Forensics of Bittorrent
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

List of TCP and UDP Port Numbers from Wikipedia, the Free Encyclopedia
List of TCP and UDP port numbers From Wikipedia, the free encyclopedia This is a list of Internet socket port numbers used by protocols of the transport layer of the Internet Protocol Suite for the establishment of host-to-host connectivity. Originally, port numbers were used by the Network Control Program (NCP) in the ARPANET for which two ports were required for half- duplex transmission. Later, the Transmission Control Protocol (TCP) and the User Datagram Protocol (UDP) needed only one port for full- duplex, bidirectional traffic. The even-numbered ports were not used, and this resulted in some even numbers in the well-known port number /etc/services, a service name range being unassigned. The Stream Control Transmission Protocol database file on Unix-like operating (SCTP) and the Datagram Congestion Control Protocol (DCCP) also systems.[1][2][3][4] use port numbers. They usually use port numbers that match the services of the corresponding TCP or UDP implementation, if they exist. The Internet Assigned Numbers Authority (IANA) is responsible for maintaining the official assignments of port numbers for specific uses.[5] However, many unofficial uses of both well-known and registered port numbers occur in practice. Contents 1 Table legend 2 Well-known ports 3 Registered ports 4 Dynamic, private or ephemeral ports 5 See also 6 References 7 External links Table legend Official: Port is registered with IANA for the application.[5] Unofficial: Port is not registered with IANA for the application. Multiple use: Multiple applications are known to use this port. Well-known ports The port numbers in the range from 0 to 1023 are the well-known ports or system ports.[6] They are used by system processes that provide widely used types of network services. -

List of TCP and UDP Port Numbers 1 List of TCP and UDP Port Numbers
List of TCP and UDP port numbers 1 List of TCP and UDP port numbers This is a list of Internet socket port numbers used by protocols of the Transport Layer of the Internet Protocol Suite for the establishment of host-to-host communications. Originally, these ports number were used by the Transmission Control Protocol (TCP) and the User Datagram Protocol (UDP), but are also used for the Stream Control Transmission Protocol (SCTP), and the Datagram Congestion Control Protocol (DCCP). SCTP and DCCP services usually use a port number that matches the service of the corresponding TCP or UDP implementation if they exist. The Internet Assigned Numbers Authority (IANA) is responsible for maintaining the official assignments of port numbers for specific uses.[1] However, many unofficial uses of both well-known and registered port numbers occur in practice. Table legend Use Description Color Official Port is registered with IANA for the application white Unofficial Port is not registered with IANA for the application blue Multiple use Multiple applications are known to use this port. yellow Well-known ports The port numbers in the range from 0 to 1023 are the well-known ports. They are used by system processes that provide widely used types of network services. On Unix-like operating systems, a process must execute with superuser privileges to be able to bind a network socket to an IP address using one of the well-known ports. Port TCP UDP Description Status 0 UDP Reserved Official 1 TCP UDP TCP Port Service Multiplexer (TCPMUX) Official [2] [3] -

Design and Implementation of a Bittorrent Tracker Overlay for Swarm Unification
ICNS 2011 : The Seventh International Conference on Networking and Services Design and Implementation of a BitTorrent Tracker Overlay for Swarm Unification Calin-Andrei˘ Burloiu, Razvan˘ Deaconescu, Nicolae T, apus˘ , Automatic Control and Computers Faculty Politehnica University of Bucharest Emails: [email protected],frazvan.deaconescu,[email protected] Abstract—The deployment of the BitTorrent protocol in the slots, geolocation and general behavior (aggressiveness, entry– early 2000s has meant a significant shift in Peer-to-Peer tech- exit time interval, churn rate). nologies. Currently the most heavily used protocol in the Internet The context in which a BitTorrent content distribution core, the BitTorrent protocol has sparked numerous implementa- tions, commercial entities and research interest. In this paper, we session takes place is defined by a BitTorrent swarm which is present a mechanism that allows integration of disparate swarms the peer ensemble that participate in sharing a given file. It is that share the same content. We’ve designed and implemented a characterized by the number of peers, number of seeders, file novel inter-tracker protocol, dubbed TSUP, that allows trackers size, peers’ upload/download speed. swarm, one that allows to share peer information, distribute it to clients and enable rapid content distribution to peers, is generally defined by a swarm unification. The protocol forms the basis for putting together small swarms into large, healthy ones with reduced good proportion of seeders and stable peers. We define stable performance overhead. Our work achieves its goals to increase peers as peers that are part of the swarm for prolonged periods the number of peers in a swarm and proves that the TSUP of time. -

