D13.2 "MILS: Business, Legal and Social Acceptance"
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

LG G3 User Guide
Available applications and services are subject to change at any time. Table of Contents Get Started 1 Your Phone at a Glance 1 Set Up Your Phone 1 Activate Your Phone 4 Complete the Setup Screens 5 Make Your First Call 6 Set Up Your Voicemail 6 Sprint Account Information and Help 7 Sprint Account Passwords 7 Manage Your Account 7 Sprint Support Services 8 Phone Basics 9 Your Phone's Layout 9 Turn Your Phone On and Off 11 Screen On/Off 11 Lock and Unlock Your Phone 12 Unlock Your Screen Using the Knock Code Feature 13 Guest Mode 14 Set Up Guest Mode 14 Use Guest Mode 15 Hardware Key Control Mode 15 Battery and Charger 15 Extend Your Battery Life 17 Phone Function Keys 17 Recent Apps Key 18 Work with Menus 18 Notifications Panel 19 Home Key 20 Back Key 21 Touchscreen Navigation 21 Your Home Screen 22 Home Screen 22 Extended Home Screen 23 i Use the Applications Key 23 Applications: How to View, Open and Switch 23 Applications 25 Customize Your Home Screen 27 Add and Remove Widgets on the Home Screen 28 Change the Phone's Wallpaper 29 Customize Applications Icons on the Home Screen 30 Access Recently-Used Applications 31 Home Screen Clean View 31 Quick Access 32 Change the Screen Orientation 32 Status Bar 32 Enter Text With the On-screen Keyboard 35 Tips for Editing Text 37 Search Your Phone and the Web 42 Phone and Web Search Using Text Entry 42 Phone and Web Search Using Voice Command 44 Using Clip Tray 44 Text Link 44 Phone Calls 46 HD™ Voice 46 Make Phone Calls 46 Call Using the Phone Dialer 46 Dialing Options 47 Missed Call Notification -

2014 BT Compatibility List 20141030
Item Brand Name Model 1 Acer Acer beTouch E210 2 Acer acer E400 3 Acer acer P400 4 Acer DX650 5 Acer E200 6 Acer Liquid E 7 Acer Liquid Mini (E310) 8 Acer M900 9 Acer S110 10 Acer Smart handheld 11 Acer Smart handheld 12 Acer Smart handheld E100 13 Acer Smart handheld E101 14 Adec & Partner AG AG vegas 15 Alcatel Alcatel OneTouch Fierce 2 16 Alcatel MISS SIXTY MSX10 17 Alcatel OT-800/ OT-800A 18 Alcatel OT-802/ OT-802A 19 Alcatel OT-806/ OT-806A/ OT-806D/ OT-807/ OT-807A/ OT-807D 20 Alcatel OT-808/ OT-808A 21 Alcatel OT-880/ OT-880A 22 Alcatel OT-980/ OT-980A 23 Altek Altek A14 24 Amazon Amazon Fire Phone 25 Amgoo Telecom Co LTD AM83 26 Apple Apple iPhone 4S 27 Apple Apple iPhone 5 28 Apple Apple iPhone 6 29 Apple Apple iPhone 6 Plus 30 Apple iPhone 2G 31 Apple iPhone 3G 32 Apple iPhone 3Gs 33 Apple iPhone 4 34 Apple iPhone 5C 35 Apple iPHone 5S 36 Aramasmobile.com ZX021 37 Ascom Sweden AB 3749 38 Asustek 1000846 39 Asustek A10 40 Asustek G60 41 Asustek Galaxy3_L and Galaxy3_S 42 Asustek Garmin-ASUS M10E 43 Asustek P320 44 Asustek P565c 45 BlackBerry BlackBerry Passport 46 BlackBerry BlackBerry Q10 47 Broadcom Corporation BTL-A 48 Casio Hitachi C721 49 Cellnet 7 Inc. DG-805 Cellon Communications 50 C2052, Technology(Shenzhen) Co., Ltd. Cellon Communications 51 C2053, Technology(Shenzhen) Co., Ltd. Cellon Communications 52 C3031 Technology(Shenzhen) Co., Ltd. Cellon Communications 53 C5030, Technology(Shenzhen) Co., Ltd. -
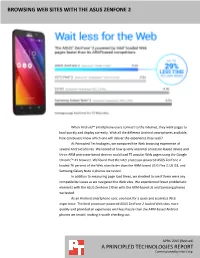
Browsing Web Sites with the Asus Zenfone 2
BROWSING WEB SITES WITH THE ASUS ZENFONE 2 When Android™ smartphone users connect to the Internet, they want pages to load quickly and display correctly. With all the different Android smartphones available, how can buyers know which one will deliver the experience they seek? At Principled Technologies, we compared the Web browsing experience of several Android phones. We looked at how quickly one Intel processor-based device and three ARM processor-based devices could load 75 popular Web pages using the Google Chrome™ 41 browser. We found that the Intel processor-powered ASUS ZenFone 2 loaded 76 percent of the Web sites faster than the ARM-based LG G Flex 2, LG G3, and Samsung Galaxy Note 4 phones we tested. In addition to measuring page load times, we checked to see if there were any compatibility issues as we navigated the Web sites. We experienced fewer problematic elements with the ASUS ZenFone 2 than with the ARM-based LG and Samsung phones we tested. As an Android smartphone user, you look for a quick and seamless Web experience. The Intel processor-powered ASUS ZenFone 2 loaded Web sites more quickly and provided an experience with less hassle than the ARM-based Android phones we tested, making it worth checking out. APRIL 2015 (Revised) A PRINCIPLED TECHNOLOGIES REPORT Commissioned by Intel Corp. A BETTER ANDROID WEB EXPERIENCE WITH ASUS & INTEL Android smartphones are a great way to view Web sites, though they don’t all behave the same way. A mobile device that does a speedy job of loading pages while displaying elements correctly can really improve the user experience. -

