Fifty-Second Report
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Sixty-Sixth Report
66 STANDING COMMITTEE ON SOCIAL JUSTICE AND EMPOWERMENT (2018-2019) (SIXTEENTH LOK SABHA) MINISTRY OF MINORITY AFFAIRS Action taken by the Government on the observations/recommendations contained in the Sixty-second Report (Sixteenth Lok Sabha)of the Standing Committee on Social Justice and Empowerment (2017-18) on 'Implementation of Scheme of Multi- Sectoral Development Programme(MsDP)/Pradhan Mantri Jan Vikas Karyakram (PMJVK)’ of the Ministry of Minority Affairs SIXTY-SIXTH REPORT LOK SABHA SECRETARIAT NEW DELHI January, 2019/Pausha, 1940 (Saka) i SIXTY-SIXTH REPORT STANDING COMMITTEE ON SOCIAL JUSTICE AND EMPOWERMENT (2018-2019) (SIXTEENTH LOK SABHA) MINISTRY OF MINORITY AFFAIRS [Action taken by the Government on the observations/recommendations contained in the Sixty-second Report (Sixteenth Lok Sabha) of the Standing Committee on Social Justice and Empowerment (2017-18) on 'Implementation of Scheme of Multi- Sectoral Development Programme (MsDP)/Pradhan Mantri Jan Vikas Karyakram (PMJVK)’ of the Ministry of Minority Affairs] Presented to Lok Sabha on 03.01.2019 Laid in Rajya Sabha on 03.01.2019 LOK SABHA SECRETARIAT NEW DELHI January, 2019/Pausha, 1940 (Saka) ii CONTENTS PAGE(s) COMPOSITION OF THE COMMITTEE iv INTRODUCTION vi CHAPTER -I Report 1 CHAPTER- II Observations/Recommendations which have 13 been accepted by the Government. CHAPTER- III Observations/Recommendations which the 25 Committee do not desire to pursue in view of the Government's reply. CHAPTER -IV Observations/Recommendations in respect of 26 which replies of the Government have not been accepted and which require reiteration. CHAPTER- V Observations/Recommendations in respect of 31 which replies of the Government are interim in nature. -

List of Successful Candidates
11 - LIST OF SUCCESSFUL CANDIDATES CONSTITUENCY WINNER PARTY Andhra Pradesh 1 Nagarkurnool Dr. Manda Jagannath INC 2 Nalgonda Gutha Sukender Reddy INC 3 Bhongir Komatireddy Raj Gopal Reddy INC 4 Warangal Rajaiah Siricilla INC 5 Mahabubabad P. Balram INC 6 Khammam Nama Nageswara Rao TDP 7 Aruku Kishore Chandra Suryanarayana INC Deo Vyricherla 8 Srikakulam Killi Krupa Rani INC 9 Vizianagaram Jhansi Lakshmi Botcha INC 10 Visakhapatnam Daggubati Purandeswari INC 11 Anakapalli Sabbam Hari INC 12 Kakinada M.M.Pallamraju INC 13 Amalapuram G.V.Harsha Kumar INC 14 Rajahmundry Aruna Kumar Vundavalli INC 15 Narsapuram Bapiraju Kanumuru INC 16 Eluru Kavuri Sambasiva Rao INC 17 Machilipatnam Konakalla Narayana Rao TDP 18 Vijayawada Lagadapati Raja Gopal INC 19 Guntur Rayapati Sambasiva Rao INC 20 Narasaraopet Modugula Venugopala Reddy