Electronic Evidence Examiner
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Google Search Bar & Search Term History
DFIR Review Google Search Bar & Search Term History - Are You Finding Everything? Joshua Hickman Published on: May 26, 2020 License: Creative Commons Attribution 4.0 International License (CC-BY 4.0) DFIR Review Google Search Bar & Search Term History - Are You Finding Everything? Synopsis Forensic question: What information can be located regarding searches conducted in the Google search bar? OS Version: Nougat (8.55.6.21) Oreo (8.91.5.21) Tools: WinHex, Version 19.7 (Specialist License) Cellebrite UFED 4PC, Version 7.10.1.1080 (Nougat) Cellebrite UFED 4PC, Version 7.12.1.100 (Oreo) DCode Version 4.02a Google Protocol Buffers, Version 3.7.1 DB Browser for SQLite, Version 3.10.1 Cellebrite Physical Analyzer, Version 7.15.1.1 Cellebrite Physical Analyzer, Version 7.16.0.93 Internet Evidence Finder, Version 6.23.1.15677 2 DFIR Review Google Search Bar & Search Term History - Are You Finding Everything? Introduction Search history. It is an excellent way to peer into someone’s mind and see what they are thinking at a particular moment in time. In a court room, search history can be used to show intent (mens rea). There are plenty of examples where search history has been used in court to establish a defendant’s intent. Probably the most gruesome was the New York City Cannibal Cop trial, where prosecutors used the accused’s search history against him. Of course, there is a fine line between intent and protected speech under the First Amendment. Over the past month and a half I have published a couple of blog posts dealing with Google Assistant and some of the artifacts it leaves behind, which you can find here and here. -

Ransomware and G Suite Business: What You Need to Know
EBOOK Pull text goes here and bold some of the copy Ransomware and G Suite Business: What You Need to Know 1 | backupify.com Pull text goes here Theand boldRansomware some Problem of the copy Small to enterprise sized businesses face an enormous computer security challenge. They have hundreds -- or thousands -- of accounts to manage. In most cases, not every account holder will ! have the training or knowledge to take the proper measures to keep the organization’s data secure. With multiple accounts, there’s a pretty good chance that someone will encounter malware. It just takes an accidental click or two to download and install. Ransomware encrypts your files then demands payment. The ransom notification promises that if you pay, you’ll receive an unlock code to decrypt your files. Of course, you have to pay in a hard-to- trace cryptocurrency. If you don’t pay, some variants delete your files -- a few at first, then more over time. Don’t think a reboot will help: that just spurs the software to delete your data. And even if you pay, you might not get your data back. You have absolutely no reason to trust the thieves behind the ransomware. Once they have your money, why would they bother to give you an unlock code that works? And why would you expect ransomware distributors to create bug-free code? There’s a decent chance they’re effective criminals, but lousy coders. Cloud apps and storage, such as G Suite and Google Drive, offer some protection from ransomware. New files you create online will be safe. -

Lf241, Applications: Gnumail.App, Der Beweis Für
LinuxFocus article number 241 http://linuxfocus.org GNUMail.app, der Beweis für Portabilität by Georges Tarbouriech <georges.t/at/linuxfocus.org> Abstract: About the author: GNUMail.app ist eine Nachbildung der NeXT Mail.app−Anwendung, welche unter GNUstep und MacOS X läuft. Sein Design erlaubt es, den Georges ist ein langjähriger gleichen Quellcode auf sehr unterschiedlichen Plattformen zu benutzen. Unixbenutzer. Als ein Entsprechend ist dieses großartige Stück Software der absolute Beweis für NeXTSTEP Liebhaber ist er Software−Portabilität zwischen GNUstep und MacOS X. von diesen drei freien Projekten, die es sich zum Ziel gesetzt haben, das Look and Feel (und vieles mehr) _________________ _________________ _________________ dieses großartigen Systems anzubieten, sehr begeistert. Es war einmal... Gegen Ende der 80er Jahre erschien ein neues Betriebssystem, genannt NeXTSTEP. Dieses Betriebssystem bot etwas, was wir noch nie zuvor gesehen hatten. Unter vielen anderen "Sachen" stellte es den Benutzern den allerersten grafischen Mail−Client zur Verfügung, Mail.app. Es bot nicht nur eine grafische Oberfläche, sondern war auch in der Lage, jeden Datentyp zu verwalten: Bilder, Klänge, usw. Einige Jahre später entschied NeXT, NeXTSTEP auf andere Plattformen zu portieren: OpenStep wurde geboren. Von da an begannen einige Leute an freien Software−Projekten zu arbeiten, die die gleiche Philosophie boten. Das größte Projekt ist natürlich GNUstep, da es dessen Ziel ist, uns eine freie Implementation von OpenStep zu liefern. Die Leute bei GNUstep machen einen sehr guten Job, wenn man die Menge an Arbeit berücksichtigt, die ein solches Projekt erfordert. Ein anderes großartiges Werk ist Window Maker. Dieser Fenster−Manager ist Teil des GNUstep−Projektes. Wenn Sie beide Webseiten aufsuchen, werden Sie alles über diese großen freien Projekte erfahren. -

