Merkblatt Online-Speicherdienste
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Every App in the Universe
THE BIGGER BOOK OF APPS Resource Guide to (Almost) Every App in the Universe by Beth Ziesenis Your Nerdy Best Friend The Bigger Book of Apps Resource Guide Copyright @2020 Beth Ziesenis All rights reserved. No part of this publication may be reproduced, distributed, or trans- mitted in any form or by any means, including photocopying, recording or other elec- tronic or mechanical methods, without the prior written permission of the publisher, except in the case of brief quotations embodied in critical reviews and certain other non- commercial uses permitted by copyright law. For permission requests, write to the pub- lisher at the address below. Special discounts are available on quantity purchases by corporations, associations and others. For details, contact the publisher at the address below. Library of Congress Control Number: ISBN: Printed in the United States of America Avenue Z, Inc. 11205 Lebanon Road #212 Mt. Juliet, TN 37122 yournerdybestfriend.com Organization Manage Lists Manage Schedules Organize and Store Files Keep Track of Ideas: Solo Edition Create a Mind Map Organize and Store Photos and Video Scan Your Old Photos Get Your Affairs in Order Manage Lists BZ Reminder Pocket Lists Reminder Tool with Missed Call Alerts NerdHerd Favorite Simple To-Do List bzreminder.com pocketlists.com Microsoft To Do Todoist The App that Is Eating Award-Winning My Manager’s Favorite Productivity Tool Wunderlist todoist.com todo.microsoft.com Wunderlist Plan The Award-Winning Task Manager with a Task Manager and Planning Tool Rabid Fanbase -

Die Meilensteine Der Computer-, Elek
Das Poster der digitalen Evolution – Die Meilensteine der Computer-, Elektronik- und Telekommunikations-Geschichte bis 1977 1977 1978 1979 1980 1981 1982 1983 1984 1985 1986 1987 1988 1989 1990 1991 1992 1993 1994 1995 1996 1997 1998 1999 2000 2001 2002 2003 2004 2005 2006 2007 2008 2009 2010 2011 2012 2013 2014 2015 2016 2017 2018 2019 2020 und ... Von den Anfängen bis zu den Geburtswehen des PCs PC-Geburt Evolution einer neuen Industrie Business-Start PC-Etablierungsphase Benutzerfreundlichkeit wird gross geschrieben Durchbruch in der Geschäftswelt Das Zeitalter der Fensterdarstellung Online-Zeitalter Internet-Hype Wireless-Zeitalter Web 2.0/Start Cloud Computing Start des Tablet-Zeitalters AI (CC, Deep- und Machine-Learning), Internet der Dinge (IoT) und Augmented Reality (AR) Zukunftsvisionen Phasen aber A. Bowyer Cloud Wichtig Zählhilfsmittel der Frühzeit Logarithmische Rechenhilfsmittel Einzelanfertigungen von Rechenmaschinen Start der EDV Die 2. Computergeneration setzte ab 1955 auf die revolutionäre Transistor-Technik Der PC kommt Jobs mel- All-in-One- NAS-Konzept OLPC-Projekt: Dass Computer und Bausteine immer kleiner, det sich Konzepte Start der entwickelt Computing für die AI- schneller, billiger und energieoptimierter werden, Hardware Hände und Finger sind die ersten Wichtige "PC-Vorläufer" finden wir mit dem werden Massenpro- den ersten Akzeptanz: ist bekannt. Bei diesen Visionen geht es um die Symbole für die Mengendarstel- schon sehr früh bei Lernsystemen. iMac und inter- duktion des Open Source Unterstüt- möglichen zukünftigen Anwendungen, die mit 3D-Drucker zung und lung. Ägyptische Illustration des Beispiele sind: Berkley Enterprice mit neuem essant: XO-1-Laptops: neuen Technologien und Konzepte ermöglicht Veriton RepRap nicht Ersatz werden. -

Tech Note--Gatelet Objects and Activities Reference
