Secure Message Communication Using Digital Signatures and Attribute Based Cryptographic Method in VANET
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-
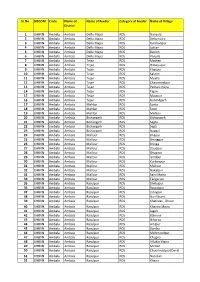
Sr.No. DISCOM Circle Name of District Name of Feeder Category Of
Sr.No. DISCOM Circle Name of Name of Feeder Category of Feeder Name of Village District 1 UHBVN Ambala Ambala Dellu Majra RDS Nanyola 2 UHBVN Ambala Ambala Dellu Majra RDS Dellumajra 3 UHBVN Ambala Ambala Dellu Majra RDS Kurchanpur 4 UHBVN Ambala Ambala Dellu Majra RDS Lottan 5 UHBVN Ambala Ambala Dellu Majra RDS Batron 6 UHBVN Ambala Ambala Dellu Majra RDS Panjola 7 UHBVN Ambala Ambala Tejan RDS Matheri 8 UHBVN Ambala Ambala Tejan RDS Himayupur 9 UHBVN Ambala Ambala Tejan RDS Khaspur 10 UHBVN Ambala Ambala Tejan RDS Sakron 11 UHBVN Ambala Ambala Tejan RDS Mujfra 12 UHBVN Ambala Ambala Tejan RDS Chaurmastpur 13 UHBVN Ambala Ambala Tejan RDS Pathan majra 14 UHBVN Ambala Ambala Tejan RDS Tejan 15 UHBVN Ambala Ambala Tejan RDS Mastpur 16 UHBVN Ambala Ambala Tejan RDS Gobindgarh 17 UHBVN Ambala Ambala Mehlan RDS Sonta 18 UHBVN Ambala Ambala Mehlan RDS Sonti 19 UHBVN Ambala Ambala Mehlan RDS Mehlan 20 UHBVN Ambala Ambala Bishangarh RDS Bishangarh 21 UHBVN Ambala Ambala Bishangarh RDS Segta 22 UHBVN Ambala Ambala Bishangarh RDS Segti 23 UHBVN Ambala Ambala Bishangarh RDS Naggal 24 UHBVN Ambala Ambala Mallour RDS Bhapur 25 UHBVN Ambala Ambala Mallour RDS Brungpur 26 UHBVN Ambala Ambala Mallour RDS Bringa 27 UHBVN Ambala Ambala Mallour RDS Daudpur 28 UHBVN Ambala Ambala Mallour RDS Ghagroo 29 UHBVN Ambala Ambala Mallour RDS Ismilpur 30 UHBVN Ambala Ambala Mallour RDS Kurbanpur 31 UHBVN Ambala Ambala Mallour RDS Mallour 32 UHBVN Ambala Ambala Mallour RDS Nakatpur 33 UHBVN Ambala Ambala Mallour RDS Saini Majra 34 UHBVN Ambala Ambala Mallour RDS -

For the Session 2016-17
Annual Quality Assurance Report (AQAR) For the Session 2016-17 Internal Quality Assurance Cell Internal Quality Assurance Cell Maharishi Markandeshwar University, Mullana- Ambala (Deemed University established under Section 3 of the UGC Act, 1956) (NAAC Accredited Grade ‘A’ University) The Annual Quality Assurance Report (AQAR) of the IQAC July 1, 2016 to June 30, 2017 Part – A AQAR for the year 2016 -17 1. Details of the Institution 1.1 Name of the Institution Maharishi Markandeshwar University 1.2 Address Line 1 Ambala-Yamunanagar Highway Mullana - Ambala Address Line 2 Ambala City/Town Haryana State Pin Code 133 207 [email protected] Institution e-mail address Contact Nos. 01731-304441 Prof. Victor Gambhir Name of the Head of the Institution: Tel. No. with STD Code: 01731-304524 80599 30111 Mobile: Name of the IQAC Co-ordinator: Dr. Sumit Mittal Mobile: 80599 30412 [email protected] IQAC e-mail address: 1.3 NAAC Track ID (For ex. MHCOGN 18879) HRUNGN11435 OR 1.4 NAAC Executive Committee No. & Date: EC/71/A&A/4.1 (For Example EC/32/A&A/143 dated 3-5-2004. This EC no. is available in the right corner-bottom of your institution’s Accreditation Certificate) www.mmumullana.org 1.5 Website address: Web-link of the AQAR: http://www.mmumullana.org/IQAC/AQAR2016 -17.pdf For ex. http://www.ladykeanecollege.edu.in/AQAR2012-13.doc 1.6 Accreditation Details Year of Sl. No. Cycle Grade CGPA Accreditatio Validity Period n 1 1st Cycle A 3.06 2015 Nov. 15, 2020 2 2nd Cycle 3 3rd Cycle 4 4th Cycle 12th June, 2007 1.7 Date of Establishment of IQAC: DD/MM/YYYY 1.8 Details of the previous year’s AQAR submitted to NAAC after the latest Assessment and Accreditation by NAAC ((for example AQAR 2010-11submitted to NAAC on 12-10-2011) i. -

