NASS White Paper on Business Identity Theft 2 Prevention and Protection in State Policy-Making Efforts
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Candidate List Grouped by Contest Alamance Board of Elections Alamance
ALAMANCE BOARD OF ELECTIONS CANDIDATE LIST GROUPED BY CONTEST CRITERIA: Election: 11/03/2020, Show Contest w/o Candidate: Y, County: ALL COUNTIES, Data Source: FULL COUNTY VIEW CANDIDATE NAME NAME ON BALLOT PARTY FILING DATE ADDRESS ALAMANCE US PRESIDENT TRUMP, DONALD J Donald J. Trump REP 08/14/2020 BIDEN, JOSEPH R Joseph R. Biden DEM 08/14/2020 BLANKENSHIP, DON Don Blankenship CST 08/14/2020 HAWKINS, HOWIE Howie Hawkins GRE 08/14/2020 JORGENSEN, JO Jo Jorgensen LIB 08/14/2020 US SENATE TILLIS, THOMAS ROLAND Thom Tillis REP 12/09/2019 P. O. BOX 97396 RALEIGH, NC 27624 BRAY, SHANNON WILSON Shannon W. Bray LIB 12/11/2019 215 MYSTIC PINE PL APEX, NC 27539 CUNNINGHAM, JAMES CALVIN III Cal Cunningham DEM 12/03/2019 PO BOX 309 RALEIGH, NC 27602 HAYES, KEVIN EUGENE Kevin E. Hayes CST 12/19/2019 416 S WEST CENTER ST FAISON, NC 28341 US HOUSE OF REPRESENTATIVES DISTRICT 13 BUDD, THEODORE PAUL Ted Budd REP 12/03/2019 PO BOX 97127 RALEIGH, NC 27624 HUFFMAN, JEFFREY SCOTT Scott Huffman DEM 12/20/2019 4311 SCHOOL HOUSE COMMONS HARRISBURG, NC 28075 NC GOVERNOR PISANO, ALBERT LAWRENCE Al Pisano CST 12/19/2019 7209 E.W.T. HARRIS BLVD. STE. J 119 CHARLOTTE, NC 28227 COOPER, ROY ASBERRY III Roy Cooper DEM 12/05/2019 434 FAYETTEVILLE ST RALEIGH, NC 27601 STE 2020 DIFIORE, STEVEN JOSEPH II Steven J. DiFiore LIB 12/20/2019 6817 FISHERS FARM LN UNIT C1 CHARLOTTE, NC 28277 FOREST, DANIEL JAMES Dan Forest REP 12/04/2019 PO BOX 471845 CHARLOTTE, NC 28247 CONT_CAND_rpt_3.rpt Page 1 of 545 Sep 02, 2020 3:52 pm ALAMANCE BOARD OF ELECTIONS CANDIDATE LIST GROUPED BY CONTEST CANDIDATE NAME NAME ON BALLOT PARTY FILING DATE ADDRESS ALAMANCE NC LIEUTENANT GOVERNOR ROBINSON, MARK KEITH Mark Robinson REP 12/02/2019 P.O. -

How Sports Help to Elect Presidents, Run Campaigns and Promote Wars."
Abstract: Daniel Matamala In this thesis for his Master of Arts in Journalism from Columbia University, Chilean journalist Daniel Matamala explores the relationship between sports and politics, looking at what voters' favorite sports can tell us about their political leanings and how "POWER GAMES: How this can be and is used to great eect in election campaigns. He nds that -unlike soccer in Europe or Latin America which cuts across all social barriers- sports in the sports help to elect United States can be divided into "red" and "blue". During wartime or when a nation is under attack, sports can also be a powerful weapon Presidents, run campaigns for fuelling the patriotism that binds a nation together. And it can change the course of history. and promote wars." In a key part of his thesis, Matamala describes how a small investment in a struggling baseball team helped propel George W. Bush -then also with a struggling career- to the presidency of the United States. Politics and sports are, in other words, closely entwined, and often very powerfully so. Submitted in partial fulllment of the degree of Master of Arts in Journalism Copyright Daniel Matamala, 2012 DANIEL MATAMALA "POWER GAMES: How sports help to elect Presidents, run campaigns and promote wars." Submitted in partial fulfillment of the degree of Master of Arts in Journalism Copyright Daniel Matamala, 2012 Published by Columbia Global Centers | Latin America (Santiago) Santiago de Chile, August 2014 POWER GAMES: HOW SPORTS HELP TO ELECT PRESIDENTS, RUN CAMPAIGNS AND PROMOTE WARS INDEX INTRODUCTION. PLAYING POLITICS 3 CHAPTER 1. -

