Evaluation of Xpath Queries on XML Streams with Networks of Early Nested Word Automata Tom Sebastian
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Towards an Analytics Query Engine *
Towards an Analytics Query Engine ∗ Nantia Makrynioti Vasilis Vassalos Athens University of Economics and Business Athens University of Economics and Business Athens, Greece Athens, Greece [email protected] [email protected] ABSTRACT with black box libraries, evaluating various algorithms for a This vision paper presents new challenges and opportuni- task and tuning their parameters, in order to produce an ef- ties in the area of distributed data analytics, at the core of fective model, is a time-consuming process. Things become which are data mining and machine learning. At first, we even more complicated when we want to leverage paralleliza- provide an overview of the current state of the art in the area tion on clusters of independent computers for processing big and then analyse two aspects of data analytics systems, se- data. Details concerning load balancing, scheduling or fault mantics and optimization. We argue that these aspects will tolerance can be quite overwhelming even for an experienced emerge as important issues for the data management com- software engineer. munity in the next years and propose promising research Research in the data management domain recently started directions for solving them. tackling the above issues by developing systems for large- scale analytics that aim at providing higher-level primitives for building data mining and machine learning algorithms, Keywords as well as hiding low-level details of distributed execution. Data analytics, Declarative machine learning, Distributed MapReduce [12] and Dryad [16] were the first frameworks processing that paved the way. However, these initial efforts suffered from low usability, as they offered expressive but at the same 1. -

QUERYING JSON and XML Performance Evaluation of Querying Tools for Offline-Enabled Web Applications
QUERYING JSON AND XML Performance evaluation of querying tools for offline-enabled web applications Master Degree Project in Informatics One year Level 30 ECTS Spring term 2012 Adrian Hellström Supervisor: Henrik Gustavsson Examiner: Birgitta Lindström Querying JSON and XML Submitted by Adrian Hellström to the University of Skövde as a final year project towards the degree of M.Sc. in the School of Humanities and Informatics. The project has been supervised by Henrik Gustavsson. 2012-06-03 I hereby certify that all material in this final year project which is not my own work has been identified and that no work is included for which a degree has already been conferred on me. Signature: ___________________________________________ Abstract This article explores the viability of third-party JSON tools as an alternative to XML when an application requires querying and filtering of data, as well as how the application deviates between browsers. We examine and describe the querying alternatives as well as the technologies we worked with and used in the application. The application is built using HTML 5 features such as local storage and canvas, and is benchmarked in Internet Explorer, Chrome and Firefox. The application built is an animated infographical display that uses querying functions in JSON and XML to filter values from a dataset and then display them through the HTML5 canvas technology. The results were in favor of JSON and suggested that using third-party tools did not impact performance compared to native XML functions. In addition, the usage of JSON enabled easier development and cross-browser compatibility. Further research is proposed to examine document-based data filtering as well as investigating why performance deviated between toolsets. -

Programming a Parallel Future
Programming a Parallel Future Joseph M. Hellerstein Electrical Engineering and Computer Sciences University of California at Berkeley Technical Report No. UCB/EECS-2008-144 http://www.eecs.berkeley.edu/Pubs/TechRpts/2008/EECS-2008-144.html November 7, 2008 Copyright 2008, by the author(s). All rights reserved. Permission to make digital or hard copies of all or part of this work for personal or classroom use is granted without fee provided that copies are not made or distributed for profit or commercial advantage and that copies bear this notice and the full citation on the first page. To copy otherwise, to republish, to post on servers or to redistribute to lists, requires prior specific permission. Programming a Parallel Future Joe Hellerstein UC Berkeley Computer Science Things change fast in computer science, but odds are good that they will change especially fast in the next few years. Much of this change centers on the shift toward parallel computing. In the short term, parallelism will thrive in settings with massive datasets and analytics. Longer term, the shift to parallelism will impact all software. In this note, I’ll outline some key changes that have recently taken place in the computer industry, show why existing software systems are ill‐equipped to handle this new reality, and point toward some bright spots on the horizon. Technology Trends: A Divergence in Moore’s Law Like many changes in computer science, the rapid drive toward parallel computing is a function of technology trends in hardware. Most technology watchers are familiar with Moore's Law, and the general notion that computing performance per dollar has grown at an exponential rate — doubling about every 18‐24 months — over the last 50 years. -

