NATIVE SAML SUPPORT for SSO FFTH – RSA Archer 6.8
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Not for Reproduction
LSC Display Module INSTRUCTION MANUAL Reproduction for Not PHONE (308) 995-4495, (800) 562-1373 FAX (308) 995-5887 PARTS DEPT. FAX (308) 995-4883 WEB www.allmand.com Reproduction for Not TABLE OF CONTENTS MAIN OPERATING SCREEN ..................................................................1 Menu Screen .......................................................................................................................................3 Automatic Control Setup Screen ...................................................................................................4 Timed Events Menu Screen .....................................................................................................5 Timed Events Screen .........................................................................................................6 Copy Day Events Screen ...................................................................................................7 Block Heater Setup Screen ......................................................................................................8 Auto-Mode – Sunset/Sunrise-based Start/Stop Screen ...........................................................9 GPS Location Setup Screen ....................................................................................................10 System Screen ..............................................................................................................................11 Update Programming Screen ..................................................................................................12 -

Duty Station: Kathmandu, Nepal
INDIVIDUAL CONSULTANT PROCUREMENT NOTICE (International Consultant – Human Rights Expert) UNDP/PN/31/2017 Date: 31 July 2017 Country: Nepal Description of the assignment: SPSP project needs a Human Rights Expert. He/She will be responsible to provide day-to-day management and technical support to implement the Project activities and ensure that the Project objectives are met as set out in the Project document. The expert will report directly to the Deputy Country Director (Programme) and be responsible to the secretary of the NHRC. Number of consultant required: 1 Project name: Strategic Plan Support Project for the National Human Rights Commission (SPSP) Period of assignment/services (if applicable): 01 September – 31 December 2017 (not to exceed 87 days in total) Duty Station: Kathmandu, Nepal Proposal should be submitted at the following address: Procurement Unit, UNDP (Ref.: UNDP/PN/31/2017: Human Rights Expert, UN House, Pulchowk, PO Box 107, Kathmandu, Nepal or by email to [email protected] not later than 1730 hours (Nepal Standard Time) of 09 August 2017. Any request for clarification must be sent in writing, or by standard electronic communication to the e- mail: [email protected] mentioning Procurement Notice Ref: UNDP/PN/31/2017: Human Rights Expert, on or before 03 August 2017. The procurement unit will respond in writing, including an explanation of the query without identifying the source of inquiry, to all consultants or via bulletin published on the UNDP website: http://www.np.undp.org/content/nepal/en/home/operations/procurement.html. Inquiries received after the above date and time shall not be entertained. -

Treadmill Operation
Adventure 1 Adventure 5 Adventure 3 Adventure 7 OPERATION GUIDE TREADMILL OPERATION This section explains how to use your treadmill’s console and programming. The BASIC OPERATION section in the TREADMILL GUIDE has instructions for the following: • LOCATION OF THE TREADMILL • USING THE SAFETY KEY • FOLDING THE TREADMILL • MOVING THE TREADMILL • LEVELING THE TREADMILL • TENSIONING THE RUNNING BELT • CENTERING THE RUNNING BELT • USING THE HEART RATE FUNCTION 2 3 K H M D A O E I ADVENTURE 1 CONSOLE OPERATION Note: There is a thin protective sheet of clear plastic on the overlay of the console that should be removed before use. A) LED DISPLAY WINDOW: time, distance, speed, calories, incline and heart rate. B) START/PAUSE KEY: press to start workout and pause workout. Time Distance Adventure 1 Zeit Entfernung C) STOP KEY: press to stop workout. Hold to reset console. Adventure 1 ENERGYSAVER Energiesparmodus Incline Speed Steigung Geschwindigkeit D) PROGRAM KEYS: press to select workout. Calories Kalorien E) ENTER KEY: press to confirm selection during programming setup. Heart Rate Herzfrequenz Programs Programme : press to adjust incline level. Enter F) INCLINE KEYS Eingabe Change Classic Calories Distance HRC Custom Display Klassisch Kalorien Entfernung Benutzer Anzeigenwechsel G) SPEED KEYS: press to adjust speed level. Quick Incline Keys 4 km/h 8 km/h 12 km/h 16 km/h 18 km/h Quick Speed Keys 2 % 4 % 6 % 8 % 10 % Direktwahl Geschwindigkeit Direktwahl Steigung 3 mph 5 mph 8 mph 10 mph 11 mph H) INCLINE QUICK KEYS: used to reach desired incline quickly. ADVENTURE1 I) SPEED QUICK KEYS: used to reach desired speed quickly. -

