NCCU Programming Languages Concepts 程式語言
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

COMMUNICATION STUDIES REGISTRATION INFORMATION DO NOT E-Mail the Professor to Request Permission for Communication Studies Class
COMMUNICATION STUDIES REGISTRATION INFORMATION DO NOT e-mail the professor to request permission for Communication Studies classes! We follow our departmental waitlist priorities found on the Department web page at: http://www.lsa.umich.edu/comm/undergraduate/generalinformation/majorpolicies. Students on the waitlist are expected to attend the first two lectures and the first discussion section for the class, just as any enrolled student. Students who do not do attend will lose their spot in the class or on the waitlist! ---------------------------------------------------------------------------------------------------------------------- Comm 101 & 102 are restricted to students with freshman and sophomore standing. If you have over 54 credits, including the current semester, you will not be able to register for these. Juniors and seniors wishing to take Comm 101 and 102 may attend the first two lectures and first discussion section of the course and ask the instructor to add them to the waitlist. Instructors will issue permissions from the waitlist after classes begin, according to department waitlist priorities. There may be some exceptions to this policy, but you will need to e-mail [email protected] 2 (TWO) days prior to your registration date to find out if you qualify for an exception. Provide the following: Name: UMID#: Registration Date: Registration Term: Course: Top 3 section choices: Exception eligibility - AP credit has pushed you over the 54 credits for junior standing, OR you have junior standing but have already completed Comm 101 or 102 to start the Comm prerequisites, OR you are a transfer student with junior standing OR you are an MDDP student with more than sophomore standing. -

Programming Languages Shouldn't and Needn't Be Turing Complete
Programming languages shouldn't and needn't be Turing complete GABRIEL PICKARD Any algorithmic problem faced by application programmers in the wild1 can in principle be solved using a Turing incomplete programming language. [Rice 1953] suggests that Turing completeness bears a heavy price, fundamentally limiting the ability of automatic assistants to help programmers be more productive, create less bugs and write safer software. Nevertheless, no mainstream general purpose programming language is Turing incomplete, with the arguable exception of SQL. We identify historical causes for this discrepancy and argue that the current moment offers better conditions for introducing Turing incompleteness. We present an approach to eliminating Turing completeness during the language design process, with several examples suitable languages targeting application development. Designers of modern practical programming languages should strongly consider evading Turing completeness and enabling better verification, security, automated testing and distributed computing. 1 CEDING POWER TO GAIN CONTROL 1.1 Turing completeness considered harmful The history of programming language design2 has been a history of removing powers which were considered harmful (cf. [Dijkstra 1966]) and replacing them with tamer, more manageable and automated constructs, including: (1) Direct access to CPU registers and instructions ! higher level compilers (2) GOTO ! structured programming (3) Manual memory management ! garbage collection (and borrow checkers) (4) Arbitrary access ! information hiding (5) Side-effects and mutability ! pure functions and persistent data structures While not all application domains benefit from all the replacement steps above3, it appears as if removing some expressive power can often enable a new kind of programming, even a new kind of application altogether. -

Turing Machines
Basics Computability Complexity Turing Machines Bruce Merry University of Cape Town 10 May 2012 Bruce Merry Turing Machines Basics Computability Complexity Outline 1 Basics Definition Building programs Turing Completeness 2 Computability Universal Machines Languages The Halting Problem 3 Complexity Non-determinism Complexity classes Satisfiability Bruce Merry Turing Machines Basics Definition Computability Building programs Complexity Turing Completeness Outline 1 Basics Definition Building programs Turing Completeness 2 Computability Universal Machines Languages The Halting Problem 3 Complexity Non-determinism Complexity classes Satisfiability Bruce Merry Turing Machines Basics Definition Computability Building programs Complexity Turing Completeness What Are Turing Machines? Invented by Alan Turing Hypothetical machines Formalise “computation” Alan Turing, 1912–1954 Bruce Merry Turing Machines If in state si and tape contains qj , write qk then move left/right and change to state sm A finite set of states, including a start state A tape that is infinite in both directions, containing finitely many non-blank symbols A head which points at one position on the tape A set of transitions Basics Definition Computability Building programs Complexity Turing Completeness What Are Turing Machines? Each Turing machine consists of A finite set of symbols, including a special blank symbol () Bruce Merry Turing Machines If in state si and tape contains qj , write qk then move left/right and change to state sm A tape that is infinite in both directions, containing -