Maharishi Markandeshwar University Mullana-Ambala
MAHARISHI MARKANDESHWAR UNIVERSITY MULLANA-AMBALA (PAPER PUBLICATIONS IN JOURNAL) Period: January 2007 to December 2010 Staff ID 120181 Publication ID JL00441 Title (Article) Author(s) Title (Journal) Place/ Year of Vol./ Issue Indexed With Impact Publication Factor Effect of maternal factors Dr. Anshu Mittal Indian Journal of Community Medicine PGIMR Vol. 32, Scopus Others on nutritional status of 1-5 Dr. Jagjeet Singh Chandigarh Issue. 4, Genemia year children Dr. S.K. Ahluwalia 2007 Web of Sc. Health reference centre Academics Google Scholar Index Copernicus Pub Med. Promocentral proquest etc. Other (If any) Staff ID 120181 Publication ID JL00442 Title (Article) Author(s) Title (Journal) Place/ Year of Vol./ Issue Indexed With Impact Publication Factor Reasons for Unmet Needs Dr. Anand Bhupinder Indian Journal of Maternal & Child Ludhiana Vol. 12 Scopus Indexed in of Family Planning Dr. Singh Jagjeet Health 2010 Issue. (1) Popline Among Married Women. Dr. Mohi M.K. Web of Sc. ISSN-0970- 8928 Google Scholar Pub Med. Other (If any) MAHARISHI MARKANDESHWAR UNIVERSITY MULLANA-AMBALA (PAPER PUBLICATIONS IN JOURNAL) Period: January 2011 to December 2011 Staff ID 120185 Publication ID JL00447 Title (Article) Author(s) Title (Journal) Place/ Year of Vol./ Issue Indexed With Impact Publication Factor Women & AIDS: Dr. Anu Bhardwaj Indian Journal of Maternal 2011 Vol.13 Scopus Awareness & Attitudes in Dr. Bhuvnesh Gupta & Child Health Issue. (2) Web of Sc. peri urban settling in Dr. S.K. Ahluwalia Google Scholar Punjab Dr. Rambha Pathak Dr. Anshu Mittal Pub Med. Dr. Mukhmohit Singh Other (If any) Popline and Indian Science Abstract Staff ID 120185 Publication ID JL00448 Title (Article) Author(s) Title (Journal) Place/ Year of Vol./ Issue Indexed With Impact Publication Factor An epidemiological study Dr. -

List of Dedicated Covid Care Centers in Haryana4
List of Dedicated Covid Care Centers in Haryana Total Isolation Isolation Isolation Sr. District beds of beds for Facilty Name Category Type Facilty ID beds No Name Confirmed Suspected (excluding Cases cases ICU beds) G.S School Main Branch,Ambala Cat. III - Dedicated COVID Other than 1 AMBALA 19624 50 0 50 Cantt Center / DCCC Hospital Cat. III - Dedicated COVID Other than 2 AMBALA Barara 18521 100 100 0 Center / DCCC Hospital Cat. III - Dedicated COVID Other than 3 AMBALA ITI,Bharanpur,Naraingarh 19604 164 0 164 Center / DCCC Hospital Hindu Maha Sabha Hall,Ambala Cat. III - Dedicated COVID Other than 4 AMBALA 19672 10 0 10 City Center / DCCC Hospital Aggarwal Dharamshala,Ambala Cat. III - Dedicated COVID Other than 5 AMBALA 19651 16 0 16 Cantt Center / DCCC Hospital Cat. III - Dedicated COVID Other than 6 AMBALA Bajrang Bhawan 19582 60 0 60 Center / DCCC Hospital Cat. III - Dedicated COVID Other than 7 AMBALA G.S.S College,Ambala Cantt 19622 100 0 100 Center / DCCC Hospital Cat. III - Dedicated COVID Other than 8 AMBALA Panchayat Bhawan,Barara 19700 40 0 40 Center / DCCC Hospital Cat. III - Dedicated COVID Other than 9 AMBALA Welcome Resorts 19603 40 0 40 Center / DCCC Hospital Gauri Shanker Cat. III - Dedicated COVID Other than 10 AMBALA Dharamshala,Near Railway 19671 8 0 8 Center / DCCC Hospital Station,Ambala City Cat. III - Dedicated COVID Other than 11 AMBALA Akal Academy Holi 18517 20 20 0 Center / DCCC Hospital List of Dedicated Covid Care Centers in Haryana Total Isolation Isolation Isolation Sr. District beds of beds for Facilty Name Category Type Facilty ID beds No Name Confirmed Suspected (excluding Cases cases ICU beds) Cat. -