Dress Fashions of Royalty Kotte Kingdom of Sri Lanka
DRESS FASHIONS OF ROYALTY KOTTE KINGDOM OF SRI LANKA . DRESS FASHIONS OF ROYALTY KOTTE KINGDOM OF SRI LANKA Dr. Priyanka Virajini Medagedara Karunaratne S. Godage & Brothers (Pvt) Ltd. Dedication First Edition : 2017 For Vidyajothi Emeritus Professor Nimal De Silva DRESS FASHIONS OF ROYALTY KOTTE KingDOM OF SRI LANKA Eminent scholar and ideal Guru © Dr. Priyanka Virajini Medagedara Karunaratne ISBN 978-955-30- Cover Design by: S. Godage & Brothers (Pvt) Ltd Page setting by: Nisha Weerasuriya Published by: S. Godage & Brothers (Pvt) Ltd. 661/665/675, P. de S. Kularatne Mawatha, Colombo 10, Sri Lanka. Printed by: Chathura Printers 69, Kumaradasa Place, Wellampitiya, Sri Lanka. Foreword This collection of writings provides an intensive reading of dress fashions of royalty which intensified Portuguese political power over the Kingdom of Kotte. The royalties were at the top in the social strata eventually known to be the fashion creators of society. Their engagement in creating and practicing dress fashion prevailed from time immemorial. The author builds a sound dialogue within six chapters’ covering most areas of dress fashion by incorporating valid recorded historical data, variety of recorded visual formats cross checking each other, clarifying how the period signifies a turning point in the fashion history of Sri Lanka culminating with emerging novel dress features. This scholarly work is very much vital for university academia and fellow researches in the stream of Humanities and Social Sciences interested in historical dress fashions and usage of jewelry. Furthermore, the content leads the reader into a new perspective on the subject through a sound dialogue which has been narrated through validated recorded historical data, recorded historical visual information, and logical analysis with reference to scholars of the subject area. -

