Part 2 / Software
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

0. Versã…O Final
Câmpus de São José do Rio Preto Fernando Henrique Crepaldi Cordeiro O romance policial contemporâneo pelos caminhos da paródia: uma vertente metalinguística São José do Rio Preto 2014 Fernando Henrique Crepaldi Cordeiro O romance policial contemporâneo pelos caminhos da paródia: uma vertente metalinguística Tese apresentada como parte dos requisitos para obtenção do título de Doutor em Letras, junto ao Programa de Pós-Graduação em Letras, Área de Concentração – Teoria da Literatura, do Instituto de Biociências, Letras e Ciências Exatas da Universidade Estadual Paulista “Júlio de Mesquita Filho”, Câmpus de São José do Rio Preto. Orientador: Profª Drª Sônia Helena de Oliveira Raymundo Piteri São José do Rio Preto 2014 Fernando Henrique Crepaldi Cordeiro O romance policial contemporâneo pelos caminhos da paródia: uma vertente metalinguística Tese apresentada como parte dos requisitos para obtenção do título de Doutor em Letras, junto ao Programa de Pós-Graduação em Letras, Área de Concentração – Teoria da Literatura, do Instituto de Biociências, Letras e Ciências Exatas da Universidade Estadual Paulista “Júlio de Mesquita Filho”, Câmpus de São José do Rio Preto. Comissão Examinadora Profª Drª Sônia Helena de Oliveira Raymundo Piteri UNESP – São José do Rio Preto Orientador Profª Drª Marisa Corrêa Silva Universidade Estadual de Maringá Profª Drª Márcia Valéria Zamboni Gobbi UNESP – Araraquara Profª Drª Maria Heloísa Martins Dias UNESP – São José do Rio Preto Prof. Dr. Arnaldo Franco Júnior UNESP – São José do Rio Preto São José do Rio Preto -

TRS-80 Software
REGISTRATION NUMBER 00000001 NEWDOS 8O FOR THE TRS-80 MODEL I / III / 4 MICRO COMPUTER Apparat Incorporated takes pleasure in presenting NEWDOS/80, Version 2.5. Above is the registration number of your NEWDOS/80. This registration number must be the same as the registration number you find on your diskette label and the enclosed registration card. If they are not, return them to the dealer from whom you purchased your NEWDOS/80 to be reissued. This registration Number is your assurance of receiving any corrections or minor revisions to NEWDOS/80 that may be released. The registration card should be completed and returned to Apparat at your earliest convenience. PLEASE RETURN THE CARD IT IS IMPORTANT! It our only method of determining who has purchased this copy of the system. This number should be included in all correspondence with Apparat. Apparat, Inc 4401 So. Tamarac Parkway • Denver, Colorado 80237 HELPFUL HINTS IN USING YOUR NEWDOS/80 VERSION 2.5 We suggest using the following checklist as a guide to setting up software on your Hard Disk System: 1. Carefully read through all related documentation. 2. Make hardware installation as directed by instructions supplied with your Hard Drive Unit. 3. Boot on your NEWDOS/80 Version 2.5 original master diskette and make backup copy or copies. Refer to Chapter 1, Section 1.4 of the NEWDOS/80 Version 2.0 manual for details if unfamiliar with the procedure. 4. Designate one of your backups as a working copy an d boot (or reset) on it. Use this diskette for the remainder of this procedure. -

