T300 User Manual CONTENT
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Ten Steps to Smartphone Security
Ten Steps to Smartphone Security Smartphones continue to grow in popularity and are now as powerful and functional as many computers. It is important to protect your smartphone just like you protect your computer as mobile cybersecurity threats are growing. These mobile security tips can help you reduce the risk of exposure to mobile security threats: 1. Set PINs and passwords. To prevent unauthorized access to your phone, set a password or Personal Identification Number (PIN) on your phone’s home screen as a first line of defense in case your phone is lost or stolen. When possible, use a different password for each of your important log-ins (email, banking, personal sites, etc.). You should configure your phone to automatically lock after five minutes or less when your phone is idle, as well as use the SIM password capability available on most smartphones. 2. Do not modify your smartphone’s security settings. Do not alter security settings for convenience. Tampering with your phone’s factory settings, jailbreaking, or rooting your phone undermines the built-in security features offered by your wireless service and smartphone, while making it more susceptible to an attack. 3. Backup and secure your data. You should backup all of the data stored on your phone – such as your contacts, documents, and photos. These files can be stored on your computer, on a removal storage card, or in the cloud. This will allow you to conveniently restore the information to your phone should it be lost, stolen, or otherwise erased. 4. Only install apps from trusted sources. -

SMS “Virtual Collection Center” Smartphone
Feed the Future Innovation Lab for Livestock Systems INNOVATION SUMMARY: SMS “VIRTUAL COLLECTION CENTER” SMARTPHONE APP The Virtual Collection Center (VCC) is an innovative short message service (SMS) mobile application (app) for improved goat marketing. Through the use of the VCC app, inventory updates flow from cooperative members to leaders, while cooperative leaders use the VCC app to share price information with members and fill orders from traders by inviting members to sales events. The VCC app improves the goat value chain by reducing transaction costs, which should strengthen cooperatives and benefit small livestock producers by increasing trade volumes. Lead Implementing Institution: University of Florida Category: Marketing & Distribution Applied in: Nepal The VCC app is implemented by Heifer International Nepal whose Innovation Type: Technology New/Adapted: New field personnel assist cooperative members in downloading the app while providing training and Created for: Mainly Women Nutrition Linkage: Dietary Quality monitoring in the initial stages. The app is designed to be intuitive, eliminating the need for intensive training. Within cooperatives, the In Nepal, goats are an essential source of income and nearly every rural Nepali household app is accessed by “VCC owns at least a few goats. To buy goats, traders often travel over large areas characterized managers”, who are members of cooperative self-help groups by rugged terrain and poor infrastructure, making multiple visits to individual households necessary to complete sales. The resulting high transaction costs can stifle the value chain. (subgroups within the Cooperatives can reduce transaction costs by allowing for bulk purchases of animals. But cooperatives), and cooperative cooperatives may struggle to coordinate sales by members spread out over large areas of leaders. -

The Classic Blackberry – Supercharged
COMING SOON! The classic BlackBerry – supercharged. BlackBerry® Curve™ 3G smartphone The new BlackBerry Curve 3G smartphone from AT&T is BlackBerry Curve 3G powerful yet affordable. This BlackBerry classic now gives smartphone you 3G speed and everything you expect from the popular The first 3G Curve BlackBerry Curve family, with a QWERTY keyboard, work and from AT&T. personal email, powerful personal management capabilities and much more. A superior connection. • Be at the forefront. With simultaneous voice and data when using the 3G or Wi-Fi network, you can check the facts on email or the web while talking on the phone with clients or colleagues. • Work with speed and confidence. The BlackBerry Curve 3G • Speed with flexibility. The BlackBerry Curve 3G smartphone has a powerful 624 MHz processor, 256 MB flash smartphone allows you to quickly download and upload memory/256 MB SDRAM and an included 2 GB microSD™ card content and surf the web faster on the nation’s fastest for storage, expandable up to 32 GB. broadband mobile network.* And with built-in Wi-Fi® • Focused applications. Keep up-to-date and informed of your (802.11 b/g/n), access the information and download the work and life – explore BlackBerry® App World™ and pre-loaded large files you need at Wi-Fi speeds. applications including LinkedIn™, My-Cast® Weather, Bloomberg® • Automatically unlimited. The new BlackBerry Curve 3G Mobile, AllSport GPS™, WHERE®, City ID®, Facebook®, MySpace™, smartphone automatically connects to AT&T Wi-Fi Hot Twitter™ and more. Spots in the U.S.** for unlimited usage on the AT&T Wi-Fi • Capture the moment. -

