Download the Program
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Etnolingwistyka Problemy Jêzyka I Kultury
ETNOLINGWISTYKA PROBLEMY JÊZYKA I KULTURY ETHNOLINGUISTICS ISSUES IN LANGUAGE AND CULTURE 28 MARIA CURIE-SK£ODOWSKA UNIVERSITY FACULTY OF HUMANITIES ETHNOLINGUISTIC COMMISSION INTERNATIONAL SLAVIC COMMITTEE ETHNOLINGUISTIC SECTION OF THE COMMITTEE OF LINGUISTICS, POLISH ACADEMY OF SCIENCES Editor−in−Chief JERZY BARTMIÑSKI Assistant to Editor STANIS£AWA NIEBRZEGOWSKA-BARTMIÑSKA Secretary MARTA NOWOSAD-BAKALARCZYK Translators ADAM G£AZ (project coordinator), RAFA£ AUGUSTYN, KLAUDIA DOLECKA, AGNIESZKA GICALA, AGNIESZKA MIERZWIÑSKA-HAJNOS Scientific Council DEJAN AJDAÈIÆ (Taras Shevchenko National University of Kyiv, Ukraine) ELENA BEREZOVIÈ (Ural Federal University, Yekaterinburg, Russia) WOJCIECH CHLEBDA (University of Opole, Poland) ALOYZAS GUDAVIÈIUS (Šiauliai University, Lithuania) ALEKSEJ JUDIN (Ghent University, Belgium) JACEK MICHAEL MIKOŒ (University of Wisconsin, Milwaukee, USA) HANNA POPOWSKA-TABORSKA (Polish Academy of Sciences, Warsaw, Poland) ZUZANA PROFANTOVÁ (Slovak Academy of Sciences, Bratislava, Slovakia) SVETLANA TOLSTAJA (Russian Academy of Sciences, Moscow, Russia) ANNA WIERZBICKA (Australian National University, Canberra, Australia) KRZYSZTOF WROC£AWSKI (Polish Academy of Sciences, Warsaw, Poland) ETNOLINGWISTYKA PROBLEMY JÊZYKA I KULTURY ETHNOLINGUISTICS ISSUES IN LANGUAGE AND CULTURE 28 Lublin 2017 Maria Curie-Sk³odowska University Press Reviewers MACIEJ ABRAMOWICZ (University of Warsaw), DEJAN AJDAÈIÆ (Taras Shevchenko National University of Kyiv), NIKOLAJ ANTROPOV (National Academy of Sciences of Belarus), ENRIQUE -

Ethnolinguistics in the Year 2016∗
Ethnolinguistic 28 Lublin 2017 I. Research articles DOI: 10.17951/et.2016.28.7 Jerzy B a r t m i ń s k i (UMCS, Lublin, Poland) Ethnolinguistics in the Year 2016∗ This article is the voice of Etnolingwistyka’s Editor-in-Chief on the current tasks of ethnolinguistics as a scholarly subdiscipline, as well as those of the journal. According to the author, of the two foundations of Slavic ethnolin- guistics mentioned by Nikita Tolstoy (i.e., its pan-Slavic character and the unity of language and culture) it is mainly the latter that has preserved its topicality: language is the source of knowledge about people and human com- munities, as well as the basis for building one’s identity (individual, national, regional, professional). The agenda of cultural linguistics has been followed by the contributors to the present journal and its editorial team with a focus on various genres of folklore, the problems of the linguistic worldview, and in recent issues with studies on the semantics of selected cultural concepts (FAMILY, DEMOCRACY, EQUALITY, OTVETSTVENNOST’, etc.). An ethnolinguistics that thus seeks “culture in language” (i.e. in the semantic layer of linguistic forms) is close – especially in its cognitivist variant – to