Windows in Concurrent PC
Using Concurrent PC DOS OTHER BOOKS BY THE AUTHOR Microcomputer Operating Systems (1982) The Byte Guide to CP/M-86 (1984) Using Concurrent PC DOS Mark Dahmke McGraw-Hili Book Company New York St. Louis San Francisco Auckland Bogota Hamburg Johannesburg London Madrid Mexico Montreal New Delhi Panama Paris Sao Paulo Singapore Sydney Tokyo Toronto Library of Congress Cataloging-in-Publication Data Dahmke, Mark. U sing Concurrent PC DOS. Bibliography: p. Includes index. 1. Concurrent PC DOS (Computer operation system) 1. Title. QA76.76.063D34 1986 005.4' 469 85-15473 ISBN 0-07-015073-7 Copyright © 1986 by McGraw-Hili, Inc. All rights reserved. Printed in the United States of America. Except as permitted under the United States Copyright Act of 1976, no part of this publication may be reproduced or distributed in any form or by any means, or stored in a data base or retrieval system, without the prior written permission of the publisher. 1234567890 DOC/DOC 893210876 ISBN 0-07-015073-7 The editors for this book were Steven Guty and Vivian Koenig, the designer was Naomi Auerbach, and the production supervisor was Teresa F. Leaden. It was set in Century Schoolbook by Byrd Data Imaging. Printed and bound by R. R. Donnelley & Sons Company. To my sister Patricia Contents Chapter 1. Introduction 1 What Is Concurrent PC DOS? 1 What Is an Operating System? 1 The DOS Family Tree 3 The Scope of This Book 5 Chapter 2. Concurrent PC DOS Compatibility 6 Concurrent PC DOS Compatibility 6 PC·DOS, TopView, and the IBM PC AT 7 Concurrent CP/M·86 9 Chapter 3. -

The Computer for Practice Management: Part 2
Computers in Family Practice Editor: Roger A. Rosenblatt, MD, MPH The Computer for Practice Management: Part 2. Software, Hardware, and Aftermarket Services Matthew Cushing, Jr, MD Andover, Massachusetts il field? Second, is it possible to get the names of In the preceding issue, Dr. Cushing introduced the e primary care people with whom he has dealt? importance o f system goals and design, hardware, enerally speaking, the broader the range of hard- elements of the system, and software elements. are brands offered, the wider the choice of soft- In Part 2, Dr. Cushing covers how to search for are available. One-brand stores have a limited the right software, how to fit the hardware to the ilection and probably should not be consulted software, and aftermarket services.—Roger A. itially. It is also wise to avoid mail-order prod- Rosenblatt, Editor ;ts entirely. These products are less expensive, at the headache factor in trying to deal with prob e s and questions at long distance more than jmpensates for any savings. Delays of three to How to Find the Right Software ve months are not unknown in response to letters f inquiry to major and reputable hardware and Finding the right software dealer may be the jftware manufacturers. Avoid also the ‘‘supei- hardest part of the whole process. Advertising is larket” stores, which thrive on volume and quick of little use, other than to make buyers aware of rmover and are not equipped, either in personne the existence of an outlet and what brands of r attitude, for hand-holding. -

Trsdos 1.3 Reference Guide
TRSDOS 1.3 REFERENCE GUIDE TRSDOS 1.3 Command Syntax 1. The general form of each command is given as the command itself, followed by the input/output field, followed by the parameters field. The parameter field and certain portions of the I/O field are optional and may be included at the discretion of the operator. 2. Capital letters and spaces in the command lines must be typed exactly as shown. 3. Brackets in the command line indicate that the instruction contained within the brackets is optional and may or may not be entered, depending on the situation and the user's desire for clarity. 4. Parentheses indicate the parameter field. This field is composed of those parameters that will modify the action of the command to suit the user's needs. 5. Braces indicate the default values of a paramter or a prompt. If <ENTER> is typed instead of the the value or switch required, the default is used. 6. The parameter values are indicated by val (value), exp (expression), or sw (switch). Sample numeric values, string expressions, or switch indicators are usually given. 7. File specifications take the following format: filespec/ext.password:d filespec - an alphabetic character A-Z followed by up to seven optional characters or numbers /ext - optional file specification extension, consisting of an alphabetic character and up to two optional characters or numbers .password - optional file password consisting of an alphabetic character followed by up to seven optional characters or numbers :d - optional drive specification, which indicates the drive on which the file is located TRSDOS 1.3 Hardware Features: 1. -