2010-2019 Election Results-Moffat County 2010 Primary Total Reg
2010-2019 Election Results-Moffat County 2010 Primary Total Reg. Voters 2010 General Total Reg. Voters 2011 Coordinated Contest or Question Party Total Cast Votes Contest or Question Party Total Cast Votes Contest or Question US Senator 2730 US Senator 4681 Ken Buck Republican 1339 Ken Buck Republican 3080 Moffat County School District RE #1 Jane Norton Republican 907 Michael F Bennett Democrat 1104 JB Chapman Andrew Romanoff Democrat 131 Bob Kinsley Green 129 Michael F Bennett Democrat 187 Maclyn "Mac" Stringer Libertarian 79 Moffat County School District RE #3 Maclyn "Mac" Stringer Libertarian 1 Charley Miller Unaffiliated 62 Tony St John John Finger Libertarian 1 J Moromisato Unaffiliated 36 Debbie Belleville Representative to 112th US Congress-3 Jason Napolitano Ind Reform 75 Scott R Tipton Republican 1096 Write-in: Bruce E Lohmiller Green 0 Moffat County School District RE #5 Bob McConnell Republican 1043 Write-in: Michele M Newman Unaffiliated 0 Ken Wergin John Salazar Democrat 268 Write-in: Robert Rank Republican 0 Sherry St. Louis Governor Representative to 112th US Congress-3 Dan Maes Republican 1161 John Salazar Democrat 1228 Proposition 103 (statutory) Scott McInnis Republican 1123 Scott R Tipton Republican 3127 YES John Hickenlooper Democrat 265 Gregory Gilman Libertarian 129 NO Dan"Kilo" Sallis Libertarian 2 Jake Segrest Unaffiliated 100 Jaimes Brown Libertarian 0 Write-in: John W Hargis Sr Unaffiliated 0 Secretary of State Write-in: James Fritz Unaffiliated 0 Scott Gessler Republican 1779 Governor/ Lieutenant Governor Bernie Buescher Democrat 242 John Hickenlooper/Joseph Garcia Democrat 351 State Treasurer Dan Maes/Tambor Williams Republican 1393 J.J. -

The State of the Right to Vote After the 2012 Election
S. HRG. 112–794 THE STATE OF THE RIGHT TO VOTE AFTER THE 2012 ELECTION HEARING BEFORE THE COMMITTEE ON THE JUDICIARY UNITED STATES SENATE ONE HUNDRED TWELFTH CONGRESS SECOND SESSION DECEMBER 19, 2012 Serial No. J–112–96 Printed for the use of the Committee on the Judiciary ( U.S. GOVERNMENT PRINTING OFFICE 81–713 PDF WASHINGTON : 2013 For sale by the Superintendent of Documents, U.S. Government Printing Office Internet: bookstore.gpo.gov Phone: toll free (866) 512–1800; DC area (202) 512–1800 Fax: (202) 512–2104 Mail: Stop IDCC, Washington, DC 20402–0001 COMMITTEE ON THE JUDICIARY PATRICK J. LEAHY, Vermont, Chairman HERB KOHL, Wisconsin CHUCK GRASSLEY, Iowa DIANNE FEINSTEIN, California ORRIN G. HATCH, Utah CHUCK SCHUMER, New York JON KYL, Arizona DICK DURBIN, Illinois JEFF SESSIONS, Alabama SHELDON WHITEHOUSE, Rhode Island LINDSEY GRAHAM, South Carolina AMY KLOBUCHAR, Minnesota JOHN CORNYN, Texas AL FRANKEN, Minnesota MICHAEL S. LEE, Utah CHRISTOPHER A. COONS, Delaware TOM COBURN, Oklahoma RICHARD BLUMENTHAL, Connecticut BRUCE A. COHEN, Chief Counsel and Staff Director KOLAN DAVIS, Republican Chief Counsel and Staff Director (II) C O N T E N T S STATEMENTS OF COMMITTEE MEMBERS Page Coons, Hon. Christopher A., a U.S. Senator from the State of Delaware ........... 6 Durbin, Hon. Dick, a U.S. Senator from the State of Illinois .............................. 4 Grassley, Hon. Chuck, a U.S. Senator from the State of Iowa ............................ 3 Leahy, Hon. Patrick J., a U.S. Senator from the State of Vermont .................... 1 prepared statement .......................................................................................... 178 Whitehouse, Hon. Sheldon, a U.S. Senator from the State of Rhode Island ..... -

