Installare Tor
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

TAZ, Ontological Anarchy, Poetic Terrorism.Pdf
T. A. Z. The Temporary Autonomous Zone, Ontological Anarchy, Poetic Terrorism By Hakim Bey Autonomedia Anti-copyright, 1985, 1991. May be freely pirated & quoted-- the author & publisher, however, would like to be informed at: Autonomedia P. O. Box 568 Williamsburgh Station Brooklyn, NY 11211-0568 Book design & typesetting: Dave Mandl HTML version: Mike Morrison Printed in the United States of America Part 1 T. A. Z. The Temporary Autonomous Zone, Ontological Anarchy, Poetic Terrorism By Hakim Bey ACKNOWLEDGMENTS CHAOS: THE BROADSHEETS OF ONTOLOGICAL ANARCHISM was first published in 1985 by Grim Reaper Press of Weehawken, New Jersey; a later re-issue was published in Providence, Rhode Island, and this edition was pirated in Boulder, Colorado. Another edition was released by Verlag Golem of Providence in 1990, and pirated in Santa Cruz, California, by We Press. "The Temporary Autonomous Zone" was performed at the Jack Kerouac School of Disembodied Poetics in Boulder, and on WBAI-FM in New York City, in 1990. Thanx to the following publications, current and defunct, in which some of these pieces appeared (no doubt I've lost or forgotten many--sorry!): KAOS (London); Ganymede (London); Pan (Amsterdam); Popular Reality; Exquisite Corpse (also Stiffest of the Corpse, City Lights); Anarchy (Columbia, MO); Factsheet Five; Dharma Combat; OVO; City Lights Review; Rants and Incendiary Tracts (Amok); Apocalypse Culture (Amok); Mondo 2000; The Sporadical; Black Eye; Moorish Science Monitor; FEH!; Fag Rag; The Storm!; Panic (Chicago); Bolo Log (Zurich); Anathema; Seditious Delicious; Minor Problems (London); AQUA; Prakilpana. Also, thanx to the following individuals: Jim Fleming; James Koehnline; Sue Ann Harkey; Sharon Gannon; Dave Mandl; Bob Black; Robert Anton Wilson; William Burroughs; "P.M."; Joel Birroco; Adam Parfrey; Brett Rutherford; Jake Rabinowitz; Allen Ginsberg; Anne Waldman; Frank Torey; Andr Codrescu; Dave Crowbar; Ivan Stang; Nathaniel Tarn; Chris Funkhauser; Steve Englander; Alex Trotter. -

“Guía Metodológica De Uso Seguro De Internet Para Personas Y Empresas Utilizando La Red Tor”
PONTIFICIA UNIVERSIDAD CATÓLICA DEL ECUADOR FACULTAD DE INGENIERÍA ESCUELA DE SISTEMAS DISERTACIÓN DE GRADO PREVIA A LA OBTENCIÓN DEL TÍTULO DE INGENIERO EN SISTEMAS Y COMPUTACIÓN “GUÍA METODOLÓGICA DE USO SEGURO DE INTERNET PARA PERSONAS Y EMPRESAS UTILIZANDO LA RED TOR” NOMBRES: Javier Andrés Vicente Alarcón Verónica Cristina Guillén Guillén DIRECTOR: Msc. Luis Alberto Pazmiño Proaño QUITO, 2015 “GUÍA METODOLÓGICA DE USO SEGURO DE INTERNET PARA PERSONAS Y EMPRESAS UTILIZANDO LA RED TOR” TABLA DE CONTENIDO RESUMEN .......................................................................................................................... 3 INTRODUCCIÓN ................................................................................................................ 6 0. ANTECEDENTES ......................................................................................................... 8 0.1. Internet .............................................................................................................. 8 0.1.1. Definición .................................................................................................... 8 0.1.2. Historia........................................................................................................ 9 0.1.3. Evolución .................................................................................................. 12 0.2. Ciberataque ...................................................................................................... 13 0.2.1. Definición ................................................................................................. -