Set up Installing the Memory Card
Set up Installing the memory card Installing the USIM cards In order to use all functions of NGM Explorer, it is advisable to install a micro‐SD card: it must be inserted in the back side of The USIM card stores information as your personal phone the phone, after powering it off and removing the battery. A number, PIN code, carrier services numbers, contacts and other dedicated slot fort the memory card is placed under the USIM1‐ important details. To access the USIM slots, turn off the phone, slot. Unlock the micro‐SD grid by pushing it into the “Open” take off the back cover by unscrewing the two big screws on the direction. Slide in the memory card into the opened metallic cover and lifting it up and extract the battery. Insert USIM2 by grid so that the gold contacts will be facing downwards when sliding it with its golden contacts facing downwards. USIM1 you close the grid. Close the grid and push it into the “Lock” supports WCDMA, it should be installed after installing the position. memory card since its slot contains the micro‐SD slot. Open the metallic grid by pushing it into the “open” position. Insert the USIM card into the metallic grid so that the metallic contact will be turned downwards when you close the grid. Push the grid into the “Lock” direction to close it. micro USIM1: UMTS or GSM SD USIM2: GSM Inserting the battery Charging the battery Your device is provided with a lithium‐ion battery and is Please charge the battery completely before starting to use the designed to be used exclusively with original NGM batteries and device. -

Digi Trustfence Integrated, Tested and Future-Proof Security DIGI.COM | PUBLIC | © DIGI INTERNATIONAL, INC
CONNECT WITH CONFIDENCE DIGI CONNECTCORE 6UL IOT EMBEDDED MODULE TRUSTFENCE EMBEDDED IOT SECURITY FRAMEWORK 1 DIGI.COM | PUBLIC | © DIGI INTERNATIONAL, INC. STRENGTH IN NUMBERS 285 100M 25K PATENTS ISSUED THINGS CUSTOMERS AND PENDING CONNECTED DGII 1985 515 14 204 137 Year Employees Consecutive Years Million In Million NASDAQ Founded Worldwide of Profitability Revenue In Cash 2DIGI.COM | PUBLIC | © DIGI INTERNATIONAL, INC. EXTENSIVE GLOBAL REACH North EMEA APAC America Global 50 71 34 5 Latin Digi Offices America 27 Distribution Partners HQ 15 200+ 180+ 800+ Minnetonka, MN Regional Digi Channel Channel USA Offices Technical Resources Partners Technical Resources 3DIGI.COM | PUBLIC | © DIGI INTERNATIONAL, INC. BRING CONNECTIVITY TO ANY DEVICE CREATE DEPLOY MANAGE RF & EMBEDDED CELLULAR ROUTERS DIGI REMOTE MANAGER MODULES & SBCs AND GATEWAYS DIGI DEVICE CLOUD CUSTOM DESIGN SERVICES DEVICE NETWORKING COLD CHAIN SOLUTIONS 4 DIGI.COM | PUBLIC | © DIGI INTERNATIONAL, INC. DIGI EMBEDDED BENEFITS Integrated 802.11 a/b/g/n/ac networking options Network Connectivity Bluetooth Smart Ready options on selected modules Single or dual Ethernet Design change notifications/approvals Process Control and Strong 5-year hardware warranty Reliability Stringent environmental testing to meet reliability requirements Design flexibility without the traditional complexity Quick Time-to-Market Pre-certified system on module solutions Complete out-of-box software support + design services Long-Term Availability Selected NXP i.MX application processors -

Lumia with Windows 10 Mobile User Guide
User Guide Lumia with Windows 10 Mobile Issue 1.0 EN About this user guide This guide is the user guide for your software release. Important: For important info on the safe use of your device and battery, read “For your safety” and “Product and safety info” in the printed or in-device user guide, or at www.microsoft.com/mobile/support before you take the device into use. To find out how to get started with your new device, read the printed user guide. For the online user guidance, videos, even more info, and troubleshooting help, go to support.microsoft.com, and browse to the instructions for Windows phones. You can also check out the support videos at www.youtube.com/lumiasupport. Moreover, there's a user guide in your phone – it's always with you, available when needed. To find answers to your questions and to get helpful tips, tap Lumia Help+Tips. If you’re new to Lumia, check out the section for new users. © 2015 Microsoft Mobile. All rights reserved. 2 User Guide Lumia with Windows 10 Mobile Contents For your safety 5 Calls 62 Get started 6 Contacts 66 Switch the phone on 6 Social networks 70 Lock the keys and screen 7 Messages 72 Charge your phone 7 Mail 76 Your first Lumia? 10 Camera 81 Learn more about your phone 10 Open your camera quickly 81 Set up your phone 10 Camera basics 81 Explore your tiles, apps, and settings 11 Advanced photography 83 Navigate inside an app 14 Photos and videos 85 Use the touch screen 15 Maps & navigation 88 Back, start, and search keys 17 Switch location services on 88 Transfer content to your Lumia -
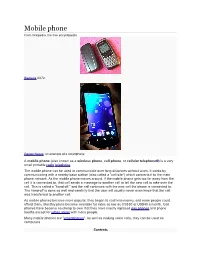
Mobile Phone from Wikipedia, the Free Encyclopedia
Mobile phone From Wikipedia, the free encyclopedia Siemens AX72. Galaxy Nexus, an example of a smartphone A mobile phone (also known as a wireless phone, cell phone, or cellular telephone[1]) is a very small portable radio telephone. The mobile phone can be used to communicate over long distances without wires. It works by communicating with a nearby base station (also called a "cell site") which connects it to the main phone network. As the mobile phone moves around, if the mobile phone gets too far away from the cell it is connected to, that cell sends a message to another cell to tell the new cell to take over the call. This is called a "hand off," and the call continues with the new cell the phone is connected to. The hand-off is done so well and carefully that the user will usually never even know that the call was transferred to another cell. As mobile phones became more popular, they began to cost less money, and more people could afford them. Monthly plans became available for rates as low as US$30 or US$40 a month. Cell phones have become so cheap to own that they have mostly replaced pay phones and phone booths except for urban areas with many people. Many mobile phones are "smartphones". As well as making voice calls, they can be used as computers. Contents [hide] 1 History 2 Technology 3 Shapes 4 How mobile phones work 5 Networks and payment 6 Smartphones 7 References History[change | change source] Mobile phones in the 1950s through 1970s were large and heavy, and most were built into cars. -