TDP 21 Bapatla Panabaka Lakshmi INC 22 Ongole Magunta Srinivasulu Reddy INC 23 Nandyal S.P.Y.Reddy INC 24 Kurnool Kotla Jaya Surya Prakash Reddy INC 25 Anantapur Anantha Venkata Rami Reddy INC 26 Hindupur Kristappa Nimmala TDP 27 Kadapa Y.S. Jagan Mohan Reddy INC 28 Nellore Mekapati Rajamohan Reddy INC 29 Tirupati Chinta Mohan INC 30 Rajampet Annayyagari Sai Prathap INC 31 Chittoor Naramalli Sivaprasad TDP 32 Adilabad Rathod Ramesh TDP 33 Peddapalle Dr.G.Vivekanand INC 34 Karimnagar Ponnam Prabhakar INC 35 Nizamabad Madhu Yaskhi Goud INC 36 Zahirabad Suresh Kumar Shetkar INC 37 Medak Vijaya Shanthi .M TRS 38 Malkajgiri Sarvey Sathyanarayana INC 39 Secundrabad Anjan Kumar Yadav M INC 40 Hyderabad Asaduddin Owaisi AIMIM 41 Chelvella Jaipal Reddy Sudini INC 1 GENERAL ELECTIONS,INDIA 2009 LIST OF SUCCESSFUL CANDIDATE CONSTITUENCY WINNER PARTY Andhra Pradesh 42 Mahbubnagar K. -

Provisional List of Eligible Candidates ( Ou ) for Admission Test to M.Ed
PROVISIONAL LIST OF ELIGIBLE CANDIDATES ( OU ) FOR ADMISSION TEST TO M.ED. COURSE (2014‐2015) UNDER UNIVERSITY OF CALCUTTA Sl Accn Form Cate ‐ Name Univ. Sex Post Graduate Sub No No No gory 1 ABHIJIT MAITY 566 OU 1455 M ECONOMICS(SPL ECONOMETRICS) GEN 2 ADITYA SAMANTA 246 OU 1075 M BENGALI GEN 3 AINDRILA TEWARI 52 OU 1320 F BENGALI GEN 4 AMARTYA PANJA 253 OU 1238 F BENGALI GEN 5 AMITAVA ADHIKARY 614 OU 1481 M ENGLISH GEN 6 AMRITA GIRI 353 OU 40011 F ZOOLOGY GEN 7 ANAMIKA MUKHERJEE 41 OU 1284 F BENGALI GEN 8 ANINDITA BANERJEE 89 OU 1129 F GEOGRAPHY GEN 9 ANINDITA PARAI 116 OU 1122 F HUMAN PHYSIOLOGY GEN 10 ANINDITA SAMANTA 343 OU 1236 F EDUCATION GEN 11 ANIRUDDHA BURMAN 173 OU 39538 M CHEMISTRY GEN 12 ANIRUDDHA DEY 448 OU 1160 M HISTORY GEN 13 ANKITA DUTTA 111 OU 1390 F SANSKRIT GEN 14 ANUP MANDAL 548 OU 39513 M GEOGRAPHY GEN 15 ANUPAM PAN 255 OU 39469 M MATHEMATICS GEN 16 ANUSHREE SANKI 588 OU 1434 F MATHEMATICS(APPLIED) GEN 17 ANUVA SAMANTA 529 OU 1293 F CHEMISTRY GEN 18 APURBA NANDI 438 OU 1257 M BENGALI GEN 19 ARABINDA DEY 12 OU 39539 M ENGLISH GEN 20 ARCHITA PAL 257 OU 39467 F GEOGRAPHY GEN 21 ARIJIT SAHA 369 OU 1459 M HISTORY GEN 22 ARIJITA KANJILAL 184 OU 1389 F SANSKRIT GEN 23 ARINDAM CHATTERJEE 494 OU 40031 M ENGLISH GEN 24 ARKA GANGULY 165 OU 39561 M ENGLISH GEN 25 ARNAB MAITRA 208 OU 39524 M EDUCATION GEN 26 ARPAN BAKSI 112 OU 1139 M ENGLISH GEN 27 ARPAN KUMAR MISHRA 187 OU 1373 M GEOGRAPHY GEN 28 ARPITA PAL 134 OU 39573 F GEOGRAPHY GEN 29 ARPITA PAL 462 OU 40004 F APPLIED GEOGRAPHY GEN 30 ARPITA PANJA 415 OU 1355 F BOTANY GEN Any discrepancy found may be reported to : Office of the Department of Education, Alipore Campus, CU latest by 24.04.2014, 4:00 PM Page : 1 of 12 PROVISIONAL LIST OF ELIGIBLE CANDIDATES ( OU ) FOR ADMISSION TEST TO M.ED. -

