Forensic Analysis of Xbox Consoles
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

The Dreamcast, Console of the Avant-Garde
Loading… The Journal of the Canadian Game Studies Association Vol 6(9): 82-99 http://loading.gamestudies.ca The Dreamcast, Console of the Avant-Garde Nick Montfort Mia Consalvo Massachusetts Institute of Technology Concordia University [email protected] [email protected] Abstract We argue that the Dreamcast hosted a remarkable amount of videogame development that went beyond the odd and unusual and is interesting when considered as avant-garde. After characterizing the avant-garde, we investigate reasons that Sega's position within the industry and their policies may have facilitated development that expressed itself in this way and was received by gamers using terms that are associated with avant-garde work. We describe five Dreamcast games (Jet Grind Radio, Space Channel 5, Rez, Seaman, and SGGG) and explain how the advances made by these industrially productions are related to the 20th century avant- garde's lesser advances in the arts. We conclude by considering the contributions to gaming that were made on the Dreamcast and the areas of inquiry that remain to be explored by console videogame developers today. Author Keywords Aesthetics; art; avant-garde; commerce; console games; Dreamcast; game studios; platforms; politics; Sega; Tetsuya Mizuguchi Introduction A platform can facilitate new types of videogame development and can expand the concept of videogaming. The Dreamcast, however brief its commercial life, was a platform that allowed for such work to happen and that accomplished this. It is not just that there were a large number of weird or unusual games developed during the short commercial life of this platform. We argue, rather, that avant-garde videogame development happened on the Dreamcast, even though this development occurred in industrial rather than "indie" or art contexts. -

Wind Waker Manual
OFFICIAL NINTENDO POWER PLAYER'S GUIDE AVAILABLE AT YOUR NEAREST RETAILER! WWW.NINTENDO.COM Nintendo of America Inc. P.O. Box 957, Redmond, WA 98073-0957 U.S.A. www.nintendo.com IN S T R U C T IO N B O O K LET 50520A IN S T R U C T IO N B O O K LET PRINTED IN USA W A R N IN G : P L E A S E C A R E FU L L Y R E A D T HE S E P A R A T E P R E C A U T IO N S B O O K L E T IN C L U D E D W IT H T HIS P R O D U C T WARNING - Electric Shock B E FO R E U S IN G Y O U R N IN T E N D O ® HA R D W A R E S Y S T E M , To avoid electric shock when you use this system: G A M E D IS C O R A C C E S S O R Y . T HIS B O O K L E T C O N T A IN S IM P O R T A N T S A FE T Y IN FO R M A T IO N . Use only the AC adapter that comes with your system. Do not use the AC adapter if it has damaged, split or broken cords or wires. -

Video Game Systems Uncovered
Everything You Ever Wanted To Know About... VIDEO GAMES But Never Dared To Ask! Introduction: 1 With the holidays quickly approaching the odds are you will be purchasing some type of video game system. The majority of U.S. households currently have at least one of these systems. With the ever changing technology in the video world it is hard to keep up with the newest systems. There is basically a system designed for every child’s needs, ranging from preschool to young adult. This can overwhelming for parents to choose a system that not only meets your child’s needs but also gives us the best quality system for our money. With the holidays coming that means many retailers will be offering specials on video game systems and of course the release of long awaited games. Now is also the time you can purchase systems in bundles with games included. Inside you will learn about all of these topics as well as other necessities and games to accompany to recent purchase. What you’ll find here: 2 In this ebook you will learn about console and portable video game systems, along with the accessories available. You will also find how many games each system has to offer. You will get an in depth look at the pro’s and con’s of each current system available in stores today, and the upcoming systems available in the near future. As a concerned parent you should also be aware of the rating label of the games and what the rating exactly means. -

The History of Nintendo: the Company, Consoles and Games
San Jose State University SJSU ScholarWorks ART 108: Introduction to Games Studies Art and Art History & Design Departments Fall 12-2020 The History of Nintendo: the Company, Consoles And Games Laurie Takeda San Jose State University Follow this and additional works at: https://scholarworks.sjsu.edu/art108 Part of the Computer Sciences Commons, and the Game Design Commons Recommended Citation Laurie Takeda. "The History of Nintendo: the Company, Consoles And Games" ART 108: Introduction to Games Studies (2020). This Final Class Paper is brought to you for free and open access by the Art and Art History & Design Departments at SJSU ScholarWorks. It has been accepted for inclusion in ART 108: Introduction to Games Studies by an authorized administrator of SJSU ScholarWorks. For more information, please contact [email protected]. The history of Nintendo: the company, consoles and games Introduction A handful of the most popular video games from Mario to The Legend of Zelda, and video game consoles from the Nintendo Entertainment System to the Nintendo Switch, were all created and developed by the same company. That company is Nintendo. From its beginning, Nintendo was not a video gaming company. Since the company’s first launch of the Nintendo Entertainment System, or NES, to the present day of the latest release of the Nintendo Switch from 2017, they have sold over 5 billion video games and over 779 million hardware units globally, according to Nintendo UK (Nintendo UK). As Nintendo continues to release new video games and consoles, they have become one of the top gaming companies, competing alongside Sony and Microsoft. -

