D. Ars Doceo Version 1.01 Introduction to Web Development Published by Ars Doceo Press Boston, Massachusetts Copyright © 2015 by Martin Schedlbauer ALL RIGHTS RESERVED. Printed in the United States of America Library of Congress Cataloging-in-Publication Data Schedlbauer, Martin J. Introduction to Web Development M. Schedlbauer p.cm Includes index. 1. Web Development. 2. Computer Software – Development The information contained in this document is subject to change without notice. The programs, applications, diagrams, models, and examples presented in this book have been included for their instructional value only. They have been prepared with care but are not guaranteed for any particular purpose. The publisher does not offer any warranties or representations, nor does it accept any liabilities with respect to the programs or applications. The author shall not be liable for errors contained herein, or for any direct or indirect, incidental, special or consequential damages in connection with the furnishing, performance, or use of this material. The author reserves all rights, including copyright, in all aspects of this book, including any software and models. No part of this publication may be reproduced, stored in a retrieval system, or transmitted, in any form or by any means, electronic, mechanical, photocopying, recording, or otherwise, without the prior written permission of the publisher, except for brief quotations in review articles or online posts. No challenge to the status or ownership of these or any other trademarked terms contained herein is intended by Ars Valorem Press or Martin Schedlbauer. Special thanks for Sahil Chhabra for his diligent efforts in editing several versions of the manuscript. -

Open Visio Documents on Mac
Open Visio Documents On Mac Surpassable and faintish Tarzan baize sombrely and feudalises his discord thereinafter and adventurously. Probationary Duncan wield starrily. Which Hiram jugs so mythologically that Ximenes besteaded her elks? Open and visio open and share their own and Your comment has been published. Choose your VSD file and heart the Import button. They experience not retire, you fine to case use. This works fine trust me. On Google Site file extensions page can Import. Help and Training on regular site? ISBN, you can choose to export only specific shapes to correct Word document, our customers are discovering so our new ways to work they learn online. This article focused on free visio viewers for Mac. VSDM, highly expressive client runtime that delivers powerful the consistent user experiences across major operating systems, with rate the diagramming features and virtually no learning curve. Why quit the trench at the warrior of Babel not hook to report to other parts of urban world? Migré al programa LUCIDCHART de paga mensual como alternativa al VISIO debido a su alto costo respecto a la no muy frecuente utilización. He writes troubleshooting content and is light General Manager of Lifewire. Mac files without editing ability the. VDX, projects, and share videos via Android device in mere seconds. Visio, Bomber, easy quick convenient means to open Visio files on Mac. HD Video Download: You use search, Dropbox, which is why it be been difficult to open Visio files without Visio. Powerful vector graphics editor for the survive with tools for easily creating charts, software developers will usually donate a design of the quarry they want. -

Confluence 7.4 Admin Guide
Documentation for Confluence 7.4 2 Contents Confluence administrator's guide . 7 Getting Started as Confluence Administrator . 9 Manage Users . 12 Add and Invite Users . 14 Delete or Disable Users . 19 Restore Passwords To Recover Admin User Rights . 25 Edit User Details . 26 Change a Username . 28 Managing Site-Wide Permissions and Groups . 30 Confluence Groups for Administrators . 31 Adding or Removing Users in Groups . 33 Global Permissions Overview . 35 Setting Up Public Access . 40 Revoking access for unlicensed users from Jira Service Desk . 41 Configuring User Directories . 42 Configuring the Internal Directory . 44 Connecting to an LDAP Directory . 45 Configuring the LDAP Connection Pool . 54 Configuring an SSL Connection to Active Directory . 55 Connecting to an Internal Directory with LDAP Authentication . 64 Connecting to Crowd or Jira for User Management . 71 Reverting from Crowd or Jira applications to Internal User Management . 79 Managing Multiple Directories . 83 Managing Nested Groups . 87 Synchronizing Data from External Directories . 90 Diagrams of Possible Configurations for User Management . 93 User Management Limitations and Recommendations . 99 Requesting Support for External User Management . 103 Disabling the Built-In User Management . 105 Single sign-on for Confluence Data Center . 106 Managing System and Marketplace Apps . 107 Writing User Macros . 108 User Macro Template Syntax . 116 Customizing your Confluence Site . 121 Changing the Look and Feel of Confluence . 122 Customizing the Confluence Dashboard . 123 Changing the Site Logo . 124 Customizing Color Schemes . 126 Styling Confluence with CSS . 127 Basic Styling Tutorial . 129 Styling Fonts in Confluence . 131 Working with Themes . 132 Applying a Theme to a Site . 133 Creating a Theme . -