Digital Security for Activists
Training the Motivated: Digital Security for Activists Glencora Borradaile Kelsy Kretschmer Abstract School of Electrical Engineering School of Public Policy The state of global surveillance and the political and Computer Science Sociology Program environment has many activists caring more about their Oregon State University Oregon State University online security culture. We report on the initiation of a Corvallis, OR 97331, USA Corvallis, OR 97331, USA Digital Security for Activists program and a pilot study of an [email protected] [email protected] introductory seminar. Pre- and post-surveys of the seminar will form an initial assessment of what kind of intervention might increase the security practices of activists and to inform the design of program offerings. We report on the pre-surveys from three offerings of the seminar. Introduction In collaboration with the Civil Liberties Defense Center (CLDC), the first author had been offering informal digital security trainings for activists and their lawyers. After the fall elections in the U.S., requests for these trainings increased dramatically and shortly thereafter we launched a Digital Security for Activists (DSA) program. The DSA program’s intent is to align with the CLDC mission (“to defend and uphold civil liberties through education, outreach, litigation, legal support, and assistance”) and enable citizen activists to assert their constitutional rights while organizing online. Copyright is held by the author/owner. Permission to make digital or hard copies of all or part of this work for personal or classroom use is granted without fee. Poster In order to provide trainings that are useful and effective, we presented at the 13th Symposium on Usable Privacy and Security (SOUPS 2017). -

Crypto Anarchy, Cyberstates, and Pirate Utopias Edited by Peter Ludlow
Ludlow cover 7/7/01 2:08 PM Page 1 Crypto Anarchy, Cyberstates, and Pirate Utopias Crypto Anarchy, Crypto Anarchy, Cyberstates, and Pirate Utopias edited by Peter Ludlow In Crypto Anarchy, Cyberstates, and Pirate Utopias, Peter Ludlow extends the approach he used so successfully in High Noon on the Electronic Frontier, offering a collection of writings that reflect the eclectic nature of the online world, as well as its tremendous energy and creativity. This time the subject is the emergence of governance structures within online communities and the visions of political sovereignty shaping some of those communities. Ludlow views virtual communities as laboratories for conducting experiments in the Peter Ludlow construction of new societies and governance structures. While many online experiments will fail, Ludlow argues that given the synergy of the online world, new and superior governance structures may emerge. Indeed, utopian visions are not out of place, provided that we understand the new utopias to edited by be fleeting localized “islands in the Net” and not permanent institutions. The book is organized in five sections. The first section considers the sovereignty of the Internet. The second section asks how widespread access to resources such as Pretty Good Privacy and anonymous remailers allows the possibility of “Crypto Anarchy”—essentially carving out space for activities that lie outside the purview of nation-states and other traditional powers. The Crypto Anarchy, Cyberstates, third section shows how the growth of e-commerce is raising questions of legal jurisdiction and taxation for which the geographic boundaries of nation- states are obsolete. The fourth section looks at specific experimental governance and Pirate Utopias structures evolved by online communities. -

Design Justice: Community-Led Practices to Build the Worlds We
Design Justice Information Policy Series Edited by Sandra Braman The Information Policy Series publishes research on and analysis of significant problems in the field of information policy, including decisions and practices that enable or constrain information, communication, and culture irrespective of the legal siloes in which they have traditionally been located, as well as state- law- society interactions. Defining information policy as all laws, regulations, and decision- making principles that affect any form of information creation, processing, flows, and use, the series includes attention to the formal decisions, decision- making processes, and entities of government; the formal and informal decisions, decision- making processes, and entities of private and public sector agents capable of constitutive effects on the nature of society; and the cultural habits and predispositions of governmentality that support and sustain government and governance. The parametric functions of information policy at the boundaries of social, informational, and technological systems are of global importance because they provide the context for all communications, interactions, and social processes. Virtual Economies: Design and Analysis, Vili Lehdonvirta and Edward Castronova Traversing Digital Babel: Information, e- Government, and Exchange, Alon Peled Chasing the Tape: Information Law and Policy in Capital Markets, Onnig H. Dombalagian Regulating the Cloud: Policy for Computing Infrastructure, edited by Christopher S. Yoo and Jean- François Blanchette Privacy on the Ground: Driving Corporate Behavior in the United States and Europe, Kenneth A. Bamberger and Deirdre K. Mulligan How Not to Network a Nation: The Uneasy History of the Soviet Internet, Benjamin Peters Hate Spin: The Manufacture of Religious Offense and Its Threat to Democracy, Cherian George Big Data Is Not a Monolith, edited by Cassidy R. -