Tech Note--Gatelet Objects and Activities Reference Tech Note--Gatelet Objects and Activities Reference Symantec CloudSOC Tech Note 1 Tech Note--Gatelet Objects and Activities Reference Copyright statement Copyright (c) Broadcom. All Rights Reserved. Broadcom, the pulse logo, Connecting everything, and Symantec are among the trademarks of Broadcom. The term “Broadcom” refers to Broadcom Inc. and/or its subsidiaries. For more information, please visit www.broadcom.com. Broadcom reserves the right to make changes without further notice to any products or data herein to improve reliability, function, or design. Information furnished by Broadcom is believed to be accurate and reliable. However, Broadcom does not assume any liability arising out of the application or use of this information, nor the application or use of any product or circuit described herein, neither does it convey any license under its patent rights nor the rights of others. 2 Tech Note--Gatelet Objects and Activities Reference Table of Contents Introduction Generic Gatelets Full Gatelet AddThis Adobe Document Cloud – Sign Amazon Web Services ARIS – MyCloud Asana Atlassian – BitBucket Atlassian - Jira Service Desk Atlassian - Jira Software Cloud Atlassian – Stride Basecamp Box Box Admin BV ShareX Cisco Webex Teams Concur Confluence Domo Dropbox Dropbox - Admin Console Dynamics Facebook – Workplace FileDropper GigaSize GitHub GitLab Gmail Google – Chat Google - Cloud Search Google – Contacts Google – Forms Google – Groups Google – Hangouts Google – Keep 3 Tech Note--Gatelet -

Electronic Data Safes – Personal Information Management at the Intersection of Electronic Process Support and User-Managed Access in E-Business and E-Government
Zurich Open Repository and Archive University of Zurich Main Library Strickhofstrasse 39 CH-8057 Zurich www.zora.uzh.ch Year: 2017 Electronic Data Safes: personal information management at the intersection of electronic process support and user-managed access in e-business and e-government Pfister, Joachim Posted at the Zurich Open Repository and Archive, University of Zurich ZORA URL: https://doi.org/10.5167/uzh-144449 Dissertation Published Version Originally published at: Pfister, Joachim. Electronic Data Safes: personal information management at the intersection ofelec- tronic process support and user-managed access in e-business and e-government. 2017, University of Zurich, Faculty of Economics. Department of Informatics Electronic Data Safes – Personal Information Management at the Intersection of Electronic Process Support and User-Managed Access in E-Business and E-Government Dissertation submitted to the Faculty of Business, Economics and Informatics of the University of Zurich to obtain the degree of Doktor der Wissenschaften, Dr. sc. corresponds to Doctor of Science, PhD presented by Joachim Pfister from Germany approved in July 7 at the request of Prof. Dr. Gerhard Schwabe Prof. Dr. Jörn von Lucke The Faculty of Business, Economics and Informatics of the University of Zurich hereby authorizes the printing of this dissertation, without indi- cating an opinion of the views expressed in the work. Zurich, July , Chairwoman of the Doctoral Board: Prof. Dr. Elaine M. Huang i To my mother Katharina who missed the beginning and my father Anton who missed the end of this journey. I know you're living in my mind. It's not the same as being alive. -
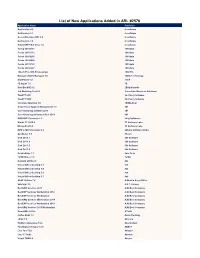
List of New Applications Added in ARL #2576
List of New Applications Added in ARL #2576 Application Name Publisher NetCmdlets 4.0 /n software NetCmdlets 3.1 /n software SecureBlackbox.NET 8.0 /n software NetCmdlets 3.0 /n software EldoS SFTP Net Drive 1.0 /n software Tenup 20190117 1010data Tendo 20151112 1010data Tendo 20160205 1010data Tendo 20190905 1010data Tendo 20170723 1010data Tendo 20161207 1010data 1042-S Pro 2016 Professional 1099 Pro Manager (10ZiG Manager) 3.0 10ZIG Technology DataParser 7.5 17a-4 1E Agent 7.2 1E SyncBackSE 8.2 2BrightSparks 2c8 Modeling Tool 4.2 2conciliate Business Solutions TaxACT 2017 2nd Story Software TaxACT 2018 2nd Story Software Complete Anatomy 5.0 3D4Medical Clean-Trace Hygiene Management 1.3 3M Core Grouping Software 2019 3M Core Grouping Software Client 2019 3M DWG DXF Converter 1.1 3nity Softwares Studio 3T 2020.9 3T Software Labs MongoChef 4.5 3T Software Labs MP4 to MP3 Converter 6.8 4Media Software Studio SendLater 3.4 4Team Disk Dril 3.7 508 Software Disk Dril 1.0 508 Software Disk Dril 3.5 508 Software Disk Dril 3.6 508 Software DoublePane 1.7 5am Code 7-PDF Maker 1.5 7-PDF Network Utility 2.2 8x8 Virtual Office Desktop 6.1 8x8 Virtual Office Desktop 6.4 8x8 Virtual Office Desktop 5.6 8x8 Virtual Office Desktop 6.7 8x8 ASAP Utilities 7.8 A Must in Every Office SafeSign 3.5 A.E.T. Europe BestSRQ Services 2015 A.M. Best Company BestESP Services Workstation 2012 A.M. Best Company BestESP Services Workstation A.M. -

