Chapter 1 - Overview
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Running ML/DL Workloads Using Red Hat Openshift Container Platform V3.11 Accelerate Your ML/DL Projects Platform Using Kubeflow and NVIDIA Gpus
Running ML/DL Workloads Using Red Hat OpenShift Container Platform v3.11 Accelerate your ML/DL Projects Platform using Kubeflow and NVIDIA GPUs January 2021 H17913.2 White Paper Abstract This white paper describes how to deploy Kubeflow v0.5 on Red Hat OpenShift Container Platform and provides recommendations for achieving optimal performance for ML/DL workloads using the latest NVIDIA Tesla GPUs. Dell Technologies Solutions Copyright The information in this publication is provided as is. Dell Inc. makes no representations or warranties of any kind with respect to the information in this publication, and specifically disclaims implied warranties of merchantability or fitness for a particular purpose. Use, copying, and distribution of any software described in this publication requires an applicable software license. Copyright © 2021 Dell Inc. or its subsidiaries. All Rights Reserved. Dell Technologies, Dell, EMC, Dell EMC and other trademarks are trademarks of Dell Inc. or its subsidiaries. Intel, the Intel logo, the Intel Inside logo and Xeon are trademarks of Intel Corporation in the U.S. and/or other countries. Other trademarks may be trademarks of their respective owners. Published in the USA 01/21 White Paper H17913.2. Dell Inc. believes the information in this document is accurate as of its publication date. The information is subject to change without notice. 2 Running ML/DL Workloads Using Red Hat OpenShift Container Platform v3.11 Accelerate your ML/DL Projects Platform using Kubeflow and NVIDIA GPUs White Paper Contents Contents Executive summary ........................................................................................................................ 4 Solution architecture ...................................................................................................................... 6 GPU accelerated TensorFlow training using TFJobs .................................................................. 9 Installing the GPU device plug-in ............................................................................................... -

SPARTAN ILY Fee Hikes May Stop KEEPING FIT and EDUCATED
VOLUME 108, NO. 88 TUESDAY MAY 6. 1 9 9 7 INSIDE * INSIDE a IS ell Spirit of friendship goes 4,#..sk The Offspring gives its.. w leehi beyond competition dose of alternative rock(---' Page 5 1" -V-- Page 8 Ma Ser San Jose State University Since 1 93 .1 SPARTAN ILY Fee hikes may stop KEEPING FIT AND EDUCATED By Dennis Knight said Ducheny, the chair of the Spartan Daily Stuff Write, Assembly Budget Committee, in a press release. "Not only would AB 01 pay Students who are tired 1318 hold the line on fee hikes for at California ing exorbitant fees die rest of the decade, but it would soon find relief if universities may give working families the opportu- Act of the College Affordability nity to plan and save for their chil- the 1997 makes its way through dren's education." State Assembly. Besides freezing fees until the Written by Assemblywoman turn of the century, AB 1318 (D - Denise Moreno Ducheny would limit student fee increases Vista), the bill, known as Chula after the year 2000 to no more AB 1318. would freeze student fees than the rise in personal income University, in the t ..difornia State from the prior year. The bill would California and University of also express the intent of the legis- College California Community lature to financially support public the year 2000. systems until colleges based on growth in enroll- continues in the spirit "This act ment and personal income, accord- 1960 in mak- of the Master Plan of ing to Ducheny. as essible ing our public colleges Currently, the cost for students by laying out a rational and pre- dictable policy for student lees," See Fees, page 5 It's standing room only in the Washington Square Hall let, ture room as author Anne Lamott speaks to SJSU students Friday afternoon. -