How to Write a Successful Curriculum Vitae Rose Filazzola
How to Write a Successful Curriculum Vitae Rose Filazzola 1 Index . Why write a C.V.? . What is a C.V.? . When should a CV be used? . Before you start . What information should a CV include? . What makes a good CV? . How long should a CV be? . Tips on presentation . Fonts . Different Types of CV . Targeting your CV . Emailed CVs and Web CVs . Summary . Websites to consult for Further Help . CV Sample 2 How to Write a Successful Curriculum Vitae Why write a CV? Nowadays, employers tend to receive thousands of applications for a job as soon as it is advertised on the job market. Therefore, it is vital that your letter should stand out from the thousands of CVs and letters that people are going to send. The first impression is always the most important one, therefore, you need a good, well- structured CV in order to attract the employers' attention. Your CV must sell you to a prospective employer and keep in mind that you are competing against other applicants who are also trying to sell themselves. So the challenge in CV writing is to be more appealing and attractive than the rest. This means that your curriculum vitae must be presented professionally, clearly and in a way that indicates you are an ideal candidate for the job, i.e., you possess the right skills, experience, behaviour, attitude, morality that the employer is seeking. The way you present your CV effectively demonstrates your ability to communicate and particularly to explain a professional business proposition. Different countries may have different requirements and styles for CV or resumes. -

Transfer Your Gmail and Drive with Google Takeout for Schools
Transfer your Gmail and Drive with Google Takeout for Schools You can take it with you! Transfer your Gmail and Drive with Google Takeout for Schools Change is a part of life: Maybe you are a high school senior or a college student and you are graduating. Or perhaps you are a student who is moving to a new school. You might be a teacher who is taking a job at a new school district. Or maybe you are an educator who is retiring after many years of service. In each situation, it is very possible you may have a Google account. G Suite may be used at your high school, your college, and any one of your jobs. So what happens to your Google account when you graduate high school, graduate college, move from one job to another, and eventually retire? You will have built up years of emails, documents, slideshows, and much more. Is there an easy way to take all those files and all that data with you? What would be great would be a simple tool to copy all of your files to a different Google account (such as your personal Gmail account). Well, thankfully we have that with Google Takeout for Schools. This is a very simple and free tool that will copy the emails and Drive files from your school account over to either a personal Gmail account or another G Suite for Education account. See below for a video demonstrating all the steps, as well as written direction on the process. Tutorial Video (9 minutes) Directions for Copying Gmail and Drive For the first step you need to have two different Google accounts, the source account that you are copying from and the destination account that you are copying to. -