Declarative Data Analytics: a Survey
Declarative Data Analytics: a Survey NANTIA MAKRYNIOTI, Athens University of Economics and Business, Greece VASILIS VASSALOS, Athens University of Economics and Business, Greece The area of declarative data analytics explores the application of the declarative paradigm on data science and machine learning. It proposes declarative languages for expressing data analysis tasks and develops systems which optimize programs written in those languages. The execution engine can be either centralized or distributed, as the declarative paradigm advocates independence from particular physical implementations. The survey explores a wide range of declarative data analysis frameworks by examining both the programming model and the optimization techniques used, in order to provide conclusions on the current state of the art in the area and identify open challenges. CCS Concepts: • General and reference → Surveys and overviews; • Information systems → Data analytics; Data mining; • Computing methodologies → Machine learning approaches; • Software and its engineering → Domain specific languages; Data flow languages; Additional Key Words and Phrases: Declarative Programming, Data Science, Machine Learning, Large-scale Analytics ACM Reference Format: Nantia Makrynioti and Vasilis Vassalos. 2019. Declarative Data Analytics: a Survey. 1, 1 (February 2019), 36 pages. https://doi.org/10.1145/nnnnnnn.nnnnnnn 1 INTRODUCTION With the rapid growth of world wide web (WWW) and the development of social networks, the available amount of data has exploded. This availability has encouraged many companies and organizations in recent years to collect and analyse data, in order to extract information and gain valuable knowledge. At the same time hardware cost has decreased, so storage and processing of big data is not prohibitively expensive even for smaller companies. -

Big Data Analytic Approaches Classification
Big Data Analytic Approaches Classification Yudith Cardinale1 and Sonia Guehis2,3 and Marta Rukoz2,3 1Dept. de Computacion,´ Universidad Simon´ Bol´ıvar, Venezuela 2Universite´ Paris Nanterre, 92001 Nanterre, France 3Universite´ Paris Dauphine, PSL Research University, CNRS, UMR[7243], LAMSADE, 75016 Paris, France Keywords: Big Data Analytic, Analytic Models for Big Data, Analytical Data Management Applications. Abstract: Analytical data management applications, affected by the explosion of the amount of generated data in the context of Big Data, are shifting away their analytical databases towards a vast landscape of architectural solutions combining storage techniques, programming models, languages, and tools. To support users in the hard task of deciding which Big Data solution is the most appropriate according to their specific requirements, we propose a generic architecture to classify analytical approaches. We also establish a classification of the existing query languages, based on the facilities provided to access the Big Data architectures. Moreover, to evaluate different solutions, we propose a set of criteria of comparison, such as OLAP support, scalability, and fault tolerance support. We classify different existing Big Data analytics solutions according to our proposed generic architecture and qualitatively evaluate them in terms of the criteria of comparison. We illustrate how our proposed generic architecture can be used to decide which Big Data analytic approach is suitable in the context of several use cases. 1 INTRODUCTION nally, despite these increases in scale and complexity, users still expect to be able to query data at interac- The term Big Data has been coined for represent- tive speeds. In this context, several enterprises such ing the challenge to support a continuous increase as Internet companies and Social Network associa- on the computational power that produces an over- tions have proposed their own analytical approaches, whelming flow of data (Kune et al., 2016). -