Magic Quadrant for Enterprise File Synchronization and Sharing Published: 22 July 2015
G00268445 Magic Quadrant for Enterprise File Synchronization and Sharing Published: 22 July 2015 Analyst(s): Monica Basso, Charles Smulders, Jeffrey Mann Today's EFSS market offers a range of maturing options to IT leaders as well as mobile and collaboration planners. New capabilities for corporate system integration and enhanced content collaboration continue to add to standard EFSS functionality. Strategic Planning Assumptions By 2018, any ECM, collaboration, MFT, backup and recovery, storage, and EMM offerings will embed natively basic EFSS features. By 2018, any EFSS deployment will require back-end integration with multiple content repositories, federation and management, and data governance capabilities. By 2018, less than 10% of today's stand-alone EFSS offerings will exist. Market Definition/Description This document was revised on 24 July 2015. The document you are viewing is the corrected version. For more information, see the Corrections page on gartner.com. Enterprise file synchronization and sharing (EFSS) refers to a range of on-premises or cloud-based capabilities that enables individuals to synchronize and share documents, photos, videos and files across mobile devices, such as smartphones, tablets and PCs. Sharing can happen between people (for example, partners and customers) within or outside the organization, or on a mobile device, as data sharing among apps. Access to files in enterprise repositories (such as file servers and content platforms) from mobile devices or remote PCs extends user productivity and collaboration to modern use cases. Security and collaboration support are critical aspects for enterprises to adopt EFSS. Beyond file synchronization, sharing and access, EFSS offerings may have different levels of support for: ■ Mobility, with native apps for a variety of mobile devices, notebooks and desktops, as well as Web browser support. -
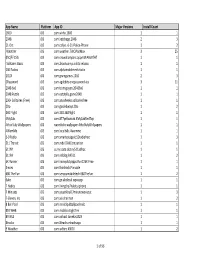
MDM App Summary 2 6 17.Xlsx
App Name Platform App ID Major Versions Install Count 1600 iOS com.whha.1600 1 1 2048 iOS com.ketchapp.2048 2 3 21‐Oct iOS com.callyo.‐0‐21‐Police‐Phone 1 2 Weather iOS com.weather.TWCiPadMax 3 25 (ISC)² CSG iOS com.crowdcompass.appmMiA9oR7HT 1 1 `Solitaire: Basic iOS com.zhaohuanyu.solitairebasic 1 1 100 Radios iOS com.alphamobiletech.radio 1 1 1010! iOS com.gramgames.1010 2 3 1Password iOS com.agilebits.onepassword‐ios 3 11 2048 6x6 iOS com.trannguyen.20486x6 1 1 2048 Puzzle iOS com.estotyllc.game2048 1 1 250+ Solitaires (Free) iOS com.anoshenko.solitairesfree 1 1 2Do iOS com.guidedways.2Do 1 2 360 Flight iOS com.360.360Flight 1 1 4MyCab iOS com.877yellowcab.4MyCabRedTop 1 1 4th of July Wallpapers iOS ivannikolic.wallpaper.4thofJulyWallpapers 1 1 4WarnMe iOS com.localtvllc.4warnme 1 1 5‐0 Radio iOS com.smartestapple.50radiofree 1 3 511 Transit iOS com.mdv.OAKCompanion 1 1 511NY iOS us.ny.state.dot.ny511adhoc 1 1 511PA iOS com.infolog.PA511 1 2 5K Runner iOS com.heavydutyapps.RunC25K‐Free 1 1 5miles iOS com.thirdrock.Pinnacle 1 1 680 The Fan iOS com.seroyamobiletech.680TheFan 1 2 6abc iOS com.go.abclocal.wpviapp 1 1 7 Habits iOS com.livingthe7habits.iphone 1 1 7 Minutes iOS com.stuartkhall.7minuteworkout 1 3 7‐Eleven, Inc. iOS com.sei.sherman 1 2 8 Ball Pool iOS com.miniclip.8ballpoolmult 1 1 810 WHB iOS com.moblico.EightTen 1 1 89 WLS iOS com.airkast.tunekast323 1 1 8tracks iOS com.8tracks.etracksapp 1 1 9 Weather iOS com.wdtinc.KWTV 1 2 1 of 96 App Name Platform App ID Major Versions Install Count 93.3 WMMR iOS com.greatermediaradio.wmmr -

Probate & Trust Newsletter