1 Immigrant Resentment and Voter Fraud Beliefs in the U.S. Electorate
Immigrant Resentment and Voter Fraud Beliefs in the U.S. Electorate Adriano Udani Assistant Professor Department of Political Science University of Missouri – St. Louis [email protected] David C. Kimball Professor Department of Political Science University of Missouri – St. Louis [email protected] July 2017 Forthcoming, American Politics Research Abstract Public beliefs about the frequency of voter fraud are frequently cited to support restrictive voting laws in the United States. However, some sources of public beliefs about voter fraud have received little attention. We identify two conditions that combine to make anti-immigrant attitudes a strong predictor of voter fraud beliefs. First, the recent growth and dispersion of the immigrant population makes immigration a salient consideration for many Americans. Second, an immigrant threat narrative in political discourse linking immigration to crime and political dysfunction has been extended to the voting domain. Using new data from a survey module in the 2014 Cooperative Congressional Election Study and the 2012 American National Election Study, we show that immigrant resentment is strongly associated with voter fraud beliefs. Widespread hostility toward immigrants helps nourish public beliefs about voter fraud and support for voting restrictions in the United States. The conditions generating this relationship in public opinion likely exist in other nations roiled by immigration politics. The topic of fraudulent electoral practices will likely continue to provoke voters to call to mind groups that are politically constructed as “un-American.” * We acknowledge the support of the University of Missouri Research Board, the College of Arts and Sciences at the University of Missouri-St. Louis and National Science Foundation Award # 1430505. -

Table 4.15 the SECRETARIES of STATE, 2014
SECRETARIES OF STATE Table 4.15 THE SECRETARIES OF STATE, 2014 Maximum Length of Number of consecutive State or other Method of regular term Date of Present term previous terms allowed jurisdiction Name and party selection in years first service ends terms by constitution Alabama .................... Beth Chapman (R) E 4 1/2007 1/2015 1 2 Alaska ........................ .....................................................................................................(a) ................................................................................................ Arizona ...................... Ken Bennett (R) E (b) 4 1/2009 (b) 1/2015 (b) 2 Arkansas .................... Mark Martin (R) E 4 1/2011 1/2015 . 2 California .................. Debra Bowen (D) E 4 1/2007 1/2015 1 2 Colorado .................... Scott Gessler (R) E 4 1/2011 1/2015 . 2 Connecticut ............... Denise Merrill (D) E 4 1/2011 1/2015 . Delaware ................... Jeffrey Bullock (D) A (c) 4 1/2009 . Florida ....................... Kenneth Detzner (R) (e) A 4 2/2012 . (e) 2 Georgia ...................... Brian Kemp (R) E (d) 4 1/2010 (d) 1/2015 (d) . Hawaii........................ .....................................................................................................(a) ................................................................................................ Idaho .......................... Ben Ysursa (R) E 4 1/2003 1/2015 2 . Illinois ........................ Jesse White (D) E 4 1/1999 1/2015 3 . Indiana ....................... Connie -