A Review of Federal Agency Experiences NATIONAL BUREAU of STANDARDS
NAT'L INST. OF STAND & TECH NB3 Reference Publi - cations AlllQb DMDSSB of Commerce . Science National Bureau and Technology of Standards NBS Special Publication 500-102 Microcomputers: A Review of Federal Agency Experiences NATIONAL BUREAU OF STANDARDS The National Bureau of Standards' was established by an act ot Congress on March 3, 1901. The Bureau's overall goal is to strengthen and advance the Nation's science and technology and facilitate their effective application for public benefit. To this end, the Bureau conducts research and provides: (1) a basis for the Nation's physical measurement system, (2) scientific and technological services for industry and government, (3) a technical basis for equity in trade, and (4) technical services to promote public safety. The Bureau's technical work is per- formed by the National Measurement Laboratory, the National Engineering Laboratory, and the Institute for Computer Sciences and Technology. THE NATIONAL MEASUREMENT LABORATORY provides the national system of physical and chemical and materials measurement; coordinates the system with measurement systems of other nations and furnishes essential services leading to accurate and uniform physical and chemical measurement throughout the Nation's scientific community, industry, and commerce; conducts materials research leading to improved methods of measurement, standards, and data on the properties of materials needed by industry, commerce, educational institutions, and Government; provides advisory and research services to other Government -

Microsoft BASIC Decoded & Other Mysteries
Written by James Farvour Microsoft BASIC Decoded & Other Mysteries Foreword by Harvard Pennington Edited by Jim Perry Graphics by John Teal Cover by Harvard Pennington TRS-80 Information Series Volume 2 Contents Foreword .............................................................................4 Single Precision Routines..............................................21 Chapter 1: Introduction .......................................................5 SP Addition ...............................................................22 Overview.........................................................................6 SP Subtraction...........................................................22 Memory Utilization .........................................................6 SP Multiply ...............................................................22 Communications Region .................................................8 SP Divide ..................................................................22 Level II Operation ...........................................................8 SP Comparison..........................................................22 Input Phase ......................................................................8 Double Precision Routines ............................................22 Interpretation & Execution..............................................9 DP Addition...............................................................22 Verb Action...................................................................11 DP Subtraction ..........................................................23 -

Radio Shack Collection
http://oac.cdlib.org/findaid/ark:/13030/c8d50t54 No online items Guide to the Radio Shack collection Finding aid prepared by Jack Doran and Sara Chabino Lott Processing of this collection was made possible through generous funding from the National Archives’ National Historical Publications & Records Commission: Access to Historical Records grant. Computer History Museum 1401 N. Shoreline Blvd. Mountain View, CA, 94043 (650) 810-1010 [email protected] October 2019 Guide to the Radio Shack X4114.2007 1 collection Title: Radio Shack collection Identifier/Call Number: X4114.2007 Contributing Institution: Computer History Museum Language of Material: English Physical Description: 34.59 Linear feet24 record cartons, 4 software boxes, and 1 manuscript box Date (bulk): Bulk, 1979-1985 Date (inclusive): 1973-1993 Abstract: The Radio Shack collection contains materials related to Tandy Corporation/Radio Shack’s microcomputer, the TRS-80. The Manuals series consists of manuals published by Tandy and others concerned with the TRS-80 and also programs authored by Radio Shack and other companies. The Software series consists largely of hand labeled disks containing utilities, operating system tools, games, and write up language programs. The Periodicals series consists of print periodicals about the TRS-80 and its programs published by Tandy and other companies. Processing Information Collection surveyed by Rita Wang, 2016. Collection processed by Jack Doran, October 2019. Access Restrictions The collection is open for research. Publication Rights The Computer History Museum (CHM) can only claim physical ownership of the collection. Copyright restrictions may apply and users are responsible for satisfying any claims of the copyright holder. Requests for copying and permission to publish, quote, or reproduce any portion of the Computer History Museum’s collection must be obtained jointly from both the copyright holder (if applicable) and the Computer History Museum as owner of the material. -