A Dataflow Language for Large Scale Processing of RDF Data
SYRql: A Dataflow Language for Large Scale Processing of RDF Data Fadi Maali1, Padmashree Ravindra2, Kemafor Anyanwu2, and Stefan Decker1 1 Insight Centre for Data Analytics, National University of Ireland Galway {fadi.maali,stefan.decker}@insight-centre.org 2 Department of Computer Science, North Carolina State University, Raleigh, NC {pravind2,kogan}@ncsu.edu Abstract. The recent big data movement resulted in a surge of activity on layering declarative languages on top of distributed computation plat- forms. In the Semantic Web realm, this surge of analytics languages was not reflected despite the significant growth in the available RDF data. Consequently, when analysing large RDF datasets, users are left with two main options: using SPARQL or using an existing non-RDF-specific big data language, both with its own limitations. The pure declarative nature of SPARQL and the high cost of evaluation can be limiting in some scenarios. On the other hand, existing big data languages are de- signed mainly for tabular data and, therefore, applying them to RDF data results in verbose, unreadable, and sometimes inefficient scripts. In this paper, we introduce SYRql, a dataflow language designed to process RDF data at a large scale. SYRql blends concepts from both SPARQL and existing big data languages. We formally define a closed algebra that underlies SYRql and discuss its properties and some unique optimisation opportunities this algebra provides. Furthermore, we describe an imple- mentation that translates SYRql scripts into a series of MapReduce jobs and compare the performance to other big data processing languages. 1 Introduction Declarative query languages have been a corner stone of data management since the early days of relational databases. -

Extracting Data from Nosql Databases a Step Towards Interactive Visual Analysis of Nosql Data Master of Science Thesis
Extracting Data from NoSQL Databases A Step towards Interactive Visual Analysis of NoSQL Data Master of Science Thesis PETTER NÄSHOLM Chalmers University of Technology University of Gothenburg Department of Computer Science and Engineering Göteborg, Sweden, January 2012 The Author grants to Chalmers University of Technology and University of Gothenburg the non-exclusive right to publish the Work electronically and in a non-commercial purpose make it accessible on the Internet. The Author warrants that he/she is the author to the Work, and warrants that the Work does not contain text, pictures or other material that violates copyright law. The Author shall, when transferring the rights of the Work to a third party (for example a publisher or a company), acknowledge the third party about this agreement. If the Author has signed a copyright agreement with a third party regarding the Work, the Author warrants hereby that he/she has obtained any necessary permission from this third party to let Chalmers University of Technology and University of Gothenburg store the Work electronically and make it accessible on the Internet. Extracting Data from NoSQL Databases A Step towards Interactive Visual Analysis of NoSQL Data PETTER NÄSHOLM © PETTER NÄSHOLM, January 2012. Examiner: GRAHAM KEMP Chalmers University of Technology University of Gothenburg Department of Computer Science and Engineering SE-412 96 Göteborg Sweden Telephone + 46 (0)31-772 1000 Department of Computer Science and Engineering Göteborg, Sweden January 2012 Abstract Businesses and organizations today generate increasing volumes of data. Being able to analyze and visualize this data to find trends that can be used as input when making business decisions is an important factor for competitive advan- tage. -

IBM Infosphere Biginsights Version 2.1: Installation Guide Chapter 1
IBM InfoSphere BigInsights Version 2.1 Installation Guide GC19-4100-00 IBM InfoSphere BigInsights Version 2.1 Installation Guide GC19-4100-00 Note Before using this information and the product that it supports, read the information in “Notices and trademarks” on page 89. © Copyright IBM Corporation 2013. US Government Users Restricted Rights – Use, duplication or disclosure restricted by GSA ADP Schedule Contract with IBM Corp. Contents Chapter 1. Introduction to InfoSphere Installing the InfoSphere BigInsights Tools for BigInsights .............1 Eclipse ................58 InfoSphere BigInsights features and architecture . 1 Configuring access to the default task controller . 61 Hadoop Distributed File System (HDFS) ....3 Installing and configuring a Linux Task Controller 61 IBM General Parallel File System ......3 Adaptive MapReduce ..........6 Chapter 5. Upgrading InfoSphere Hadoop MapReduce...........7 BigInsights software .........63 Additional Hadoop technologies.......7 Preparing to upgrade software ........64 Text Analytics .............9 Upgrading InfoSphere BigInsights .......65 IBMBigSQL.............10 Upgrading the InfoSphere BigInsights Tools for InfoSphere BigInsights Console .......11 Eclipse ................68 InfoSphere BigInsights Tools for Eclipse ....11 Migrating from HDFS to GPFS ........68 Integration with other IBM products .....12 Chapter 6. Removing InfoSphere Chapter 2. Planning to install BigInsights software .........71 InfoSphere BigInsights ........15 Removing InfoSphere BigInsights by using scripts 71 Reviewing -