UOCAVA Election Notice
Official Election Notice County of ALAMANCE 2020 GENERAL Election Date: 11/03/2020 This is an official notice of an election to be conducted in ALAMANCE County on 11/03/2020. This notice contains a list of all of the ballot measures and federal, State, and local offices this county expects, as of this date, to be on the ballot on the date of the election. (See Attachment) An Election Notice will be prepared not later than 100 days before a regularly scheduled election that permits absentee voting, and as soon as practicable in the case of an election or vacancy election not regularly scheduled. For a second primary, an Election Notice will be prepared, no later than the day following the date the appropriate board of elections orders that a second primary be held. As soon as ballot styles are printed, this county board of elections will update this notice with the certified candidates for each office and ballot measures and referenda questions that will be on the ballot. For General Elections during even-numbered years, ballots will be printed 60 days prior to the election. For statewide primaries and other elections (except municipal elections), ballots will be printed 50 days prior to the election. Municipal ballots are available 30 days prior to Election Day. You must request an updated Election Notice. Transmitting a Federal Write-in Absentee Ballot: This notice may be used in conjunction with the federal write-in absentee ballot (FWAB). Covered military & overseas voters seeking to vote by absentee ballot may use the FWAB to register to vote, request an absentee ballot, and vote an official military-overseas ballot. -
![Motion for Preliminary Injunction [PDF]](https://docslib.b-cdn.net/cover/8486/motion-for-preliminary-injunction-pdf-3328486.webp)
Motion for Preliminary Injunction [PDF]
Case 1:21-cv-02070-JPB Document 15 Filed 06/14/21 Page 1 of 6 IN THE UNITED STATES DISTRICT COURT FOR THE NORTHERN DISTRICT OF GEORGIA ATLANTA DIVISION COALITION FOR GOOD GOVERNANCE, et al., Plaintiffs, Civil Action No. 21-cv-02070-JPB v. BRIAN KEMP, et al., Defendants. MOTION FOR PRELIMINARY INJUNCTION, FOR EXPEDITED BRIEFING AND FOR ORAL HEARING Plaintiffs move this Court to enter a preliminary injunction, to grant expedited briefing, and to hold an oral hearing, as follows: PreliMinary Injunction Pursuant to Rule 65 of the Federal Rules of Civil Procedure, Plaintiffs move the Court to preliminarily enjoin Defendants, effectively immediately, from enforcing the following laws: (A) O.C.G.A. § 21-2-568.1 (the “Elector Observation Felony”), which makes it a felony to “intentionally observe an elector while casting a ballot in a manner that would allow such person to see for whom or what the elector is voting”; 1 Case 1:21-cv-02070-JPB Document 15 Filed 06/14/21 Page 2 of 6 (B) O.C.G.A. § 21–2–386(a)(2)(B)(vii) (the “Gag Rule”), which prohibits “monitors” and “observers,” under penalty of criminal misdemeanor, from “[c]ommunicating any information that they see while monitoring the processing and scanning of the absentee ballots” “to anyone other than an election official who needs such information to lawfully carry out his or her official duties”; (C) O.C.G.A. §§ 21-2-386(a)(2)(A) and (B)(vi) (the “Estimating Bans”), which make it a misdemeanor for “monitors and observers” to, among other things, tally, tabulate, estimate or attempt to tally, tabulate, or estimate the number of absentee ballots cast or any votes on the absentee ballots cast; (D) O.C.G.A. -

UOCAVA Election Notice
Official Election Notice County of ORANGE 2020 GENERAL Election Date: 11/03/2020 This is an official notice of an election to be conducted in ORANGE County on 11/03/2020. This notice contains a list of all of the ballot measures and federal, State, and local offices this county expects, as of this date, to be on the ballot on the date of the election. (See Attachment) An Election Notice will be prepared not later than 100 days before a regularly scheduled election that permits absentee voting, and as soon as practicable in the case of an election or vacancy election not regularly scheduled. For a second primary, an Election Notice will be prepared, no later than the day following the date the appropriate board of elections orders that a second primary be held. As soon as ballot styles are printed, this county board of elections will update this notice with the certified candidates for each office and ballot measures and referenda questions that will be on the ballot. For General Elections during even-numbered years, ballots will be printed 60 days prior to the election. For statewide primaries and other elections (except municipal elections), ballots will be printed 50 days prior to the election. Municipal ballots are available 30 days prior to Election Day. You must request an updated Election Notice. Transmitting a Federal Write-in Absentee Ballot: This notice may be used in conjunction with the federal write-in absentee ballot (FWAB). Covered military & overseas voters seeking to vote by absentee ballot may use the FWAB to register to vote, request an absentee ballot, and vote an official military-overseas ballot. -
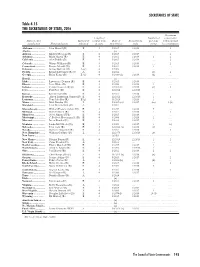
Table 4.15 the SECRETARIES of STATE, 2016
SECRETARIES OF STATE Table 4.15 THE SECRETARIES OF STATE, 2016 Maximum Length of Number of consecutive State or other Method of regular term Date of Present term previous terms allowed jurisdiction Name and party selection in years first service ends terms by constitution Alabama .................... John Merrill (R) E 4 1/2015 1/2019 . 2 Alaska ........................ .....................................................................................................(a) ................................................................................................ Arizona ...................... Michele Reagan (R) E 4 1/2015 1/2019 . 2 Arkansas .................... Mark Martin (R) E 4 1/2011 1/2019 1 2 California .................. Alex Padilla (D) E 4 1/2015 1/2019 . 2 Colorado .................... Wayne Williams (R) E 4 1/2015 1/2019 . 2 Connecticut ............... Denise Merrill (D) E 4 1/2011 1/2019 1 . Delaware ................... Jeffrey Bullock (D) A (c) 4 1/2009 . Florida ....................... Kenneth Detzner (R) (e) A 4 2/2012 . (e) 2 Georgia ...................... Brian Kemp (R) E (d) 4 1/2010 (d) 1/2019 (d) . Hawaii........................ .....................................................................................................(a) ................................................................................................ Idaho .......................... Lawerence Denney (R) E 4 1/2015 1/2019 . Illinois ........................ Jesse White (D) E 4 1/1999 1/2019 4 . Indiana ....................... Connie -