Case 5:18-Cv-06739-VKD Document 27 Filed 07/02/18 Page 1 of 11
Case 5:18-cv-06739-VKD Document 27 Filed 07/02/18 Page 1 of 11 IN THE UNITED STATES DISTRICT COURT FOR THE NORTHERN DISTRICT OF TEXAS DALLAS DIVISION § UNILOC USA, INC. and § UNILOC LUXEMBOURG, S.A., § Civil Action No. 3:18-cv-00560-DCG § Plaintiffs, § § v. § PATENT CASE § LG ELECTRONICS U.S.A., INC., § LG ELECTRONICS MOBILECOMM § U.S.A. INC. and § LG ELECTRONICS, INC., § § Defendant. § JURY TRIAL DEMANDED § FIRST AMENDED COMPLAINT FOR PATENT INFRINGEMENT Plaintiffs, Uniloc USA, Inc. (“Uniloc USA”) and Uniloc Luxembourg, S.A. (“Uniloc Luxembourg”) (together, “Uniloc”), for their First Amended Complaint against defendant, LG Electronics U.S.A. (“LGE”), Inc., LG Electronics Mobilecomm U.S.A., Inc., and LG Electronics, Inc., (“LG Korea”) (together “LG”), allege as follows:1 THE PARTIES 1. Uniloc USA is a Texas corporation having a principal place of business at Legacy Town Center I, Suite 380, 7160 Dallas Parkway, Plano Texas 75024. Uniloc USA also maintains a place of business at 102 N. College, Suite 603, Tyler, Texas 75702. 1 An amended complaint supersedes the original complaint and renders it of no legal effect, King v. Dogan, 31 F.3d 344. 346 (5th Cir. 1994), rendering a motion to dismiss the original complaint moot. See, e.g., Mangum v. United Parcel Services, No. 3:09-cv-0385, 2009 WL 2700217 (N.D. Tex. Aug. 26, 2009). 2988606.v1 Case 5:18-cv-06739-VKD Document 27 Filed 07/02/18 Page 2 of 11 2. Uniloc Luxembourg is a Luxembourg public limited liability company having a principal place of business at 15, Rue Edward Steichen, 4th Floor, L-2540, Luxembourg (R.C.S. -