HIL: a High-Level Scripting Language for Entity Integration
HIL: A High-Level Scripting Language for Entity Integration Mauricio Hernández Georgia Koutrika Rajasekar Krishnamurthy IBM Research – Almaden HP Labs IBM Research – Almaden [email protected] [email protected] [email protected] Lucian Popa Ryan Wisnesky IBM Research – Almaden Harvard University [email protected] [email protected] ABSTRACT domain [5, 7], where the important entities and their relationships We introduce HIL, a high-level scripting language for entity res- are extracted and integrated from the underlying documents. We olution and integration. HIL aims at providing the core logic for refer to the process of extracting data from documents, integrating complex data processing flows that aggregate facts from large col- the information, and then building domain-specific entities, as en- lections of structured or unstructured data into clean, unified enti- tity integration.Enablingsuchintegrationinpracticeisachallenge, ties. Such flows typically include many stages of processing that and there is a great need for tools and languages that are high-level start from the outcome of information extraction and continue with but still expressive enough to facilitate the end-to-end development entity resolution, mapping and fusion. A HIL program captures the and maintenance of complex integration flows. overall integration flow through a combination of SQL-like rules There are several techniques that are relevant, at various levels, that link, map, fuse and aggregate entities. A salient feature of for entity integration: information extraction [9], schema match- HIL is the use of logical indexes in its data model to facilitate the ing [20], schema mapping [11], entity resolution [10], data fu- modular construction and aggregation of complex entities. -

Schemas and Types for JSON Data
Schemas and Types for JSON Data: from Theory to Practice Mohamed-Amine Baazizi Dario Colazzo Sorbonne Université, LIP6 UMR 7606 Université Paris-Dauphine, PSL Research University France France [email protected] [email protected] Giorgio Ghelli Carlo Sartiani Dipartimento di Informatica DIMIE Università di Pisa Università della Basilicata Pisa, Italy Potenza, Italy [email protected] [email protected] ABSTRACT CCS CONCEPTS The last few years have seen the fast and ubiquitous diffusion • Information systems → Semi-structured data; • The- of JSON as one of the most widely used formats for publish- ory of computation → Type theory. ing and interchanging data, as it combines the flexibility of semistructured data models with well-known data struc- KEYWORDS tures like records and arrays. The user willing to effectively JSON, schemas, schema inference, parsing, schema libraries manage JSON data collections can rely on several schema languages, like JSON Schema, JSound, and Joi, as well as on ACM Reference Format: the type abstractions offered by modern programming and Mohamed-Amine Baazizi, Dario Colazzo, Giorgio Ghelli, and Carlo scripting languages like Swift or TypeScript. Sartiani. 2019. Schemas and Types for JSON Data: from Theory The main aim of this tutorial is to provide the audience to Practice. In 2019 International Conference on Management of (both researchers and practitioners) with the basic notions Data (SIGMOD ’19), June 30-July 5, 2019, Amsterdam, Netherlands. for enjoying all the benefits that schema and types can offer ACM, New York, NY, USA, 4 pages. https://doi.org/10.1145/3299869. while processing and manipulating JSON data. This tuto- 3314032 rial focuses on four main aspects of the relation between JSON and schemas: (1) we survey existing schema language proposals and discuss their prominent features; (2) we ana- 1 INTRODUCTION lyze tools that can infer schemas from data, or that exploit The last two decades have seen a dramatic change in the schema information for improving data parsing and manage- data processing landscape. -
Technology Overview
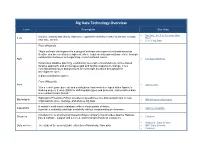
Big Data Technology Overview Term Description See Also Big Data - the 5 Vs Everyone Must Volume, velocity and variety. And some expand the definition further to include veracity 3 Vs Know and value as well. 5 Vs of Big Data From Wikipedia, “Agile software development is a group of software development methods based on iterative and incremental development, where requirements and solutions evolve through collaboration between self-organizing, cross-functional teams. Agile The Agile Manifesto It promotes adaptive planning, evolutionary development and delivery, a time-boxed iterative approach, and encourages rapid and flexible response to change. It is a conceptual framework that promotes foreseen tight iterations throughout the development cycle.” A data serialization system. From Wikepedia, Avro Apache Avro “It is a remote procedure call and serialization framework developed within Apache's Hadoop project. It uses JSON for defining data types and protocols, and serializes data in a compact binary format.” BigInsights Enterprise Edition provides a spreadsheet-like data analysis tool to help Big Insights IBM Infosphere Biginsights organizations store, manage, and analyze big data. A scalable multi-master database with no single points of failure. Cassandra Apache Cassandra It provides scalability and high availability without compromising performance. Cloudera Inc. is an American-based software company that provides Apache Hadoop- Cloudera Cloudera based software, support and services, and training to business customers. Wikipedia - Data Science Data science The study of the generalizable extraction of knowledge from data IBM - Data Scientist Coursera Big Data Technology Overview Term Description See Also Distributed system developed at Google for interactively querying large datasets. Dremel Dremel It empowers business analysts and makes it easy for business users to access the data Google Research rather than having to rely on data engineers. -