Physio-Chemical & EDXRF Analysis of Groundwater of Ambala, Haryana
Researcher 2010 Physio-Chemical & EDXRF Analysis of Groundwater of Ambala, Haryana, India Prem Singh1,*, J.P. Saharan2, Kavita Sharma3 and Sunita Saharan4 1Dept. of Physics, S.D. College (Lahore) Ambala Cantt.,, Haryana, India 2Dept. of Chemistry, S.D. College (Lahore) Ambala Cantt., Haryana, India 3Dept. of Chemistry, ICL College of Engg. And Technology, Shazadpur, Ambala, Haryana, India 4Dept. of Environmental Studies, HCTM, Kaithal, Haryana, India *[email protected] Abstract: Characterization of the physiochemical parameters of groundwater from fifteen different locations in Ambala, Haryana (India) was carried out. To assess the quality of ground water each parameter was compared with the standard desirable limits prescribed by World health organization (WHO), Bureau of Indian Standard (BIS) and Indian council of medical research (ICMR). Systematic calculation was made to determine the correlation coefficient ‘r’ amongst the parameters. Significant value of the observed correlation coefficients between the parameters was also worked out. Elemental analysis of three samples was carried out using the EDXRF technique. It is concluded that the water quality of water supply systems in different locations of Ambala is of medium quality and can be used for domestic use after suitable treatment. Suitable suggestions were made to improve the quality of water. [Researcher. 2010;2(1):68-75] (ISSN:1553-9865) Keywords: Ambala, ground water, water quality parameter, physiochemical parameter, pollution and EDXRF. 1. Introduction the domestic waste water seep down into the ground Water is the precious gift of nature to the human water sources. In Ambala, the water for drinking being. It is essential for the growth and maintenance of purpose was sourced from ground water without our bodies, as it is involved in a number of biological biochemical treatment. -

Annexure-V State/Circle Wise List of Post Offices Modernised/Upgraded
State/Circle wise list of Post Offices modernised/upgraded for Automatic Teller Machine (ATM) Annexure-V Sl No. State/UT Circle Office Regional Office Divisional Office Name of Operational Post Office ATMs Pin 1 Andhra Pradesh ANDHRA PRADESH VIJAYAWADA PRAKASAM Addanki SO 523201 2 Andhra Pradesh ANDHRA PRADESH KURNOOL KURNOOL Adoni H.O 518301 3 Andhra Pradesh ANDHRA PRADESH VISAKHAPATNAM AMALAPURAM Amalapuram H.O 533201 4 Andhra Pradesh ANDHRA PRADESH KURNOOL ANANTAPUR Anantapur H.O 515001 5 Andhra Pradesh ANDHRA PRADESH Vijayawada Machilipatnam Avanigadda H.O 521121 6 Andhra Pradesh ANDHRA PRADESH VIJAYAWADA TENALI Bapatla H.O 522101 7 Andhra Pradesh ANDHRA PRADESH Vijayawada Bhimavaram Bhimavaram H.O 534201 8 Andhra Pradesh ANDHRA PRADESH VIJAYAWADA VIJAYAWADA Buckinghampet H.O 520002 9 Andhra Pradesh ANDHRA PRADESH KURNOOL TIRUPATI Chandragiri H.O 517101 10 Andhra Pradesh ANDHRA PRADESH Vijayawada Prakasam Chirala H.O 523155 11 Andhra Pradesh ANDHRA PRADESH KURNOOL CHITTOOR Chittoor H.O 517001 12 Andhra Pradesh ANDHRA PRADESH KURNOOL CUDDAPAH Cuddapah H.O 516001 13 Andhra Pradesh ANDHRA PRADESH VISAKHAPATNAM VISAKHAPATNAM Dabagardens S.O 530020 14 Andhra Pradesh ANDHRA PRADESH KURNOOL HINDUPUR Dharmavaram H.O 515671 15 Andhra Pradesh ANDHRA PRADESH VIJAYAWADA ELURU Eluru H.O 534001 16 Andhra Pradesh ANDHRA PRADESH Vijayawada Gudivada Gudivada H.O 521301 17 Andhra Pradesh ANDHRA PRADESH Vijayawada Gudur Gudur H.O 524101 18 Andhra Pradesh ANDHRA PRADESH KURNOOL ANANTAPUR Guntakal H.O 515801 19 Andhra Pradesh ANDHRA PRADESH VIJAYAWADA -