Docusign Envelope ID: 3F71DABF-9E5D-4742-9D5D-E477C06C49A4 Docusign Envelope ID: 3F71DABF-9E5D-4742-9D5D-E477C06C49A4
DocuSign Envelope ID: 3F71DABF-9E5D-4742-9D5D-E477C06C49A4 DocuSign Envelope ID: 3F71DABF-9E5D-4742-9D5D-E477C06C49A4 IMPORTANT INFORMATION or at Phuentsholing check post. Further advice from Customs authorities in the US At Greaves Tours LLC we strongly hope that your information on Visas for Bhutan may be before departing on your tour. When shopping holiday lives up to your expectations. Our years discussed with your travel consultant or for expensive items such as precious stones, of experience in dealing with the Indian through the Bhutan Mission to the United carpets etc, the shopkeepers may guarantee the Subcontinent has gone into formulating the tour Nations in New York Tel: 1-212-682-2268 authenticity of the item, however expert programs on offer. Due care has been taken to knowledge is essential to ascertain their true put the best possible ground arrangements in TIBET: value. Please note that Greaves Tours LLC place for you to have a memorable holiday. Visas for Tibet will be processed by Greaves cannot be held responsible for any purchase that Tours LLC. The cost of the Visa for Tibet is you make and nor can we take up However, we seek your patience and included in your tour price. Visa applications correspondence on your behalf if you are not understanding while travelling in the and documentation will be completed by you satisfied with the item purchased or if goods are Subcontinent. Sometimes minor problems may on tour whilst in Kathmandu, en route to Tibet. not delivered in time. We pride ourselves on the occur, but our ground staff will always be on Only once the Visa has been cleared can quality of our sightseeing guides, however if at hand to try and solve such occurrences. -
![JOURNEY to the END of the EARTH BY-TISHANI DOSHI CLASS XII ENGLISH [CORE] VISTAS PRESENTED by MRS LILY KUMAR DELHI PUBLIC SCHOOL RANCHI Akademik Shokalskiy](https://docslib.b-cdn.net/cover/5738/journey-to-the-end-of-the-earth-by-tishani-doshi-class-xii-english-core-vistas-presented-by-mrs-lily-kumar-delhi-public-school-ranchi-akademik-shokalskiy-615738.webp)
JOURNEY to the END of the EARTH BY-TISHANI DOSHI CLASS XII ENGLISH [CORE] VISTAS PRESENTED by MRS LILY KUMAR DELHI PUBLIC SCHOOL RANCHI Akademik Shokalskiy
JOURNEY TO THE END OF THE EARTH BY-TISHANI DOSHI CLASS XII ENGLISH [CORE] VISTAS PRESENTED BY MRS LILY KUMAR DELHI PUBLIC SCHOOL RANCHI Akademik Shokalskiy • MV Akademik Shokalskiy (Russian: Академик Шокальский) is an Akademik Shuleykin-class ice- strengthened ship, built in Finland in 1982 and originally used for oceanographic research.In 1998 she was fully refurbished to serve as a research ship for Arctic and Antarctic work; she is used also for expedition cruising. She is named after the Russian oceanographer Yuly Shokalsky. • For two weeks from 25 December 2013 Akademik Shokalskiy was trapped in thick ice in Commonwealth Bay, Antarctica, while operating an expedition for the Australasian Antarctic Expedition 2013-2014. The scientists and passengers were evacuated on 2 January. Introduction to the author: tishani doshi Tishani Doshi (9 December 1975) is an Indian poet, journalist and a dancer based in Chennai. Born in Madras, India, to a Welsh mother and Gujarati father, she graduated with a Master’s degree in Creative Writing from the Johns Hopkins University. She received Eric Gregory Award in 2001. Her first poetry collection Countries of the Body won the 2006 Forward Poetry Prize for the best first collection. Her First novel The Pleasure Seekers was published by Bloomsbury in 2010 and was long-listed for the Orange Prize in 2011 and shortlisted for The Hindu Best Fiction Award in 2010. She works as a freelance writer and worked with choreographer Chandralekha. Her poetry collection Everything Begins Elsewhere was published by Copper Canyon Press in 2013. Her most recent book of poetry, Girls Are Coming Out Of the Woods, was published by HarperCollins India in 2017. -

PGNP Native OLE DB Provider for Postgresql, Greenplum, Redshift Developer’S Manual
CATA 2021 PGNP Native OLE DB Provider for PostgreSQL, Greenplum, Redshift Developer’s Manual This document contains description of various PGNP features, use cases and programming techniques. It is written for professional developers. Konstantin Izmailov Copyright © 2006-2019. All Rights Reserved. 2/12/2021 This document is property of PGNP team. Neither a part nor the entire document can be reproduced, changed, distributed or published without prior written permission of owners. Please contact us if you have any questions: [email protected]. Page 2 Table of Contents 1 Introduction .................................................................................................................................................................... 6 2 Installation and Product Activation ................................................................................................................................ 7 2.1.1 UI based installation ........................................................................................................................................ 7 2.1.2 Unattended/silent installation ...................................................................................................................... 10 2.1.3 Activation on a computer behind a firewall (in DMZ) .................................................................................. 11 3 Provider’s Features ...................................................................................................................................................... -

Research Report Irides Fact-Finding and Relationship-Building Mission
Research Report InternationalResearch Research Institute of Disaster Science Research Report IRIDeS Fact-finding and Relationship-building Mission to Nepal IRIDeS Fact-finding and Relationship-building Mission to Nepal International Research Institute of Disaster Science Tohoku University Sendai, Japan 13 March 2016 IRIDeS Fact-Finding and relationship-building mission to Nepal IRIDeS Task Force Team Hazard and Risk Evaluation Research Division: Prof. F. Imamura, Prof. S. Koshimura, Dr. J. D. Bricker, Dr. E. Mas Human and Social Response Research Division: Prof. M. Okumura, Dr. R. Das, Dr. E. A. Maly Regional and Urban Reconstruction Research Division: Dr. S. Moriguchi, Dr. C. J. Yi Disaster Medical Science Division: Prof. S. Egawa (Team Leader), Prof. H. Tomita, Emeritus Prof. T. Hattori, Dr. H. Chagan-Yasutan, Dr. H. Sasaki Disaster Information Management and Public Collaboration Division: Dr. A. Sakurai i IRIDeS Fact-Finding and relationship-building mission to Nepal IRIDeS would like to expresses our gratitude to the following people: IRIDeS Task Force Team ¥ Mr. Khagaraj Adhikari Minister, MoHP ¥ Dr. Lohani Guna Raj, Secretary, MoHP ¥ Dr. Basu Dev. Pandey, Director, Division of Leprosy Control, MoHP ¥ Dr. Khem Karki; Member Secretary, Nepal Health Research Council, MoHP Hazard and Risk Evaluation Research Division: ¥ Mr. Edmondo Perrone, Cluster coordinator/World Food Program Prof. F. Imamura, Prof. S. Koshimura, Dr. J. D. Bricker, Dr. E. Mas ¥ Mr. Surendra Babu Dhakal, World Vision Internationa ¥ Mr. Prafulla Pradhan, UNHabitat ¥ Mr. Vijaya P. Singh, Assistant Country Director, UNDP Nepal Office Human and Social Response Research Division: ¥ Mr. Rajesh Sharma, Programme Specialist UNDP Bangkok Regional Hub Prof. M. Okumura, Dr. R. Das, Dr. -

