Master Glossary
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Extension of the Lean 5S Methodology to 6S with an Additional Layer to Ensure Occupational Safety and Health Levels
sustainability Article Extension of the Lean 5S Methodology to 6S with An Additional Layer to Ensure Occupational Safety and Health Levels Mariano Jiménez 1,2 , Luis Romero 2,* , Jon Fernández 2, María del Mar Espinosa 2 and Manuel Domínguez 2 1 Department of Mechanical Engineering, Technical School of Engineering—ICAI, Comillas Pontifical University, 25, 28015 Madrid, Spain 2 Design Engineering Area, Industrial Engineering School, National Distance Education University (UNED), 38, 28015 Madrid, Spain * Correspondence: [email protected] Received: 12 June 2019; Accepted: 11 July 2019; Published: 12 July 2019 Abstract: This paper proposes an expansion of the Lean 5S methodology, which includes the concept of Safety–Security as 6S. Implementation was done by a standardized process tested in a pilot area that is part of the Integrated Industrial Manufacturing System Laboratory at the Higher Technical School of Engineering (ICAI). The additional 6S phase (Safety-Security) thoroughly reviews all areas of an industrial plant by analyzing the risks at each workstation, which let employees be fitted out with protection resources depending on each of their personal characteristics and to guarantee the safety of the workstation by strictly complying with occupational safety and health and machinery use standards, which must hold a CE certificate of compliance. The main objective was to increase the scope of 5S methodology to respond to the occupational safety and health needs for machines required in optimizing production processes. It is important to remember that companies must guarantee that their employees use personal protection equipment (PPE) at their work posts or stations that protect them properly from risks to their health and safety and that cannot be prevented or sufficiently limited by using collective means of protection or by adopting work organization measures. -

Lesson 6: Trigonometric Identities
1. Introduction An identity is an equality relationship between two mathematical expressions. For example, in basic algebra students are expected to master various algbriac factoring identities such as a2 − b2 =(a − b)(a + b)or a3 + b3 =(a + b)(a2 − ab + b2): Identities such as these are used to simplifly algebriac expressions and to solve alge- a3 + b3 briac equations. For example, using the third identity above, the expression a + b simpliflies to a2 − ab + b2: The first identiy verifies that the equation (a2 − b2)=0is true precisely when a = b: The formulas or trigonometric identities introduced in this lesson constitute an integral part of the study and applications of trigonometry. Such identities can be used to simplifly complicated trigonometric expressions. This lesson contains several examples and exercises to demonstrate this type of procedure. Trigonometric identities can also used solve trigonometric equations. Equations of this type are introduced in this lesson and examined in more detail in Lesson 7. For student’s convenience, the identities presented in this lesson are sumarized in Appendix A 2. The Elementary Identities Let (x; y) be the point on the unit circle centered at (0; 0) that determines the angle t rad : Recall that the definitions of the trigonometric functions for this angle are sin t = y tan t = y sec t = 1 x y : cos t = x cot t = x csc t = 1 y x These definitions readily establish the first of the elementary or fundamental identities given in the table below. For obvious reasons these are often referred to as the reciprocal and quotient identities. -

Software Testing
Software Testing PURPOSE OF TESTING CONTENTS I. Software Testing Background II. Software Error Case Studies 1. Disney Lion King 2. Intel Pentium Floating Point Division Bug 3. NASA Mars Polar Lander 4. Patriot Missile Defense System 5. Y2K Bug III. What is Bug? 1. Terms for Software Failure 2. Software Bug: A Formal Definition 3. Why do Bugs occur? and cost of bug. 4. What exactly does a Software Tester do? 5. What makes a good Software Tester? IV. Software Development Process 1. Product Components 2. What Effort Goes into a Software Product? 3. What parts make up a Software Product? 4. Software Project Staff V. Software Development Lifecycle Models 1. Big Bang Model 2. Code and Fix Model 3. Waterfall Model 4. Spiral Model VI. The Realities of Software Testing VII. Software Testing Terms and Definition 1. Precision and Accuracy 2. Verification and Validation 3. Quality Assurance and Quality Control Anuradha Bhatia Software Testing I. Software Testing Background 1. Software is a set of instructions to perform some task. 2. Software is used in many applications of the real world. 3. Some of the examples are Application software, such as word processors, firmware in an embedded system, middleware, which controls and co-ordinates distributed systems, system software such as operating systems, video games, and websites. 4. All of these applications need to run without any error and provide a quality service to the user of the application. 5. The software has to be tested for its accurate and correct working. Software Testing: Testing can be defined in simple words as “Performing Verification and Validation of the Software Product” for its correctness and accuracy of working. -