List of Gazette Notified Mosques in the State Of
Khata Property No./War Khewat/Ro Sr.No. Waqf ID Waqf Estate Class Type Area Location dNo adNo Plot No. Amsom/Lane Boundaries Specification Mosque Situated Sahla (1), 27/2/2,14 in barara distt. 8863.25 Barara, /1,14/2,14 Situated in Vill. Sayla, Distt. 0‐7‐0‐4 K.M.S.Sq.ft, Mosque in Abadi and with 1‐ 1 HRAM0001 Ambala Sunni Mosque Sq. Yard Ambala ‐ /3,15/1 ‐‐ Ambala Room,1‐Courtyard,1‐Well, Agri‐land,Total 14K 13M Mosque Situated Tharwa (2), 7/7,14,17, in Tharwa, Distt. 16577. Sq. Barara, 24/1,37/1 Situated in Tharwa, Distt. 0‐5‐4‐18 K.M.S.Sq.ft, Mosque in Abadi with 1‐Room,1‐ 3 HRAM0002 Ambala Sunni Mosque Yard Ambala ‐ 6 ‐‐ Ambala Courtyard,Agri‐land.Total 27K 08M Mosque House Lakh Data Alies Sahki Sarwara 141,6/21/ Sultani Situated Tharwa (2), 1,7/25,9/5 Mosque House Lakh Data Alies in Tharwa Distt. 12281.5 Barara, /2,10/1,10 Sahki Sarwara Sultani, Situated 0K 07M,0K 11M,6K 16M,5|K 10M,2K 11M,4K 11M 7 HRAM0003 Ambala Sunni Mosque Sq. Yard Ambala ‐ /2 ‐‐ in Tharwa total 20K 06M Mosque Situated Salakhani (4), 11/19/2,2 0‐6‐7‐22 K.M.S.Sq.Ft, Mosque in Abadi with 1‐Room,1‐ at Vill. Sulkhni, 8318.75 Barara, 2/2,12/3,2 Situated at Vill. Sulkhni, Distt. Courtyard.Agri‐land,3K 00M,3K 10M,0K 13M,6K 8 HRAM0004 Distt. Ambala Sunni Mosque Sq. Yard Ambala ‐ 3,27 ‐‐ Ambala 05M,0K 07M,total 13K 15M Mosque Situated Sherpur (5), total nos. -

0F4b65a238ca6dec417c
CURRICULUM VITAE SUBASH CHAUDHARY (MSc. Medical Microbiology) ADDRESS : Tulsipur Sub- Metropolitan City, Dang Province No: 6, Nepal. CORRESPONDING ADDRESS : Mullana, Ambala, Haryana Pin: 133207 PHONE NO : 8218420278, 7895437486 EMAIL ID : [email protected] CAREER OBJECTIVE To secure a responsible and remarkable position in the area of my profession utilizing hard work determination and qualification. ACADEMIC QUALIFICATION M.Sc Medical Microbiology (Master’s of Science in Medical Microbiology) from Maharishi Markandeshwar (Deemed To be) University, Mullana, Haryana B.Sc MM( Medical Microbiology) from HNB Garhwal Central University (HNBGU) Srinagar, Uttarakhand in 2016 12th from H.S.E.B Board, Nepal in 2013 10th from SLC Board, Nepal in 2011 WORKING EXPERIENCE: Done internship from Synergy Institute of Medical Sciences, Dehradun in 2016- 2017. Provided teaching assistance on B.Sc courses (OTT, MLT) ,DMLT & practical of MBBS, BDS during M.Sc at Maharishi Markandeshwar deemed to be university, Mullana, Ambala PROFESSIONAL QUALIFICATION DISSERTATION NAME OF INSTITUTE Prevalence of Methicillin resistant Maharishi Markandeshwar (Deemed To be) Staphylococcus aureus and its University, Mullana, Haryana antibiotic susceptibility patterns in pus samples CONFERENCES AND SYMPOSIUM: Participated in National Seminar on Current challenges of Biodiversity at Uttaranchal (P.G) College technology and Biomedical Sciences and Research, Dehradun in 28th, 2014. Participated in Chandigarh Chapter & Scientific Seminar on World Biomedical Laboratory -

MMUCET Syllabus.Pdf