Western cultural or anthropological linguistics. When Slavic ethnolinguistics focuses on the semantics of value terms, it stands a good chance of engaging in a dialogue with Western anthropological linguistics and contribute original insights to the common body of research on values. A specific proposal in this direction is the international project EUROJOS. Key words: cultural linguistics, culture in language, Etnolingwistyka, EUROJOS, Axiological Lexicon of Slavs and their Neighbours, cultural concepts ∗ This is a revised and extended version of the paper presented at the conference Slawische Ethnolinguistik: Methoden, Ergebnisse, Perspektive (17–19 December, 2015), organized by the Department of Slavonic Studies at the University of Vienna. -

Team Standings
23rd IAAF World Race Walking Cup Cheboksary Saturday 10 and Sunday 11 May 2008 20 Kilometres Race Walk WOMEN ATHLETIC ATHLETIC ATHLETIC ATHLETIC ATHLETIC ATHLETIC ATHLETIC ATHLETIC ATHLETIC ATHLETIC ATHLETIC ATHLETIC ATHLETIC ATHLETIC ATHLETIC ATHLETIC ATHLETIC ATHLETIC ATHLETIC ATHLETIC ATHLETIC ATHLETIC ATHLETIC ATHL Team Standings ATHLETIC ATHLETIC ATHLETIC ATHLETIC ATHLETIC ATHLETIC ATHLETIC ATHLETIC ATHLETIC ATHLETIC ATHLETIC ATHLETIC ATHLETIC ATHLETIC ATHLETIC ATHLETIC ATHLETIC ATHLETIC ATHLETIC ATHLETIC ATHLETIC ATHLETIC ATHLETIC ATHLETI 11 May 2008 13:00 1 3 POSMARK BIB COMPETITOR 1 7 RUSSIA 11:25:42 136 Olga KANISKINA 21:26:29 139 Tatyana SIBILEVA 41:28:29 134 Lyudmila ARKHIPOVA DNF 138 Tatyana SHEMYAKINA DQ 137 Anisya KIRDYAPKINA 2 24 PORTUGAL 31:28:17 124 Vera SANTOS 101:29:38 120 Susana FEITOR 111:29:39 118 Ana CABECINHA 191:32:35 123 Inês HENRIQUES 261:33:56 122 Maribel GONÇALVES 3 38 SPAIN 5481:28:39 María VASCO 8471:29:31 María José POVES 251:33:55 46 Beatriz PASCUAL 281:34:26 42 Rocío FLORIDO 341:35:37 43 Maria Teresa GARGALLO 4 61 LITHUANIA 121:30:35 99 Sonata MILUŠAUSKAITÉ 171:31:21 100 Kristina SALTANOVIC 321:35:10 97 Neringa AIDIETYTE 391:36:52 101 Brigita VIRBALYTÉ 601:41:22 98 Jurgita KRINICKAITÉ-MEŠKAUSKIENE 5 75 AUSTRALIA 741:29:27 Jane SAVILLE 311:35:01 8 Claire WOODS 371:36:32 5 Natalie SAVILLE DNF 6 Megan SZIROM 6 79 ROMANIA 181:31:37 130 Ana Maria GROZA 211:33:19 131 Claudia STEF 401:36:57 127 Veronica BUDILEANU Issued Sunday, 11 May 2008 at 15:04 Timing by SEIKO Data processing by EPSON 2 3 POSMARK BIB COMPETITOR -

FULL AUST WALK RESULTS 2006-2007.Pdf
2006 / 2007 THE RACEWALKING YEAR IN REVIEW COMPLETE VICTORIAN RESULTS MAJOR AUSTRALIAN AND MAJOR INTERNATIONAL RESULTS Tim Erickson 25 February 2010 1 Table of Contents INTERNATIONAL RESULTS ASIAN GAMES RACEWALKS, THURSDAY 7 DECEMBER 2006 ................................................................................ 4 AUSTRALIAN YOUTH OLYMPIC FESTIVAL, SYDNEY, 17-21 JAN 2007 ................................................................. 5 IAAF RACE WALKING CHALLENGE, ROUND 1, NAUCALPAN, MEXICO, SATURDAY 10 MARCH 12007 ....... 