Probate and Trust Law Section Newsletter Published by the Section on Probate and Trust Law of the Philadelphia Bar Association SEPTEMBER 2014 | NO. 137 IN THIS ISSUE 03 The Uniform Fiduciary REPORT OF THE CHAIR Access to Digital Assets Act: The Information BY KAREN M. STOCKMAL, ESQUIRE | KMS LAW Superhighway Now Has I remember the advice I was a chance to meet new people, HOV Lanes for Fiduciaries given as a second year associate many of whom have become as I attended my first Education mentors, referral sources, colleagues 12 Tax Update Committee meeting. “Just keep and friends. The annual meeting 16 Recent U.S. Supreme showing up and pretty soon you’ll has become a sort of family reunion Court Decision on be running things,” someone told for me, with an opportunity to see Inherited IRAs in me. Funny, I thought, but not likely. friends that I would not otherwise Bankruptcy Fourteen years later, I am finishing see, but with whom I remain close my final year as an officer and while and a phone call away, if needed. 19 The Frank Aragona I have never felt like I was “running These people are a part of my life, Trust Case: Material things” due to the incredible team- not just my work. Participation by Estates work we employ, I’ve given others and Trusts the same advice that I received Many attorneys have told me that 21 Practice Points many times. Stick around, it’s an they don’t have time to spend amazing place to be. 22 Ethics Column working in the Section, because they have to spend their nonbillable 23 Case Summary from the As I wind down the four year officer work time on marketing. -
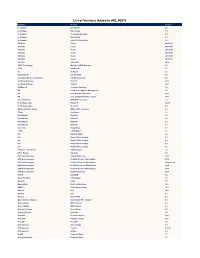
List of Versions Added in ARL #2576
List of Versions Added in ARL #2576 Publisher Product Version /n software NetCmdlets 4.0 /n software NetCmdlets 3.1 /n software SecureBlackbox.NET 8.0 /n software NetCmdlets 3.0 /n software EldoS SFTP Net Drive 1.0 1010data Tendo 20151112 1010data Tendo 20160205 1010data Tendo 20190905 1010data Tendo 20170723 1010data Tendo 20161207 1010data Tenup 20190117 1099 Pro 1042-S Pro 2016 10ZIG Technology Manager (10ZiG Manager) 3.0 17a-4 DataParser 7.5 1E 1E Agent 7.2 2BrightSparks SyncBackSE 8.2 2conciliate Business Solutions 2c8 Modeling Tool 4.2 2nd Story Software TaxACT 2018 2nd Story Software TaxACT 2017 3D4Medical Complete Anatomy 5.0 3M Clean-Trace Hygiene Management 1.3 3M Core Grouping Software 2019 3M Core Grouping Software Client 2019 3nity Softwares DWG DXF Converter 1.1 3T Software Labs Studio 3T 2020.9 3T Software Labs Studio 3T 4.5 4Media Software Studio MP4 to MP3 Converter 6.8 4Team SendLater 3.4 508 Software Disk Dril 3.6 508 Software Disk Dril 1.0 508 Software Disk Dril 3.5 508 Software Disk Dril 3.7 5am Code DoublePane 1.7 7-PDF 7-PDF Maker 1.5 8x8 Network Utility 2.2 8x8 Virtual Office Desktop 6.1 8x8 Virtual Office Desktop 6.4 8x8 Virtual Office Desktop 5.6 8x8 Virtual Office Desktop 6.7 A Must in Every Office ASAP Utilities 7.8 A.E.T. Europe SafeSign 3.5 A.M. Best Company BestSRQ Services 2015 A.M. Best Company BestESP Services Workstation 2012 A.M. Best Company BestESP Services Workstation Unspecified A.M. -

A Worldwide Survey of Encryption Products
A Worldwide Survey of Encryption Products Bruce Schneier Kathleen Seidel Saranya Vijayakumar Berkman Center for Internet Independent Researcher Harvard College and Society [email protected] [email protected] Harvard University [email protected] February 11, 2016 Version 1.0 Introduction Data security is a worldwide problem, and there is a wide world of encryption solutions available to help solve this problem. Most of these products are developed and sold by for-profit entities, although some are created as free open-source projects. They are available, either for sale or free download, all over the world. In 1999, a group of researchers from George Washington University attempted to survey the worldwide market for encryption products [HB+99]. The impetus for their survey was the ongoing debate about US encryption export controls. By collecting information about 805 hardware and software encryption products from 35 countries outside the US, the researchers showed that restricting the export of encryption products did nothing to reduce their availability around the world, while at the same time putting US companies