ISRAEL Executive Summary
Underwritten by CASH AND TREASURY MANAGEMENT COUNTRY REPORT ISRAEL Executive Summary Banking The Israeli central bank is the Bank of Israel. Bank supervision is performed by the Bank of Israel’s Banking Supervision Department. Israel applies central bank reporting requirements. All transactions between residents and non- residents are reported to the Bank of Israel. Resident entities are permitted to hold fully convertible domestic and foreign currency bank accounts domestically and outside Israel. Non-resident entities are permitted to hold fully convertible domestic and foreign currency bank accounts within Israel. The banking system is dominated by Bank Hapoalim and Bank Leumi le-Israel. There are also another 15 commercial banks in operation, one non-bank financial institution plus five branches of foreign banks. Payments Israel has three principal payment systems: the RTGS system (Zahav), the Banks’ Automated Clearing House (Masav) and the Banks’ Paper-based Clearing House (BCH). The increased use of electronic and internet banking has led to growth in the use of electronic transfers and direct debits. Card payments are increasing rapidly, especially in the retail sector. Checks remain commonly used. Liquidity Management Israel-based companies have access to a variety of short-term funding options. There is also a range of short-term investment instruments available. Both cash concentration and notional pooling are used by companies in Israel to manage company and group liquidity. Trade Finance Israel has established free trade arrangements with the European Union (EU), the European Free Trade Association (EFTA), Mercosur (a common market comprising Argentina, Brazil, Paraguay and Uruguay), the USA, Panama, Colombia, Canada, Mexico, Egypt, Russia, Jordan, Vietnam, Sri Lanka and Turkey. -
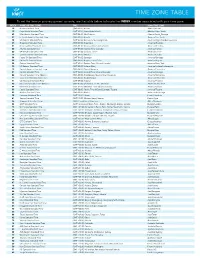
Time Zone Table
TIME ZONE TABLE To set the time on your equipment console, use the table below to locate the INDEX number associated with your time zone. INDEX NAME OF TIME ZONE TIME IANA TIME ZONE 10 Azores Standard Time (GMT-01:00) Azores Atlantic/Azores 12 Cape Verde Standard Time (GMT-01:00) Cape Verde Islands Atlantic/Cape_Verde 43 Mid-Atlantic Standard Time (GMT-02:00) Mid-Atlantic Atlantic/South_Georgia 27 E. South America Standard Time (GMT-03:00) Brasilia America/Sao_Paulo 58 SA Eastern Standard Time (GMT-03:00) Buenos Aires, Georgetown America/Argentina/Buenos_Aires 35 Greenland Standard Time (GMT-03:00) Greenland America/Godthab 51 Newfoundland Standard Time (GMT-03:30) Newfoundland and Labrador America/St_Johns 06 Atlantic Standard Time (GMT-04:00) Atlantic Time (Canada) America/Halifax 60 SA Western Standard Time (GMT-04:00) Caracas, La Paz America/La_Paz 17 Central Brazilian Standard Time (GMT-04:00) Manaus America/Cuiaba 54 Pacific SA Standard Time (GMT-04:00) Santiago America/Santiago 59 SA Pacific Standard Time (GMT-05:00) Bogota, Lima, Quito America/Bogota 28 Eastern Standard Time (GMT-05:00) Eastern Time (US and Canada) America/New_York 70 US Eastern Standard Time (GMT-05:00) Indiana (East) America/Indiana/Indianapolis 15 Central America Standard Time (GMT-06:00) Central America America/Costa_Rica 21 Central Standard Time (GMT-06:00) Central Time (US and Canada) America/Chicago 22 Central Standard Time (Mexico) (GMT-06:00) Guadalajara, Mexico City, Monterrey America/Monterrey 11 Canada Central Standard Time (GMT-06:00) Saskatchewan -