Electronic 3D Models Catalogue (On July 26, 2019)
Electronic 3D models Catalogue (on July 26, 2019) Acer 001 Acer Iconia Tab A510 002 Acer Liquid Z5 003 Acer Liquid S2 Red 004 Acer Liquid S2 Black 005 Acer Iconia Tab A3 White 006 Acer Iconia Tab A1-810 White 007 Acer Iconia W4 008 Acer Liquid E3 Black 009 Acer Liquid E3 Silver 010 Acer Iconia B1-720 Iron Gray 011 Acer Iconia B1-720 Red 012 Acer Iconia B1-720 White 013 Acer Liquid Z3 Rock Black 014 Acer Liquid Z3 Classic White 015 Acer Iconia One 7 B1-730 Black 016 Acer Iconia One 7 B1-730 Red 017 Acer Iconia One 7 B1-730 Yellow 018 Acer Iconia One 7 B1-730 Green 019 Acer Iconia One 7 B1-730 Pink 020 Acer Iconia One 7 B1-730 Orange 021 Acer Iconia One 7 B1-730 Purple 022 Acer Iconia One 7 B1-730 White 023 Acer Iconia One 7 B1-730 Blue 024 Acer Iconia One 7 B1-730 Cyan 025 Acer Aspire Switch 10 026 Acer Iconia Tab A1-810 Red 027 Acer Iconia Tab A1-810 Black 028 Acer Iconia A1-830 White 029 Acer Liquid Z4 White 030 Acer Liquid Z4 Black 031 Acer Liquid Z200 Essential White 032 Acer Liquid Z200 Titanium Black 033 Acer Liquid Z200 Fragrant Pink 034 Acer Liquid Z200 Sky Blue 035 Acer Liquid Z200 Sunshine Yellow 036 Acer Liquid Jade Black 037 Acer Liquid Jade Green 038 Acer Liquid Jade White 039 Acer Liquid Z500 Sandy Silver 040 Acer Liquid Z500 Aquamarine Green 041 Acer Liquid Z500 Titanium Black 042 Acer Iconia Tab 7 (A1-713) 043 Acer Iconia Tab 7 (A1-713HD) 044 Acer Liquid E700 Burgundy Red 045 Acer Liquid E700 Titan Black 046 Acer Iconia Tab 8 047 Acer Liquid X1 Graphite Black 048 Acer Liquid X1 Wine Red 049 Acer Iconia Tab 8 W 050 Acer -

Lg G5 “Friends” Companion Devices Launch in Us
www.LG.com LG G5 “FRIENDS” COMPANION DEVICES LAUNCH IN US Available Now, LG CAM Plus, LG 360 CAM, LG 360 VR, LG TONE via Carriers, Retailers and on LG.COM ENGLEWOOD CLIFFS, N.J., May 24 2016 — Beginning today, LG Electronics’ (LG) customers in the US can get their hands on the highly anticipated LG G5 “Friends” companion devices, including the LG CAM Plus, LG 360 CAM, LG 360 VR and LG TONE Platinum™ on LG.com. The recently launched LG G5 smartphone showcases a new modular design that lets owners easily add LG Friends to transform the G5 into a DSLR-inspired camera, mobile virtual reality viewer and even a 360 video camera. The LG Friends are available now via major US carriers and at retail locations as well as the expanded LG online store – a destination to find great products that help customers get the most out of their favorite LG smartphones. LG.com will also serve as a way to order LG G5 batteries and new charging cradles in the coming weeks – which can be used to charge the G5. In addition, the online store offers batteries and charging cradles for beloved products such as the LG G3, LG G4, and LG V10*. For a limited time only, the store will be rewarding loyal customers with several promotions to celebrate some of LG’s most successful products and innovations. Consumers can take advantage of deep discounts including up to 70 percent off MSRP for, G4 and V10 battery and charger bundles starting for as low as $20.** “The LG ‘Friends’ make the G5 so much more than any other phone on the market. -