6 IAAF RACE WALKING CHALLENGE, SHENZHEN, CHINA, 24-25 MARCH 2007 ................................................... 8 26TH DUDINCE 50 KM WALKING CARNIVAL, SLOVAKIA, SATURDAY 24 MARCH 2007 ............................... 10 IAAF RACEWALKING GRAND PRIX, RIO MAIOR, PORTUGAL, SATURDAY 14 APRIL 2007 ........................... 12 7TH EUROPEAN CUP RACE WALKING, ROYAL LEAMINGTON SPA, SUNDAY 20 MAY 2007 .......................... 13 IAAF RACE WALKING CHALLENGE, LA CORUNA, SPAIN, 2 JUNE 2007 ............................................................ 17 RUSSIAN RACEWALKING CHAMPIONSHIPS, CHEBOKSARY, RUSSIA, SUNDAY 17 JUNE 2007 ................... 19 2007 IAAF RACEWALKING GRAND PRIX, KRAKOW, POLAND, JUNE 23, 2007 ................................................. 20 5TH WORLD YOUTH CHAMPIONSHIPS, OSTRAVA, CZECH REPUBLIC, 11-15 JULY 2007 .............................. 22 6TH EUROPEAN UNDER 23 CHAMPIONSHIPS, DEBRECEN, HUNGARY, 12-15 JULY 2007 ............................ 24 EUROPEAN JUNIOR CHAMPIONSHIPS, HENGELO, THE NETHERLANDS, -
NEWSLETTER Volume 6, No
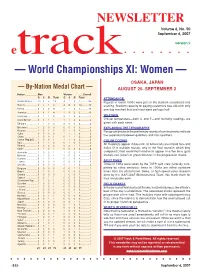
NEWSLETTER Volume 6, No. 50 September 6, 2007 version ii etrack — World Championships XI: Women — OSAKA, JAPAN — By-Nation Medal Chart — AUGUST 25–SEPTEMBER 2 Nation ..................Men Women ......Overall G S B Total G S B Total ATTENDANCE United States .......10 3 6 19 4 1 2 7 ............26 Figures in round 1000s were put on the stadium scoreboard one Russia ..................0 1 1 2 4 8 2 14 ..........16 evening. Stadium capacity for paying customers was c36,000; only Kenya ..................3 2 3 8 2 1 2 5 ............13 one day reached that and most were perhaps half. Jamaica ...............0 3 1 4 1 3 2 6 ............10 Germany ..............0 1 1 2 2 1 2 5 ..............7 WEATHER Great Britain .........0 0 1 1 1 1 2 4 ..............5 Official temperature—both C and F—and humidity readings are Ethiopia ................1 1 0 2 2 0 0 2 ..............4 given with each event. Bahamas ..............1 2 0 3 0 0 0 0 ..............3 EXPLAINING THE TYPOGRAPHY Belarus ................1 0 1 2 0 1 0 1 ..............3 Paragraph breaks in the preliminary rounds of running events indicate Cuba ....................0 0 0 0 1 1 1 3 ..............3 the separation between qualifiers and non-qualifiers. China ...................1 0 0 1 0 1 1 2 ..............3 Czech Republic ....1 0 0 1 1 1 0 2 ..............3 COLOR CODING Italy ......................0 1 1 2 0 1 0 1 ..............3 All medalists appear in blue ink; all Americans are in bold face and Poland .................0 0 2 2 0 0 1 1 ..............3 Spain ...................0 1 0 1 0 0 2 2 ..............3 italics (if in multiple rounds, only in the final round in which they Australia ...............1 0 0 1 1 0 0 1 ..............2 competed); field-event/multi medalists appear in either blue (gold Bahrain ................0 1 0 1 1 0 0 1 ..............2 medal), red (silver) or green (bronze) in the progression charts. -

