Agora� a Minimal Distributed Proto Col For
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Myagora Parent Update for January 4, 2018
myAgora Parent Update for January 4, 2018 Subscribe Past Issues Translate RSS View this email in your browser Welcome Back! One Last Final Reminder: Deadline to Submit Fall ISP Rebate is January 5! Friday, January 5 is the deadline to submit your internet bill for the Fall ISP Rebate! Parents/legal guardians can log in to the Sapphire Community Web Portal to submit for the Fall Rebate period which covers September through December and is due by January 5, 2018. Fall rebate checks will be mailed January 31, 2018. Watch this video for step-by-step instructions on how to submit your ISP rebate. Additional information can be found on our website at https://agora.org/pupil-parent- services/isp-rebate-program/ https://us13.campaign-archive.com/?u=2a591de2a33ed5c751ca978a2&id=205e786611[1/23/2018 3:10:45 PM] myAgora Parent Update for January 4, 2018 PLEASE NOTE: We cannot accept Internet bills submitted by email, fax, mail or Agora Staff on behalf of families. If you need help setting up your Sapphire account, visit our Resources & Guides page on the Agora.org website https://agora.org/resources-and- guides/ Time to RSVP For National School Choice Events! Parents at Agora know that school choice is one of the most important decisions you'll make for your child so we are joining with schools all across this country to celebrate! During the last week in January and into early February, Agora will be part of these special events to raise public awareness of the different K-12 education options available to children and families, while spotlighting the benefits of school choice. -

Guia Rápido Firefox, Pegue O Seu Aqui: Personalizar
ARQUIVO HISTÓRICO no topo da página. Você pode desbloqueá-lo ou não, clicando Nova Janela Ctrl N Voltar Alt ¬ no botão Opções da barra. Para liberar todos os Popup, Nova Aba Ctrl T Avançar Alt ® escolha em Preferências/Opções, Conteúdo e ligue ou Abrir endereço... Ctrl L Página Inicial Alt Home desligue a opção Bloquear Janelas Popup. Curso a Distância e Grátis – você pode fazer o curso Abrir Arquivo... Ctrl O Exibir todo o histórico Ctrl Shift H do Firefox a distância e de graça no site www.cdtc.org.br (p/ Fechar Janela Alt F4 ou Ctrl Shift W Reabrir Aba todos) e em http://cursos.cdtc.org.br (p/ funcionário público). Fechar Aba Ctrl F4 ou Ctrl W FAVORITOS Download do Firefox: Para fazer o download do Salvar Como... Ctrl S Adicionar página... Ctrl D programa Mozilla Firefox, acesse: www.mozilla.com/en- Enviar Endereço Inscrever RSS... US/firefox/all.html Configurar Página... Adicionar todas as abas... Ctrl Shift D Extensões: São programas adicionados ao Firefox para Visualizar Impressão Organizar Favoritos ... torná-lo mais poderoso. Você pode adicionar novos recursos e adaptar o seu Firefox ao seu estilo de navegar. A instalação Imprimir... Ctrl P Barra dos Favoritos pode ser feita a partir da opção Complementos em Importar... Favoritos recentes Ferramentas. Exemplos: Sage (leitor de RSS), Forecastfox Modo Offline Marcadores recentes (previsão do tempo), Tab Mix Plus, etc. Sair Get Bookmarks Add-ons Favorito Dinâmico – RSS: O conteúdo do favorito Mozilla Firefox dinâmico é atualizado periodicamente, não necessita visitar o EDITAR FERRAMENTAS site constantemente pra saber das novidades. -

Student Handbook and Academic Catalog
20 21 STUDENT HANDBOOK & ACADEMIC CATALOG Revised 06.21.2021 www.agora.ac | 1.866.GO.AGORA 2021 Agora University Contact Information 7406 Alban Station Court • Suite B207 Springfield, VA 22150 Phone:1.866.GO.AGORA Fax: 202.930.7909 Agora University is a religious institution exempt from state regulation and oversight in the Commonwealth of Virginia. Hours of Operation Agora University’s programs and courses are always available through our Learning Management System. Our faculty and support staff are available: Monday – Friday 9:00 am to 4:00 pm EST Agora University offices are closed during the following holidays: Martin Luther, King Jr. Day, Presidents Day, Eastern Orthodox Holy Week, Good Friday, Memorial Day, Independence Day, Labor Day, Veteran’s Day, Thanksgiving Week, and the final two weeks of December through January 7th of every year. 2 | AGORA Handbook Version 2021.06.21 Contents Contents Contents .......................................................................................................................................................................... 3 A LETTER FROM THE CHANCELLOR ................................................................................................................................. 6 ABOUT AGORA UNIVERSITY ............................................................................................................................................ 7 AGORA UNIVERSITY MISSION ......................................................................................................................................... -