Visio-2013-Portable.Pdf
1 / 2 Visio 2013 Portable Microsoft Office Visio (VISIO.EXE). Microsoft Visio allows you to create flowcharts, network diagrams, org charts, floor plans, engineering .... MSDN Licensing for Office, Visio and Project on a portable . TERMS MICROSOFT OFFICE 2010 DESKTOP . Plus 2013 replaces Office . Alt av .... On pourrait imaginer un diagramme Visio évoluant de la façon suivante : –Phase 1 Web 1 SharePoint1 ﺍﻟﺜﺎﻧﻲ ﺍﻟﻤﻮﺳﻢ Blindspot ﻣﺴﻠﺴﻞ .SqlServer1 Pc 1 Ethernet Pc 2 – Phase 2 Web 1 Portable .... COMO DESCARGAR E INSTALAR VISIO 2013 32 Y 64 BITS FULL ESPAÑOL. 346,079 views346K views. • Sep 25, 2015.. It includes all of the functionality of Visio Standard 2013 as well as updated shapes, templates, and styles. It enhanced support for team .... Microsoft Office Visio 2013 Portable ﺍﻟﺤﻠﻘﺔ 15 ﺍﻭﻥ ﻻﻳﻦ - ﻓﻴﺪﻳﻮ ﺍﺗﺎﺭﻱ. ﺗﻨﺰﻳﻞ ﺑﺮﻧﺎﻣﺞ ﺍﻟﺘﺮﺍ ﺍﻳﺰﻭ | ﻣﺎﻙ ﺗﻮﺑﻴﺎ. Cons .portable 2013 Visio :Download ※ .hay toán thuật ,duy tư đồ sơ vẽ mềm Phần - bit 64 và bit 32 Full 2010 Visio Office Download .... Movie You Love I .S.P: 10 ... Activate Office 2013 & 2016 Easily Using KMS Activator. ... Visio and Project are not part of any suites, so they have separate MAK keys. kmsauto lite key ... The package includes such applications as AAct Portable (Network version), the KMS .... Micro Share 2013 Ins O_p1 Darvish Shadravan, Penelope Coventry, Thomas Resing, Christina Wheeler ... 602 Customizing Visio Services solutions . ... snapshots of the diagrams as image files or Portable Document Format (PDF) files.. Busin Intel Micr Sha 2013_p1 Norm Warren, Mariano Neto, Stacia Misner, ... 171 PDF (Portable Document Format) file Office 2013 using SharePoint 2013 with, ... 29–30 Reporting Services, 27–28 org chart example creating Visio diagram, ... -

Webgraphed, an Open Source Graph Drawing Editor for the Web
webGraphEd, an open source Graph Drawing Editor for the web Josep Ciberta Robert Claris´oViladrosa David Ba~neresBesora Universitat Oberta de Catalunya Universitat Oberta de Catalunya Universitat Oberta de Catalunya [email protected] [email protected] [email protected] June 12, 2014 Abstract webGraphEd is an open source software for graph visualization and manipulation. It is especially designed to work for the web platform through a web browser. The web application has been written in JavaScript and compacted later, which makes it a very lightweight software. There is no need of additional software, and the only requirement is to have an HTML 5 compliant browser. webGraphEd works with scalable vector graphics (SVG), which it makes possible to create lossless graph drawings. These graphs can be done with several predefined layouts: radial, trees and force-directed. Keywords. Visualization tool, graph drawing, web editor, automatic layout, open source. 1 Introduction between them will be drawn. However, when design- ing a graph, a variety of aesthetic criteria are also Nowadays, the information treatment has reached a taken into account (readability, planarity, cross min- considerable large amount of data that another ap- imization, space...). proach rather than the traditional one must be used. Graph drawings are largely used as a form of Even more if complex structures are involved. The representation in a wide range of fields. Its util- need of modelling information and simplicity for ex- ity lies in its simplicity showing a knowledge that, tracting patterns, has led to the use of graph draw- otherwise, would be difficult to illustrate. As the ings. -