CHAPTER 8. COMPLEX NUMBERS Why Do We Need Complex Numbers? First of All, a Simple Algebraic Equation Like X2 = −1 May Not Have
CHAPTER 8. COMPLEX NUMBERS Why do we need complex numbers? First of all, a simple algebraic equation like x2 = 1 may not have a real solution. − Introducing complex numbers validates the so called fundamental theorem of algebra: every polynomial with a positive degree has a root. However, the usefulness of complex numbers is much beyond such simple applications. Nowadays, complex numbers and complex functions have been developed into a rich theory called complex analysis and be- come a power tool for answering many extremely difficult questions in mathematics and theoretical physics, and also finds its usefulness in many areas of engineering and com- munication technology. For example, a famous result called the prime number theorem, which was conjectured by Gauss in 1849, and defied efforts of many great mathematicians, was finally proven by Hadamard and de la Vall´ee Poussin in 1896 by using the complex theory developed at that time. A widely quoted statement by Jacques Hadamard says: “The shortest path between two truths in the real domain passes through the complex domain”. The basic idea for complex numbers is to introduce a symbol i, called the imaginary unit, which satisfies i2 = 1. − In doing so, x2 = 1 turns out to have a solution, namely x = i; (actually, there − is another solution, namely x = i). We remark that, sometimes in the mathematical − literature, for convenience or merely following tradition, an incorrect expression with correct understanding is used, such as writing √ 1 for i so that we can reserve the − letter i for other purposes. But we try to avoid incorrect usage as much as possible. -

Magma: a Ground-Truth Fuzzing Benchmark
Magma: A Ground-Truth Fuzzing Benchmark Ahmad Hazimeh Mathias Payer EPFL EPFL ABSTRACT fuzzer is evaluated against a set of target programs. These target pro- High scalability and low running costs have made fuzz testing grams can be sourced from a benchmark suite—such as the Cyber the de-facto standard for discovering software bugs. Fuzzing tech- Grand Challenge [9], LAVA-M[12], the Juliet Test Suite [30], and niques are constantly being improved in a race to build the ultimate Google’s Fuzzer Test Suite [17], oss-fuzz [2], and FuzzBench [16]— bug-finding tool. However, while fuzzing excels at finding bugs, or from a set of real-world programs [34]. Performance metrics— comparing fuzzer performance is challenging due to the lack of including coverage profiles, crash counts, and bug counts—are then metrics and benchmarks. Crash count, the most common perfor- collected during the evaluation. Unfortunately, while such metrics mance metric, is inaccurate due to imperfections in de-duplication can provide insight into a fuzzer’s performance, they are often methods and heuristics. Moreover, the lack of a unified set of targets insufficient to compare different fuzzers. Moreover, the lackofa results in ad hoc evaluations that inhibit fair comparison. unified set of target programs makes for unfounded comparisons. We tackle these problems by developing Magma, a ground-truth Most fuzzer evaluations consider crash count a reasonable metric fuzzer evaluation framework enabling uniform evaluations and for assessing fuzzer performance. However, crash count is often comparison. By introducing real bugs into real software, Magma inflated [25], even after attempts at de-duplication (e.g., via coverage allows for a realistic evaluation of fuzzers against a broad set of profiles or stack hashes), highlighting the need for more accurate targets. -

White Paper the PDCA Cycle and Management System Standards
The PDCA cycle and Management System Standards ISO uses a very simple but powerful tool for quality system standards. This tool is the Plan- Do-Check-Act (PDCA) cycle shown in the figure below. It is also known as the Deming cycle after J.W. Deming, who proposed the concept in the 50s. The entire logic, structure, and sequence of standards like ISO 9001 and ISO 13485 are based on this cycle. Every process or activity needs to pass through these four phases. Plan Phase Perhaps, planning tasks are the most important ones in a management system. ISO recognizes this fact, as well as the fact that the plan phase should be the very first thing we do. To better understand this phase, activities like “establish” and “determine” should be associated to planning. Other words we can use instead are “identify” or “define”. Let´s see what an organization needs to plan. ACT PLAN First, the organization needs to establish its high- level planning. This will set direction and provide a framework for the entire system. We are talking about the organization´s purpose. And also, in CHECK DO terms of quality, about: policy, system´s scope, and objectives. The output of the high-level planning process will provide the necessary guide to the next step. The PDCA Cycle Next the organization needs to identify the processes that will be part of the quality system. It also needs to define how to apply or operate these processes, their sequence and how they interact. Also, the organization must identify risks related to the processes and how to control them according to those risks. -