Ubuntu: Unleashed 2017 Edition
Matthew Helmke with Andrew Hudson and Paul Hudson Ubuntu UNLEASHED 2017 Edition 800 East 96th Street, Indianapolis, Indiana 46240 USA Ubuntu Unleashed 2017 Edition Editor-in-Chief Copyright © 2017 by Pearson Education, Inc. Mark Taub All rights reserved. Printed in the United States of America. This publication is protected Acquisitions Editor by copyright, and permission must be obtained from the publisher prior to any prohib- Debra Williams ited reproduction, storage in a retrieval system, or transmission in any form or by any means, electronic, mechanical, photocopying, recording, or likewise. For information Cauley regarding permissions, request forms and the appropriate contacts within the Pearson Managing Editor Education Global Rights & Permissions Department, please visit www.pearsoned.com/ permissions/. Sandra Schroeder Many of the designations used by manufacturers and sellers to distinguish their Project Editor products are claimed as trademarks. Where those designations appear in this book, and Lori Lyons the publisher was aware of a trademark claim, the designations have been printed with initial capital letters or in all capitals. Production Manager The author and publisher have taken care in the preparation of this book, but make Dhayanidhi no expressed or implied warranty of any kind and assume no responsibility for errors or omissions. No liability is assumed for incidental or consequential damages in Proofreader connection with or arising out of the use of the information or programs contained Sasirekha herein. Technical Editor For information about buying this title in bulk quantities, or for special sales opportunities (which may include electronic versions; custom cover designs; and content José Antonio Rey particular to your business, training goals, marketing focus, or branding interests), Editorial Assistant please contact our corporate sales department at [email protected] or (800) 382-3419. -

Application Development with Azure
Application Development with Azure Karim Vaes Specialist – Azure Application Development 0032 497 219577 @kvaes Agenda • Kubernetes Kubernetes Kubernetes momentum “By 2020, more than 50% of enterprises Larger companies will run mission-critical, containerized are leading the cloud-native applications in production.” adoption. 77% For the organizations running Kubernetes today, 77%1 of those with more than 1,000 developers are running it in production. 1Heptio: state of Kubernetes 2018 What’s behind the growth? Kubernetes: the leading orchestrator shaping the future app development and management It’s widely used It’s vendor-neutral It’s community-supported Kubernetes is in production for A variety of cloud providers There’s a huge community of active global companies across industries1 offer robust Kubernetes support contributors supporting Kubernetes3 24,000 1.1 million contributors contributions since 2016 since 2016 1Kubernetes.io. “Kubernetes User Case Studies.” 2CNCF. “Kubernetes Is First…” 3CNCF. Keynote address. Azure Kubernetes Service (AKS) Ship faster, operate easily, and scale confidently with managed Kubernetes on Azure Manage Kubernetes Accelerate Build on an Run anything, with ease containerized enterprise-grade, anywhere development secure foundation Top scenarios for Kubernetes on Azure Lift and shift Machine Microservices IoT Secure DevOps to containers learning Cost saving Agility Performance Portability Automation without refactoring Faster application Low latency Build once, Deliver code faster and your app development processing run anywhere securely at scale Azure Kubernetes momentum Trusted by thousands of customers 30x Azure Kubernetes Service usage grew 30x since it was made generally available in June 2018 Dated November 2018 How Kubernetes works Kubernetes control Worker node Internet kubelet kube-proxy 1. -

Running Large-Scale Machine Learning Experiments in the Cloud
O’REILLY Artificial Intelligence Conference, San Jose 2019 Running large-scale machine learning experiments in the cloud Shashank Prasanna, Amazon Web Services @shshnkp September 12, 2019 © 2019, Amazon Web Services, Inc. or its Affiliates. All rights reserved. Agenda • Machine Learning, experiments and the scientific method • Scaling challenges with machine learning setups • Containers technologies for large-scale machine learning • Demo 1: Hyperparameter optimization with Amazon SageMaker • Demo 2: Custom designed experiments with Amazon SageMaker • Demo 3: Hyperparameter optimization with Kubernetes, Kubeflow and Katib • Summary and additional resources © 2019, Amazon Web Services, Inc. or its Affiliates. All rights reserved. Experimentation in machine learning Data acquisition Data preparation for Design and run curation and labeling training experiments Model optimization Distributed Deployment and validation training © 2019, Amazon Web Services, Inc. or its Affiliates. All rights reserved. Why do we run experiments? The scientific method Question Hypothesis empirical procedure to determine Experiment whether observations agree or conflict with our hypothesis Interpret Iterate © 2019, Amazon Web Services, Inc. or its Affiliates. All rights reserved. Why do we run machine learning experiments? Machine learning researcher may want to: Question • Identify factors that affect model performance Hypothesis • Explain the root causes of performance Experiment • Choose between alternate models Interpret • Study variability and robustness of -