2019 World Championships Statistics
2019 World Championships Statistics - Women’s 20Km Walk by K Ken Nakamura The records to look for in Doha: 1) No nation ever swept medals; can CHN do it? 2) Can Morejon win first medal for ECU at W20kmWalk? Summary: All time Performance List at the World Championships Performance Performer Time Name Nat Pos Venue Year 1 1 1:25:41 Olimpiada Ivanova RUS 1 Helsinki 2005 2 2 1:26:18 Yang Jiayu CHN 1 London 2017 3 3 1:26:19 Mari a Guadalupe Gonzalez MEX 2 London 2017 4 4 1:26:36 Antonella Palmisano ITA 3 London 2017 5 5 1:26:52 Yelena Nikolayeva RUS 1 Paris 2003 6 6 1:26:59 Erica De Sena BRA 4 London 2017 7 7 1:27:05 Rita Turova BLR 2 Helsinki 2005 8 8 1:27:08 Elena L ashmanova RUS 1 Moskva 2013 9 9 1:27:11 Anisya Kirdyapkina RUS 2 Moskva 20 13 10 10 1:27:34 Gillian O’Sullivan IRL 2 Paris 2003 Margin of Victory Difference Winning time Name Nat Venue Year Max 1 min 24 second s 1:25:41 Olimpiada Ivanova RUS Helsinki 2005 1 min 1 second 1:27:48 Olimpiada Ivanova RUS Edmonton 2001 Min 0 second 1:27:45 Liu Hong CHN Beijing 2015 1 second 1:26:18 Yang Jiayu CHN London 2017 2 seconds 1:30:50 Liu Hongyu CHN Sevilla 1999 3 seconds 1:27:08 Elena Lashmanova RUS Moskva 2013 Best Marks for Places in the World Championships Pos Time Name Nat Venue Year 1 1:25:41 Olimpiada Ivanova RUS Helsinki 2005 2 1:26:19 Maria Guadalupe Gonzalez MEX London 2017 1:27:05 Rita Turova BLR Helsinki 2005 3 1:26:36 Antonella Palmisano ITA London 2017 1:28:10 Valentina Tsybulskaya BLR Paris 2003 Liu Hong CHN Moskva 2013 4 1:26:59 Erica De Sena BRA London 2017 1:28:32 Sun Huanhuan -

Text Analysis Culture, Framework & Teaching
Text Analysis Culture, Framework & Teaching Edited by Jane Mattisson and Maria Bäcke KRISTIANSTAD UNIVERSITY PRESS Text Analysis Culture, Framework & Teaching Högskolan Kristianstad Text Analysis Culture, Framework & Teaching Conference proceedings from the Text Analysis Symposium at Kristianstad University, April 2014 Edited by Jane Mattisson and Maria Bäcke !1 Kristianstad University Press 2014:4 © Jane Mattisson and Maria Bäcke 2014 Department of Human Sciences School of Education and Environment Kristianstad University 291 88 Kristianstad ISBN: 978-91-87973-00-0 !2 Table of Contents Foreword 4 Bianca Foghel's “Through the Maze of the Unconscious in John Fowles’s The Magus” 5 Alena Rudenka & Michael Zukosky’s “Traditional Culture as a Discourse” 13 Erliza Lopez Pedersen’s “Representations of the Filipino Identities in Blogs” 26 Maria Freij & Lena Ahlin’s “Going Forward with Feedback: On Autonomy and Teacher Feedback” 42 Jane Mattisson’s “The Two Stories of Detective Fiction” 59 Alla Kozhinova & Alena Sourkova’s “Montage as a Method of One Ancient Text Organization: On text structure of the Book of Daniel from the Vilnius Old Testament Florilegium” 68 Larisa Suarez’ “Figures of Speech in Somerset Maugham’s Short Story ‘Louise’” 83 Sharon Ahlquist’s “Appreciating Literature: A Focus