Super Smash Bros. for Wii U That You've Unlocked
1 Importan t Informati on Gtget in Srdta te 2 Supporte d Controlle rs 3 amiibo 4 Internet Enhancemen ts 5 Note to Par ents and Guardi ans TeBh aiss c 6 What K ind of Game I s Th is? 7 Srnta ti g a Gam e 8 Saving an d Deleting D ata Actio ns ( Wii U Ga mePa d) 9 Meov mten 10 Aatt ckgin 11 Shields WUP-P-AXFE-04 Actions (For Other Controlle rs) 12 Meov mten 13 Atta cki ng/Shie ldi ng Sett ing Up a Mat ch 14 Sitart ntg Ou 15 Bsca i Rlsu e 16 Items Mode I ntroducti on 17 Smash 18 Oinl ne (Bt)at le 19 Online (Spec tator/Share /Even ts) 20 Sahm s Toru 21 Games & M ore (Solo/Gro up) 22 Geamus & More (Cts om /e Steag Build)r 23 Games & Mor e (Vault/Optio ns) Other 24 CnonnNeict go t intdenSeoD 3 Systsm 25 Play ing with a mii bo 26 Post ing to Mii ver se 27 Download able Conte nt Fhig tser 28 Mario/Donke y Kong/Link/Sa mus 29 YhKos i/ ir/xby Fo 30 Pikachu/Lui gi/Captain Fal con 31 Ness/Jig glypuff/Pea ch 32 Bows er/ Zelda/ She ik 33 Marth/ Gano ndorf/Meta Knight 34 Pit/Z ero Suit Samus/I ke 35 Crhadirza di/D dy Kgone/nKi ge D ded 36 Olimar/Lu cario/Toon L ink 37 Vlai lgrWe / ii FitTa r ie/n rLRslo a ia&n um a 38 Little Mac/ Greninja/Palut ena 39 Robin /Shu lk/Bows er J r. -
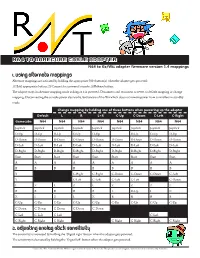
1. Using Alternate Mappings 2. Adjusting Analog Stick Sensitivity
N64 to Gamecube cable adapter N64 to Gc/Wii adapter firmware version 1.4 mappings 1. Using alternate mappings Alternate mappings are activated by holding the appropriate N64 button(s) when the adapter gets powered: 1) Hold appropriate button, 2) Connect to a powered console, 3) Release button. The adapter stays in alternate mapping mode as long as it is powered. Disconnect and reconnect to revert to default mapping or change mapping. Disconnecting the console power also works, but beware of the Wii which does not remove power from controllers in standby mode. Change mapping by holding one of these buttons when powering up the adapter Default L R L+R C-Up C-Down C-Left C-Right Gamecube N64 N64 N64 N64 N64 N64 N64 N64 Joystick Joystick Joystick Joystick Joystick Joystick Joystick Joystick Joystick D-Up D-Up D-Up D-Up D-Up D-Up D-Up D-Up D-Down D-Down D-Down D-Down D-Down D-Down D-Down D-Down D-Down D-Left D-Left D-Left D-Left D-Left D-Left D-Left D-Left D-Left D-Right D-Right D-Right D-Right D-Right D-Right D-Right D-Right D-Right Start Start Start Start Start Start Start Start Start A A A A A A A A A B B B B B B B B B X C-Right C-Right C-Down C-Down C-Down C-Left Y C-Left C-Left C-Left C-Left C-Down L Z L Z L Z Z Z L R R R R R L D-Up L Z Z L Z L Z R R R R C-Up C-Up C-Up C-Up C-Up C-Up C-Up C-Up C-Up C-Down C-Down C-Down C-Down C-Down C-Left C-Left C-Left C-Left C-Right C-Right C-Right C-Right C-Right C-Right C-Right 2. -