Elementary Education Agencies, School Administrators, Teachers
DOCUMENT RESUME ED 238 895 TM 830 717 AUTHOR Lockheed, Marlaine E.; And Others TITLE Computer Literacy: Definition and Survey Items for Assessment in Schools. INSTITUTION Educational Testing Service., Princeton, N.J.; Human Resources Research Organization, Alexandria, Va.; Instructional Computing, Inc., Minneapolis, MN. SPONS AGENCY National Center for Education Statistics (ED), Washington, DC. PUB DATE Sep 83 CONTRACT 400 -82 -004 NOTE 222p. PUB TYPE Reports - Research/Technical (143) -- Tests /Evaluation Iffstruments (160) EDRS PRICE. MF01/PC09 Plus Postage. DESCRIPTORS *Computer Literacy; Curriculum Development; *Data CollectionrElementary School Students; Elementary School Teachers; Elementary Secondary Education; Glossaries; *Item Banks; *Needs Assessment; Principals; *School Surveys; Secondary School Students; Secondary School Teachers; Superintendents; Test Items; Test Validity ABSTRACT This project presents a pool of questions that can be used-in surveys to provide data that would enable state and local education agencies, school administrators, teachers, parents, and the computer industry to make better informed decisions regarding: (1) curriculum planning and implementation in elementary and secondary school; (2) design of inservice and preservice training programs for teachers and administrators; (3) development of educational computer equipment, software, and computer-related learning materials; and (4) evaluation and selection of computer equipment, software, and learning materials. The pool of questions contain three different types. The first type is the survey item that asks the respondent about his or her computer-related knowledge, skills, experience, and use. The second type is the validation item whose purpose is to objectively validate the survey items. The third type is the _inventory-item-that-seeks information-regarding-computer-related resources in the district, school, or classroom. -

Summary of Commands
1616: Quick Reference Guide Version 4.059 August 1993 Applix 1616 microcomputer project Applix pty limited Lot 1, Kent St., Yerrinbool, NSW 2575 1 Appl x 1616 Computer System Do you want a standard MS-DOS or Macintosh computer system full of custom ASIC chips and undocumented features? Do you want to deal with sales people who know little more than the price of the computer? Do you want to buy expensive programs, and then find the dealer knows nothing that isn’t obvious from the manual. If so, don’t bother to read this. Or do you like to understand every single chip in your system, have every function accessible and changeable, and have interface facilities readily available? If you have a difficult problem, would you like to talk to the person who designed the computer? Would you like to read the source code for the programs you are using? Would you like to build your own custom computer, or have one assembled to suit your needs? The Applix 1616 is an Australian designed and built computer system for engineers, programmers, advanced students, and DIY enthusiasts. Particularly suited to custom interfaces, industrial control, andeducation, itmakes a finegeneral purpose personal computer system. Provides a powerful EPROM resident multiuser, multitasking operating system, not unlike Unix, with lots of interface facilities. Accepts industry standard peripherals, no hard to get add-ons. Built with common TTL and LSI electronic components, no special parts (except for two 16R8 PAL chips). All facilities open and accessible from C, assembler, Forth, BASIC, or straight from the keyboard. -