Well-Known Ports
20 & 21: File Transfer Protocol (FTP) 22: Secure Shell (SSH) 23: Telnet remote login service 25: Simple Mail Transfer Protocol (SMTP) 53: Domain Name System (DNS) service 80: Hypertext Transfer Protocol (HTTP) used in the World Wide Web 110: Post Office Protocol (POP3) 119: Network News Transfer Protocol (NNTP) 143: Internet Message Access Protocol (IMAP) 161: Simple Network Management Protocol (SNMP) 443: HTTP Secure (HTTPS) Well-known ports The port numbers in the range from 0 to 1023 are the well-known ports. They are used by system processes that provide widely used types of network services. On Unix-like operating systems, a process must execute with superuser privileges to be able to bind a network socket to an IP address using one of the well-known ports. Port TCP UDP Description Status 0 UDP Reserved Official 1 TCP UDP TCP Port Service Multiplexer (TCPMUX) Official 2 TCP UDP CompressNET[2] Management Utility[3] Official 3 TCP UDP CompressNET[2] Compression Process[4] Official 4 TCP UDP Unassigned Official 5 TCP UDP Remote Job Entry Official Port TCP UDP Description Status 7 TCP UDP Echo Protocol Official 8 TCP UDP Unassigned Official 9 TCP UDP Discard Protocol Official 10 TCP UDP Unassigned Official 11 TCP UDP Active Users (systat service)[5][6] Official 12 TCP UDP Unassigned Official 13 TCP UDP Daytime Protocol (RFC 867) Official 14 TCP UDP Unassigned Official 15 TCP UDP Previously netstat service[5] Unofficial 16 TCP UDP Unassigned Official 17 TCP UDP Quote of the Day Official 18 TCP UDP Message Send Protocol Official 19 TCP UDP Character Generator Protocol (CHARGEN) Official Port TCP UDP Description Status 20 TCP FTP data transfer Official 21 TCP FTP control (command) Official Secure Shell (SSH)—used for secure logins, file transfers (scp, sftp) 22 TCP Official and port forwarding 23 TCP Telnet protocol—unencrypted text communications Official 24 TCP UDP Priv-mail : any private mail system. -

Cloud Storage NAS Series
Cloud Storage NAS Series Version 5.1 Edition 2 Quick Start Guide User’s Guide Default Login Details Web Address nas326 nas542 www.zyxel.comnas540 nas520 User Name admin Password 1234 Copyright © 2016 ZyXEL Communications Corporation Related Documentation and Online Support Related Documentation and Online Support IMPORTANT! READ CAREFULLY BEFORE USE. KEEP THIS GUIDE FOR FUTURE REFERENCE. Screenshots and graphics in this book may differ slightly from your product due to differences in your product firmware or your computer operating system. Every effort has been made to ensure that the information in this manual is accurate. Related Documentation • Quick Start Guide The Quick Start Guide shows how to connect the NAS and get up and running right away. • Web Configurator Online Help The embedded Web Help contains descriptions of individual screens and supplementary information. Online Support Information Visit our product support website at http://www.zyxel.com/support/support_landing.shtml and choose from these topics: • ZyXEL Support Center - Acquire firmware, software, FAQ, product application or other support files for ZyXEL devices. • Downloads - Acquire firmware, software, driver or other support files for ZyXEL devices. • Knowledge Base - Find articles related to product applications, FAQ, and user experience. • Warranty I nformation - ZyXEL offers warranty to the original end user (purchaser) that the product is free from any material or workmanship defects for a specific period (the Warranty Period) from the date of purchase. The -