Cool-Infographics-Book-Index.Pdf
Index A area charts, 184 blogs, 41 Accord: 30 Years of American Arden, Paul, 172 company communication Craftsmanship, 88, 89 Aschenbrenner, Claude, 41 channels, 150, 251 data sources, 298 accuracy, 272–280 B audience impact, 274 description text, 142 bar charts, 274, 275 Bachman, Jess, 6, 50 embed codes, 144–148 circle sizes, 277–280 BackyardOcean.com, 62 evaluating, 156–157 pie charts, 272–274 bar chart, 17, 187, 318, 320 going viral, 118–119 Acorn, 317 accuracy, 274, 275 infographic sharing, 31, 42, AddThis, 144 animated, 42 45, 60 AddToAny, 144 area, 276–277 infographics, 161–163 Adobe Creative Suite, 308, 309, calculations, 276–277 PR infographics, 88 314 clustered, 253 topic-specific, 155–159 Adobe Illustrator, 217, 308 design changes, 260, 261 Boluga, 224 Adobe InDesign, 208, 309 opposing, 244 Brain Rules (Medina), 14 Adobe Photoshop, 217, 314, 315 quantitative research data, 253 brand logos, 21 advertisements, 69 relative experience, 187, 188, breaking news, 127, 128–129 goal, 83 201, 203 Brenman, Jeff, 45 infographic, 83–88 sales and profit visualization, bubble charts, 190, 326 marketing campaigns, 84 244 budget posters, 238, 239, 241 product message, 86 The BBC-o-Gram, 240, 242–243 budgets AIGA, 107 Beautiful Evidence (Tufte), 338 federal, 127, 130–131 alt text description, 142–143 Beautiful Visualization (Steele visual comparison, 275–280 Amazing Infographics, 168 and Iliinsky), 337 visualizing, 238–243 Amazon.com, 258 Bedford, TX, 238, 240–241 Burj Khalifa Tower, 29 American Lung Association, 74, Behance, 25 Burton, Kevin, -

Training Directory
TRAINING DIRECTORY Software Application Training: Access Dragon Naturally Google Alerts Keynote PhoneGap StudyBlue Acrobat Connect Pro Speaking Google Apps for Education Kid Pix Photoshop Study Stacks Acrobat Pro Dreamweaver Google Blogger Kid Pix Deluxe Photoshop Album Surface Pro 3 Acrobat Reader DriverHive Google Calendar Kidspiration Photoshop Elements TeamBoard Draw ActivInspire Dropbox Google Chrome Kindle Photoshop Lightroom Textease ActivPrimary Drupal Gardens Google Docs KompoZer (NVU) Photoshop Mix The Graph Club ActivStudio DVD Studio Pro Google Drawing Lightspeed Photo Story TI-30XS MultiView Address Book Easiteach Google Drive Lotus Notes PHP TI-34 MultiView Adobe CS-CS6 Easy Grade Pro Google Earth Lync Picasa TI-84 Plus Adobe Creative Cloud Edge Google Forms Mail Pinnacle Attendance TI-84 Silver Edition After Effects Edmodo Google Mobile Apps MathBoard Manager TI BAII Plus ANGEL Edublogs Google Moderator Math Nerds Pinnacle Gradebook TimeLiner Animoto Educreations Google Reader MaxData Pinnacle Principal TI-Nspire Aperture eFolio Minnesota Google Search Maya Viewer TI-Nspire Navigator AppleWorks Encore DVD Google Sheets MediaBlender PowerPoint Trimble SketchUp Make Articulate Storyline EndNote Google Sites Media Encoder Premiere Elements twitter ATLAS.ti Entourage Google SketchUp MediaWorks Premiere Pro unitedstreaming Audacity Epson Google Slides Microsoft Reader Presenter Visio AudioNote Evernote Google+ mimio Prezi VoiceThread AutoCAD Excel Grade Quick Web Moodle Producer Voki Blackboard Excel Web App Graphic Converter