The Concept and Implementation of Kaizen in an Organization
Global Journal of Management and Business Research: A Administration and Management Volume 19 Issue 1 Version 1.0 Year 201 Type: Double Blind Peer Reviewed International Research Journal Publisher: Global Journals Online ISSN: 2249-4588 & Print ISSN: 0975-5853 The Concept and Implementation of Kaizen in an Organization By Lubna Rahman Lina & Hafiz Ullah University of Dhaka Abstract- For continuous improvement in an organization, Japanese philosophy Kaizen is very popular. Flawless concepts of kaizen methodology and proper implementation of tools can lead to a successful kaizen program in a company. From the reviews of various case studies, it has revealed that most of the companies have implemented kaizen efficiently and observe better performance. Besides, some companies also failed to implement kaizen due to the lacking of proper knowledge about the concepts of kaizen. Keywords: kaizen, 5 why technique, 5s, 7 QC tools, 7 wastes, jidoka, PDCA cycle, poka-yoke. GJMBR-A Classification: JEL Code: M00 TheConceptandImplementationofKaizeninanOrganization Strictly as per the compliance and regulations of: © 2019. Lubna Rahman Lina & Hafiz Ullah. This is a research/review paper, distributed under the terms of the Creative Commons Attribution-Noncommercial 3.0 Unported License http://creativecommons.org/licenses/by-nc/3.0/), permitting all non-commercial use, distribution, and reproduction in any medium, provided the original work is properly cited. The Concept and Implementation of Kaizen in an Organization α σ Lubna Rahman Lina & Hafiz Ullah Abstract - For continuous improvement in an organization, over the longer term, without having to go through any Japanese philosophy Kaizen is very popular. Flawless radical innovation. It can be a much gentler and concepts of kaizen methodology and proper implementation employee-friendly way to institute the changes that must of tools can lead to a successful kaizen program in a occur as a business grows and adapts to its changing company. -

Agile and Devops Overview for Business
NELKINDA SOFTWARE CRAFT Ƅ TRAINING Agile and DevOps Overview for Business Duration: 2 Days Available Languages: English Audience Everyone who is steering or involved in software delivery: Business, Management, Operations, Development, for example: CxOs, managers, directors, team leads, systems administrators, development managers, business analysts, requirements engineers, architects, product owners, scrum masters, IT operations sta', IT stakeholders, developers, testers Goals Agile and DevOps are the big drivers of organizational transformation today. What do they mean? Where do they come from? What are their goals? How can they help my organization and my team? How can I use and implement them? And are there any side-e'ects or challenges to consider? Learn the answers to these questions in a holistic perspective from the CxO level to the code about what Agile and DevOps mean for organizations of all sizes. Contents • Business Case for Improving the Software Development Life Cycle ◦ Evolution of the Software Development Life Cycle (SDLC) ◦ Business Drivers of the SDLC Evolution ◦ Principles of Agile, DevOps, Extreme Programming (XP), and Software Craft ◦ Goals and Objectives of Agile, DevOps (Development Operations), XP, and Software Craft ◦ The Pipeline for Value Delivery • Essential Principles ◦ Manifesto for Agile Software Development ("Agile Manifesto") ◦ The Values and Principles of XP ◦ Manifesto of Software Craft ◦ The Two Values of Software ◦ The Deming (PDCA, plan-do-check-act) Cycle ◦ The XP Feedback Loops ◦ Parkinson's Law and Timeboxing ◦ Conway's Law, Organizational Structure and Cross-functional responsibility ◦ KPIs (Key Performance Indicators) and Drivers: Story-Point Velocity, Cycle Time, WIP (Work In Progress) limit ◦ Heisenberg's Uncertainty Principle of Agile Estimation 1/3 https://nelkinda.com/training/DevOps-Driven-Agile © Copyright 2015-2020 Nelkinda Software Craft Private Limited. -
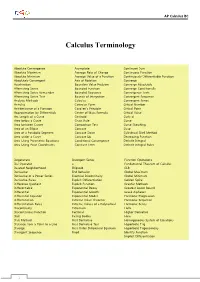
Calculus Terminology
AP Calculus BC Calculus Terminology Absolute Convergence Asymptote Continued Sum Absolute Maximum Average Rate of Change Continuous Function Absolute Minimum Average Value of a Function Continuously Differentiable Function Absolutely Convergent Axis of Rotation Converge Acceleration Boundary Value Problem Converge Absolutely Alternating Series Bounded Function Converge Conditionally Alternating Series Remainder Bounded Sequence Convergence Tests Alternating Series Test Bounds of Integration Convergent Sequence Analytic Methods Calculus Convergent Series Annulus Cartesian Form Critical Number Antiderivative of a Function Cavalieri’s Principle Critical Point Approximation by Differentials Center of Mass Formula Critical Value Arc Length of a Curve Centroid Curly d Area below a Curve Chain Rule Curve Area between Curves Comparison Test Curve Sketching Area of an Ellipse Concave Cusp Area of a Parabolic Segment Concave Down Cylindrical Shell Method Area under a Curve Concave Up Decreasing Function Area Using Parametric Equations Conditional Convergence Definite Integral Area Using Polar Coordinates Constant Term Definite Integral Rules Degenerate Divergent Series Function Operations Del Operator e Fundamental Theorem of Calculus Deleted Neighborhood Ellipsoid GLB Derivative End Behavior Global Maximum Derivative of a Power Series Essential Discontinuity Global Minimum Derivative Rules Explicit Differentiation Golden Spiral Difference Quotient Explicit Function Graphic Methods Differentiable Exponential Decay Greatest Lower Bound Differential -