Cloud Forensics: Google
Hackinbo 2018 Cloud Forensics: Google Extracting Google Account data © ElcomSoft Ltd. www.elcomsoft.com 1 Google Forensics In This Presentation § Cloud and Over-the-Air Acquisition § Synchronized data § Passwords § Two-Factor Authentication 2 Cloud Forensics Cloud Acquisition: Why? • Helps dealing with locked and encrypted devices • Android 6 and up encrypted by default • Google Account may contain more data than the phone itself • Last resort: may succeed where all other methods fail • Google collects information from all signed-in devices 3 Page 3 Cloud Forensics Cloud Acquisition Helps Bypass All of This: • Secure Lock Screen • Locked Bootloader • Factory Reset Protection (FRP) • Full-Disk Encryption (FDE) and File-Based Encryption (FBE) • Device is broken, wiped, or locked 4 Page 4 Google Forensics Google: Why Cloud Forensics? • Tens of thousand device models • Several thousand manufacturers • Extreme platform fragmentation • Not every Android device is a Google device • Acquisition approaches vary Google Account acquisition • Single point of entry • Unified approach • Impressive amount of information 5 Page 5 Google Forensics Android Open Source vs. Google Mobile Services • Not every Android device is a Google device • AOSP does not mean GMS • Google collects data from other sources if user signs in to: • Chrome browser • Google Maps • Gmail • Google Search • Including competing platforms 6 Page 6 Google Forensics Google Collects Data from Multiple Sources • Multiple devices • Mac • Windows • iPhone • iPad + 23 more • …and Android -

Introducción a Linux Equivalencias Windows En Linux Ivalencias
No has iniciado sesión Discusión Contribuciones Crear una cuenta Acceder Página discusión Leer Editar Ver historial Buscar Introducción a Linux Equivalencias Windows en Linux Portada < Introducción a Linux Categorías de libros Equivalencias Windows en GNU/Linux es una lista de equivalencias, reemplazos y software Cam bios recientes Libro aleatorio análogo a Windows en GNU/Linux y viceversa. Ayuda Contenido [ocultar] Donaciones 1 Algunas diferencias entre los programas para Windows y GNU/Linux Comunidad 2 Redes y Conectividad Café 3 Trabajando con archivos Portal de la comunidad 4 Software de escritorio Subproyectos 5 Multimedia Recetario 5.1 Audio y reproductores de CD Wikichicos 5.2 Gráficos 5.3 Video y otros Imprimir/exportar 6 Ofimática/negocios Crear un libro 7 Juegos Descargar como PDF Versión para im primir 8 Programación y Desarrollo 9 Software para Servidores Herramientas 10 Científicos y Prog s Especiales 11 Otros Cambios relacionados 12 Enlaces externos Subir archivo 12.1 Notas Páginas especiales Enlace permanente Información de la Algunas diferencias entre los programas para Windows y y página Enlace corto GNU/Linux [ editar ] Citar esta página La mayoría de los programas de Windows son hechos con el principio de "Todo en uno" (cada Idiomas desarrollador agrega todo a su producto). De la misma forma, a este principio le llaman el Añadir enlaces "Estilo-Windows". Redes y Conectividad [ editar ] Descripción del programa, Windows GNU/Linux tareas ejecutadas Firefox (Iceweasel) Opera [NL] Internet Explorer Konqueror Netscape / -