on Lexis in Second Language Reading” 88 Sven Kristersson’s “Singing as a Means of Text Analysis” 97 Maria Bäcke’s “The Framework for University Level Text Analysis” 104 Johan Landgren’s “The Medium and the Vandal: A study of English translations of Tomas Tranströmer’s poetry” 112 Ulrica Skagert’s “Things within Things: Possible Readings of Alice Munro’s ‘The Love of a Good Woman’” 122 Yelena Makarova’s “Text Analysis as the Basis for Teaching Academic Writing” 132 Peter Svensson’s “Barn- och ungdomsutredningar ur ett språkligt perspektiv” 140 Lubomir Vladimirov Vouchev’s ” Frequently Occurring Mistakes and Linguistic Interference at High-School Level” 156 "3 The articles included in these proceedings were presented at a text analysis sympo- sium on 14 and 15 April 2014. -

The XXIX Olympic Games Beijing (National Stadium) (NED) - Friday, Aug 15, 2008
The XXIX Olympic Games Beijing (National Stadium) (NED) - Friday, Aug 15, 2008 100 Metres Hurdles - W HEPTATHLON ------------------------------------------------------------------------------------- Heat 1 - revised 15 August 2008 - 9:00 Position Lane Bib Athlete Country Mark . Points React 1 8 Laurien Hoos NED 13.52 (=PB) 1047 0.174 2 7 Haili Liu CHN 13.56 (PB) 1041 0.199 3 2 Karolina Tyminska POL 13.62 (PB) 1033 0.177 4 6 Javur J. Shobha IND 13.62 (PB) 1033 0.210 5 9 Kylie Wheeler AUS 13.68 (SB) 1024 0.180 6 1 Gretchen Quintana CUB 13.77 . 1011 0.171 7 5 Linda Züblin SUI 13.90 . 993 0.191 8 4 G. Pramila Aiyappa IND 13.97 . 983 0.406 9 3 Sushmitha Singha Roy IND 14.11 . 963 0.262 Heat 2 - revised 15 August 2008 - 9:08 Position Lane Bib Athlete Country Mark . Points React 1 2 Nataliya Dobrynska UKR 13.44 (PB) 1059 0.192 2 4 Jolanda Keizer NED 13.90 (SB) 993 0.247 3 9 Wassana Winatho THA 13.93 (SB) 988 0.211 4 7 Aryiró Stratáki GRE 14.05 (SB) 971 0.224 5 3 Julie Hollman GBR 14.43 . 918 0.195 6 5 Kaie Kand EST 14.47 . 913 0.242 7 8 Györgyi Farkas HUN 14.66 . 887 0.236 8 1 Yana Maksimava BLR 14.71 . 880 0.247 . 6 Irina Naumenko KAZ DNF . 0 Heat 3 - revised 15 August 2008 - 9:16 Position Lane Bib Athlete Country Mark . Points React 1 4 Aiga Grabuste LAT 13.78 . -

Master Schedule.Xlsx
Date Baton Rouge Berlin Morning Time Time Sex Event Round Saturday 8/15 3:05 AM 10:05 M Shot PutQualification Saturday 8/15 3:10 AM 10:10 W 100 Metres Hurdles Heptathlon Saturday 8/15 3:50 AM 10:50 W 3000 Metres Steeplechase Heats Saturday 8/15 4:00 AM 11:00 W Triple Jump Qualification Saturday 8/15 4:20 AM 11:20 W High Jump Heptathlon Saturday 8/15 4:40 AM 11:40 M 100 Metres Heats SaturdaSaturdayy 88/15/15 55:00:00 AM 12:00M Hammer Throw QQualificationualification Saturday 8/15 5:50 AM 12:50 W 400 Metres Heats Saturday 8/15 6:00 AM 13:00 M 20 Kilometres Race Walk Final Saturday 8/15 6:20 AM 13:20 M Hammer ThrowQualification Afternoon session Saturday 8/15 11:15 AM 18:15 M 1500 Metres Heats Saturday 8/15 11:20 AM 18:20 W Shot Put Heptathlon Saturday 8/15 11:50 AM 18:50 M 100 Metres