Why Websites Can Change Without Warning
Why Websites Can Change Without Warning WHY WOULD MY WEBSITE LOOK DIFFERENT WITHOUT NOTICE? HISTORY: Your website is a series of files & databases. Websites used to be “static” because there were only a few ways to view them. Now we have a complex system, and telling your webmaster what device, operating system and browser is crucial, here’s why: TERMINOLOGY: You have a desktop or mobile “device”. Desktop computers and mobile devices have “operating systems” which are software. To see your website, you’ll pull up a “browser” which is also software, to surf the Internet. Your website is a series of files that needs to be 100% compatible with all devices, operating systems and browsers. Your website is built on WordPress and gets a weekly check up (sometimes more often) to see if any changes have occured. Your site could also be attacked with bad files, links, spam, comments and other annoying internet pests! Or other components will suddenly need updating which is nothing out of the ordinary. WHAT DOES IT LOOK LIKE IF SOMETHING HAS CHANGED? Any update to the following can make your website look differently: There are 85 operating systems (OS) that can update (without warning). And any of the most popular roughly 7 browsers also update regularly which can affect your site visually and other ways. (Lists below) Now, with an OS or browser update, your site’s 18 website components likely will need updating too. Once website updates are implemented, there are currently about 21 mobile devices, and 141 desktop devices that need to be viewed for compatibility. -

Open Access Bibliography This Work Has Been Published As a Printed Book By
open access bibliography This work has been published as a printed book by: Association of Research Libraries 21 Dupont Circle, NW, Suite 800 Washington, D.C. 20036 ISBN 1-59407-670-7 ISBN 978-1-59407-670-1 It can be ordered from: ARL Publications Distribution Center PO Box 531 Annapolis Junction, MD 20701-0531 Phone: 301-362-8196 Fax: 301-206-9789 Orders: [email protected] http://www.arl.org/pubscat/pubs/openaccess/ http://www.arl.org/pubscat/index.html Open Access Bibliography Liberating Scholarly Literature with E-Prints and Open Access Journals Charles W. Bailey, Jr. Association of Research Libraries 2005 Association of Research Libraries 21 Dupont Circle, NW, Suite 800 Washington, D.C. 20036 © 2005 Charles W. Bailey, Jr. This work is licensed under the Creative Commons Attribution-NonCommercial License. To view a copy of this license, visit http://creativecommons.org/licenses/by-nc/2.0/ or send a letter to Creative Commons, 559 Nathan Abbott Way, Stanford, California 94305, USA. ISBN 1-59407-670-7 ISBN 978-1-59407-670-1 The paper used in this publication meets the requirements of ANSI/NISO Z39.48-1992 (R1997) Permanence of Paper for Publications and Documents in Libraries and Archives. Design and layout by David S. Noble. contents preface xi acknowledgments xv key open access concepts xvi i. general works 3 1.1 Overviews 3 1.2 Analysis and Critiques 6 1.3 Debates and Dialogs 10 1.3.1 Nature Web Debate on Future E-Access to the Primary Literature 10 1.3.2 Nature Web Focus on Access to the Literature: The Debate Continues 13 1.3.3 Other 15 1.4 Research Studies 15 1.5 Other 16 ii. -

The Internet Companion, 2Nd Edition
The Internet Companion, 2nd edition The Internet Companion A Beginner's Guide to Global Networking (2nd edition) by Tracy LaQuey The OBS is pleased to present our free, "distributive" full-text HTML version of the second edition of this bestselling title, linked to resources around the world. As with all our distributive publications, we invite you to browse, comment, and send in your link suggestions. We are also pleased to offer paths to a sibling version of the Internet Companion, produced as a class project at the University of North Carolina. This use of online files points the way to a new form of reading and publishing on the Net: true interactivity where the students or readers can affect a book's content by finding, choosing, and implementing links for it. About the Internet Companion What World Media is Saying About the Internet Companion About Tracy LaQuey Copyright The Internet Companion at the University of North Carolina Buy this Book http://www.obs-us.com/obs/english/books/editinc/top.htm (1 of 3) [5/1/1999 11:46:04 PM] The Internet Companion, 2nd edition Contents Front Matter Foreword Preface Chapter 1 What Is the Internet and Why Should You Know About It? Whence It Came It Keeps Going and Going . The Equalizer Peeling Back the Layers: Differences between Networks Convergence: A Traffic Circle on the Information Highway Mrs. Smith Connects to Washington Business Use Backing Out of the Driveway The Future Chapter 2 Internet: The Lowdown A Network of Networks In the Beginning How Computers Talk Who Runs the Internet? Acceptable -