Pipenightdreams Osgcal-Doc Mumudvb Mpg123-Alsa Tbb
pipenightdreams osgcal-doc mumudvb mpg123-alsa tbb-examples libgammu4-dbg gcc-4.1-doc snort-rules-default davical cutmp3 libevolution5.0-cil aspell-am python-gobject-doc openoffice.org-l10n-mn libc6-xen xserver-xorg trophy-data t38modem pioneers-console libnb-platform10-java libgtkglext1-ruby libboost-wave1.39-dev drgenius bfbtester libchromexvmcpro1 isdnutils-xtools ubuntuone-client openoffice.org2-math openoffice.org-l10n-lt lsb-cxx-ia32 kdeartwork-emoticons-kde4 wmpuzzle trafshow python-plplot lx-gdb link-monitor-applet libscm-dev liblog-agent-logger-perl libccrtp-doc libclass-throwable-perl kde-i18n-csb jack-jconv hamradio-menus coinor-libvol-doc msx-emulator bitbake nabi language-pack-gnome-zh libpaperg popularity-contest xracer-tools xfont-nexus opendrim-lmp-baseserver libvorbisfile-ruby liblinebreak-doc libgfcui-2.0-0c2a-dbg libblacs-mpi-dev dict-freedict-spa-eng blender-ogrexml aspell-da x11-apps openoffice.org-l10n-lv openoffice.org-l10n-nl pnmtopng libodbcinstq1 libhsqldb-java-doc libmono-addins-gui0.2-cil sg3-utils linux-backports-modules-alsa-2.6.31-19-generic yorick-yeti-gsl python-pymssql plasma-widget-cpuload mcpp gpsim-lcd cl-csv libhtml-clean-perl asterisk-dbg apt-dater-dbg libgnome-mag1-dev language-pack-gnome-yo python-crypto svn-autoreleasedeb sugar-terminal-activity mii-diag maria-doc libplexus-component-api-java-doc libhugs-hgl-bundled libchipcard-libgwenhywfar47-plugins libghc6-random-dev freefem3d ezmlm cakephp-scripts aspell-ar ara-byte not+sparc openoffice.org-l10n-nn linux-backports-modules-karmic-generic-pae -

On the Security of Practical Mail User Agents Against Cache Side-Channel Attacks †
applied sciences Article On the Security of Practical Mail User Agents against Cache Side-Channel Attacks † Hodong Kim 1 , Hyundo Yoon 1, Youngjoo Shin 2 and Junbeom Hur 1,* 1 Department of Computer Science and Engineering, Korea University, Seoul 02841, Korea; [email protected] (H.K.); [email protected] (H.Y.) 2 School of Computer and Information Engineering, Kwangwoon University, Seoul 01897, Korea; [email protected] * Correspondence: [email protected] † This paper is an extended version of our paper published in the 2020 International Conference on Information Networking (ICOIN), Barcelona, Spain, 7–10 January 2020. Received: 30 April 2020; Accepted: 26 May 2020; Published: 29 May 2020 Abstract: Mail user agent (MUA) programs provide an integrated interface for email services. Many MUAs support email encryption functionality to ensure the confidentiality of emails. In practice, they encrypt the content of an email using email encryption standards such as OpenPGP or S/MIME, mostly implemented using GnuPG. Despite their widespread deployment, there has been insufficient research on their software structure and the security dependencies among the software components of MUA programs. In order to understand the security implications of the structures and analyze any possible vulnerabilities of MUA programs, we investigated a number of MUAs that support email encryption. As a result, we found severe vulnerabilities in a number of MUAs that allow cache side-channel attacks in virtualized desktop environments. Our analysis reveals that the root cause originates from the lack of verification and control over the third-party cryptographic libraries that they adopt. In order to demonstrate this, we implemented a cache side-channel attack on RSA in GnuPG and then conducted an evaluation of the vulnerability of 13 MUAs that support email encryption in Ubuntu 14.04, 16.04 and 18.04. -
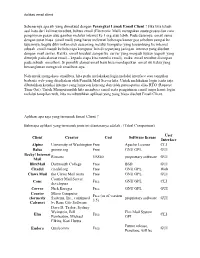
Sebenarnya Apa Sih Yang Dimaksud Dengan Perangkat Lunak Email Client
Aplikasi email client Sebenarnya apa sih yang dimaksud dengan Perangkat Lunak Email Client ? Jika kita telaah asal kata dari kalimat tersebut, bahwa email (Electronic Mail) merupakan suatu proses dan cara pengiriman pesan atau gambar melalui internet ke 1 org atau lebih. Pada dasarnya email sama dengan surat biasa (snail mail) yang harus melewati beberapa kantor pos sebelum sampai ke tujuannya, begitu dikirimkan oleh seseorang melalui komputer yang tersambung ke internet sebuah email masuk ke beberapa komputer lain di sepanjang jaringan internet yang disebut dengan mail server. Ketika email tersebut sampai ke server yang menjadi tujuan (seperti yang ditunjuk pada alamat email – kepada siapa kita menulis email), maka email tersebut disimpan pada sebuah emailbox. Si pemilik alamat email baru bisa mendapatkan email itu kalau yang bersangkutan mengecek emailbox-nya. Nah untuk mengakses emailbox, kita perlu melakukan login melalui interface atau tampilan berbasis web yang disediakan oleh Pemilik Mail Server kita. Untuk melakukan login tentu saja dibutuhkan koneksi internet yang lumayan kencang dan tidak putus-putus alias RTO (Request Time Out). Untuk Mempermudah kita membaca email serta pengiriman email tanpa harus login melalui tampilan web, kita membutuhkan aplikasi yang yang biasa disebut Email Client. Aplikasi apa saja yang termasuk Email Client ? Beberapa aplikasi yang termasuk jenis ini diantaranya adalah : (Tabel Comparison) User Client Creator Cost Software license Interface Alpine University of Washington Free Apache License CLI Balsa gnome.org Free GNU GPL GUI Becky! Internet Rimarts US$40 proprietary software GUI Mail BlitzMail Dartmouth College Free BSD GUI Citadel citadel.org Free GNU GPL Web Claws Mail the Claws Mail team Free GNU GPL GUI Courier Mail Server Cone Free GNU GPL CLI developers Correo Nick Kreeger Free GNU GPL GUI Courier Micro Computer Free (as of version (formerly Systems, Inc., continued proprietary software GUI 3.5) Calypso) by Rose City Software Dave D. -