Design & Implementation of Classification & Clustering
Summer Internship Report On Design & Implementation of Classification & Clustering Algorithm for Mobile Phones At IDRBT, Hyderabad 6th May 2014 to 5th July 2014 Submitted By: Ratnesh Chandak B. Tech- CSE (2nd Year) Roll Number: CS12B1030 Indian Institute of Technology, Hyderabad Guided By: Dr. V.N. Sastry Designation: Professor IDRBT, Hyderabad Date of Submission: 4th July 2014 1 Abstract This project is broadly divided in two parts, in the first part we would be finding intersection of common objects from different sets taking an example of finding common colored balls from different sets of containers. In second part we would describe K-Means Clustering Algorithm to find similar numerical sets and we will experimentally find optimal value of “K” in clustering algorithm by using Elbow Method. Both the these are explained with an example of mobiles phones and done implementation in java. 2 Certificate Certified that this is a bonafide record of summer internship project work entitled Design & Implementation of Classification & Clustering Algorithm for Mobile Phones Done By Ratnesh Chandak B. Tech - CSE (2nd Year) Indian Institute of Technology, Hyderabad at IDRBT, Hyderabad during 6th May to 5th July 2014 Prof. V N Sastry (Project Guide) IDRBT, Hyderabad 3 Acknowledgement We have completed this project as summer internship in IDRBT (Institute for Development and Research in Banking Technology), Hyderabad under the guidance of Dr. V.N. Sastry. We would like to thank all our friends and our mentor for great support in completing this project. -

Udynamo Compatibility List
uDynamo Compatibility List Reader Manuf. Device Name Alt. Model Info Model Info OS OS Version Carrier Date Added Date Tested Type iDynamo 5 Apple iPad Air 2 Lightning N/A iOS N/A N/A Tablet iDynamo 5 Apple iPad Air* Lightning N/A iOS N/A N/A Tablet iDynamo 5 Apple iPad with Retina Display* Lightning N/A iOS N/A N/A Tablet iDynamo 5 Apple iPad mini 3 Lightning N/A iOS N/A N/A Tablet iDynamo 5 Apple iPad mini 2 Lightning N/A iOS N/A N/A Tablet iDynamo 5 Apple iPad mini* Lightning N/A iOS N/A N/A Tablet iDynamo 5 Apple iPhone 5c* Lightning N/A iOS N/A N/A Phone iDynamo 5 Apple iPhone 5s* Lightning N/A iOS N/A N/A Phone iDynamo 5 Apple iPhone 5* Lightning N/A iOS N/A N/A Phone iDynamo 5 Apple iPod touch (5th* generation) Lightning N/A iOS N/A N/A iPod iDynamo 5 Apple iPhone 6* Lightning N/A iOS N/A N/A Phone iDynamo 5 Apple iPhone 6 Plus* Lightning N/A iOS N/A N/A Phone iDynamo Apple iPad (3rd generation) 30 PIN N/A iOS N/A N/A Tablet iDynamo Apple iPad 2 30 PIN N/A iOS N/A N/A Tablet iDynamo Apple iPad 30 PIN N/A iOS N/A N/A Tablet iDynamo Apple iPhone 4s 30 PIN N/A iOS N/A N/A Phone iDynamo Apple iPhone 4 30 PIN N/A iOS N/A N/A Phone iDynamo Apple iPhone 3GS 30 PIN N/A iOS N/A N/A Phone iDynamo Apple iPod touch (3rd and 4th generation) 30 PIN N/A iOS N/A N/A iPod uDynamo Acer liquid MT liquid MT Android 2.3.6 101.18 1/24/14 1/24/14 uDynamo Alcatel Alcatel OneTouch Fierce 7024W Android 4.2.2 101.18 3/6/14 3/6/14 uDynamo ALCATEL Megane ALCATEL ONE TOUCH 5020T Android 4.1.2 101.18 8/10/15 8/10/15 uDynamo ALCATEL ALCATEL ONE TOUCH IDOL X ALCATEL -