Instalacion Juju
Universidad Nacional de Quilmes Laboratorio de Sistemas Operativos y Redes Trabajo Práctico JUJU - UBUNTU Elaborado: Gabriel Angel Garcia Descripción del proyecto: Juju (antes Ensemble ) es una herramienta de gestión de implementacion de servicios desarrollada por Canonical Ltd. Es un proyecto de software libre presentado en Launchpad y liberado bajo la licencia pública general de Affero (AGPL). Juju se concentra en la noción del servicio, abstrayendo la noción de la máquina o el servidor, y define las relaciones entre aquellos servicios que son actualizados automáticamente cuando dos servicios relacionados observan una modificación notable. Esto permite subir o bajar escaladamente los servicios a través de la llamada de un simple comando. Por ejemplo, un servicio web denominado Charm , que tiene una relación establecida con un equilibrador de carga, puede subirse horizontalmente con una simple orden de "añadir unidad" sin tener que preocuparse de volver a configurar el equilibrador de carga para declarar las nuevas instancias: las relaciones basadas en eventos del Charm se encargan de eso. Los Charms de Juju pueden ser escritos en cualquier lenguaje ejecutable. Relevamiento de características de la maquina utilizada: Procesador: Pentium Dual Core E5300 Ram: 2 GB Disco Rigido: 200 GB Relevamiento de sistema operativo y software utilizado y/o necesario: Ubuntu 16.04 JUJU Charms: son conjuntos de scripts para desplegar y administrar servicios. Con el manejo de eventos integrado, pueden declarar interfaces que encajan con otros servicios, por lo que pueden formarse relaciones. LXD: es un hypervisor (plataforma que permite aplicar diversas técnicas de control de virtualización) para contenedores Linux desarrollado por Canonical Ltd. Es un complemento para los contenedores de Linux (LXC) que facilita su uso y añade nuevas posibilidades. -

Firefox Hacks Is Ideal for Power Users Who Want to Maximize The
Firefox Hacks By Nigel McFarlane Publisher: O'Reilly Pub Date: March 2005 ISBN: 0-596-00928-3 Pages: 398 Table of • Contents • Index • Reviews Reader Firefox Hacks is ideal for power users who want to maximize the • Reviews effectiveness of Firefox, the next-generation web browser that is quickly • Errata gaining in popularity. This highly-focused book offers all the valuable tips • Academic and tools you need to enjoy a superior and safer browsing experience. Learn how to customize its deployment, appearance, features, and functionality. Firefox Hacks By Nigel McFarlane Publisher: O'Reilly Pub Date: March 2005 ISBN: 0-596-00928-3 Pages: 398 Table of • Contents • Index • Reviews Reader • Reviews • Errata • Academic Copyright Credits About the Author Contributors Acknowledgments Preface Why Firefox Hacks? How to Use This Book How This Book Is Organized Conventions Used in This Book Using Code Examples Safari® Enabled How to Contact Us Got a Hack? Chapter 1. Firefox Basics Section 1.1. Hacks 1-10 Section 1.2. Get Oriented Hack 1. Ten Ways to Display a Web Page Hack 2. Ten Ways to Navigate to a Web Page Hack 3. Find Stuff Hack 4. Identify and Use Toolbar Icons Hack 5. Use Keyboard Shortcuts Hack 6. Make Firefox Look Different Hack 7. Stop Once-Only Dialogs Safely Hack 8. Flush and Clear Absolutely Everything Hack 9. Make Firefox Go Fast Hack 10. Start Up from the Command Line Chapter 2. Security Section 2.1. Hacks 11-21 Hack 11. Drop Miscellaneous Security Blocks Hack 12. Raise Security to Protect Dummies Hack 13. Stop All Secret Network Activity Hack 14. -