A Comparative Analysis of Mobile Operating Systems Rina
International Journal of Computer Sciences and Engineering Open Access Research Paper Vol.-6, Issue-12, Dec 2018 E-ISSN: 2347-2693 A Comparative Analysis of mobile Operating Systems Rina Dept of IT, GGDSD College, Chandigarh ,India *Corresponding Author: [email protected] Available online at: www.ijcseonline.org Accepted: 09/Dec/2018, Published: 31/Dec/2018 Abstract: The paper is based on the review of several research studies carried out on different mobile operating systems. A mobile operating system (or mobile OS) is an operating system for phones, tablets, smart watches, or other mobile devices which acts as an interface between users and mobiles. The use of mobile devices in our life is ever increasing. Nowadays everyone is using mobile phones from a lay man to businessmen to fulfill their basic requirements of life. We cannot even imagine our life without mobile phones. Therefore, it becomes very difficult for the mobile industries to provide best features and easy to use interface to its customer. Due to rapid advancement of the technology, the mobile industry is also continuously growing. The paper attempts to give a comparative study of operating systems used in mobile phones on the basis of their features, user interface and many more factors. Keywords: Mobile Operating system, iOS, Android, Smartphone, Windows. I. INTRUDUCTION concludes research work with future use of mobile technology. Mobile operating system is the interface between user and mobile phones to communicate and it provides many more II. HISTORY features which is essential to run mobile devices. It manages all the resources to be used in an efficient way and provides The term smart phone was first described by the company a user friendly interface to the users. -

Maxphone—Multi-Access Extension for Smartphones Fact Sheet
Completed DHS Science and Technology Directorate MaXphone—Multi-Access Extension for Smartphones Providing devices that embrace Land Mobile P25, cellular/Public Switched Telephone Network voice, Radio (LMR) and broadband cellular networks and Voice-over-IP. It also allows for enhanced security by The First Responder Network Authority (FirstNet) is providing end-to-end P25 encryption across LMR and charged with creating a nationwide public safety broadband broadband networks. network that provides the public safety community with a Enabling customizable, affordable applications boost in network capacity and capability. Still, commercial MaXphone leverages rapid development in commercial cellular broadband networks (e.g., 4G LTE and 3G) will broadband networks and smartphone capability. Open likely remain the dominant option to support first responder application development environments (e.g., Android) broadband applications for the immediate future. enable novel, innovative, customizable and affordable first Broadband networks do not provide first responders with responder applications. An open source, fully functioning mission critical voice capabilities (i.e., radio-to-radio or P25 software package will be available on the Android one-to-many communications) that are available on LMR environment. MaxJacket will be based on COTS networks. However, application and service development in components and contain the necessary functions for the P25 the LMR domain stand in stark contrast to the explosive solution. growth in the commercial broadband sector. Therefore, a reasonable, cost effective approach to creating more capable first responder devices embraces existing LMR networks Legacy P25 handset and commercial broadband cellular networks by using open P25 platforms to encourage application development. IP25 P25 Network Gateway Access The Department of Homeland Security Science and Technology Directorate and U.S. -