Lions Film Awards 01/01/1993 at Gd Birla Sabhagarh
1ST YEAR - LIONS FILM AWARDS 01/01/1993 AT G. D. BIRLA SABHAGARH LIST OF AWARDEES FILM BEST ACTOR TAPAS PAUL for RUPBAN BEST ACTRESS DEBASREE ROY for PREM BEST RISING ACTOR ABHISEKH CHATTERJEE for PURUSOTAM BEST RISING ACTRESS CHUMKI CHOUDHARY for ABHAGINI BEST FILM INDRAJIT BEST DIRECTOR BABLU SAMADDAR for ABHAGINI BEST UPCOMING DIRECTOR PRASENJIT for PURUSOTAM BEST MUSIC DIRECTOR MRINAL BANERJEE for CHETNA BEST PLAYBACK SINGER USHA UTHUP BEST PLAYBACK SINGER AMIT KUMAR BEST FILM NEWSPAPER CINE ADVANCE BEST P.R.O. NITA SARKAR for BAHADUR BEST PUBLICATION SUCHITRA FILM DIRECTORY SPECIAL AWARD FOR BEST FILM PREM TELEVISION BEST SERIAL NAGAR PARAY RUP NAGAR BEST DIRECTOR RAJA SEN for SUBARNALATA BEST ACTOR BHASKAR BANERJEE for STEPPING OUT BEST ACTRESS RUPA GANGULI for MUKTA BANDHA BEST NEWS READER RITA KAYRAL STAGE BEST ACTOR SOUMITRA CHATTERHEE for GHATAK BIDAI BEST ACTRESS APARNA SEN for BHALO KHARAB MAYE BEST DIRECTOR USHA GANGULI for COURT MARSHALL BEST DRAMA BECHARE JIJA JI BEST DANCER MAMATA SHANKER 2ND YEAR - LIONS FILM AWARDS 24/12/1993 AT G. D. BIRLA SABHAGARH LIST OF AWARDEES FILM BEST ACTOR CHIRANJEET for GHAR SANSAR BEST ACTRESS INDRANI HALDER for TAPASHYA BEST RISING ACTOR SANKAR CHAKRABORTY for ANUBHAV BEST RISING ACTRESS SOMA SREE for SONAM RAJA BEST SUPPORTING ACTRESS RITUPARNA SENGUPTA for SHWET PATHARER THALA BEST FILM AGANTUK OF SATYAJIT ROY BEST DIRECTOR PRABHAT ROY for SHWET PATHARER THALA BEST MUSIC DIRECTOR BABUL BOSE for MON MANE NA BEST PLAYBACK SINGER INDRANI SEN for SHWET PATHARER THALA BEST PLAYBACK SINGER SAIKAT MITRA for MISTI MADHUR BEST CINEMA NEWSPAPER SCREEN BEST FILM CRITIC CHANDI MUKHERJEE for AAJKAAL BEST P.R.O. -

World Bank Document
Public Disclosure Authorized Public Disclosure Authorized Public Disclosure Authorized Public Disclosure Authorized DRAFT FINAL REPORT FINAL DRAFT NOVEMBER 2009 TABLE OF CONTENTS Page No CHAPTER 1: INTRODUCTION 1 1.1 Project Background 1 1.1.1 Need for the Project 2 1.2 Introduction to overall project & components 4 1.2.1 National level component 5 1.2.2 State level component 6 1.3 Objectives of the Environmental and Social Assessment 10 1.4 Scope of the present study 10 1.4.1 Inception Report 10 1.4.2 Overall Context of Integrated Coastal Zone Management in India 11 1.4.3 Hazard Mapping and Mapping of ESAs 11 1.4.4 National Level Capacity Building & National Institute for 11 Sustainable Coastal Zone Management 1.4.5 Preparation of ICZM Plans in Participating States 12 1.4.6 Priority Investments in Orissa, Gujarat and West Bengal 12 1.4,7 Final Documentation 13 1.5 Methodology Adopted