Managing Defects in an Agile Environment
Managing Defects in an Agile environment Auteur Ron Eringa Managing Defects in an Agile environment Introduction Injecting passion, Agility Teams often struggle with answering the following and quality into your question: “How to manage our Defects in an organisation. Agile environment?”. They start using Scrum as a framework for developing their software and while implementing, they experience trouble on how to deal with the Defects they find/cause along the way. Scrum is a framework that does not explicitly tell you how to handle Defects. The strait forward answer is to treat your Defects as Product Backlog Items that should be added to the Product Backlog. When the priority is set high enough by the Product Owner, they will be picked up by the Development Team in the next Sprint. The application of this is a little bit more difficult and hence should be explained in more detail. RON ERINGA 1. What is a defect? AGILE COACH Wikipedia: “A software bug (or defect) is an error, flaw, After being graduated from the Fontys failure, or fault in a computer program or system that University in Eindhoven, I worked as a Software produces an incorrect or unexpected result, or causes Engineer/Designer for ten years. Although I it to behave in unintended ways. Most bugs arise have always enjoyed technics, helping people from mistakes and errors made by people in either a and organizations are my passion. Especially program’s source code or its design, or in frameworks to deliver better quality together. When people and operating systems used by such programs, and focus towards a common goal, interaction is a few are caused by compilers producing incorrect increasing and energy is released. -

CMMN Modeling of the Risk Management Process Extended Abstract
CMMN modeling of the risk management process Extended abstract Tiago Barros Ferreira Instituto Superior Técnico [email protected] ABSTRACT Enterprise Risk Management (ERM) is thus a very important activity to support the Risk management is a development activity and achievement of the organizations' goals. increasingly plays a crucial role in Risk management is defined as “coordinated organization´s management. Being very activities to direct and control an organization valuable for organizations, they develop and with regard to risk” [1]. ERM, as a risk implement enterprise risk management management activity, comprises the strategies that improve their business model identification of the potential events in the whole and bring them better results. Enterprise risk organization that can affect the objectives, the management strategies are based on the respective risk appetite, and thus, with implementation of a risk management process reasonable assurance, the fulfillment of the and supporting structure. Together, this process organization's goals [2]. and structure form a framework. ISO 31000 Many organizations nowadays have their standard is currently the main global reference risk management framework, including framework for risk management, proposing the activities to identify their risks, and their general principles and guidelines for risk prevention measures, documented. To this end, management, regardless of context. The most [1] is at this moment the main reference for risk recent revision of the standard ISO 31000:2018 management frameworks, proposing the [1] depicts the process of risk management as general principles and guidelines for risk a case rather than a sequential process. To that management, regardless of their context. -

Section 5.4 the Other Trigonometric Functions 333
Section 5.4 The Other Trigonometric Functions 333 Section 5.4 The Other Trigonometric Functions In the previous section, we defined the sine and cosine functions as ratios of the sides of a right triangle in a circle. Since the triangle has 3 sides there are 6 possible combinations of ratios. While the sine and cosine are the two prominent ratios that can be formed, there are four others, and together they define the 6 trigonometric functions. Tangent, Secant, Cosecant, and Cotangent Functions For the point (x, y) on a circle of radius r at an angle of θ , we can define four additional important functions as the ratios of the (x, y) sides of the corresponding triangle: y r The tangent function: tan(θ ) = y x θ r The secant function: sec(θ ) = x x r The cosecant function: csc(θ ) = y x The cotangent function: cot(θ ) = y Geometrically, notice that the definition of tangent corresponds with the slope of the line segment between the origin (0, 0) and the point (x, y). This relationship can be very helpful in thinking about tangent values. You may also notice that the ratios defining the secant, cosecant, and cotangent are the reciprocals of the ratios defining the cosine, sine, and tangent functions, respectively. Additionally, notice that using our results from the last section, y r sin(θ ) sin(θ ) tan(θ ) = = = x r cos(θ ) cos(θ ) Applying this concept to the other trig functions we can state the other reciprocal identities. Identities The other four trigonometric functions can be related back to the sine and cosine functions using these basic relationships: sin(θ ) 1 1 1 cos(θ ) tan(θ ) = sec(θ ) = csc(θ ) = cot(θ ) = = cos(θ ) cos(θ ) sin(θ ) tan(θθ ) sin( ) 334 Chapter 5 These relationships are called identities.