INDEXINDEX Sr. PARTICULARS PAGE No. No 1. Distribution of Seats 2 2. Important Dates for MMUCET-2012 3 3. MM University : A Profile 4 4. About the Participating Institutions 6 5. Duration of the Courses (MBBS/BDS) 8 6. Eligibility Conditions 8 7. Scheme of Entrance Test 9 8. Syllabus for Entrance Test 12 9. Method of Selection and Admission 14 10. Fee Structure 17 11. Important Instructions 18 12. Regulations on Curbing the Menace of Ragging 20 13. Phone Nos. of Important Functionaries 22 14. Appendices a) Application Form b) Admit Cards c) Formats of Affidavits against Ragging MMUCET-2012 DISTRIBUTION OF SEATS Sr. Name of the Institution Name of the Sanctioned General Seats No. Course Intake Open 3% Locomotive Disability 1. MM Institute of Medical MBBS 150 95 3 Sciences & Research, Mullana-Ambala 2. MM College of Dental BDS 100 63 2 Sciences & Research, Mullana-Ambala l65% General Seats of the total sanctioned intake will be filled up through Entrance Test. l3% seats of the total sanctioned intake will be filled up by candidates with Locomotive Disability of lower limbs between 50% to 70%. However, in case any seat in this 3% quota remains unfilled on account of non- availability of candidates with Locomotive Disability of lower limbs between 50% to 70% then any such unfilled seat in this 3% quota shall be filled up by persons with Locomotive Disability of lower limbs between 40% to 50% - before they are included in the annual sanctioned seats for General Category candidates. For claiming seat under this category, a Certificate to this effect from the Civil Surgeon/Chief Medical Officer of the respective district will have to be submitted alongwith the duly filled in application for admission to the couse. -
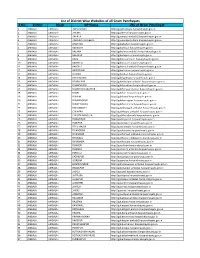
List of District Wise Websites of All Gram Panchayats S.No
List of District Wise Websites of all Gram Panchayats S.No. District Block GP Name URL of Gram Panchayat 1 AMBALA AMBALA-I ADHO MAJRA http://gpadhomajra.harpanchayats.gov.in 2 AMBALA AMBALA-I AHEMA http://gpahema.harpanchayats.gov.in 3 AMBALA AMBALA-I AMIPUR http://gpamipur-ambala1.harpanchayats.gov.in 4 AMBALA AMBALA-I ANANDPUR JALBERA http://gpanandpurjalbera.harpanchayats.gov.in 5 AMBALA AMBALA-I BABAHERI http://gpbabaheri.harpanchayats.gov.in 6 AMBALA AMBALA-I BAKNAUR http://gpbaknaur.harpanchayats.gov.in 7 AMBALA AMBALA-I BALANA http://gpbalana-ambala1.harpanchayats.gov.in 8 AMBALA AMBALA-I BALAPUR http://gpbalapur.harpanchayats.gov.in 9 AMBALA AMBALA-I BARA http://gpbara-ambala1.harpanchayats.gov.in 10 AMBALA AMBALA-I BAROULA http://gpbaroula.harpanchayats.gov.in 11 AMBALA AMBALA-I BAROULI http://gpbarouli-ambala1.harpanchayats.gov.in 12 AMBALA AMBALA-I BATROHAN http://gpbatrohan.harpanchayats.gov.in 13 AMBALA AMBALA-I BEDSAN http://gpbedsan.harpanchayats.gov.in 14 AMBALA AMBALA-I BEGO MAJRA http://gpbegomajra.harpanchayats.gov.in 15 AMBALA AMBALA-I BEHBALPUR http://gpbehbalpur-ambala1.harpanchayats.gov.in 16 AMBALA AMBALA-I BHANOKHERI http://gpbhanokheri.harpanchayats.gov.in 17 AMBALA AMBALA-I BHANPUR NAKATPUR http://gpbhanpurnakatpur.harpanchayats.gov.in 18 AMBALA AMBALA-I BHARI http://gpbhari.harpanchayats.gov.in 19 AMBALA AMBALA-I BHUNNI http://gpbhunni.harpanchayats.gov.in 20 AMBALA AMBALA-I BHURANGPUR http://gpbhurangpur.harpanchayats.gov.in 21 AMBALA AMBALA-I BHURE MAJRA http://gpbhuremajra.harpanchayats.gov.in 22 AMBALA -

International Brochure 2019