Webrtc for Business People
API Platform Vendors: Agora This is an example of what you can expect to find for each vendor covered in the Choosing a WebRTC API Platform report, courtesy of Agora. The following four pages include the information covering Agora capabilities related to WebRTC. The full report covers the following active vendors: The report is available for purchase online at https://bloggeek.me/webrtc-paas-report Choosing a WebRTC API Platform; 9th edition Licensed for [YOUR COMPANY] Agora At a glance Focus Real Time Engagement services Reference • Bunch (bunch.live) Customers • Dr First (drfirst.com) • Noon Academy (noonacademy.net) • Scener (scener.com) • The Meet Group (themeetgroup.com) History & Founded in 2013, Agora offers a Real Time Engagement Platform-as-a- Pedigree service (RTE PaaS) that allows developers to easily embed voice and video call or interactive streaming, and text messaging on a global scale for mobile, web, desktop, or XR application Main office Santa Clara, CA (United States) Size 498 employees as of Q1 2020 Financials Raised $350 million in its IPO in June 2020 Interesting stat Agora powers an average of over 40 billion real-time voice and video minutes per month globally Data centers Agora has over 250 data centers across the globe Consider when you’re looking for a very low latency voice or video call solution over the public Internet, and an interactive streaming solution for very large group sessions (up to 1 million peak concurrent users) Skip if you’re looking for traditional telephony 1 ©2020 BlogGeek.me All Rights Reserved Choosing a WebRTC API Platform; 9th edition Licensed for [YOUR COMPANY] Overview Agora founded in 2013, enabling developers to easily embed voice and video call for mobile, web, desktop or XR application. -
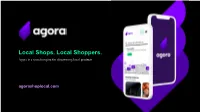
Local Shops. Local Shoppers. Agora Is a Search Engine for Discovering Local Products
Local Shops. Local Shoppers. Agora is a search engine for discovering local products. agorashoplocal.com Founding Story. When coming out of class in Harvard Square, Allie remembered the need for a black dress. She thought to herself, why Why cant I just can’t I search for it in stores nearby? search “black dress” on my This problem continued to persist for phone and know where items beyond just clothing. they are in stores near me? Allie stumbled upon the demand for... a search engine for Allie Walsh local inventory. Founder & CEO of Agora Two Ways to Shop. If a search engine for local inventory existed, we could combine the best aspects of both retail experiences. In-Person Retail. Online Shopping. Immediate gratification and ability Able to see across multiple retailers; to use. can compare items/prices easily. No shipping delay. Higher certainty about getting a “good deal”. Uncertainty about whether you will find desired product and whether you are No physical interaction with product getting the best deal. upon purchase. Wasted time going from store to store. Delayed gratification; 2 day shipping or longer. Lack of price transparency from inability to compare across vendors Delay and ambiguity with returns and in person. package tracking. The Problem. 70% of In-Person Retail. stores find Local stores struggle due to Amazon’s inventory dominance and COVID-19. They need help optimization to generating more internet and foot traffic. be a problem* Inventory optimization is also a problem. The data generated from searching Agora can help stores optimize their inventory. Inventory systems are a highly fragmented market with many stores using 53% of For Consumers. -