Tech Security for Activists
Tech Security for Activists Dimi (Climate Action Camp / CJA Belgium) https://we.riseup.net/psi36 http://www.booki.cc/tech-tools-for-activists/ Secure electronic communication Browsing the Internet Anonymously Organising Online Securing your email Hiding Stuff on your Computer Secure electronic communication Mobile or landline phone Yes Yes* No** VoIP phone Yes Yes Yes*** Instant messaging using Off- The-Record Yes Yes Yes Skype-to-Skype call or chat Yes Yes No Email No No No Facebook chat Yes No No Crabgrass chat Yes Yes Yes Signed Email No Yes No Encrypted Email No No Yes Signed, Encrypted Email No Yes Yes * A phone call can be authenticated if you recognise the voice of the caller. ** Phone calls can be intercepted. *** VoIP calls can be routed through secure networks Browsing the Internet Anonymously HTTPS (SSL, install cacert.org root certificate) Public wifi hotspot Pay-as-you-go 3G adapter (bought w/ cash) Firefox on a GNU/Linux system Linux live CD TOR (The Onion Router) VPN (virtual private network) Tunneling (SSH) Organising Online Ways people Organise Online Social Networking Sites Instant Messaging and Twitter Email and Email lists Secure tools Crabgrass, Friendika, Diaspora IRC and Identi.ca Activist mailing lists (weakest link) aktivix.org, riseup.net, psand.net Securing your email Use BCC rather than To or CC Don©t use a commercial webmail provider (Google, Hotmail, Yahoo, ¼) Log of your mails / Termination of your account Activist mail hosting: Riseup, Aktivix or Inventati Securing your own email GPG encryption Hiding Stuff -

Journalist Security in the Digital World: a Survey Are We Using the Right Tools?
Journalist Security in the Digital World: A Survey Are We Using the Right Tools? BY JAVIER GARZA RAMOS March 2016 Journalist Security in the Digital World: A Survey ABOUT CIMA Are We Using the Right Tools? The Center for International Media Assistance MARCH 2016 (CIMA), at the National Endowment for Democracy, works to strengthen the support, raise the visibility, and improve the effectiveness of independent media development throughout the world. The center provides information, builds networks, Contents conducts research, and highlights the indispensable role independent media play in the creation and Introduction . 1 development of sustainable democracies. An important aspect of CIMA’s work is to research ways The Survey . 2 to attract additional U.S. private sector interest in and support for international media development. The Responses . 4 CIMA convenes working groups, discussions, and Going Forward . 12 panels on a variety of topics in the field of media development and assistance. The center also issues reports and recommendations based on working group discussions and other investigations. These reports aim to provide policymakers, as well as donors and practitioners, with ideas for bolstering ABOUT THE AUTHOR the effectiveness of media assistance. Javier Garza Ramos is a journalist Center for International Media Assistance based in northern Mexico. Currently National Endowment for Democracy he is developing a program on media 1025 F STREET, N.W., 8TH FLOOR WASHINGTON, DC 20004 development and press freedom in PHONE: (202) 378-9700 Latin America for the World Association FAX: (202) 378-9407 EMAIL: [email protected] of Newspapers. He was a Knight URL: http://cima.ned.org Fellow at the International Center for Journalist specializing in journalist Mark Nelson SENIOR DIRECTOR protection and digital security. -

OSINT Handbook September 2020
OPEN SOURCE INTELLIGENCE TOOLS AND RESOURCES HANDBOOK 2020 OPEN SOURCE INTELLIGENCE TOOLS AND RESOURCES HANDBOOK 2020 Aleksandra Bielska Noa Rebecca Kurz, Yves Baumgartner, Vytenis Benetis 2 Foreword I am delighted to share with you the 2020 edition of the OSINT Tools and Resources Handbook. Once again, the Handbook has been revised and updated to reflect the evolution of this discipline, and the many strategic, operational and technical challenges OSINT practitioners have to grapple with. Given the speed of change on the web, some might question the wisdom of pulling together such a resource. What’s wrong with the Top 10 tools, or the Top 100? There are only so many resources one can bookmark after all. Such arguments are not without merit. My fear, however, is that they are also shortsighted. I offer four reasons why. To begin, a shortlist betrays the widening spectrum of OSINT practice. Whereas OSINT was once the preserve of analysts working in national security, it now embraces a growing class of professionals in fields as diverse as journalism, cybersecurity, investment research, crisis management and human rights. A limited toolkit can never satisfy all of these constituencies. Second, a good OSINT practitioner is someone who is comfortable working with different tools, sources and collection strategies. The temptation toward narrow specialisation in OSINT is one that has to be resisted. Why? Because no research task is ever as tidy as the customer’s requirements are likely to suggest. Third, is the inevitable realisation that good tool awareness is equivalent to good source awareness. Indeed, the right tool can determine whether you harvest the right information. -