Text Editing in UNIX: an Introduction to Vi and Editing
Text Editing in UNIX A short introduction to vi, pico, and gedit Copyright 20062009 Stewart Weiss About UNIX editors There are two types of text editors in UNIX: those that run in terminal windows, called text mode editors, and those that are graphical, with menus and mouse pointers. The latter require a windowing system, usually X Windows, to run. If you are remotely logged into UNIX, say through SSH, then you should use a text mode editor. It is possible to use a graphical editor, but it will be much slower to use. I will explain more about that later. 2 CSci 132 Practical UNIX with Perl Text mode editors The three text mode editors of choice in UNIX are vi, emacs, and pico (really nano, to be explained later.) vi is the original editor; it is very fast, easy to use, and available on virtually every UNIX system. The vi commands are the same as those of the sed filter as well as several other common UNIX tools. emacs is a very powerful editor, but it takes more effort to learn how to use it. pico is the easiest editor to learn, and the least powerful. pico was part of the Pine email client; nano is a clone of pico. 3 CSci 132 Practical UNIX with Perl What these slides contain These slides concentrate on vi because it is very fast and always available. Although the set of commands is very cryptic, by learning a small subset of the commands, you can edit text very quickly. What follows is an outline of the basic concepts that define vi. -

Python C/C++ Java Perl Ruby
Programming Languages Big Ideas for CS 251 • What is a PL? Theory of Programming Languages • Why are new PLs created? Principles of Programming Languages – What are they used for? – Why are there so many? • Why are certain PLs popular? • What goes into the design of a PL? CS251 Programming Languages – What features must/should it contain? Spring 2018, Lyn Turbak – What are the design dimensions? – What are design decisions that must be made? Department of Computer Science Wellesley College • Why should you take this course? What will you learn? Big ideas 2 PL is my passion! General Purpose PLs • First PL project in 1982 as intern at Xerox PARC Java Perl • Created visual PL for 1986 MIT Python masters thesis • 1994 MIT PhD on PL feature Fortran (synchronized lazy aggregates) ML JavaScript • 1996 – 2006: worked on types Racket as member of Church project Haskell • 1988 – 2008: Design Concepts in Programming Languages C/C++ Ruby • 2011 – current: lead TinkerBlocks research team at Wellesley • 2012 – current: member of App Inventor development team CommonLisp Big ideas 3 Big ideas 4 Domain Specific PLs Programming Languages: Mechanical View HTML A computer is a machine. Our aim is to make Excel CSS the machine perform some specifieD acEons. With some machines we might express our intenEons by Depressing keys, pushing OpenGL R buIons, rotaEng knobs, etc. For a computer, Matlab we construct a sequence of instrucEons (this LaTeX is a ``program'') anD present this sequence to IDL the machine. Swift PostScript! – Laurence Atkinson, Pascal Programming Big ideas 5 Big ideas 6 Programming Languages: LinguisEc View Religious Views The use of COBOL cripples the minD; its teaching shoulD, therefore, be A computer language … is a novel formal regarDeD as a criminal offense. -

Unusable for Programming
UNUSABLE FOR PROGRAMMING DANIEL TEMKIN Independent, New York, USA [email protected] 2017.xCoAx.org Lisbon Computation Communication Aesthetics & X Abstract Esolangs are programming languages designed for non-practical purposes, often as experiments, par- odies, or experiential art pieces. A common goal of esolangs is to achieve Turing Completeness: the capability of implementing algorithms of any Keywords complexity. They just go about getting to Turing Esolangs Completeness with an unusual and impractical set Programming languages of commands, or unexpected waysDraft of representing Code art code. However, there is a much smaller class of Oulipo esolangs that are entirely “Unusable for Program- Tangible Computing ming.” These languages explore the very boundary of what a programming language is; producing uns- table programs, or for which no programs can be written at all. This is a look at such languages and how they function (or fail to). Final 1. INTRODUCTION Esolangs (for “esoteric programming languages”) include languages built as thought experiments, jokes, parodies critical of language practices, and arte- facts from imagined alternate computer histories. The esolang Unlambda, for example, is both an esolang masterpiece and typical of the genre. Written by David Madore in 1999, Unlambda gives us a version of functional programming taken to its most extreme: functions can only be applied to other functions, returning more functions, all of them unnamed. It’s a cyberlinguistic puzzle intended as a challenge and an experiment at the extremes of a certain type of language design. The following is a program that calculates the Fibonacci sequence. The code is nearly opaque, with little indication of what it’s doing or how it works. -

