Proceedings of the International Conference on Recent Trends of Computer Science and Electronics 2017
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Firms in Aor of Rd Sindh
Appendix-B FIRMS IN AOR OF RD SINDH Ser Name of Firm Chemical RD 1 M/s A.A Industries, Karachi Acetone, MEK, Toluene, Sindh 2 M/s A.J Steel Wire Industries Pvt Ltd, Karachi Hydrochloric Acid Sindh 3 M/s Aarfeen Traders, Karachi Hydrochloric Acid Sindh 4 M/s Abbott Laboratories, Karachi Acetone Sindh Hydrochloric Acid & Sulphuric 5 M/s ACI Industrial Chemicals (Pvt) Ltd, Karachi Sindh Acid 6 M/s Adamjee Engineering, Karachi Hydrochloric Acid Sindh 7 M/s Adnan Galvanizig Works, Karachi Hydrochloric Acid Sindh 8 M/s Agar International, Karachi Hydrochloric Acid Sindh Hydrochloric Acid & Sulphuric 9 M/s Ahmed & Sons, Karachi Sindh Acid MEK, Potassium 10 M/s Ahmed Chemical Co, Karachi Permanganate, Acetone & Sindh Hydrochloric Acid 11 M/s Aisha Steel Mills Ltd, Karachi Hydrochloric Acid Sindh Hydrochloric Acid & Sulphuric 12 M/s Al Falah Chemical, Karachi Sindh Acid 13 M/s Al Karam Textile Mills (Pvt) Ltd, Karachi Hydrochloric Acid Sindh 14 M/s Al Kausar Chemical Works, Karachi Hydrochloric Acid Sindh 15 M/s Al Makkah Enterprises Industrial Area, Karachi Sulphuric Acid Sindh 16 M/s Al Noor Metal Industries, Karachi Sulphuric Acid Sindh Toluene, MEK & Hydrochloric 17 M/s Al Rahim Trading Co (Pvt) Ltd, Karachi Sindh Acid 18 M/s Ali Murtaza Associate (Pvt) Ltd, Karachi Potassium Permanganate Sindh 19 M/s Al-Kausar Chemical Works, Karachi Hydrochloric Acid Sindh 20 M/s Allied Plastic Industries (Pvt) Ltd, Karachi Toluene & MEK Sindh 21 M/s Almakkah Enterprises, Karachi Hydrochloric Acid Sindh 22 M/s AL-Noor Oil Agency, Karachi Toluene Sindh 23 -
List of Stations
Sr # Code Division Name of Retail Outlet Site Category City / District / Area Address 1 101535 Karachi AHMED SERVICE STATION N/V CF KARACHI EAST DADABHOY NOROJI ROAD AKASHMIR ROAD 2 101536 Karachi CHAND SUPER SERVICE N/V CF KARACHI WEST PSO RETAIL DEALERSST/1-A BLOCK 17F 3 101537 Karachi GLOBAL PETROLEUM SERVICE N/V CF KARACHI EAST PLOT NO. 234SECTOR NO.3, 4 101538 Karachi FAISAL SERVICE STATION N/V CF KARACHI WEST ST 1-A BLOCK 6FEDERAL B AREADISTT K 5 101540 Karachi RAANA GASOLINE N/V CF KARACHI WEST SERVICE STATIONPSO RETAIL DEALERAPWA SCHOOL LIAQA 6 101543 Karachi SHAHGHAZI P/S N/V DFA MALIR SURVEY#81,45/ 46 KM SUPER HIGHWAY 7 101544 Karachi GARDEN PETROL SERVICE N/V CF KARACHI SOUTH OPP FATIMA JINNAHGIRLS HIGH SCHOOLN 8 101545 Karachi RAZA PETROL SERVICE N/V CF KARACHI SOUTH 282/2 LAWRENCE ROADKARACHIDISTT KARACHI-SOUTH 9 101548 Karachi FANCY SERVICE STATION N/V CF KARACHI WEST ST-1A BLOCK 10FEDERAL B AREADISTT KARACHI WEST 10 101550 Karachi SIDDIQI SERVIC STATION S/S DFB KARACHI EAST RASHID MINHAS ROADKARACHIDISTT KARACHI EAST 11 101555 Karachi EASTERN SERIVCE STN N/V DFA KARACHI WEST D-201 SITEDIST KARACHI-WEST 12 101562 Karachi AL-YASIN FILL STN N/V DFA KARACHI WEST ST-1/2 15-A/1 NORTHKAR TOWNSHIP KAR WEST 13 101563 Karachi DUREJI FILLING STATION S/S DFA LASBELA KM-4/5 HUB-DUREJI RDPATHRO HUBLASBE 14 101566 Karachi R C D FILLING STATION N/V DFA LASBELA HUB CHOWKI LASBELADISTT LASBELA 15 101573 Karachi FAROOQ SERVICE CENTRE N/V CF KARACHI WEST N SIDDIQ ALI KHAN ROADCHOWRANGI NO-3NAZIMABADDISTT 16 101577 Karachi METRO SERVICE STATION -

Data Collection Survey on Infrastructure Improvement of Energy Sector in Islamic Republic of Pakistan