Tensorflow 2.0 and Kubeflow for Scalable and Reproducable Enterprise Ai
TENSORFLOW 2.0 AND KUBEFLOW FOR SCALABLE AND REPRODUCABLE ENTERPRISE AI Romeo Kienzler1, 2, Holger Kyas2, 3, 4 1IBM Center for Open Source Data and AI Technologies, 505 Howard St, San Francisco, CA, USA 2Berne University of Applied Sciences, Technology and Informatics, Wankdorffeldstrasse 102, 3014 Berne, Switzerland 3Open Group, 548 Market St #54820, San Francisco, CA 94104-5401 4Helvetia Insurance Switzerland, St. Alban-Anlage 26, 4002 Basel, Switzerland ABSTRACT Towards the End of 2015 Google released TensorFlow 1.0, which started out as just another numerical library, but has grown to become a de-facto standard in AI technologies. TensorFlow received a lot of hype as part of its initial release, in no small part because it was released by Google. Despite the hype, there have been complaints on usability as well. Especially, for example, the fact that debugging was only possible after construction of a static execution graph. In addition to that, neural networks needed to be expressed as a set of linear algebra operations which was considered as too low level by many practitioners. PyTorch and Keras addressed many of the flaws in TensorFlow and gained a lot of ground. TensorFlow 2.0 successfully addresses these complaints and promises to become the go-to framework for many AI problems. This paper introduces the most prominent changes in TensorFlow 2.0 targeted towards ease of use followed by introducing TensorFlow Extended Pipelines and KubeFlow in order to illustrate the latest TensorFlow and Kubernetes ecosystem movements towards simplification for large scale Enterprise AI adoption. KEYWORDS Artificial Intelligence, TensorFlow, Keras, Kubernetes, KubeFlow, TFX, TFX Pipelines 1. -

Using Ipus from Docker Release 1.4.0
Using IPUs from Docker Release 1.4.0 Graphcore Ltd Dec 08, 2020 CONTENTS 1 Introduction 1 2 Initial setup 2 3 Using gc-docker 3 3.1 Loading docker images.............................................3 3.2 Verifying IPU access from inside container..................................4 3.3 Mounting directories from the host......................................5 3.4 Setting environment variables.........................................5 4 Running a TensorFlow application on an IPU6 5 Extending the images 7 6 Further reading 8 7 Trademarks & copyright 9 i CHAPTER ONE INTRODUCTION This guide explains how you can run applications in Docker on a Linux machine with one or more physical IPU devices. Prerequisites: • A machine with IPU devices • Ubuntu 18.04 / CentOS 7.6 1 CHAPTER TWO INITIAL SETUP First check if your machine has the IPU device driver installed. You can check this is loaded and running with the following command: $ modinfo ipu_driver If the driver is are installed and running, you should see something similar to: $ modinfo ipu_driver filename: /lib/modules/4.15.0-55-generic/updates/dkms/ipu_driver.ko version: 1.0.39 description: IPU PCI Driver author: Graphcore Limited license: GPL srcversion: 49FFB7D8556EB58899AE41A alias: pci:v00001D95d00000003sv*sd*bc*sc*i* alias: pci:v00001D95d00000002sv*sd*bc*sc*i* alias: pci:v00001D95d00000001sv*sd*bc*sc*i* depends: retpoline: Y name: ipu_driver vermagic: 4.15.0-55-generic SMP mod_unload parm: memmap_start:array of ulong parm: memmap_size:array of ulong If so, proceed to the next section. If it returns an error along the lines of: $ modinfo ipu_driver modinfo: ERROR: Module ipu_driver not found. You will need to install the driver. -