Instruction Manual For
Instruction Manual for v1.2 ™ For use with the Nintendo® GameCube UK/US Manual ACTION REPLAY™ FOR GAMECUBE™ INSTRUCTION MANUAL V1.2 1. INTRODUCTION Action Replay is the ultimate game enhancer for the Nintendo GameCube™ console and what’s more you can even use it with GameCube games on your Nintendo Wii™! Unleash the power of Action Replay to master even the toughest games, quickly and easily. Access all areas and skip difficult levels, unlock secret characters and vehicles, and gain unlimited lives, health, bullets, all weapons and items. These are just a small sample of the many powerful codes that are now available to you, all thanks to Action Replay. Your Action Replay comes packed with thousands of pre-loaded codes for almost every GameCube game. Action Replay incorporates a powerful import game enabler (“FreeLoader”). We recommend you always buy a game designed for your own region wherever possible due to language differences, extra features, etc. However there will be occasions when you simply can’t obtain a game, or are not prepared to wait many months for a foreign title to be released in your region. In these cases, FreeLoader is your passport to playing games from any region on your GameCube. No modifications to your console are needed. If you’re one of the many gamers that bought an imported GameCube console and you now want to play games from your own country, then FreeLoader is also ideal for this task. Now read on to find out how to take your gaming to the next level with Action Replay! 2. -

Installing the Game Boy Advance Wireless Adapter Using the Game
ENGLISH ▲! WARNING Using the Game Boy Advance Wireless Adapter PLEASE CAREFULLY READ THE HEALTH AND SAFETY PRECAUTIONS BOOKLET There are two ways to play multi-player games with the wireless adapter depending on INCLUDED WITH THE GAME BOY ADVANCE OR GAME PAKS BEFORE USING how the game is designed. Some games will include both types of multi-player THIS ACCESSORY. THIS BOOKLET CONTAINS IMPORTANT HEALTH AND SAFETY game play in one Game Pak. INFORMATION. Single Game Pak Player 1 has a Game Boy Advance Game Pak in their Game Boy Advance. Players 2, 3 and/or 4 download the game information into their Game Boy Advance systems for multi- Lock Release Buttons player games. This method needs only one Game Boy Advance Game Pak. Press inwards to release the adapter. Multiple Game Paks All players have the same Game Boy Advance Game Pak in each Game Boy Advance system. This method requires a Game Boy Advance Game Pak for each player. External Extension Connector Plug For best results, follow these guidelines: Connects to the External Extension • Do not hold, carry or shake the Game Boy Advance by the wireless adapter. Connector (EXT. on the Game Boy Advance • Remove the wireless adapter when not in use. and EXT.1 on the Game Boy Advance SP) on the top of the Game Boy Advance. • Use the wireless adapter within 3 meters (10feet) of each other. The effective range may Model-No.: AGB-015 vary depending on outside interference from radio frequency sources. • Avoid using the wireless adapter around devices that may cause radio frequency The Game Boy Advance Wireless Adapter allows up to five people to play wireless compa- interference such as cordless phones, microwave devices or wireless LANs (local area tible multi-player games without the use of cables. -

Wii Operations Manual
RVL-S-GL-USZ Wii Operations Manual NEED HELP WITH INSTALLATION, BESOIN D’AIDE POUR L’INSTALLATION, ¿NECESITAS AYUDA DE INSTALACIÓN, System Setup MAINTENANCE OR SERVICE? L’ENTRETIEN OU LA RÉPARATION? MANTENIMIENTO O SERVICIO? Nintendo Customer Service Service à la Clientèle de Nintendo Servicio al Cliente de Nintendo NINTENDO OF AMERICA INC. P.O. BOX 957, REDMOND, WA SUPPORT.NINTENDO.COM SUPPORT.NINTENDO.COM SUPPORT.NINTENDO.COM 98073-0957 U.S.A. or call 1-800-255-3700 ou composez le 1-800-255-3700 o llama al 1-800-255-3700 61914J PRINTED IN CHINA Wii Operations Manual 148Hx210W Contents To protect your health and safety, and for correct use of the Wii system, please read and follow the The official seal is your assurance Health and Safety Information 2-3 that this product is licensed or instructions in this operations manual before setup manufactured by Nintendo. System Components or use. Always look for this seal when Wii Console 4-5 buying video game systems, Wii Remote™ 6 Throughout this manual, you will see this symbol followed by WARNING or accessories, games and related Wii MotionPlus™ 7 CAUTION. These terms have different levels of meaning: products. Nunchuk™ 8 Sensor Bar 8 WARNING - Warns you about incorrect use of the Wii system that could result in serious personal injury. Wii AC Adapter 9 Wii AV Cable 9 CAUTION - Cautions you about incorrect use of the Wii system that could result in Wii Console Stand & Stand Plate 9 personal injury or damage to the Wii system, components, game discs or accessories. -