for Achieving Study Objectives 13 1.5.1 Overall context of Integrated Coastal Zone Management in India 14 1.5.2 Hazard Mapping and Mapping of Environmentally Sensitive Areas 15 1.5.3 National Level Capacity Building and National Institute for Sustainable 15 Coastal Zone Management 1.5.4 Preparation of ICZM plans 15 1.5.5 Priority Investments in Orissa, Gujarat and West Bengal 15 1.6 Report Structure 16 CHAPTER 2: POLICY, REGULATION AND INSTITUTIONAL FRAMEWORK 17 2.1 Constitutional provisions 17 2.2 International conventions and treaties signed by India 18 2.3 National Policies related to Coastal Areas and Marine Areas 22 2.4 Legal and Regulatory Framework -

Parliamentary Bulletin
RAJYA SABHA Parliamentary Bulletin PART-II Nos.: 51236-51237] WEDNESDAY, SEPTEMBER 4, 2013 No. 51236 Committee Co-ordination Section Meeting of the Parliamentary Forum on Youth As intimated by the Lok Sabha Secretariat, a meeting of the Parliamentary Forum on Youth on the subject ‘Youth and Social Media: Challenges and Opportunities’ will be held on Thursday, 05 September, 2013 at 1530 hrs. in Committee Room No.074, Ground Floor, Parliament Library Building, New Delhi. Shri Naman Pugalia, Public Affairs Analyst, Google India will make a presentation. 2. Members are requested to kindly make it convenient to attend the meeting. ——— No. 51237 Committee Co-ordination Section Re-constitution of the Department-related Parliamentary Standing Committees (2013-2014) The Department–related Parliamentary Standing Committees have been reconstituted w.e.f. 31st August, 2013 as follows: - Committee on Commerce RAJYA SABHA 1. Shri Birendra Prasad Baishya 2. Shri K.N. Balagopal 3. Shri P. Bhattacharya 4. Shri Shadi Lal Batra 2 5. Shri Vijay Jawaharlal Darda 6. Shri Prem Chand Gupta 7. Shri Ishwarlal Shankarlal Jain 8. Shri Shanta Kumar 9. Dr. Vijay Mallya 10. Shri Rangasayee Ramakrishna LOK SABHA 11. Shri J.P. Agarwal 12. Shri G.S. Basavaraj 13. Shri Kuldeep Bishnoi 14. Shri C.M. Chang 15. Shri Jayant Chaudhary 16. Shri K.P. Dhanapalan 17. Shri Shivaram Gouda 18. Shri Sk. Saidul Haque 19. Shri S. R. Jeyadurai 20. Shri Nalin Kumar Kateel 21. Shrimati Putul Kumari 22. Shri P. Lingam 23. Shri Baijayant ‘Jay’ Panda 24. Shri Kadir Rana 25. Shri Nama Nageswara Rao 26. Shri Vishnu Dev Sai 27. -
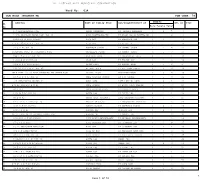
Ward No: 034 ULB Name :KOLKATA MC ULB CODE: 79