California Proposition 65
AT&T Wireless Handsets, Tablets, Wearables and other Connected Wireless Products California Proposition 65 If you received a Proposition 65 warning on your receipt, packing slip or email confirmation document, please see the following list of products to determine which product you purchased is subject to the warning. Manufacturer SKU Marketing Name and/or model # ASUS 6588A ASUS PadFone X mini Black ASUS 6593A ASUS PadFone X mini Black ASUS 6594A ASUS PadFone X mini Black ASUS R588A ASUS PadFone X mini Black - certified like new ASUS R593A ASUS PadFone X mini Black - certified like new ASUS R594A ASUS PadFone X mini Black - certified like new ASUS S588A ASUS PadFone X mini Black - warranty replacement ASUS S593A ASUS PadFone X mini Black - warranty replacement ASUS S594A ASUS PadFone X mini Black - warranty replacement ASUS 6768A ASUS ZenFone 2E White ASUS 6769A ASUS ZenFone 2E White ASUS 6770A ASUS ZenFone 2E White ASUS R768A ASUS ZenFone 2E White - certified like new ASUS R769A ASUS ZenFone 2E White - certified like new ASUS R770A ASUS ZenFone 2E White - certified like new ASUS S768A ASUS ZenFone 2E White - warranty replacement ASUS S769A ASUS ZenFone 2E White - warranty replacement ASUS S770A ASUS ZenFone 2E White - warranty replacement ASUS 6722A ASUS MeMO Pad 7 LTE (ME375CL) -BLK ASUS 6723A ASUS MeMO Pad 7 LTE (ME375CL) -BLK ASUS 6725A ASUS MeMO Pad 7 LTE (ME375CL) -BLK May 18, 2016 © 2016 AT&T Intellectual Property. All rights reserved. AT&T and the Globe logo are registered trademarks of AT&T Intellectual Property. AT&T Wireless -

Lumo10 RGB Fast Wireless Charger
Lumo10 RGB Fast Wireless Charger #23426 RGB fast wireless charger for smartphones Fast wireless charger with RGB lights and 10W output to charge your Qi-compatible phone Key features • Round wireless charging pad for easy phone placement • Touch-and-charge: simply put your smartphone on the pad and it will charge automatically • With RGB LED lights (rainbow wave) • Works with all Qi-compatible smartphones • Charging works without removing your phone case (supports plastic cases up to 3mm thick) • Supports fast-charging 7.5W output for iPhone and 10W output for Samsung Galaxy phones What's in the box System requirements • Wireless charger • For fast charging: USB charger compatible with Quick Charge 2.0/3.0. Example: • Micro-USB cable • Wall charger: trust.com/21818 • User guide • For normal charging: USB charger with 2A power output • Smartphone compatible with Qi wireless charging Publication date: 12-10-2019 Item number: 23426 © 2019 Trust. All rights reserved. URL: www.trust.com/23426 All brand names are registered trademarks of their respective owners. EAN Code: 8713439234268 Specifications are subject to change without prior notice. High resolution images: www.trust.com/23426/materials Lumo10 RGB Fast Wireless Charger Fuss-Free Wireless Charging There’s no more need to hunt for a cable with the Lumo10 RGB Fast Wireless Charger 10W. Touch-and-charge any Qi-compatible smartphone easily and quickly – and enjoy the charger’s stylish design and RGB light show on the side. Touch-and-Charge Could it be any easier? Just connect the charging pad to a USB charger (not included), place your phone on the charger’s surface and it will begin powering up instantly. -