Nintendo Gamecube Teardown Guide ID: 1727 - Draft: 2021-04-30
Nintendo GameCube Teardown Guide ID: 1727 - Draft: 2021-04-30 Nintendo GameCube Teardown Written By: Thomas J This document was generated on 2021-05-02 01:29:45 PM (MST). © iFixit — CC BY-NC-SA www.iFixit.com Page 1 of 9 Nintendo GameCube Teardown Guide ID: 1727 - Draft: 2021-04-30 INTRODUCTION The Nintendo GameCube launching 2001 was the second most powerful gaming console of its time, though it didn't feature any other multimedia capabilities. It was my first stationary gaming device and I still appreciate it, because a lot of good games like Zelda: The WindWaker and the best version of Resident Evil 4 have their homes on this platform. The unit disassembled in this teardown is a PAL one. That's it. Enjoy the teardown! TOOLS: Gamebit 4.5mm (1) Phillips #00 Screwdriver (1) Spudger (1) This document was generated on 2021-05-02 01:29:45 PM (MST). © iFixit — CC BY-NC-SA www.iFixit.com Page 2 of 9 Nintendo GameCube Teardown Guide ID: 1727 - Draft: 2021-04-30 Step 1 — Nintendo GameCube Teardown Before you can even think of disassembling any Nintendo device you have to face the same problem with every console except NES and Wii: the screws of the enclosure. And the most tricky fact of these screws is their type because this is not a reasonable standard screw. Step 2 The four screws I'm talking about are a compound of a flat plate with a thicker convex layer with six notches in the brass. This screw is a 4.5 mm line head screw, commonly known as a "Gamebit" screw. -

Instruction Booklet
C/IM-DOL-USA-3 TO PURCHASE ADDITIONAL NINTENDO ACCESSORIES OR PARTS, SEE YOUR LOCAL NINTENDO RETAILER, VISIT OUR WEB SITE (USA ONLY) AT WWW.NINTENDO.COM OR CALL 1-800-255-3700. NOTE: This Nintendo product is not designed for use with any unlicensed or unauthorized accessories. INSTRUCTION BOOKLET NEED HELP WITH INSTALLATION, MAINTENANCE OR SERVICE? NINTENDO CUSTOMER SERVICE www.nintendo.com (in Canada, www.nintendo.ca) or call 1-800-255-3700, MON.-SUN., 6:00 a.m. to 7:00 p.m, Pacific Time (Times subject to change) TTY Consumer Service: 800-422-4281 NEED HELP PLAYING A GAME? You can visit our web site at www.nintendo.com (in Canada, www.nintendo.ca) for game play information. For automated game play tips and news, call Nintendo's Power Line at: 1-425-885-7529. This may be a long distance call, so please ask permission from whomever pays the phone bill. Rather talk with a game counselor? 1-800-521-0900 Available in U.S. and Canada - $1.50 Per Minute (In U.S. Funds) Please have Visa or MasterCard Ready MON. - SUN., 6:00 a.m. to 7:00 p.m.; Pacific Time Callers under 18 need to obtain parental permission to call. Prices subject to change. TTY Game Play Assistance: 425-883-9714 Nintendo of America Inc. P.O. Box 957, Redmond, WA 98073-0957 U.S.A. PN 45979E PRINTED IN CHINA WARNING: PLEASE CAREFULLY READ THE SEPARATE HEALTH AND SAFETY PRECAUTIONS BOOKLET INCLUDED WITH THIS PRODUCT BEFORE USING YOUR NINTENDO ® HARDWARE SYSTEM, GAME DISC IMPORTANT SAFETY INFORMATION: OR ACCESSORY. -

Safety Information: Gamecube/Wii Wireless Controller Package Contents
GameCube/Wii Wireless Controller • Do not place or store the GameCube/Wii Wireless Controller in a Product features humid area and do not expose it to water or rain. Controller • Read all instructions before operating the GameCube/Wii Wireless Controller. Use the GameCube/Wii Wireless Controller only as Warnings: instructed. Failure to follow these instructions may void the warranty. • Some medical studies have suggested that long periods of repetitive motion may be linked to certain types of physical discomfort or Battery warnings: injuries. You should take frequent breaks during game play. If you Incorrect use of batteries may result in battery fl uid leakage, Y MACRO feel aching, numbness, or tingling in your arms, wrists, or hands, overheating, or explosion. There is a risk of fi re if batteries START A X consult a qualifi ed health professional. are replaced by an incorrect type. Released battery fl uid is B • Do not use the GameCube/Wii Wireless Controller if you have corrosive and may be toxic. It can cause skin and eye burns POWER respiratory, heart, or other physical ailments that limit your and is harmful if swallowed. To reduce the risk of injury: physical activity. If you have any doubts, consult a qualifi ed health C professional. • Keep batteries out of reach of children. • The GameCube/Wii Wireless Controller is not intended for use by • Do not heat, open, puncture, or dispose of batteries in small children. It may contain small pieces that may pose a choking fi re. hazard. • Only use AAA alkaline batteries. • The GameCube/Wii Wireless Controller can emit radio waves that • Do not mix new and old batteries.