←ボックス隠してある Pakistan by Japan International Cooperation Agency (JICA) Data Collection Survey on Infrastructure Improvement of Energy Sector in Islamic Republic of Pakistan Data Collection Survey ←文字上 / 上から 70mm on Infrastructure Improvement of Energy Sector in Pakistan by Japan International Cooperation Agency (JICA) Final Report Final Report February 2014 February 2014 ←文字上 / 下から 70mm Japan International Cooperation Agency (JICA) Nippon Koei Co., Ltd. 4R JR 14-020 ←ボックス隠してある Pakistan by Japan International Cooperation Agency (JICA) Data Collection Survey on Infrastructure Improvement of Energy Sector in Islamic Republic of Pakistan Data Collection Survey ←文字上 / 上から 70mm on Infrastructure Improvement of Energy Sector in Pakistan by Japan International Cooperation Agency (JICA) Final Report Final Report February 2014 February 2014 ←文字上 / 下から 70mm Japan International Cooperation Agency (JICA) Nippon Koei Co., Ltd. 4R JR 14-020 Data Collection Survey on Infrastructure Improvement of Energy Sector in Pakistan Final Report Location Map Islamabad Capital Territory Punjab Province Islamic Republic of Pakistan Sindh Province Source: Prepared by the JICA Survey Team based on the map on http://www.freemap.jp/. February 2014 i Nippon Koei Co., Ltd. Data Collection Survey on Infrastructure Improvement of Energy Sector in Pakistan Final Report Summary Objectives and Scope of the Survey This survey aims to collect data and information in order to explore the possibility of cooperation with Japan for the improvement of the power sector in Pakistan. The scope of the survey is: Survey on Pakistan’s current power supply situation and review of its demand forecast; Survey on the power development policy, plan, and institution of the Government of Pakistan (GOP) and its related companies; Survey on the primary energy in Pakistan; Survey on transmission/distribution and grid connection; and Survey on activities of other donors and the private sector. -
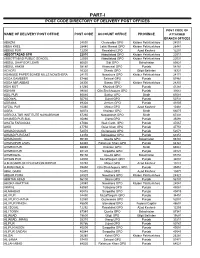
Part-I: Post Code Directory of Delivery Post Offices
PART-I POST CODE DIRECTORY OF DELIVERY POST OFFICES POST CODE OF NAME OF DELIVERY POST OFFICE POST CODE ACCOUNT OFFICE PROVINCE ATTACHED BRANCH OFFICES ABAZAI 24550 Charsadda GPO Khyber Pakhtunkhwa 24551 ABBA KHEL 28440 Lakki Marwat GPO Khyber Pakhtunkhwa 28441 ABBAS PUR 12200 Rawalakot GPO Azad Kashmir 12201 ABBOTTABAD GPO 22010 Abbottabad GPO Khyber Pakhtunkhwa 22011 ABBOTTABAD PUBLIC SCHOOL 22030 Abbottabad GPO Khyber Pakhtunkhwa 22031 ABDUL GHAFOOR LEHRI 80820 Sibi GPO Balochistan 80821 ABDUL HAKIM 58180 Khanewal GPO Punjab 58181 ACHORI 16320 Skardu GPO Gilgit Baltistan 16321 ADAMJEE PAPER BOARD MILLS NOWSHERA 24170 Nowshera GPO Khyber Pakhtunkhwa 24171 ADDA GAMBEER 57460 Sahiwal GPO Punjab 57461 ADDA MIR ABBAS 28300 Bannu GPO Khyber Pakhtunkhwa 28301 ADHI KOT 41260 Khushab GPO Punjab 41261 ADHIAN 39060 Qila Sheikhupura GPO Punjab 39061 ADIL PUR 65080 Sukkur GPO Sindh 65081 ADOWAL 50730 Gujrat GPO Punjab 50731 ADRANA 49304 Jhelum GPO Punjab 49305 AFZAL PUR 10360 Mirpur GPO Azad Kashmir 10361 AGRA 66074 Khairpur GPO Sindh 66075 AGRICULTUR INSTITUTE NAWABSHAH 67230 Nawabshah GPO Sindh 67231 AHAMED PUR SIAL 35090 Jhang GPO Punjab 35091 AHATA FAROOQIA 47066 Wah Cantt. GPO Punjab 47067 AHDI 47750 Gujar Khan GPO Punjab 47751 AHMAD NAGAR 52070 Gujranwala GPO Punjab 52071 AHMAD PUR EAST 63350 Bahawalpur GPO Punjab 63351 AHMADOON 96100 Quetta GPO Balochistan 96101 AHMADPUR LAMA 64380 Rahimyar Khan GPO Punjab 64381 AHMED PUR 66040 Khairpur GPO Sindh 66041 AHMED PUR 40120 Sargodha GPO Punjab 40121 AHMEDWAL 95150 Quetta GPO Balochistan 95151 -