The National Association of Secretaries of State
A=Secretaries Appointed 10 Republicans 24 CEO=Chief Election Official E=Secretaries Elected 38 Democrats 27 Appointed Secretaries serving as CEO 4 LEG=Secretaries Selected by Legislature 3 Elected Secretaries serving as CEO 33 Men 32 Legislatively Selected Secretaries serving as CEO 2 Women 19 THE NATIONAL ASSOCIATION OF SECRETARIES OF STATE ALABAMA (R) (CEO) CONNECTICUT (D) (CEO) ILLINOIS (D) MAINE (D) (CEO) MISSOURI (D) (CEO) Hon. Beth Chapman Hon. Susan Bysiewicz Hon. Jesse White Hon. Matthew Dunlap Hon. Robin Carnahan Secretary of State -E Secretary of State -E Secretary of State -E Secretary of State -LEG Secretary of State -E State Capitol State Capitol, Room 104 213 State Capitol 148 State House Station 600 West Main 600 Dexter Avenue, Hartford, CT 06105 Springfield, IL 62756 Augusta, ME 04333-0148 PO Box 1767 Ste. S-105 (860) 509-6200 (217) 782-2201 (207) 626-8400 Jefferson City, MO 65101 Montgomery, AL 36104 Fax (860) 509-6209 Fax (217) 785-0358 Fax (207) 287-8598 (573)751-4936 (334) 242-7200 [email protected] [email protected] [email protected] Fax (573)552-3082 Fax (334) 242-4993 [email protected] [email protected] DELAWARE (D) INDIANA (R) (CEO) MARYLAND (D) Hon. Harriet Smith Windsor Hon. Todd Rokita Hon. John McDonough MONTANA (R) (CEO) ALASKA (R) (CEO) Secretary of State -A Secretary of State -E Secretary of State -A Hon. Brad Johnson Hon. Sean Parnell Townsend Building 201State House State House Secretary of State -E Lieutenant Governor -E 401 Federal St, Ste 3 Indianapolis, IN 46204 Annapolis, MD 21401 State Capitol, Rm.260 P.O. -

NC Voter Guide
NORTH CAROLINA About This Guide I care because . This Guide features candidates for federal and state- wide offices in NC. The Guide’s two sponsors are Democracy North Carolina and Common Cause NC. They are not affiliated with any candidate or party. this is a historic moment. Not voting Candidates with opponents were sent a question- naire. The Guide provides some of their answers; to would be giving my power read more answers from state and local candidates, away; we must use every go to NCVoterGuide.org and Vote411.org. tool we have to be heard. - Rena McNeil For questions about this Guide, call 919-286-6000. You may download a PDF copy at NCVoter.org. AM I REGISTERED? . women’s health, fair courts and public schools To learn if you are registered, visit demnc.co/lookup; are all on the ballot. I click the “?” if you have trouble. The regular deadline want officials who care! to register is Oct. 9, but you can register during Early - Becky Carver Voting with same-day registration; see box on page 5. WHO IS ON MY BALLOT? To view your own ballot, go to demnc.co/lookup for a link to your registration page; it shows your“ Election . by voting, we make Day polling place” and your “Sample Ballots” - click on leaders respect us and our the blue 3- or 4-digit code under Ballots. issues. Advocacy and voting go side by side. HOW CAN I VOTE & STAY SAFE? - Robert Dawkins By Mail: You can vote from the safety of your home by using mail-in absentee voting.