BPL LIST-KOLKATA MUNICIPAL CORPORATION Ward No: 034 ULB Name :KOLKATA MC ULB CODE: 79 Member Sl Address Name of Family Head Son/Daughter/Wife of BPL ID Year No Male Female Total 1 1/6 BAROWARITALA ROAD ABHAY KARMAKAR LT. MARARI KARMAKAR 3 2 5 3 2 2/12A RASHMONI BAZAR ROAD KOL-10 AJAY BHATTACHARJEE LT.ABONI MOHON BHATTACHAR 3 1 4 5 3 122/11/1 B M RD.KOL-10 AJAY DAS LT HARIPADA DAS 4 3 7 6 4 B T RD 47/C B T RD KOL-10 AJOY DAS LT BIJOY DAS 2 1 3 10 5 23 C P RD.KOL-10 AKHILESH SINGH LT SAMBHU SINGH 3 1 4 12 6 CHALPATTI ROAD 23 CHALPATTI ROAD AKSHILESH SINGH LT SAMBHU SINGH 3 1 4 13 7 29A/H/7 C P RD.KOL-10 ALO RANI SAHA LT NARAYAN CH SAHA 0 1 1 14 8 153/8 B M RD.KOL-10 ALOK ROY LT TARINI ROY 2 1 3 16 9 44/B R R L M RD.KOL-85 ALOKA KHAN LT BANOBI KHAN 1 1 2 17 10 131/20 R R L M RD.KOL-85 ALPANA PANJA LT KHUDIRAM PANJA 0 4 4 18 11 JELE PARA 131/20 RAJA RAJENDRA PAL MITRA ROAD ALPANA PANJA KHUDIRAM PANJA 2 2 4 19 12 29/4/A B T RD.KOL-10 AMAL KRISHNA SARKAR LT A K SARKAR 3 1 4 21 13 5/B HEMCHANDRA NASKAR RD AMAL SAHA LATE HARIDAS SAHA 2 4 6 22 14 B M RD 162/H/2 B M RD AMAL SARKAR LT BISTU PADA SARKAR 2 1 3 23 15 9A B M RD AMAR KRISHNA KUNDU NITYANANDA KUNDU 2 2 4 25 16 1/16 B T RD.KOL-10 AMITA DAS LT DILIP DAS 0 1 1 26 17 9A B M RD AMIYA BALA ADHIKARI LATE BALARAM ADHIKARY 0 3 3 27 18 12/H/11 K B LANE.KOL-10 AMULYA BANERJEE LT MANORANJAN BANERJEE 2 1 3 28 19 2/11 R B RD.KOL-10 AMULYA MONDAL LT MAHENDRA MONDAL 0 0 1 29 20 163/3 B M RD ANANDA DAS GURUDAS DAS 3 2 5 30 21 MUCHI PARA 4A/20 RASMANI BAZAR ROAD ANANDA PAL LT GANESH PAL 2 1 3 31 22 10/1/H/2 S K RD.KOL-10 ANIL BARAN CHAKRABORTY LT ABINASH CHAKRABORTY 2 1 3 36 23 27/13 B M ROAD ANIL CHANDRA DAS LT. -
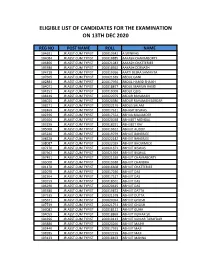
Eligible List of Candidates for the Examination on 13Th Dec 2020
ELIGIBLE LIST OF CANDIDATES FOR THE EXAMINATION ON 13TH DEC 2020 REG NO POST NAME ROLL NAME 104691 JR.ASST.CUM TYPIST 200019342 A SRINIVAS 104084 JR.ASST.CUM TYPIST 200018885 AAKASH CHAKRABORTY 106866 JR.ASST.CUM TYPIST 200021043 AAKASH CHATTERJEE 103386 JR.ASST.CUM TYPIST 200018362 AAKASH DEBNATH 104718 JR.ASST.CUM TYPIST 200019366 AARTI BESRA SAMANTA 107605 JR.ASST.CUM TYPIST 200021639 ABDUL GANI 102884 JR.ASST.CUM TYPIST 200017956 ABDUL HAMID SHAIKH 104071 JR.ASST.CUM TYPIST 200018877 ABDUL MAMUN RASID 104252 JR.ASST.CUM TYPIST 200019009 ABDUL QUIS 108149 JR.ASST.CUM TYPIST 200022079 ABDUR RAHAMAN 106025 JR.ASST.CUM TYPIST 200020386 ABDUR RAHAMAN SARDAR 108271 JR.ASST.CUM TYPIST 200022176 ABDUS SALAM 102469 JR.ASST.CUM TYPIST 200017611 ABHIGIT BISWAS 102396 JR.ASST.CUM TYPIST 200017554 ABHIJA MAJUMDER 105604 JR.ASST.CUM TYPIST 200020038 ABHIJEET MONDAL 103296 JR.ASST.CUM TYPIST 200018291 ABHIJEET RAY 105068 JR.ASST.CUM TYPIST 200019622 ABHIJIT AUDDY 105246 JR.ASST.CUM TYPIST 200019759 ABHIJIT BANERJEE 108228 JR.ASST.CUM TYPIST 200022142 ABHIJIT BANERJEE 108087 JR.ASST.CUM TYPIST 200022029 ABHIJIT BHOWMICK 107270 JR.ASST.CUM TYPIST 200021371 ABHIJIT BISWAS 107962 JR.ASST.CUM TYPIST 200021929 ABHIJIT BISWAS 107491 JR.ASST.CUM TYPIST 200021539 ABHIJIT CHAKRABORTY 105008 JR.ASST.CUM TYPIST 200019588 ABHIJIT CHANDRA 101178 JR.ASST.CUM TYPIST 200016608 ABHIJIT CHATTERJEE 102078 JR.ASST.CUM TYPIST 200017296 ABHIJIT DAS 102364 JR.ASST.CUM TYPIST 200017527 ABHIJIT DAS 103559 JR.ASST.CUM TYPIST 200018501 ABHIJIT DAS 106290 JR.ASST.CUM TYPIST -