Intro Some General Sources/Big Thanks
Guide: Anonymity and Privacy for Advanced Linux Users Created by: beac0n brought to you by DeepDotWeb.com Intro The goal is to bring together enough information in one document for a beginner to get started. Visiting countless sites, and combing the internet for information can make it obvious your desire to obtain anonymity, and lead to errors, due to conflicting information. Every effort has been made to make this document accurate. This guide is image heavy so it may take some time to load via Tor. Some general sources/Big Thanks For more general guides checkout: EFF Surveillance Self-Defense project Riseup.net Security Guide Security in a box TAILS Documentation – for those looking for a solid starting place TAILS OS is a great choice. Thanks! securityinabox.org Deepdotweb.com EFF and EPIC riseup.net For educational purposes. Not legal advice or call to action. Table of Contents 1 Intro 2 Some general sources/Big Thanks 3 Technical Information 3.1 Strong Passwords 3.2 Internet Connectivity 3.2.1 Firewall 3.2.2 Changing MAC Address 3.2.3 Intrustion Detection 3.2.4 Disk Encryption 3.2.5 Browsers 3.2.6 Router Configuration 3.2.7 Anonymity Networking 3.2.8 VPN 3.2.9 Proxy Chains 3.3 Operating Systems 3.3.1 Flash Firmware 3.3.2 Enabling a BIOS boot password 3.3.3 USB Bootable Operating Systems: 3.3.4 Linux (image files can be found at http://distrowatch.org) 3.4 Secure Data-Wiping Linux 3.5 Physical Destruction 3.6 Cold-Boot Attack 3.7 Basic Communications 3.7.1 Images 3.7.2 Email Providers 3.7.3 Jabber_XMPP/OTR 3.7.4 Alternative Messaging Options 3.8 GNUPG/PGP Basics 3.8.1 TAILS PGP 3.8.2 Additional reading on PGP 3.8.3 PGP Versions 3.9 Validating Files with MD5 or SHA1: 3.9.1 SHA1 Sum 3.9.2 MD5 Sum Technical Information Strong Passwords It’s difficult to remember many passwords. -
02 Anonimato Con Tor (PDF)
Comunicaciones Seguras Anonimato con Tor Rafael Bonifaz: [email protected] 1/18 ¿Por qué anonimato en Internet? ● Toda actividad en Internet deja huella ● Dirección IP ● Ubicación geográfica ● Búsquedas asociadas a una persona ● Hacer denuncias ● Filtrar información a Wikileaks ● Mucho más 2/18 Opciones de anonimato ● Tor es la opción más reconocida y funciona solo con TCP ● I2P cumple objetivos similares a Tor, pero técnicamente diferente ● Soporta TCP y UDP ● FreeNet es red de distribución de información descentralizada, resistente a la censura ● VPNs 3/18 ¿Cómo Funciona Tor? 4/18 Sin Tor y sin HTTPS https://www.eff.org/pages/tor-and-https 5/18 Con HTTPS y sin Tor https://www.eff.org/pages/tor-and-https 6/18 Con Tor y sin HTTPS https://www.eff.org/pages/tor-and-https 7/18 Con Tor y sin HTTPS https://www.eff.org/pages/tor-and-https 8/18 Tor y servicios ocultos ● Existen sitios del tipo http://abcxyz.onion que son accesibles solo a través de Tor ● La comunicación es siempre cifrada ● Parte importante de la Deepweb, Darknet, etc. ● El servidor nunca sabe desde donde se conectan los clientes ● La ubicación del servidor es secreta ● Wikileaks: http://wlupld3ptjvsgwqw.onion 9/18 Tor permite ocultar metadata 10/18 La NSA y Tor ● Tor es financiado principalmente por el gobierno de EEUU ● Tor es software libre ● Tor es una red con miles de nodos ● Los nodos se seleccionan de forma aleatoria en el cliente ● Según presentación filtrada por Snowden para la NSA “Tor Stincks” 11/18 La NSA y Tor https://edwardsnowden.com/2013/10/04/tor-stinks-presentation/ -