Cruel Number 2010
mbe Nu rs el 20 u 1 r 0 C 2010 2010 Wajeeha Anwar Sahil Offices Sahil Head Office Sahil Referral Unit, Jaffarabad Sahil Referral Unit, Sukkur No 13, First Floor, Al Babar Center Khosa Mohalla, Near Civil Hospital, House # B 62, Street # 2 F-8 Markaz, Islamabad, Pakistan Dera Allah Yar Sindhi Muslim Housing Society Phone # (92 51)2260636, 2856950 Jaffarabad Airport Road, Sukkur Fax # (92 51)2254678 Phone # 0838-510912 Phone # (92-71) 5633615 [email protected] [email protected] [email protected] Sahil Referral Unit, Abbotabad Sahil Referral Unit, Lahore House # 686-C, Faisal Town Makhdoom Colony, Nari road Sahil Toll Free Line: 0800-13518 Mandian, Purana Ayub Medical Lahore College Website: www.sahil.org Phone: 92-42-35165357 Abbotabad [email protected] Phone # (92-992) 383880 [email protected] T 2010 Contents Foreword 01 Report Highlights 02 Definitions Of Child Sexual Abuse 03 Objectives of the Report 04 Methodology 04 Limitations of the Report 05 Presentation of Statistical Data 05 Newspaper Reported Cases 2010 06 The Gender Divide 06 Crime Categories 07 Abuser’s Categories 10 Age of Victims 12 Places of Abuse 14 Time Period of Abuse 15 Geographical Area of Crime 16 Reporting Issues 17 Case Registration with Police 18 Court Convictions of CSA Cases in 2010 18 Court Convictions of CSA Cases by Sahil 20 Sahil’s Juvenile Data 21 Parental Guidance for Protection of Children 22 Recommendations 24 Annexure -1: List of Newspapers 25 Annexure -2: List of Cities 26 2010 Foreword: Child sexual abuse is a global issue which expands its vicious impression not only on the individual or a family but on the whole society. -
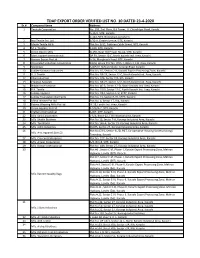
TDAP EXPORT ORDER VERIFIED LIST NO. 10 DATED 23-4-2020 Sr.# Company Name Address 1 Texstyle Corporation No
TDAP EXPORT ORDER VERIFIED LIST NO. 10 DATED 23-4-2020 Sr.# Company Name Address 1 Texstyle Corporation No. 208, 2nd Floor, Gul Tower, I.I. Chundrigar Road, Kaachi. A-15/C, SITE, Karachi. C-144, SITE, Nooriabad, Jamshoro. 2 Naz Textile Pvt. Ltd. E/32-A, Estate Avenue, SITE, Karachi. 3 Maple Textile Mills Plot No. B-32, Pakistan Cable Street, SITE, Karachi. 4 M. J. Textiles F-610, SITE, Karachi. 5 Union Denim Mills D-255, Near Old Power House, SITE, Karachi. 6 Mass Apparel International DP 59, Sector 12-C, North Karachi Ind. Area, Karachi. 7 Haroon Export Pvt Ltd. A-26, Manghopir Road, SITE, Karachi. 8 Associated Industries Corporation Siddiq House Plot No. WSA-1, Block 3, F.B. Area, Karachi. 9 Starimpex A-8/517, Akhtar Colony, Korangi Road, Karachi. 10 Jubilee Knitwear Industries Plot No. 10, Sector C-III, Karachi Export Processing Zone, Karachi. 11 A.U. Textile Plot No. DP-73, Sector 12-C, North Karachi Ind. Area, Karachi. 12 Khas Industries Plot No. 326, Sector 7/A, KIA, Karachi. 13 Creative Apparels Plot No. DP-72, Sector 12-C, North Karachi Ind. Area, Karachi. 14 Nabiha International Plot No. 46-3, Sector 12-D, North Karachi Ind. Area, Karachi. 15 B.K. Textile Plot No. 25/9, Sector 12-C, North Karachi Ind. Area, Karachi. 16 Jubilee Apparel Plot No. 2&3, Sector A-IV, KEPZ, Karachi. 17 Jubilee Foundation Garments Plot No. 15, Sector B-VII, KEPZ, Karachi. 18 Mima Leather Pvt Ltd. Plot No. 4, Sector 17, KIA, Karachi. 19 Fatima Weaving Mills Pvt Ltd. -

View of the Above, the Government of Sindh (Gos) Has Decided to Build, Own and Operate Generation Facilities at Various Industrial Estates of the Province