Du « Piratage » À La Communauté
1 L’émergence, la marchandisation et la chute d’un réseau hellénophone de peer-to-peer Nikos Smyrnaios et Ioanna Vovou Il ne se passe pas de semaine sans que le conflit qui oppose depuis plusieurs années les principaux acteurs des industries culturelles, ainsi que les pouvoirs politiques et économiques qui les soutiennent, aux communautés d’internautes qui partagent des contenus protégés par le droit d’auteur ne fasse la Une de l’actualité. Ce conflit, qui se déroule à une échelle mondiale et dont la nature se révèle être non seulement socioéconomique mais également politique, est porteur d’enjeux déterminants : il démontre l’importance que revêt le contrôle de la propriété intellectuelle dans le contexte de ce que d’aucuns appellent le capitalisme cognitif1, au point qu’elle est assimilée au « pétrole du XXIe siècle2 ». Pour ce qui est plus spécifiquement des industries culturelles, il est clair que la période actuelle est décisive pour la future évolution des canaux de distribution numériques3. D’un côté, les représentants des industries culturelles et médiatiques s’efforcent de reprendre le contrôle de ces canaux et, de l’autre, une multitude de communautés d’internautes tente de pérenniser les pratiques de partage et de libre diffusion des mots, des images et des musiques, désormais socialement fortement ancrées. En effet, à travers des initiatives d’amateur, ont progressivement émergé des plateformes qui font office de distributeurs de contenu auprès des millions d’internautes dans le monde4. Ces acteurs se retrouvent pour beaucoup dans un espace d’entre deux, à la limite de la légalité et aux marges de la sphère marchande du web, tout en touchant un nombre d’internautes souvent supérieur à certaines plateformes de distribution légales. -

Institute for Information Management and Communication, Kyoto University Table of Contents for the 2016 Information Environment Manual for Students 1
Institute for Information Management and Communication, Kyoto University Table of Contents for the 2016 Information Environment Manual for Students 1. Introduction to the Information Environment of Kyoto University ……………………… 2 1.1. Notations …………………………………………………………………………………………………………………………………………………………… 2 1.2. Information Related Services Provided by Kyoto University …………………………………………………………………………………………………… 3 1.3. Information Related Services Websites …………………………………………………………………………………………………………………………… 3 2. Acquiring and Using University Authentication IDs (ECS-IDs) ……………………………… 4 2.1. About ECS-IDs ……………………………………………………………………………………………………………………………………………………… 4 2.2. Procedure for Acquiring an ECS-ID ……………………………………………………………………………………………………………………………… 4 2.3. Activating ECS-ID …………………………………………………………………………………………………………………………………………………… 4 2.4. IT Services using ECS-ID …………………………………………………………………………………………………………………………………………… 5 2.5. Managing your ECS-ID ……………………………………………………………………………………………………………………………………………… 5 2.6. Remark to use ECS-ID ……………………………………………………………………………………………………………………………………………… 5 3. Safe and Appropriate Use of the Information Systems ……………………………………… 6 3.1. Kyoto University's Network and Security ………………………………………………………………………………………………………………………… 6 3.2. Appropriate Management of ECS-IDs and Passwords ………………………………………………………………………………………………………… 7 3.3. Changing Your Password …………………………………………………………………………………………………………………………………………… 7 3.4. Points to Keep in Mind When Using the Network ……………………………………………………………………………………………………………… 8 3.5. Information Security e-Learning -
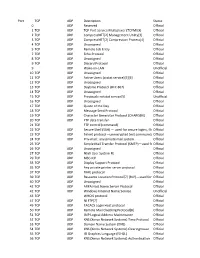
Official 2 TCP UDP Compr
Port TCP UDP Description Status 0 UDP Reserved Official 1 TCP UDP TCP Port Service Multiplexer (TCPMUX) Official 2 TCP UDP CompressNET[2] Management Utility[3] Official 3 TCP UDP CompressNET[2] Compression Process[4] Official 4 TCP UDP Unassigned Official 5 TCP UDP Remote Job Entry Official 7 TCP UDP Echo Protocol Official 8 TCP UDP Unassigned Official 9 TCP UDP Discard Protocol Official 9 UDP Wake-on-LAN Unofficial 10 TCP UDP Unassigned Official 11 TCP UDP Active Users (systat service)[5][6] Official 12 TCP UDP Unassigned Official 13 TCP UDP Daytime Protocol (RFC 867) Official 14 TCP UDP Unassigned Official 15 TCP UDP Previously netstat service[5] Unofficial 16 TCP UDP Unassigned Official 17 TCP UDP Quote of the Day Official 18 TCP UDP Message Send Protocol Official 19 TCP UDP Character Generator Protocol (CHARGEN) Official 20 TCP UDP FTP data transfer Official 21 TCP FTP control (command) Official 22 TCP UDP Secure Shell (SSH) — used for secure logins, file Officialtransfers (scp, sftp) and port forwarding 23 TCP UDP Telnet protocol—unencrypted text communicationsOfficial 24 TCP UDP Priv-mail : any private mail system. Official 25 TCP Simple Mail Transfer Protocol (SMTP)—used forOfficial e-mail routing between mail servers 26 TCP UDP Unassigned Official 27 TCP UDP NSW User System FE Official 29 TCP UDP MSG ICP Official 33 TCP UDP Display Support Protocol Official 35 TCP UDP Any private printer server protocol Official 37 TCP UDP TIME protocol Official 39 TCP UDP Resource Location Protocol*7+ (RLP)—used for determiningOfficial the location -