Binpac: a Yacc for Writing Application Protocol Parsers
binpac: A yacc for Writing Application Protocol Parsers Ruoming Pang∗ Vern Paxson Google, Inc. International Computer Science Institute and New York, NY, USA Lawrence Berkeley National Laboratory [email protected] Berkeley, CA, USA [email protected] Robin Sommer Larry Peterson International Computer Science Institute Princeton University Berkeley, CA, USA Princeton, NJ, USA [email protected] [email protected] ABSTRACT Similarly, studies of Email traffic [21, 46], peer-to-peer applica- A key step in the semantic analysis of network traffic is to parse the tions [37], online gaming, and Internet attacks [29] require under- traffic stream according to the high-level protocols it contains. This standing application-level traffic semantics. However, it is tedious, process transforms raw bytes into structured, typed, and semanti- error-prone, and sometimes prohibitively time-consuming to build cally meaningful data fields that provide a high-level representation application-level analysis tools from scratch, due to the complexity of the traffic. However, constructing protocol parsers by hand is a of dealing with low-level traffic data. tedious and error-prone affair due to the complexity and sheer num- We can significantly simplify the process if we can leverage a ber of application protocols. common platform for various kinds of application-level traffic anal- This paper presents binpac, a declarative language and com- ysis. A key element of such a platform is application-protocol piler designed to simplify the task of constructing robust and effi- parsers that translate packet streams into high-level representations cient semantic analyzers for complex network protocols. We dis- of the traffic, on top of which we can then use measurement scripts cuss the design of the binpac language and a range of issues that manipulate semantically meaningful data elements such as in generating efficient parsers from high-level specifications. -
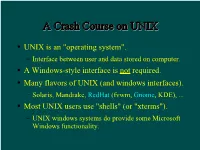
A Crash Course on UNIX
AA CCrraasshh CCoouurrssee oonn UUNNIIXX UNIX is an "operating system". Interface between user and data stored on computer. A Windows-style interface is not required. Many flavors of UNIX (and windows interfaces). Solaris, Mandrake, RedHat (fvwm, Gnome, KDE), ... Most UNIX users use "shells" (or "xterms"). UNIX windows systems do provide some Microsoft Windows functionality. TThhee SShheellll A shell is a command-line interface to UNIX. Also many flavors, e.g. sh, bash, csh, tcsh. The shell provides commands and functionality beyond the basic UNIX tools. E.g., wildcards, shell variables, loop control, etc. For this tutorial, examples use tcsh in RedHat Linux running Gnome. Differences are minor for the most part... BBaassiicc CCoommmmaannddss You need these to survive: ls, cd, cp, mkdir, mv. Typically these are UNIX (not shell) commands. They are actually programs that someone has written. Most commands such as these accept (or require) "arguments". E.g. ls -a [show all files, incl. "dot files"] mkdir ASTR688 [create a directory] cp myfile backup [copy a file] See the handout for a list of more commands. AA WWoorrdd AAbboouutt DDiirreeccttoorriieess Use cd to change directories. By default you start in your home directory. E.g. /home/dcr Handy abbreviations: Home directory: ~ Someone else's home directory: ~user Current directory: . Parent directory: .. SShhoorrttccuuttss To return to your home directory: cd To return to the previous directory: cd - In tcsh, with filename completion (on by default): Press TAB to complete filenames as you type. Press Ctrl-D to print a list of filenames matching what you have typed so far. Completion works with commands and variables too! Use ↑, ↓, Ctrl-A, & Ctrl-E to edit previous lines. -

Puremessage for Unix Help Contents Getting Started
PureMessage for Unix help Contents Getting Started......................................................................................................................................... 1 Welcome to PureMessage for Unix.............................................................................................. 1 Deployment Strategies.................................................................................................................. 6 Installing PureMessage............................................................................................................... 18 Upgrading PureMessage.............................................................................................................51 Quick Reference Guide...............................................................................................................65 Contacting Sophos...................................................................................................................... 75 Managing PureMessage........................................................................................................................ 77 Dashboard Tab............................................................................................................................77 Policy Tab....................................................................................................................................79 Quarantine Tab..........................................................................................................................130 -