Insight Installation Directions
INSIGHT INSTALLATION DIRECTIONS During the 2017-18 school year, all middle and high school students are required to install the INSIGHT software to complete their CDT assessments. Agora recommends families install the INSIGHT software using Mozilla Firefox. You cannot install the software using Internet Explorer. 1. Click the installation link below: Tinyurl.com/CDTinstall 2. Click ‘Download’. 3. Disregard the security warning. The installation file is safe. Click ‘Download anyway’. 4. If using Mozilla Firefox, the next step after clicking ‘Download anyway’ is to click 5. If using Mozilla Firefox and the file doesn’t launch, click the arrow in the top-right corner of your page and select the file titled ‘DRN_INSIGHT_Setup_Student.msi’. Then click ‘Run’. 1 | P a g e INSIGHT INSTALLATION DIRECTIONS 6. If using Mozilla Firefox a security warning may appear. The file is safe. Click OK and then Run. 7. If using Google Chrome click the file in the bottom-left corner of the page to open the file. It is titled ‘DRN_INSIGHT_Setup_Student.msi’. Then click ‘Run’. 2 | P a g e INSIGHT INSTALLATION DIRECTIONS 8. After selecting Run, both Chrome and Firefox will launch the System Setup Wizard. Click ‘Next’. 9. Click the bubble next to ‘I accept the terms in the License Agreement’ and click ‘Next. 10. Leave the boxes checked and click ‘Next’. It’s important to have the software on your Desktop and Start Menu for easy access. 3 | P a g e INSIGHT INSTALLATION DIRECTIONS Note, your computer will momentarily lock during the System Readiness Check and you will not be able to open any other programs. -
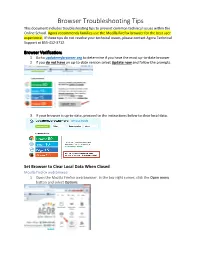
Browser Troubleshooting Tips This Document Includes Troubleshooting Tips to Prevent Common Technical Issues Within the Online School
Browser Troubleshooting Tips This document includes troubleshooting tips to prevent common technical issues within the Online School. Agora recommends families use the Mozilla Firefox browser for the best user experience. If these tips do not resolve your technical issues, please contact Agora Technical Support at 855-412-3712. Browser Verification: 1. Go to updatemybrowser.org to determine if you have the most up-to-date browser 2. If you do not have an up-to-date version select Update now and follow the prompts. 3. If your browser is up-to-date, proceed to the instructions below to clear local data. Set Browser to Clear Local Data When Closed Mozilla Firefox web browser: 1. Open the Mozilla Firefox web browser. In the top-right corner, click the Open menu button and select Options Browser Troubleshooting Tips 2. Click the Privacy button 3. In the History section, set Firefox will: to Use custom settings for history 4. Select the check box for Clear history when Firefox closes 5. Click the Settings... button. The Settings for Clearing History window will open 6. In the Settings for Clearing History window, click the check mark box next to Cache. 7. Click OK and you are all done. Call Technical Support at 855-412-3712 if you need additional support. Browser Troubleshooting Tips Google Chrome Note: Agora recommends students use the Mozilla Firefox browser for the best user experience. If you are using Chrome, discontinue and open the Mozilla Firefox browser. If you can only use Chrome at this time, follow the instructions below. 1. -

Kenneth Arnes Ryan Paul Jaca Network Software Applications History
Kenneth Arnes Ryan Paul Jaca Network Software Applications Networks consist of hardware, such as servers, Ethernet cables and wireless routers, and networking software. Networking software differs from software applications in that the software does not perform tasks that end-users can see in the way word processors and spreadsheets do. Instead, networking software operates invisibly in the background, allowing the user to access network resources without the user even knowing the software is operating. History o Computer networks, and the networking software that enabled them, began to appear as early as the 1970s. Early networks consisted of computers connected to each other through telephone modems. As personal computers became more pervasive in homes and in the workplace in the late 1980s and early 1990s, networks to connect them became equally pervasive. Microsoft enabled usable and stable peer-to-peer networking with built-in networking software as early as 1995 in the Windows 95 operating system. Types y Different types of networks require different types of software. Peer-to-peer networks, where computers connect to each other directly, use networking software whose basic function is to enable file sharing and printer sharing. Client-server networks, where multiple end-user computers, the clients, connect to each other indirectly through a central computer, the server, require networking software solutions that have two parts. The server software part, running on the server computer, stores information in a central location that client computers can access and passes information to client software running on the individual computers. Application-server software work much as client-server software does, but allows the end-user client computers to access not just data but also software applications running on the central server. -

JULY 13, 2021 the Joy of Sweat: the Strange Science of Perspiration
SANTA CRUZ RECORD JULY13, 2021 – VOL. 50, #39 LOCAL BUSINESS STARTS HERE WWW.SANTACRUZRECORD.COM MAY 4, 2021 – VOL. 50, #29 LOCAL BUSINESS STARTS HERE WWW.SANTACRUZRECORD.COM National SBIR Week he Small Business Association will The SBIR program was created to Small Business Innovation Research Tbe hosting the 2021 National SBIR support scientific excellence and (SBIR) and Small Business Technology Week, to connect entrepreneurs with technological innovation through the Transfer (STTR) programs. Also known SBIR/STTR program managers through investment of federal as America’s Seed Fund, live panels & direct 1-on-1 meetings. research funds in criti- these programs provide The Small Business Innovation Re- cal American priorities over $4 billion in funding search (SBIR) program is a highly com- to build a strong na- to small businesses each petitive United States Government tional economy. In the year in a wide variety of funding source, coordinated by the words of program founder Roland Tib- technology areas. Small Business Administration. It is in- betts: “to provide funding for some of This event provides you with an op- tended to encourage domestic small the best early-stage innovation ideas, portunity to participate in live stream- businesses to engage in high-growth ideas that, however promising, are still ing panels and presentations with research and development (R&D). too high risk for private investors, in- participating federal agencies that Funding takes the form of contracts cluding venture capital firms.” administer over 7,000 new awards an- or grants and the awardee projects This is a virtual event connecting en- nually and to meet virtually One on must have the potential for commer- trepreneurs working on advanced One with program decision makers.