(Sixteenth Lok Sabha) Ministry of Social Justice And
67 STANDING COMMITTEE ON SOCIAL JUSTICE AND EMPOWERMENT (2018-2019) (SIXTEENTH LOK SABHA) MINISTRY OF SOCIAL JUSTICE AND EMPOWERMENT (DEPARTMENT OF SOCIAL JUSTICE AND EMPOWERMENT) Action taken by the Government on the observations/recommendations contained in the Fifty-fourth Report (Sixteenth Lok Sabha) of the Standing Committee on Social Justice and Empowerment (2018-19) on "Impact Analysis of the Micro-Credit Finance Schemes of the National Scheduled Castes Finance and Development Corporation (NSFDC)” of the Ministry of Social Justice and Empowerment (Department of Social Justice and Empowerment). SIXTY-SEVENTH REPORT LOK SABHA SECRETARIAT NEW DELHI February, 2019/Magha, 1940 (Saka) i SIXTY-SEVENTH REPORT STANDING COMMITTEE ON SOCIAL JUSTICE AND EMPOWERMENT (2018-19) (SIXTEENTH LOK SABHA) MINISTRY OF SOCIAL JUSTICE AND EMPOWERMENT (DEPARTMENT OF SOCIAL JUSTICE AND EMPOWERMENT) Action taken by the Government on the observations/recommendations contained in the Fifty-fourth Report (Sixteenth Lok Sabha) of the Standing Committee on Social Justice and Empowerment (2018-19) on "Impact Analysis of the Micro-Credit Finance Schemes of the National Scheduled Castes Finance and Development Corporation (NSFDC)” of the Ministry of Social Justice and Empowerment (Department of Social Justice and Empowerment). Presented to Lok Sabha on 13.02.2019 Laid in Rajya Sabha on 13.02.2019 LOK SABHA SECRETARIAT NEW DELHI February, 2019/Magha, 1940 (Saka) ii CONTENTS PAGE COMPOSITION OF THE COMMITTEE iv INTRODUCTION vi CHAPTER -I Report 1 CHAPTER- II Observations/Recommendations which have been accepted 17 by the Government. CHAPTER- III Observations/Recommendations which the Committee do not 31 desire to pursue in view of the Government's reply. -

List of Panel Advocates Empanelled Under Kolkata Circle Sl Name of the Advocate Address & Phone No of the Advocate Locality No 1 M/S Sanderson & Morgans
LIST OF PANEL ADVOCATES EMPANELLED UNDER KOLKATA CIRCLE SL NAME OF THE ADVOCATE ADDRESS & PHONE NO OF THE ADVOCATE LOCALITY NO 1 M/S SANDERSON & MORGANS. OFFICE: KOLKATA ROYAL INSURANCE BUILDING, 5, NETAJI SUBHASH ROAD, KOLKATA - 700001 PHONE: 22482644, 22486247 9830429205 (SHRI P C GHOSH) PATRA: 9830976209 2 SHRI S P SARKAR OFFICE: KOLKATA 5, K S ROY ROAD, 3RD FLOOR, KOLKATA – 700001 PHONE 5344895, 