National Electric Power Regulatory Authority nann Islamic Republic of Pakistan NEPRA Tower, Attaturk Avenue (East), G-511, Islamabad Registrar Ph:+92-51-9206500, Fax: +92-51-2600026 Web: www.nepra.org.pk, E-mail: [email protected] No. NEPRA/R/DL/LAG-279/ (c c 3 July 15, 2015 Mr. Najam UI Hasnain, Chief Executive Officer, Sindh Nooriabad Power Company (Pvt.) Limited, 28, Army Housing Scheme, National Stadium Colony, Karachi. Subject: Generation Licence No. IGSPL/63/2015 Licence Application No. LAG-279 Sindh Nooriabad Power Company (Pvt.) Limited (SNPCPL) Reference: Your application vide letter No. Nil, dated Nil, received on August 21, 2014. Enclosed please find herewith Generation Licence No. IGSPL/63/2015 granted by National Electric Power Regulatory Authority (NEPRA) to Sindh Nooriabad Power Company (Pvt.) Limited, pursuant to Section 15 of the Regulation of Generation, Transmission and Distribution of Electric Power Act (XL of 1997). Further, the determination of the Authority in the subject matter is also attached. 2. Please quote above mentioned Generation Licence No. for future correspondence. Enclosure: Generation Licence (IGSPL/63/2015) Vq‘ (Syed Safeer Hussain) AS Copy to: 1. Chief Executive Officer, Hyderabad E y Limited (HESCO), Old State Bank Building, G.O.R Colony, Hy 2. Chief Executive Officer, K-Electric Ltd, K , Sunset Boulevard, Phase-II, DHA, Karachi. 3. Chief Executive Officer, NTDC, 414-WAPDA House, Lahore 4. Chief Operating Officer, CPPA-G, 107-WAPDA House, Lahore 5. Director General, Environment and Alternative Energy Department, Government of Sindh, Plot No ST/2/1, Sector 23, Korangi Industrial Area, Karachi. th 6. -

NGO Resource Centre (A Project of Aga Khan Foundation)
NGO Resource Centre (A Project of Aga Khan Foundation) VI pHoo Directory of Intermediary NGOs in Pakistan NGO Resource Centre (A Project of Aga Khan Foundation) Copyrights © NGO Resource Centre, 2000 NGO Resource Centre (A project of Aga Khan Foundation) D-114, Block 5, Clifton, Karachi-75600, Pakistan Tel:92-21-586 5501, 586 5502 Fax:92-21-586 5503 Email: [email protected], [email protected] LIBRARY JBCGUE to Contents Preface Introduction i Background Methodology Limitations Criteria Typology Sectoral Analysis v How to use this directory x Abbreviations xi Thematic Preference Matrix xiv List of Intermediary NGOs xxi Directory 1 Annex A: NGOs - Thematic Area wise 147 Annex B: NGOs - Operation Area wise 156 Annex C: List of NGOs Contacted 162 Annex D: List of NGOs Not Included 165 Annex E: Questionnaire 166 Preface Forming the pivotal second-tier of the citizen-sector, mid-level or intermediary NGOs are increasingly being recognized as the lifeline of citizens-led development initiatives. Distinct from small grass-root or community based organizations, these mid-level groups are managed and run by professional paid staff to provide development related services and resources in their area of operation which is invariably sizeable-up to country, province or at least district level. Regrettably, however, the understanding of the citizen sector in Pakistan continues to be confused as a rule. This can partly be attributed to the acute dearth of reliable data and information about civil society institutions. Much of the available information is sketchy and generalized and does not take into account the inter-sectoral diversities and gradations. -

Sindhuniversityresearch