The Misuse of Android Unix Domain Sockets and Security Implications
The Misuse of Android Unix Domain Sockets and Security Implications Yuru Shaoy, Jason Ott∗, Yunhan Jack Jiay, Zhiyun Qian∗, Z. Morley Maoy yUniversity of Michigan, ∗University of California, Riverside {yurushao, jackjia, zmao}@umich.edu, [email protected], [email protected] ABSTRACT eral vulnerabilities (e.g., CVE-2011-1823, CVE-2011-3918, In this work, we conduct the first systematic study in un- and CVE-2015-6841) have already been reported. Vendor derstanding the security properties of the usage of Unix do- customizations make things worse, as they expose additional main sockets by both Android apps and system daemons Linux IPC channels: CVE-2013-4777 and CVE-2013-5933. as an IPC (Inter-process Communication) mechanism, espe- Nevertheless, unlike Android IPCs, the use of Linux IPCs cially for cross-layer communications between the Java and on Android has not yet been systematically studied. native layers. We propose a tool called SInspector to ex- In addition to the Android system, apps also have access pose potential security vulnerabilities in using Unix domain to the Linux IPCs implemented within Android. Among sockets through the process of identifying socket addresses, them, Unix domain sockets are the only one apps can easily detecting authentication checks, and performing data flow make use of: signals are not capable of carrying data and analysis. Our in-depth analysis revealed some serious vul- not suitable for bidirectional communications; Netlink sock- nerabilities in popular apps and system daemons, such as ets are geared for communications across the kernel space root privilege escalation and arbitrary file access. Based and the user space. -

Avis Safedrive Compatible Smartphones
Avis SafeDrive Compatible smartphones The Avis SafeDrive app is compatible with the smartphones listed below. If you have one of the phones below, you can earn Active Rewards for driving well. ANDROID iOS Samsung Motorola – Droid Motorola HTC LG Sony Google Huawei Blackberry Apple Galaxy Mega 2 Droid Mini Moto X One E8 LG G3 Xperia Z2 Nexus 5 Honor 6 Dtek 50 iPhone SE Galaxy Mega 5.8 I9150 Droid Ultra Moto G (2014) One E8 CDMA LG G3 Stylus Xperia T2 Ultra Nexus 4 Mate 8 iPhone 6s Plus Galaxy Mega 6.3 I920 Droid Maxx Moto G Dual SIM (2014) One Max (4.3+) LG G3 A Xperia Z1 COMPACT (4.3+) Nexus 5X iPhone 6s Galaxy S5 Mini Moto Z Force Moto G 4G One Mini (4.3+) LG G3 LTE-A Xperia Z1S (4.3+) Nexus 6P iPhone 6 Plus Galaxy S5 Sport Moto X (2014) One (M7) (4.3+) LG G3 (CDMA) Xperia Z1F (4.3+) iPhone 6 Galaxy S5 Active Nexus 6 One S9 LG G4 Xperia Z1 (4.3+) iPhone 5S Galaxy S5 Moto Z Droid DNA (4.4.2) LG G5 Xperia Z (4.3+) iPhone 5C Galaxy S4 Active Evo 4G LTE (4.3+) LG G Pro2 Xperia ZL (4.3+) iPhone 5 Galaxy S4 HTC 10 LG G Flex Xperia SP (4.3+) iPhone 4S Galaxy S4 Zoom LG G Flex 2 Xperia ZR (4.3+) iPhone 7 Galaxy S3 Neo LG G2 Xperia Z ULTRA (4.3+) iPhone 7 Plus Galaxy S3 LG Optimus G Pro (4.4.2+) Xperia T (4.3+) iPhone 8 Galaxy Grand I19082 LG Optimus G (4.4.2+) Xperia TX (4.3+) iPhone 8 Plus Galaxy J LG VU (3.0) Xperia VL (4.3+) Galaxy Note 3 LG V10 Xperia V (4.3+) Galaxy Note 4 LG X Cam Xperia AX (4.3+) Galaxy K Zoom LG G5 SE Xperia Z3 (4.3+) Galaxy S6 LG G6 Xperia Z3 Compact Galaxy S6 Edge LG V20 Xperia Z5 Galaxy Alpha Xperia X Galaxy S4 Mini Xperia X Performance Galaxy Note 5 Sony Xperia XZ Galaxy S7 Sony Xperia X Compact Galaxy S7 Edge Xperia Z5 Compact Galaxy S8 Sony Xperia XA1 Ultra Galaxy Note8 Powered by Vitalitydrive administered by Discovery Insure Limited.