Exotic Programming Languages
I. Babich, Master student V. Spivachuk, PHD in Phil., As. Prof., research advisor Khmelnytskyi National University EXOTIC PROGRAMMING LANGUAGES The word ―exotic‖ is defined by the Oxford dictionary as ―of a kind not ordinarily encountered‖. If that is so, what is meant by exotic programming languages? These are languages that are not used for commercial purposes or even for anything ―useful‖. This definition can be applied a little loosely and, hence, many different types of programming languages can be classified as ―exotic‖. So, after some consideration, I have included three types of languages as belonging to this category. Exotic programming languages include languages that are intentionally designed to be difficult to learn and program with. Such languages are often used to analyse the power of programming languages. They are known as esoteric programming languages. Some exotic languages, known as joke languages, are created for the sake of fun. And the third type includes non – English – based programming languages. The definition clearly mentions that these languages do not serve any practical purpose. Then what’s all the fuss about exotic programming languages? To understand their importance, we need to first understand what makes a programming language a programming language. The “Turing completeness” of programming languages A language qualifies as a programming language in the true sense only if it is ―Turing complete‖ [1, c. 4]. A language that is Turing complete can be used to represent any computable algorithm. Many of the so called languages are, in fact, not languages, in the true sense. Examples of tools that are not Turing complete and hence not languages in the strict sense include HTML, XML, JSON, etc. -
![[MS-MAIL-Diff]: Remote Mailslot Protocol](https://docslib.b-cdn.net/cover/6097/ms-mail-diff-remote-mailslot-protocol-1656097.webp)
[MS-MAIL-Diff]: Remote Mailslot Protocol
[MS-MAIL-Diff]: Remote Mailslot Protocol Intellectual Property Rights Notice for Open Specifications Documentation ▪ Technical Documentation. Microsoft publishes Open Specifications documentation (“this documentation”) for protocols, file formats, data portability, computer languages, and standards support. Additionally, overview documents cover inter-protocol relationships and interactions. ▪ Copyrights. This documentation is covered by Microsoft copyrights. Regardless of any other terms that are contained in the terms of use for the Microsoft website that hosts this documentation, you can make copies of it in order to develop implementations of the technologies that are described in this documentation and can distribute portions of it in your implementations that use these technologies or in your documentation as necessary to properly document the implementation. You can also distribute in your implementation, with or without modification, any schemas, IDLs, or code samples that are included in the documentation. This permission also applies to any documents that are referenced in the Open Specifications documentation. ▪ No Trade Secrets. Microsoft does not claim any trade secret rights in this documentation. ▪ Patents. Microsoft has patents that might cover your implementations of the technologies described in the Open Specifications documentation. Neither this notice nor Microsoft's delivery of this documentation grants any licenses under those patents or any other Microsoft patents. However, a given Open Specifications document might be covered by the Microsoft Open Specifications Promise or the Microsoft Community Promise. If you would prefer a written license, or if the technologies described in this documentation are not covered by the Open Specifications Promise or Community Promise, as applicable, patent licenses are available by contacting [email protected]. -

Proof Pearl: Proving a Simple Von Neumann Machine Turing Complete
Proof Pearl: Proving a Simple Von Neumann Machine Turing Complete J Strother Moore Dept. of Computer Science, University of Texas, Austin, TX, USA [email protected] http://www.cs.utexas.edu Abstract. In this paper we sketch an ACL2-checked proof that a simple but unbounded Von Neumann machine model is Turing Complete, i.e., can do anything a Turing machine can do. The project formally revisits the roots of computer science. It requires re-familiarizing oneself with the definitive model of computation from the 1930s, dealing with a simple “modern” machine model, thinking carefully about the formal statement of an important theorem and the specification of both total and partial programs, writing a verifying compiler, including implementing an X86- like call/return protocol and implementing computed jumps, codifying a code proof strategy, and a little “creative” reasoning about the non- termination of two machines. Keywords: ACL2, Turing machine, Java Virtual Machine (JVM), ver- ifying compiler 1 Prelude I have often taught an undergraduate course at the University of Texas at Austin entitled A Formal Model of the Java Virtual Machine. In the course, students are taught how to model sophisticated computing engines and, to a lesser extent, how to prove theorems about such engines and their programs with the ACL2 theorem prover [5]. The course starts with a pedagogical (“toy”) JVM-like model which the students elaborate over the semester towards a more realistic model, which is then compared to an accurate JVM model[9]. The pedagogical model is called M1: a stack based machine providing a fixed number of registers (JVM’s “locals”), an unbounded operand stack, and an execute-only program providing the following bytecode instructions ILOAD, ISTORE, ICONST, IADD, ISUB, IMUL, IFEQ, GOTO, and HALT, with unbounded arithmetic.