SindhUniv. Res. Jour. (Sci. Ser.) Vol. 52 (04) 353-362 (2020) http://doi.org/10.26692/sujo/2020.12.53 SINDHUNIVERSITYRESEARCHJOURNAL(SCIENCE SERIES) Exploration of Iron Ore Deposits of Aliabad Area Jamshoro District Southern Indus Basin, Sindh, Pakistan M. A. JAMALI, A. H. MARKHAND, M. R. KHASKHELI++*, M. H. AGHEEM, A. G. SAHITO, S. LAGHARI, A. Y. W. ARAIN Centre for Pure and Applied Geology, University of Sindh, Jamshoro, Pakistan Received 20th January 2020 and Revised 11th July 2020 Abstract: Geophysical and Geochemical investigations were carried out at the exposed rocks around Aliabad area near Jamshoro city in Sindh, for the exploration of iron ore deposit. An area of 2.5 km2 has been covered through detailed ground magnetic survey at the line interval of 500m and station interval of 100m. Magnetic data interpreted that only 27nT magnetic signature occurs in study area. 2D and 3D magnetic maps interpreted that magnetic response was very low due to the presence of hematite type iron ore deposits. Total eight samples of iron ore were collected along profile with different interval and analyzed in scanning electron microscope (SEM) and energy dispersive x-ray spectroscopy (EDS). SEM data shows the highest peaks of iron, silicon and oxygen. That indicates the composition of quartz and iron, color of samples is dark grey to light grey and texture is medium to fine grains, the whitish color grains indicate the iron and dark grey grains indicate the Quartz is present in SEM image. The discrimination of geochemical data particularly the Harker’s bivariate plots indicate the source being rich in silicon dioxide and iron. -

SINDH Power Company (Pvt) Limited
SINDH Power Company (Pvt) Limited SCHEDULE I (Regulation 3(1)) FORM OF APPLICATION The Registrar National Electric Power Regulatory Authority Subject: Application for a GENERATION License I, Commodore (Retd) Najam ul Hasnain. CEO and Khurshid Anwar Jamali. Director. being the duly authorized representatives of Sind Nooriabad Power Company (Pvt) Ltd by virtue of BOARD RESOLUTION dated 15/07/2014. hereby apply to the National Electric Power Regulatory Authority for the grant of a GENERATION LICENCSE to the Sind Nooriabad Power Company (Pvt) Ltd pursuant to section 15 of the Regulation of Generation. Transmission and Distribution of Electric Power Act. 1997. I certify that the documents-in-support attached with this application are prepared and submitted in conformity with the provisions of the National Electric Power Regulator) Authority Licensing (Application and Modification Procedure) Regulations, 1999. and undertake to abide by the terms and provisions of the above-said regulations. 1 further undertake and confirm that the information provided in the attached documents-in-support is true and correct to the best of m knowledge and belief. A BANK DRAFT in the sum of Rupees 338.000.00, being the non-refundable license application fee calculated in accordance with Schedule 11 to the National Electric Power Regulatory Authority Licensing (Application and Modification Procedure) Regulations, 1999, is also attached herewith. \s, NAJAN1 J1_ HASNAIN Commodore (Retd) CEO 28, Army Housing Scheme, National Stadium Colony, Karachi 75260 Phone: +92 21 3483 8755-56; Fax +92 21 3483 8757, infc4/snpc.com.pk SECURITIES AND EXCHANGE COMM iSSION OF PAKISTAN COMPANY REGISTRATION OFFICE, KARACHI • CERTIFICATE OF INCORPORATION , • • [Under section 32 of the Companies Ordinance, t984tXLVII of 1984)] Corporate Universal Identification No. -