ED 192Ale IR 000 906 AUTHOR () Frederick, Franz 4
DOCUMENT RESUME ED 192ale IR 000 906 AUTHOR () Frederick, Franz 4. TITLE Guide to Microcomputers. INSTITUTION Association for Educational Communications and Technology, Washington, D.C.: ERIC Clearinghouse on Information Resources, Syracuse, N.Y. SPONS AGENCY National Inst. of Education (DHEW), Washington, D.C. EEPORT NO ISBN-0-89240-030-2 PUB LATE SO CONTRACT 400-77-0015 NOTE 159p. AVAILABLE PRCMAECT Publications Sales, 1126 16th Street NW, Washington, DC 20036 ($9.50/AECT members: $11,50/non-members). TDES PRICE MF01/PC07 Plus Postage. DESCRIPTORS *Computer Assisted Instruction: Computer Graphics: *Computer Managed Instruction: Equipment Maintenance: *Microcomputers: *Minicomputers: *Programing Languages: Videodisc Recordings ABSTRACT This comprehensive guide to microcomputers and their role Ln education discusses the general nature of microcomputers: computer languages in simple English: operating systems and what they can do for you: compatible systems: special accessories: service and maintenance: computer assisted instruction, computer managed instruction, and computer graphics: time sharing and resource sharing: Potential instructional and media center applications: and special applications, e.g., eleqtronic mail, networks, and videodiscs. Available resources are presented in a bibliography of magazines and journals about microcomputers and software and their uses, a selected list of companies specializing in creating specialized languages and applications programs for microcomputers, and a selected list of companies specializing in the preparation of educational programs for use on microcomputers. (CNC) *********************************************************************** * Reproductions supplied by EDRS ari the best that can be made * * from the original document,. *********************.************************************************* U S010Ail1iNtNIOF HEALTH. ltOUCAt*ON VOW AN' 14A t ioNat. INSSIFUlt OF IOUCAtiON o,M0 Nt 1, A'. It( 11.Nf 1,141, 1 IMP,A OW (IIM A /y WI I ly. -
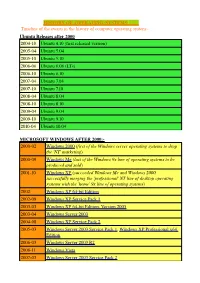
HISTORY of OPERATING SYSTEMS Timeline of The
HISTORY OF OPERATING SYSTEMS Timeline of the events in the history of computer operating system:- Ubuntu Releases after 2000 2004-10 Ubuntu 4.10 (first released version) 2005-04 Ubuntu 5.04 2005-10 Ubuntu 5.10 2006-06 Ubuntu 6.06 (LTs) 2006-10 Ubuntu 6.10 2007-04 Ubuntu 7.04 2007-10 Ubuntu 7.10 2008-04 Ubuntu 8.04 2008-10 Ubuntu 8.10 2009-04 Ubuntu 9.04 2009-10 Ubuntu 9.10 2010-04 Ubuntu 10.04 MICROSOFT WINDOWS AFTER 2000:- 2000-02 Windows 2000 (first of the Windows server operating systems to drop the ©NT© marketing) 2000-09 Windows Me (last of the Windows 9x line of operating systems to be produced and sold) 2001-10 Windows XP (succeeded Windows Me and Windows 2000, successfully merging the ©professional© NT line of desktop operating systems with the ©home© 9x line of operating systems) 2002 Windows XP 64-bit Edition 2002-09 Windows XP Service Pack 1 2003-03 Windows XP 64-bit Edition, Version 2003 2003-04 Windows Server 2003 2004-08 Windows XP Service Pack 2 2005-03 Windows Server 2003 Service Pack 1, Windows XP Professional x64 Edition 2006-03 Windows Server 2003 R2 2006-11 Windows Vista 2007-03 Windows Server 2003 Service Pack 2 2007-11 Windows Home Server 2008-02 Windows Vista Service Pack 1, Windows Server 2008 2008-04 Windows XP Service Pack 3 2009-05 Windows Vista Service Pack 2 2009-10 Windows 7(22 occtober 2009), Windows Server 2008 R2 EVENT IN HISTORY OF OS SINCE 1954:- 1950s 1954 MIT©s operating system made for UNIVAC 1103 1955 General Motors Operating System made for IBM 701 1956 GM-NAA I/O for IBM 704, based on General Motors