Service Bulletin: Viafit 2.0 Supplement Sheet
Service Bulletin: ViaFit 2.0 Supplement Sheet Prepared by: Date Prepared: Regina Templeton 9/23/2015 Models Affected: Elite T7 PROBLEM A limited number of new treadmills with ViaFit 2.0 software have been sent to customers. The cartons were missing a supplement sheet highlighting changes from the v1.0 software. The serial numbers of these treadmills are listed on the following page. SOLUTION The attached 4-page supplement sheet should be used in place of pages 8 and 9 in the OPERATION GUIDE. The supplement sheet is now being included in the carton, and it is also posted on the Horizon website. Treadmill Serial Numbers Container Number Serial Number TM4751505CC00001-TM4751505CC00007 TM4751505CC00009-TM4751505CC00012 TM4751505CC00014-TM4751505CC00027 TM4751505CC00030-TM4751505CC00041 TM4751505CC00043-TM4751505CC00054 GESU5188024 TM4751505CC00057-TM4751505CC00058 TM4751505CC00060-TM4751505CC00070 TM4751505CC00073-TM4751505CC00083 TM4751505CC00085-TM4751505CC00086 TM4751505CC00090-TM4751505CC00098 TM4751507CA00099-TM4751507CA00113 FCIU9814414 TM4751507CB00197-TM4751507CB00294 TGHU6676427 TM4751507CA00001-TM4751507CA00098 TM4751508CB00006 TM4751508CB00010-TM4751508CB00023 TM4751508CB00028 TM4751508CB00044 TM4751508CB00050 CBHU8429138 TM4751508CB00054-TM4751508CB00105 TM4751508CB00107-TM4751508CB00110 TM4751508CB00112-TM4751508CB00115 TM4751508CB00145 TM4751508CB00161 TM4751508CB00179-TM4751508CB00196 TM4751508CB00197-TM4751508CB00220 TM4751508CB00235-TM4751508CB00242 TM4751508CB00251-TM4751508CB00256 TM4751508CB00305-TM4751508CB00313 TM4751508CB00315-TM4751508CB00322 -

ISRAEL Executive Summary
Underwritten by CASH AND TREASURY MANAGEMENT COUNTRY REPORT ISRAEL Executive Summary Banking The Israeli central bank is the Bank of Israel. Bank supervision is performed by the Bank of Israel’s Banking Supervision Department. Israel applies central bank reporting requirements. All transactions between residents and non- residents are reported to the Bank of Israel. Resident entities are permitted to hold fully convertible domestic and foreign currency bank accounts domestically and outside Israel. Non-resident entities are permitted to hold fully convertible domestic and foreign currency bank accounts within Israel. The banking system is dominated by Bank Hapoalim and Bank Leumi le-Israel. There are also another 15 commercial banks in operation, one non-bank financial institution plus four branches of foreign banks. Payments Israel has three principal payment systems: the RTGS system (Zahav), the Banks’ Automated Clearing House (Masav) and the Banks’ Paper-based Clearing House (BCH). The increased use of electronic and internet banking has led to growth in the use of electronic transfers and direct debits. Card payments are increasing rapidly, especially in the retail sector. Checks remain commonly used. Liquidity Management Israel-based companies have access to a variety of short-term funding options. There is also a range of short-term investment instruments available. Both cash concentration and notional pooling are used by companies in Israel to manage company and group liquidity. Trade Finance Israel has established free trade arrangements with the European Union (EU), the European Free Trade Association (EFTA), Mercosur (a common market comprising Argentina, Brazil, Paraguay and Uruguay), the USA, Panama, Colombia, Canada, Mexico, Egypt, Russia, Jordan, Vietnam, Sri Lanka and Turkey.