List of TCP and UDP Port Numbers - Wikipedia, the Free Encyclopedia List of TCP and UDP Port Numbers from Wikipedia, the Free Encyclopedia
8/21/2014 List of TCP and UDP port numbers - Wikipedia, the free encyclopedia List of TCP and UDP port numbers From Wikipedia, the free encyclopedia This is a list of Internet socket port numbers used by protocols of the Transport Layer of the Internet Protocol Suite for the establishment of host-to-host connectivity. Originally, port numbers were used by the Network Control Program (NCP) which needed two ports for half duplex transmission. Later, the Transmission Control Protocol (TCP) and the User Datagram Protocol (UDP) needed only one port for bidirectional traffic. The even numbered ports were not used, and this resulted in some even numbers in the well-known port number range being unassigned. The Stream Control Transmission Protocol (SCTP) and the Datagram Congestion Control Protocol (DCCP) also use port numbers. They usually use port numbers that match the services of the corresponding TCP or UDP implementation, if they exist. The Internet Assigned Numbers Authority (IANA) is responsible for maintaining the official assignments of port numbers for specific uses.[1] However, many unofficial uses of both well-known and registered port numbers occur in practice. Contents 1 Table legend 2 Well-known ports 3 Registered ports 4 Dynamic, private or ephemeral ports 5 See also 6 References 7 External links Table legend Use Description Color Official Port is registered with IANA for the application[1] White Unofficial Port is not registered with IANA for the application Blue Multiple use Multiple applications are known to use this port. Yellow Well-known ports The port numbers in the range from 0 to 1023 are the well-known ports or system ports.[2] They are used by system processes that provide widely used types of network services. -

NAS540 User's Guide
NAS540 Cloud Storage Version 5.00 Edition 1 Quick Start Guide User’s Guide Default Login Details Web Address nas540 User Name admin Passwordwww.zyxel.com 1234 Copyright © 2014 ZyXEL Communications Corporation IMPORTANT! READ CAREFULLY BEFORE USE. KEEP THIS GUIDE FOR FUTURE REFERENCE. Screenshots and graphics in this book may differ slightly from your product due to differences in your product firmware or your computer operating system. Every effort has been made to ensure that the information in this manual is accurate. Related Documentation •Quick Start Guide The Quick Start Guide shows how to connect the NAS and get up and running right away. • Web Configurator Online Help The embedded Web Help contains descriptions of individual screens and supplementary information. 2 NAS540 User’s Guide Contents Overview Contents Overview User’s Guide ........................................................................................................................... 13 Getting to Know Your NAS .........................................................................................................15 NAS Starter Utility ......................................................................................................................19 zCloud ........................................................................................................................................27 Web Configurator Basics ...........................................................................................................29 Tutorials .....................................................................................................................................91 -