Data Analytics Using Mapreduce Framework for DB2's Large Scale XML Data Processing
® IBM Software Group Data Analytics using MapReduce framework for DB2's Large Scale XML Data Processing George Wang Lead Software Egnineer, DB2 for z/OS IBM © 2014 IBM Corporation Information Management Software Disclaimer and Trademarks Information contained in this material has not been submitted to any formal IBM review and is distributed on "as is" basis without any warranty either expressed or implied. Measurements data have been obtained in laboratory environment. Information in this presentation about IBM's future plans reflect current thinking and is subject to change at IBM's business discretion. You should not rely on such information to make business plans. The use of this information is a customer responsibility. IBM MAY HAVE PATENTS OR PENDING PATENT APPLICATIONS COVERING SUBJECT MATTER IN THIS DOCUMENT. THE FURNISHING OF THIS DOCUMENT DOES NOT IMPLY GIVING LICENSE TO THESE PATENTS. TRADEMARKS: THE FOLLOWING TERMS ARE TRADEMARKS OR ® REGISTERED TRADEMARKS OF THE IBM CORPORATION IN THE UNITED STATES AND/OR OTHER COUNTRIES: AIX, AS/400, DATABASE 2, DB2, e- business logo, Enterprise Storage Server, ESCON, FICON, OS/390, OS/400, ES/9000, MVS/ESA, Netfinity, RISC, RISC SYSTEM/6000, System i, System p, System x, System z, IBM, Lotus, NOTES, WebSphere, z/Architecture, z/OS, zSeries The FOLLOWING TERMS ARE TRADEMARKS OR REGISTERED TRADEMARKS OF THE MICROSOFT CORPORATION IN THE UNITED STATES AND/OR OTHER COUNTRIES: MICROSOFT, WINDOWS, WINDOWS NT, ODBC, WINDOWS 95, WINDOWS VISTA, WINDOWS 7 For additional information see ibm.com/legal/copytrade.phtml Information Management Software Agenda Motivation Project Overview Architecture and Requirements Technical design problems Hardware/software constraints, and solutions System Design and Implementation Performance and Benchmark showcase Conclusion, Recommendations and Future Work Information Management Software IBM’s Big Data Portfolio IBM views Big Data at the enterprise level thus we aren’t honing in on one aspect such as analysis of social media or federated data 1.