Google Data Collection —NEW—
Digital Content Next January 2018 / DCN Distributed Content Revenue Benchmark Google Data Collection —NEW— August 2018 digitalcontentnext.org CONFIDENTIAL - DCN Participating Members Only 1 This research was conducted by Professor Douglas C. Schmidt, Professor of Computer Science at Vanderbilt University, and his team. DCN is grateful to support Professor Schmidt in distributing it. We offer it to the public with the permission of Professor Schmidt. Google Data Collection Professor Douglas C. Schmidt, Vanderbilt University August 15, 2018 I. EXECUTIVE SUMMARY 1. Google is the world’s largest digital advertising company.1 It also provides the #1 web browser,2 the #1 mobile platform,3 and the #1 search engine4 worldwide. Google’s video platform, email service, and map application have over 1 billion monthly active users each.5 Google utilizes the tremendous reach of its products to collect detailed information about people’s online and real-world behaviors, which it then uses to target them with paid advertising. Google’s revenues increase significantly as the targeting technology and data are refined. 2. Google collects user data in a variety of ways. The most obvious are “active,” with the user directly and consciously communicating information to Google, as for example by signing in to any of its widely used applications such as YouTube, Gmail, Search etc. Less obvious ways for Google to collect data are “passive” means, whereby an application is instrumented to gather information while it’s running, possibly without the user’s knowledge. Google’s passive data gathering methods arise from platforms (e.g. Android and Chrome), applications (e.g. -

Students: Transfer/Download Your Google School Content
Students: Transfer/Download Your Google School Content Student Google Drive Files cannot be recovered after graduation or after a student leaves the district. School G Suite accounts are closed when students are no longer enrolled. This means that once you graduate or leave the district, you will no longer have access to your files and resources in G Suite unless you take them with you. This process must be completed before graduation or leaving Elwood Community School Corporation. Follow these instructions to transfer your Google Drive files and information: 1. Have or create a personal Google account. a. If needed, click here to create a Google account (instructions) b. Having trouble? Visit the Google Help Center 2. While you are logged into your Elwood Community School Corporation Google account, click here and complete the following steps: a. Select the content you’d like to transfer b. Choose ‘send download link via e-mail’, one-time archive, .zip file, and the 2GB options, then click ‘Create Archive’ c. When the archiving finishes, visit your Elwood school email and retrieve the data from the link sent to you by Google Takeout d. Download the data directly to your device e. Sign out of your Elwood school account, then sign into your personal account, and upload the data to your personal account f. Click here for help Please Note: A personal Google account has 15 gigabytes of storage while school accounts have unlimited storage. If the documents from your school account will exceed this amount, you will need to download the documents separately or create multiple personal accounts.