Dissecting Darknets: Measurement and Performance Analysis
Dissecting Darknets: Measurement and Performance Analysis Xiaowen Chu, Xiaowei Chen Hong Kong Baptist University Adele L. Jia, Johan A. Pouwelse, and Dick H.J. Epema Delft University of Technology BitTorrent (BT) plays an important role in Internet content distribution. Because public BTs suffer from the free-rider problem, Darknets are becoming increasingly popular, which use Sharing Ratio Enforcement to increase their efficiency. We crawled and traced 17 Darknets from September 2009 to Feb 2011, and obtained data sets about over 5 million torrents. We conducted a broad range of measurements, including traffic, sites, torrents, and users activities. We found that some of the features of Darknets are noticeably different from public BTs. The results of our study reflect both macroscopic and microscopic aspects of the overall ecosystem of BitTorrent Darknets. 1. INTRODUCTION BitTorrent (BT) is currently the dominant Peer-to-Peer (P2P) content sharing protocol [Zhang et al. 2011]. It changes the way of content distribution from traditional Client/Server mode to P2P mode, which greatly decreases the burden on file servers. The tracker (together with its communities), which is one of the core components of the BT protocol, plays an important role in the course of content distribution by periodically providing updated peer lists to connected peers. In practice, a peer accesses website-based BT communities to obtain torrents and then to join the content distribution swarms. The BT communities can be divided into two categories: public (a.k.a. public BT) and private (a.k.a. Darknet, private tracker) communities [Zhang et al. 2010]. There are numerous public BT communities, such as ThePirateBay, Mininova, and ISOHunt, which anyone can access. -

AXMEDIS Copyright Notice
DE3.1.2.2.10 – Specification of AXEPTool and AXMEDIA Tools AXMEDIS Automating Production of Cross Media Content for Multi-channel Distribution www.AXMEDIS.org DE3.1.2.2.10 Specification of AXEPTool and AXMEDIA Tools Version: 1.5 Date: 31-07-2006 Responsible: DSI (revised and approved by coordinator) Project Number: IST-2-511299 Project Title: AXMEDIS Deliverable Type: report Visible to User Groups: yes Visible to Affiliated: yes Visible to the Public: yes Deliverable Number: DE3.1.2.2.10 Contractual Date of Delivery: M18 (in delay) Actual Date of Delivery: 31/07/2006 Title of Deliverable: Document Work-Package contributing to the Deliverable: WP3.1 Task contributing to the Deliverable: WP3, WP2 Nature of the Deliverable: report Author(s): DSI, EXITECH Abstract: this part includes the specification of components, formats, databases and protocol related to the AXMEDIS Framework area of P2P including AXMEDIS P2P tools, AXEPTool, AXMEDIA, AXMEDIS P2P Query Service Servers, etc. Keyword List: AXMEDIS P2P network, AXEPTool, AXMEDIA, bittorrent AXMEDIS Project 1 DE3.1.2.2.10 – Specification of AXEPTool and AXMEDIA Tools AXMEDIS Copyright Notice The following terms (including future possible amendments) set out the rights and obligations licensee will be requested to accept on entering into possession of any official AXMEDIS document either by downloading it from the web site or by any other means. Any relevant AXMEDIS document includes this license. PLEASE READ THE FOLLOWING TERMS CAREFULLY AS THEY HAVE TO BE ACCEPTED PRIOR TO READING/USE OF THE DOCUMENT. 1. DEFINITIONS i. "Acceptance Date" is the date on which these terms and conditions for entering into possession of the document have been accepted.