Quarter-Final Saturday 8/15 12:00 PM 19:00 W Pole Vault Qualification Saturday 8/15 12:25 PM 19:25 W 10,000 Metres Final Saturday 8/15 1:15 PM 20:15 M Shot Put Final Saturday 8/15 1:20 PM 20:20 M 400 Metres Hurdles Heats Saturday 8/15 2:10 PM 21:10 W 200 Metres Heptathlon Date Baton Rouge Berlin Date Time Time Morning session Sex Event Round Sunday 8/16 3:05 AM 10:05 W Shot PutQualification Sunday 8/16 3:10 AM 10:10 W 800 Metres Heats Sunday 8/16 3:45 AM 10:45 W Javelin Throw Qualification Sunday 8/16 4:00 AM 11:00 M 3000 Metres Steeplechase Heats Sunday 8/16 4:35 AM 11:35 W Long Jump Heptathlon SundaSundayy 88/16/16 44:55:55 AM 11:11:5555 W 100 Metres Heats Sunday 8/16 5:00 AM 12:00 W 20 Kilometres Race Walk Final Sunday 8/16 5:15 AM 12:15 W Javelin Throw -

Resultados De Competencias
9th IAAF World Championships in Athletics Paris (FRA) 23-31 Aug 2003 MEN 100 metres WC Record 9.80 +0.2 Maurice GREENE USA Sevilla 22 Aug 1999 Final 25 Aug Wind: 0.0 1 Kim COLLINS 5/04/76 SKN 10.07 2 Darrel BROWN 11/10/84 TRI 10.08 3 Darren CAMPBELL 12/09/73 GBR 10.08 4 Dwain CHAMBERS 5/04/78 GBR 10.08 5 Tim MONTGOMERY 28/01/75 USA 10.11 6 Bernard WILLIAMS 19/01/78 USA 10.13 7 Deji ALIU 22/11/75 NGR 10.21 8 Echenna EMEDOLU 17/09/76 NGR 10.22 Semifinals 25 Aug Heat 1 Wind: +0.5 4 Kim COLLINS 5/04/76 SKN 10.16 Heat 2 Wind: +0.6 2 Darrel BROWN 11/10/84 TRI 10.11 5 Dwight THOMAS 23/09/80 JAM 10.19 6 Ato BOLDON 30/12/73 TRI 10.22 Quarterfinals 24 Aug Heat 2 Wind: +0.7 1 Ato BOLDON 30/12/73 TRI 10.09 4 Dwight THOMAS 23/09/80 JAM 10.23 Asafa POWELL 11/11/82 JAM DQ Heat 3 Wind: 0.0 1 Darrel BROWN 11/10/84 TRI 10.01 WRj 6 Michael FRATER 6/10/82 JAM 10.25 Heat 4 Wind: +0.6 1 Kim COLLINS 5/04/76 SKN 10.02 5 Obadele THOMPSON 30/03/76 BAR 10.14 Heats 24 Aug Heat 1 Wind: +0.7 1 Obadele THOMPSON 30/03/76 BAR 10.15 Heat 3 Wind: 0.0 2 Michael FRATER 6/10/82 JAM 10.32 Heat 5 Wind: +1.7 2 Darrel BROWN 11/10/84 TRI 10.10 Heat 8 Wind: -0.6 4 Marc BURNS 7/01/83 TRI 10.28 5 Churandy MARTINA 3/07/84 AHO 10.35 Heat 9 Wind: +0.9 1 Asafa POWELL 11/11/82 JAM 10.05 2 Kim COLLINS 5/04/76 SKN 10.09 7 Andre BLACKMAN 3/11/80 GUY 10.86 Heat 10 Wind: +0.7 2 Dwight THOMAS 23/09/80 JAM 10.22 3 Ato BOLDON 30/12/73 TRI 10.23 200 metres WC Record 19.79 +0.5 Michael JOHNSON USA Göteborg 11 Aug 1995 Final 29 Aug Wind: +0.1 1 John CAPEL 27/10/78 USA 20.30 2 Darvis PATTON 4/12/77 USA 20.31 3 Shingo SUETSUGU 2/06/80 JPN 20.38 4 Darren CAMPBELL 12/09/73 GBR 20.39 AthleCAC - Results service Page 1 5 Stéphane BUCKLAND 20/01/77 MRI 20.41 6 Joshua J. -

Download Book (PDF)