9831315311 3 SHRI JAYDEB BRAHMACHARI. OFFICE: KOLKATA 1B, OLD POST OFFICE STREET, EMRALD HOUSE, GROUND FLOOR, KOLKATA – 700001 PHONE: 22430891, 22481463, 22536977 (RESIDENCE) 4 SHRI DEBASISH CHAKRABARTI. OFFICE:9831325750 KOLKATA 7 A, KIRAN SHANKER ROY ROAD, TOP FLOOR, KOLKATA – 700001 PHONE – 9331050350 26807571 (RESIDENCE). [email protected] 9836158734 ( Anindita) 9088724614, 9614226285( Mortoza/ A/c) 5 SHRI RADHEY SHYAM TEWARI. OFFICE: KOLKATA 9, K. S. Roy 2nd Floor, KOLKATA –700001 PHONE: 22310941, 9830123503. 6 SHRI ASHIM KUMAR ROY OFFICE: KOLKATA CHOUDHURY. 7,OLD POST OFFICE, STREET, KOLKATA – 700001 PHONE: 22485588 24155224 (RESIDENCE) 7 SMT DEBJANI MITRA NEOGY. RESIDENCE: KOLKATA 66/1,RAJA S C MULLICK ROAD, KOLKATA– 700047 49/11B, Hindustan Park, Kol-29 PHONE: 24407316, 24656180 9830360953 8 MS. DEVYANI ASHRA. OFFICE: KOLKATA 11, OLD POST OFFICE STREET, 3RD FLOOR, KOLKATA – 700001 PHONE: 22109169, 22439427, 9831028333 24764793 & 24721192 (RESIDENCE) 9903155982(tarun patra) 9 SMT SASWATI GHOSH SINHA. OFFICE: KOLKATA C/O INDRANIL CHATTERJEE & COMPANY. 6, OLD POST OFFICE STREET, SOUTH BASEMENT, ROOM NO 28, KOLKATA – 700001 PHONE: 9874382917 9331218617, 22428447 10 SHRI TAPAN KUMAR BANERJEE. OFFICE: H C Bar Ass Room No 7, 1, KALI BANERJEE LANE, HOWRAH – 711101, KOLKATA PHONE – 26410147, 9433673525 11 SHRI TIMIR KUMAR ROY. -
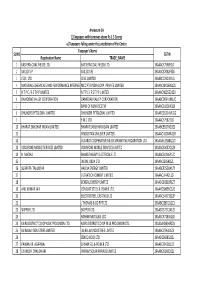
FINAL DISTRIBUTION.Xlsx
Annexure-1A 1)Taxpayers with turnover above Rs 1.5 Crores a) Taxpayers falling under the jurisdiction of the Centre Taxpayer's Name SL NO GSTIN Registration Name TRADE_NAME 1 EASTERN COAL FIELDS LTD. EASTERN COAL FIELDS LTD. 19AAACE7590E1ZI 2 SAIL (D.S.P) SAIL (D.S.P) 19AAACS7062F6Z6 3 CESC LTD. CESC LIMITED 19AABCC2903N1ZL 4 MATERIALS CHEMICALS AND PERFORMANCE INTERMEDIARIESMCC PTA PRIVATE INDIA CORP.LIMITED PRIVATE LIMITED 19AAACM9169K1ZU 5 N T P C / F S T P P LIMITED N T P C / F S T P P LIMITED 19AAACN0255D1ZV 6 DAMODAR VALLEY CORPORATION DAMODAR VALLEY CORPORATION 19AABCD0541M1ZO 7 BANK OF NOVA SCOTIA 19AAACB1536H1ZX 8 DHUNSERI PETGLOBAL LIMITED DHUNSERI PETGLOBAL LIMITED 19AAFCD5214M1ZG 9 E M C LTD 19AAACE7582J1Z7 10 BHARAT SANCHAR NIGAM LIMITED BHARAT SANCHAR NIGAM LIMITED 19AABCB5576G3ZG 11 HINDUSTAN UNILEVER LIMITED 19AAACH1004N1ZR 12 GUJARAT COOPERATIVE MILKS MARKETING FEDARATION LTD 19AAAAG5588Q1ZT 13 VODAFONE MOBILE SERVICES LIMITED VODAFONE MOBILE SERVICES LIMITED 19AAACS4457Q1ZN 14 N MADHU BHARAT HEAVY ELECTRICALS LTD 19AAACB4146P1ZC 15 JINDAL INDIA LTD 19AAACJ2054J1ZL 16 SUBRATA TALUKDAR HALDIA ENERGY LIMITED 19AABCR2530A1ZY 17 ULTRATECH CEMENT LIMITED 19AAACL6442L1Z7 18 BENGAL ENERGY LIMITED 19AADCB1581F1ZT 19 ANIL KUMAR JAIN CONCAST STEEL & POWER LTD.. 