(DEEMED TO BE UNIVERSITY) OF ACADEMIC Mullana-Ambala, Haryana, India EXCELLENCE (Established under Section 3 of UGC Act, 1956) (Accredited by NAAC with Grade ‘A’) THINK. LEARN. SUCCEED. INTERNATIONAL STUDENT INFORMATION GUIDE 2019-20 • The Maharishi Markandeshwar Trust (MMT) is the brain child of Shri Tarsem Kumar Garg, a great visionary and social entrepreneur. • The Trust has grown in a short span of over two decades into a group of institutions imparting high quality education targeted at generating employment, creating entrepreneurs and training M students, researchers & professionals. • The institutions under the trust have been rated by Globally renowned agencies as the best in their domains. • The professional, medical & technical institutions under the aegis of the MMT collectively seek to innovate & discover synergies to maximize opportunities for all its stakeholders. • Innovative, synergistic, integrated and inter- M disciplinary courses, such as Hospital Management, Hospitality Management, Mechatronics, Bio Technology etc. are offered. • Doctoral programs are offered to enhance the research skills qualitatively, in the society. • Nation building through the development of human T resource is the ultimate objective of MMT. Bringing First First First First First World Class Self-financing Self-financing Self-financing Self-financing College Self-financing Engineering Medical College Deemed to be of Hotel Management & Medical College Education to You! College in Haryana in Haryana University Catering Technology in Himachal Pradesh Sh. Tarsem Kumar Garg in Haryana in Haryana Hon'ble Chancellor, MMUs I believe that one can only grow by sharing and giving. I’ve always believed in strong principles “Best Medical Education, I could ever “Best education combined with and value-based policies. -

Analysis & Simulated Designe of Number Plate Detection
ISSN : 0976-8491 (Online) | ISSN : 2229-4333 (Print) IJCST VOL . 4, Iss UE 1, JAN - MAR C H 2013 Analysis & Simulated Designe of Number Plate Detection 1Dr. Amit Verma, 2Ravi Kant, 3Parminder Kaur, 4Surinder Kaur, 5Iqbaldeep Kaur 1,4,5Dept. of CSE, Chandigarh University, Gharuan, Mohali, Punjab, India 2Dept. of ECE, PTU, RBIEBT 3PTU, RBIEBT Abstract recognition rate with the image processing algorithms [2]. In real time number plate detection , some vehicle number plates can not be recognized due to very poor illumination, motion II. Applications of Object Detection blurred effect, fade characters and so on. The key problem is Detection means finding the location of the object and recognizing that number plate can not be segmented accurately and correctly. what it is . traffic control video surveillance of unattended outdoor Many techniques have been proposed. In this paper, we present a environments, video surveillance of objects. edge detection method based on neural network. In Neural network Applications of digital image processing are such as: systems, each character is introduced as an input data to the system. A. Digital Camera Images: Digital cameras generally include The system learns these characters. After that, it compares the dedicated digital image processing chips to convert the raw data input data characters to the existing characters. As a result, the from the image sensor into a colour-corrected image in a standard character which has very similar rate is activated. Neural Network. image file format. Images from digital cameras often receive classifier is used to recognize the characters.in which adaboost further processing to improve their quality, a distinct advantage and template matching techniques are also used for more accuracy that digital cameras have over film cameras.