Risks and Rewards of the Anytime-Anywhere Internet Risks and Rewards of the Anytime-Anywhere Internet
Research Collection Monograph ON/OFF: Risks and Rewards of the Anytime-Anywhere Internet Risks and Rewards of the Anytime-Anywhere Internet Author(s): Genner, Sarah Publication Date: 2017 Permanent Link: https://doi.org/10.3929/ethz-a-010805600 Originally published in: http://doi.org/10.3218/3800-2 Rights / License: Creative Commons Attribution-NonCommercial 3.0 Unported This page was generated automatically upon download from the ETH Zurich Research Collection. For more information please consult the Terms of use. ETH Library ON | OFF Risks and Rewards of the Anytime-Anywhere Internet Sarah Genner This work was accepted as a PhD thesis by the Faculty of Arts and Social Sciences, University of Zurich in the spring semester 2016 on the recommendation of the Doctoral Committee: Prof. Dr. Daniel Sü ss (main supervisor, University of Zurich, Switzerland) and Prof. Dr. Urs Gasser (Harvard University, USA). Published with the support of the Swiss National Science Foundation. Bibliographic Information published by Die Deutsche Nationalbibliothek Die Deutsche Nationalbibliothek lists this publication in the Internet at http://dnb.d-nb.de. This work is licensed under Creative Commons license CC BY-NC-SA 3.0. Cover photo: fl ickr.com/photos/zuerichs-strassen © 2017, vdf Hochschulverlag AG an der ETH Zürich ISBN 978-3-7281-3799-9 (Print) ISBN 978-3-7281-3800-2 (Open Access) DOI 10.3218/3800-2 www.vdf.ethz.ch [email protected] Table of Contents Preface ................................................................................................................................... -

Award Win at First Time of Asking
ISSUE 03 VOLUME 17 Award win at first time of asking As a boutique developer specialising in high-end residential schemes, Surrey- based Twist’s quality-led approach was epitomised on its recent The Mansion at Sondes Place project in Dorking, which showcased the very best of its skills. Contents ISSUE_03.2019 News 4 News Section 12 Topping Out Anniversary 13 Gap group Ltd AWARDS 25 Tavener Joinery 26 Intium Construction Ltd 27 Valeo Management Limited 31 SPAW Construction 32 IDS Irish Door Systems Limited 33 Mainline 9 34 Platinum Property Partners 36 Fleur Developments 40 Twist 42 E.ON Control Solutions 45 Sontay 46 SDA Build London 47 C&W BERRY 26 Company Profile 40 48 Minster Surfacing Ltd 52 Covers 54 Norse Group 27 59 JMS Retail Concepts Ltd 60 Reflex 62 Rilmac Insulation Ltd 63 Harvey Group 64 Point of Rental 66 SCS Group Public Sector 67 Adey Steel Group Waste Management 68 Acorn Waste Management Limited Rospa Awards 54 69 GMG Contractors CONSTRUCTION INDUSTRY NEWS © CODEBLUE MEDIA LIMITED. EDITOR STUDIO MANAGER ALL CONTENTS ARE COPYRIGHT. ALL RIGHTS ARE RESERVED. NO PART OF THE NIGEL MARTIN CHRIS BAGLEY PUBLICATION MAY BE STORED IN ANY RETRIEVAL SYSTEM OR TRANSMITTED T 01484 441 420 E: [email protected] CODEBLUE MEDIA PUBLICATION IN ANY FORM WITHOUT PRIOR WRITTEN PERMISSION FROM THE PUBLISHERS. E [email protected] WHILST EVERY EFFORT IS MADE TO ENSURE ACCURACY, NO RESPONSIBILITY FEATURE TEAM CODEBLUE MEDIA LTD, CAN BE ACCEPTED FOR INACCURACIES HOWEVER CAUSED. CONTRIBUTED EDITORAL STAFF SCOTT RICE 2 SPRING BANK, MATERIAL DOES NOT NECESSARILY REFLECT THE OPINION OF THE PUBLISHER. -

Cyber Trouble
CYBER TROUBLE Printing: one-sided Number of players: 2 and above Scale: actual size (100 %) Age of players: 6–99 years Card game, whose author is CZ.NIC, is subject to a CC BY-NC-SA license. THE WELL MINI-GAME #1 Set-up: deal all the cards, one at a time, to all players, starting with the player who won the last mini-game. Place the last card in the middle of the table, face-up. Each player shuffles his or her cards and makes a draw pile placed before him or her, face down. Object of the game: to be the fastest to get rid of all your cards – make sure you’re not the last! How to play?: On go, the players flip their draw pile face-up. Players must be faster than the others to discard the cards from their draw pile by placing them on the card in the middle. To do that, they have to name the identical symbol between the top card of their draw pile and the card in the middle. As the middle card changes as soon as a player places one of his or her cards on top of it, players must be quick. The winner: The last player to get rid of his or her cards loses the game. THE HOT POTATO MINI-GAME #2 (played over multiple rounds) Set-up: on each round, give each player a card he or she will keep hidden in their hand without looking at it. Set the remai- ning cards aside, they will be used for the subsequent rounds.