at a competitive disadvantage in the information security market. Seventeen years later, we have tried to replicate this survey. Findings We collected information on as many encryption products as we could find anywhere in the world. This is a summary of our findings: We have identified 865 hardware or software products incorporating encryption from 55 different countries. This includes 546 encryption products from outside the US, representing two-thirds of the total. Table 1 summarizes the number of products from each country. The most common non-US country for encryption products is Germany, with 112 products. -

Cloud Applications Supported by Cloudsoc
Cloud Applications Supported by CloudSOC Cloud Applications Supported by CloudSOC Table of Contents Cloud Applications Supported by CloudSOC.................................................................................. 3 Securlets........................................................................................................................................................................... 3 Gatelets............................................................................................................................................................................. 3 2 Cloud Applications Supported by CloudSOC Cloud Applications Supported by CloudSOC The following lists of Securlets and Gatelets are current as of September 2020. Securlets CloudSOC offers Securlets for the following cloud applications: • Amazon Web Services • Box • Google G Suite • Microsoft Azure NOTE Microsoft Azure does not support malware scanning. • Microsoft Office 365 • Salesforce • ServiceNow • Slack Gatelets CloudSOC offers Gatelets for the cloud applications listed in alphabetic order in the following table. Gatelets denoted as having generic support have limited activity monitoring; usually only upload, download, login, and logout. We monitor activities for these services, and support them in Gatelet-based Protect policies, on a best-effort basis. Gatelets denoted as having full support have more granular support for application activities. The content inspection column indicates that content of the file is inspected for content violating DLP -

Magic Quadrant for Enterprise File Synchronization and Sharing Published: 21 July 2016
G00290239 Magic Quadrant for Enterprise File Synchronization and Sharing Published: 21 July 2016 Analyst(s): Monica Basso, Karen A. Hobert, Jeffrey Mann EFSS destination vendors increasingly Additonal Perspectives address digital workplace enablement. IT leaders can consider this market and Company Size: Small & Midsize (<1000 choose among a range of maturing options Employees) for cloud-based content collaboration and data infrastructure modernization. Strategic Planning Assumption This document was revised on 5 August 2016. The document you are viewing is the corrected version. For more information, see the Corrections page on gartner.com. By 2018, 70% of EFSS destination vendors will cease to exist, having been acquired or put out of business, and the remaining 30% will evolve to support the digital workplace or modernize corporate data infrastructures. Market Definition/Description Gartner defines the enterprise file synchronization and sharing (EFSS) market as a range of cloud- based or on-premises offerings that enables individuals to synchronize and share files (such as documents, photos and videos) among mobile devices and PCs. Sharing can happen among people (for example, partners and customers) within or outside the organization, as well as among applications. Smooth search, retrieval and access of files stored in multiple data repositories (e.g., file servers or content management platforms) from different client devices complement these offerings, as well as security, data protection and collaboration capabilities. EFSS offerings enable modern user productivity and collaboration scenarios for the creation of a digital workplace (see Note 1). Typical deployment architectures for EFSS offerings can be public cloud, hybrid cloud, private cloud or on-premises.