Edited by: Adam Głaz, David S. Danaher, Przemysław Łozowski The Linguistic Worldview Ethnolinguistics, Cognition, and Culture Versita Discipline: Language, Literature Managing Editor: Anna Borowska Language Editor: David S. Danaher Published by Versita, Versita Ltd, 78 York Street, London W1H 1DP, Great Britain. This work is licensed under the Creative Commons Attribution-NonCommercial- NoDerivs 3.0 license, which means that the text may be used for non-commercial purposes, provided credit is given to the author. Copyright © 2013 Wojciech Chlebda (chapter 1); Anna Pajdzińska (chapter 2); Agnieszka Gicala (chapter 3); Irena Vaňková (chapter 4); David S. Danaher (chapter 5, introduction); José Vergara (chapter 6); Anna Wierzbicka (chapter 7); Jerzy Bartmiński (chapter 8); Katarzyna Prorok (chapter 9); Stanisława Niebrzegowska- Bartmińska (chapter 10); Agata Bielak (chapter 11); Marta Nowosad-Bakalarczyk (chapter 12); Dorota Piekarczyk (chapter 13); Dorota Filar (chapter 14); Aneta Wysocka (chapter 15); Małgorzata Brzozowska (chapter 16); Elżbieta Tabakowska (chapter 17); James W. Underhill (chapter 18); Przemysław Łozowski (chapter 19, introduction); Adam Głaz (chapter 20, introduction); Agnieszka Mierzwińska- Hajnos (chapter 21); Enrique Bernárdez (chapter 22); Anna Niderla (chapter 23); Wiktoria Kudela-Świątek (chapter 24) ISBN (paperback): 978-83-7656-072-4 ISBN (hardcover): 978-83-7656-073-1 ISBN (for electronic copy): 978-83-7656-074-8 Managing Editor: Anna Borowska Language Editor: David S. Danaher Cover illustration: © istock.com/alexsl -

ETN2009 46(Wwc)Ii
Volume 8, No. 46 August 28, 2009 version ii — World Championships XII Women — BERLIN, GERMANY — By–Nation Medal Chart — AUGUST 15–23 Nation ................Men Women ....Overall ATTENDANCE Stadium capacity was listed as “56,000 plus the IAAF Fam- G S B Total G S B Total ily”; there were no morning sessions on 8/17 or 8/21–23. The United States ......6 4 4 14 4 2 2 8 ..........22 figures: 8/15—25,300/42,546; 8/16—23,300/51,113; 8/17—30,496; Jamaica ..............3 – 1 4 4 4 1 9 ..........13 8/18—19,951/29,897; 8/19—20,312/32,158; 8/20—32,514/57,937; Russia .................3 – 2 5 1 3 4 8 ..........13 8/21—42,378; 8/22—59,926 (sellout); 8/23—50,754. Kenya .................2 3 1 6 2 2 1 5 .......... 11 Germany .............1 – 2 3 1 3 2 6 ............9 WEATHER Official temperature—both F and C—and humidity readings are given Ethiopia ...............2 1 1 4 – 1 3 4 ............8 with each event. Poland ................– 3 1 4 2 1 1 4 ............8 Cuba ...................– 2 1 3 1 2 – 3 ............6 EXPLAINING THE TYPOGRAPHY Great Britain ........1 1 1 3 1 1 1 3 ............6 Paragraph breaks in the preliminary rounds of running events indicate the separation between qualifiers and non-qualifiers. Australia ..............1 – 2 3 1 – – 1 ............4 China ..................– 1 – 1 1 – 2 3 ............4 COLOR CODING Bahrain ...............1 – 1 2 1 – – 1 ............3 All medalists appear in blue ink; all Americans are in bold face and France ................– 1 2 3 – – – 0 ............3 italics (if in multiple rounds, only in the final round in which they com- South Africa ........1 1 – 2 1 – – 1 ............3 peted); field-event/multi medalists appear in either blue (gold medal), red (silver) or green (bronze) in the progression charts.