Pakistan, First Quarter 2018
PAKISTAN, FIRST QUARTER 2018: Update on incidents according to the Armed Conflict Location & Event Data Project (ACLED) - Updated 2nd edition compiled by ACCORD, 20 December 2018 Number of reported incidents with at least one fatality Number of reported fatalities National borders: GADM, November 2015a; administrative divisions: GADM, November 2015b; China/India border status: CIA, 2006; Kashmir border status: CIA, 2004; geodata of disputed borders: GADM, November 2015a; Natural Earth, undated; incident data: ACLED, 15 December 2018; coastlines and inland waters: Smith and Wessel, 1 May 2015 PAKISTAN, FIRST QUARTER 2018: UPDATE ON INCIDENTS ACCORDING TO THE ARMED CONFLICT LOCATION & EVENT DATA PROJECT (ACLED) - UPDATED 2ND EDITION COMPILED BY ACCORD, 20 DECEMBER 2018 Contents Conflict incidents by category Number of Number of reported fatalities 1 Number of Number of Category incidents with at incidents fatalities Number of reported incidents with at least one fatality 1 least one fatality Riots/protests 1266 2 3 Conflict incidents by category 2 Battles 68 48 133 Development of conflict incidents from March 2016 to March 2018 2 Remote violence 37 17 33 Violence against civilians 22 12 18 Methodology 3 Strategic developments 16 0 0 Conflict incidents per province 4 Total 1409 79 187 This table is based on data from ACLED (datasets used: ACLED, 15 December 2018). Localization of conflict incidents 4 Disclaimer 5 Development of conflict incidents from March 2016 to March 2018 This graph is based on data from ACLED (datasets used: ACLED, 15 December 2018). 2 PAKISTAN, FIRST QUARTER 2018: UPDATE ON INCIDENTS ACCORDING TO THE ARMED CONFLICT LOCATION & EVENT DATA PROJECT (ACLED) - UPDATED 2ND EDITION COMPILED BY ACCORD, 20 DECEMBER 2018 Methodology Geographic map data is primarily based on GADM, complemented with other sources if necessary. -

Triconboston Cino.� - Private Limited
TriconBoston cino. - Private Limited The Registrar, National Electric Power Regulatory Authority Subject: Application for a Generation License TBCCPL-C 50MW Wind Power Project I, Nadeem Abdullah, Chief Executive Officer, being the duly authorized representative of TriconBoston Consulting Corporation (Private) Limited by virtue of board resolution dated 28 September 2015, hereby apply to the National Electric Power Regulatory Authority for the grant of a Generation License to TriconBoston Consulting Corporation (Private) Limited pursuant to section 15 of the Regulation of Generation, Transmission and Distribution rl....of Electric Power Act, 1997. I certify that the documents-in-support attached with this application are prepared an submitted in conformity with the provisions of the National Electric Power Regulato Authority Licensing (Application and Modification Procedure) Regulations, 1999, an -- undertake to abide by the terms and provisions of the above-said regulations. I further undertake and confirm that the information provided in the attached documents-in-support is true and correct to the best of my knowledge and belief. A bank draft in the sum of PKR 280,640 (Pakistan Rupees Two I kindred Eighty Thousand Six Hundred Forty), being the non-refundable licence application fee calculated in accordance with Schedule II to the National Electric Power Regulatory Authority Licensing (Application and Modification Procedure) Regulations, 1999, is also attached herewith. Date: 2nd October 2015 Nadeem Abdullah CEO Company Seal A Project