The Onion Crate - Tor Hidden Service Index
onion.to does not host this content; we are simply a conduit connecting Internet users to content hosted inside the Tor network.. onion.to does not provide any anonymity. You are strongly advised to download the Tor Browser Bundle and access this content over Tor. For more information see our website for more details and send us your feedback. hide Tor2web header Online onions The Onion Crate - Tor Hidden Service Index nethack3dzllmbmo.onion A public nethack server. j4ko5c2kacr3pu6x.onion/wordpress Paste or blog anonymously, no registration required. redditor3a2spgd6.onion/r/all Redditor. Sponsored links 5168 online onions. (Ctrl-f is your friend) A AUTOMATED PAYPAL AND CREDIT CARD MARKET 2222bbbeonn2zyyb.onion A Beginner Friendly Comprehensive Guide to Installing and Using A Safer yuxv6qujajqvmypv.onion A Coca Growlog rdkhliwzee2hetev.onion ==> https://freenet7cul5qsz6.onion.to/freenet:USK@yP9U5NBQd~h5X55i4vjB0JFOX P97TAtJTOSgquP11Ag,6cN87XSAkuYzFSq-jyN- 3bmJlMPjje5uAt~gQz7SOsU,AQACAAE/cocagrowlog/3/ A Constitution for the Few: Looking Back to the Beginning ::: Internati 5hmkgujuz24lnq2z.onion ==> https://freenet7cul5qsz6.onion.to/freenet:USK@kpFWyV- 5d9ZmWZPEIatjWHEsrftyq5m0fe5IybK3fg4,6IhxxQwot1yeowkHTNbGZiNz7HpsqVKOjY 1aZQrH8TQ,AQACAAE/acftw/0/ A Declaration of the Independence of Cyberspace ufbvplpvnr3tzakk.onion ==> https://freenet7cul5qsz6.onion.to/freenet:CHK@9NuTb9oavt6KdyrF7~lG1J3CS g8KVez0hggrfmPA0Cw,WJ~w18hKJlkdsgM~Q2LW5wDX8LgKo3U8iqnSnCAzGG0,AAIC-- 8/Declaration-Final%5b1%5d.html A Dumps Market - Dumps, Cloned Cards, -
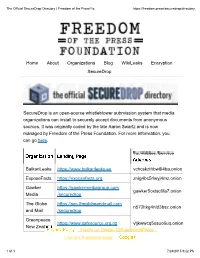
Home About Organizations Blog Wikileaks Encryption Securedrop Securedrop Is an Open-Source Whistleblower Submission System That
The Official SecureDrop Directory | Freedom of the Press Fo... https://freedom.press/securedrop/directory Home About Organizations Blog WikiLeaks Encryption SecureDrop SecureDrop is an open-source whistleblower submission system that media organizations can install to securely accept documents from anonymous sources. It was originally coded by the late Aaron Swartz and is now managed by Freedom of the Press Foundation. For more information, you can go here. Tor Hidden Service Organization Landing Page Address BalkanLeaks https://www.balkanleaks.eu vchcskzthbw6l4ba.onion ExposeFacts https://exposefacts.org znig4bc5rlwyj4mz.onion Gawker https://gawkermediagroup.com gawker5oxtsc6fa7.onion Media /securedrop The Globe https://sec.theglobeandmail.com n572ltkg4nld3bsz.onion and Mail /securedrop Greenpeace https://www.safesource.org.nz vtjkwwcq5osuo6uq.onion New Zealand 1 of 3 7/28/2015 9:22 PM The Official SecureDrop Directory | Freedom of the Press Fo... https://freedom.press/securedrop/directory The freepress3xxs3hk.onion https://securedrop.theguardian.com 33y6fjyhs3phzfjj.onion Guardian https://firstlook.org/theintercept ThisThe workIntercept is licensed under a Creative Commons Attributiony6xjgkgwj47us5ca.onion 4.0 International /securedrop License NEOSleaks https://neos.eu/leaks/ udrciweihl4qe63p.onion B89A29DB2128160B8E4B1B4CBADDE0C7FC9F6818 (master signing The New https://projects.newyorker.com key—not for communication) strngbxhwyuu37a3.onion Yorker /strongbox NRKbeta https://nrkbeta.no/tips swdi5ymnwmrqhycl.onion Project On Gov't https://securedrop.pogo.org