19AAHCS8656C1Z0 20 ELECTROSTEEL CASTINGS LTD 19AAACE4975B1ZP 21 J THOMAS & CO PVT LTD 19AABCJ2851Q1Z1 22 SKIPPER LTD. SKIPPER LTD. 19AADCS7272A1ZE 23 RASHMI METALIKS LTD 19AACCR7183E1Z6 24 KAIRA DISTRICT CO-OP MILK PRO.UNION LTD. KAIRA DISTRICT CO-OP MILK PRO.UNION LTD. 19AAAAK8694F2Z6 25 JAI BALAJI INDUSTRIES LIMITED JAI BALAJI INDUSTRIES LIMITED 19AAACJ7961J1Z3 26 SENCO GOLD LTD. 19AADCS6985J1ZL 27 PAWAN KR. AGARWAL SHYAM SEL & POWER LTD. 19AAECS9421J1ZZ 28 GYANESH CHAUDHARY VIKRAM SOLAR PRIVATE LIMITED 19AABCI5168D1ZL 29 KARUNA MANAGEMENT SERVICES LIMITED 19AABCK1666L1Z7 30 SHIVANANDAN TOSHNIWAL AMBUJA CEMENTS LIMITED 19AAACG0569P1Z4 31 SHALIMAR HATCHERIES LIMITED SHALIMAR HATCHERIES LTD 19AADCS6537J1ZX 32 FIDDLE IRON & STEEL PVT. -

Hon'ble Justice Girish Chandra Gupta and Hon'ble Justice Tapabrata Chakraborty
1 FORM NO.(J2) IN THE HIGH COURT AT CALCUTTA CIVIL APPELLATE JURISDICTION APPELLATE SIDE Present: Hon'ble Justice Girish Chandra Gupta And Hon'ble Justice Tapabrata Chakraborty AST 352 of 2014 With ASTA 254 of 2014 TAPAS PAUL VS. BIPLAB KUMAR CHOWDHURY & ORS With AST 355 of 2014 With ASTA 255 of 2014 STATE OF WEST BENGAL & ORS. Versus BIPLAB KUMAR CHOWDHURY & ORS. Advocate for the Appellant in AST 355 of 2014:-Mr. Kalyan Banerjee, Sr. Adv. Mr. Manjit Singh, ld. Public Prosecutor Mr. Sakya Sen, Mr. Suman Sengupta, Mr. B.P. Vaisya Mr. Pawan Kumar Gupta Advocate for the Appellant in AST 352 of 2014 :Mr. Kishore Dutta, Sr. Adv. Mr. Rajdeep Majumder Advocate for the Respondent No.1 in AST 355 of 2014 & AST 352 of 2014: Mr. Aniruddha Chatterjee Mr. Sukanta Chakraborty Heard on :30.07.2014, 31.07.2014 & 01.08. 2014 Judgment delivered on : 13.08.2014 GIRISH CHANDRA GUPTA, J.: 1. The case of the writ petitioner is that there has been “inaction on the part of the respondent authorities thereby not taking necessary steps to arrest the private respondent No.7 2 thereby treating the complaint dated July 2, 2014 of the petitioner as F.I.R.” 2. The written complaint dated 2nd July, 2014 addressed to the Inspector-in- Charge, Nakashipara Police Station, District Nadia referred to above reads as follows:- Dear Sir(s), This is to bring to your kind notice that I, Biplab Kumar Chowdhury, son of Late Birendra Nath Chowdhury, residing a 108 M. B. Road, Purbati Kumari Kabi, Sukanta Sarani Birati, Kolkata – 700051, being a public spirited citizen is highly perturbed by the way when I heard and came to know from video footage telecast by some private channels that a sitting Member of Parliament, Sri Tapas Paul who openly declared on June 14, 2014 that he “carries a revolver” which he would use to “liquidate” CPIM activists and claimed that he was a top “gangster”.