Reference Architecture for Kubeflow on Openshift Accelerate ML/DL Workloads Using Kubeflow and Poweredge Servers
Solution brief Reference Architecture for Kubeflow on OpenShift Accelerate ML/DL workloads using Kubeflow and PowerEdge servers Artificial intelligence (AI) and its subsets, machine learning (ML) and deep learning (DL), Customer are gaining widespread adoption for use cases such as computer vision, speech recognition and natural language processing (NLP). Integrating production‑grade AI technologies Results in well‑defined platforms within the protection of the data center can facilitate wider adoption of advanced computing, extending investments by supporting AI use cases as well as augmenting the resources available to data science teams. 2 hours vs. But not every IT organization has the time and resources to research, integrate and test all the components required to deploy a customized system to run AI workloads. Building 9 months a production‑ready AI system involves combining various components, often from different to run analysis1 vendors, and integrating and managing these disparate pieces. As well, deployments are often tied to a specific cluster, so that moving models — for example, between laptops and cloud clusters or from DevOps to production and back — significantly increases 218% ROI complexity and the chance for human errors. over 3 years2 Kubeflow together with the Red Hat® OpenShift® Container Platform help address these challenges. Kubeflow is an open‑source Kubernetes®‑native platform designed 20 million to accelerate ML workloads. It’s a composable, scalable, portable stack that includes images used to train a components and automation features to integrate ML tools, so they work together to deep neural network3 create a cohesive pipeline that makes it easy to deploy ML applications at scale. -

CNCF Webinar Taming Your AI/ML Workloads with Kubeflow
CNCF Webinar Taming Your AI/ML Workloads with Kubeflow The Journey to Version 1.0 David Aronchick (Microsoft) - @aronchick Elvira Dzhuraeva (Cisco) - @elvirafortune Johnu George (Cisco) - @johnugeorge SNARC Maze Solver Minsky / Edmonds (1951) 2000 3 2006 4 2007 5 2008 6 2010 7 2013 8 2014 9 2015 10 Today 11 One More ML ???Solution??? 12 One More ML ???Solution??? 13 14 GitHub Natural Language Search Prototype MVP With Demo In Jupyter Demo with front-end mockup with Experiments.Github.Com: +3 Months Notebook: 2 Weeks blog post: +3 Days https://github.com/hamelsmu/code_search https://towardsdatascience.com/semantic-code-se https://experiments.github.com/ arch-3cd6d244a39c 15 Resource Provisioning Numpy Scheduling Experiment Tracking Jupyter Access Control Declarative Deployment TF.Transform Drivers HP Tuning TF.Estimator Orchestration Profiling Docker Lifecycle Management Validation Seldon Networking KubeCon 2017 17 Resource Provisioning Numpy Scheduling Experiment Tracking Jupyter Access Control Declarative Deployment TF.Transform Drivers HP Tuning TF.Estimator Orchestration Profiling Docker Lifecycle Management Validation Seldon Networking Mission (2017) Make it Easy for Everyone to Develop, Deploy and Manage Portable, Distributed ML on Kubernetes 20 Kubeflow 2018 Mission (2018) Make it Easy for Everyone to Develop, Deploy and Manage Portable, Distributed ML on Kubernetes 23 Kubeflow 2019 Mission (2019) Make it Easy for Everyone to Develop, Deploy and Manage Portable, Distributed ML on Kubernetes 26 Mission (2020) Make it Easy for Everyone -
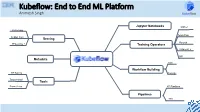
Kubeflow: End to End ML Platform Animesh Singh
Kubeflow: End to End ML Platform Animesh Singh Jupyter Notebooks MXNet KFServing Tensorflow Seldon Core Serving Pytorch TFServing, + Training Operators XGBoost, + MPI Metadata Kale Workflow Building HP Tuning Fairing Tensorboard Tools Prometheus KF Pipelines Pipelines TFX Your Speaker Today: CODAIT 2 Animesh Singh Kubeflow STSM and Chief Architect - Data and AI Open Source github.com/kubeflow Platform o CTO, IBM RedHat Data and AI Open Source Alignment o IBM Kubeflow Engagement Lead, Kubeflow Committer o Chair, Linux Foundation AI - Trusted AI o Chair, CD Foundation MLOps Sig o Ambassador, CNCF o Member of IBM Academy of Technology (IBM AoT) © 2019 IBM Corporation Kubeflow: Current IBM Contributors Untrained Model Christian Kadner Weiqiang Zhuang Tommy Li Andrew Butler Prepared Preparedand Trained AnalyzedData Model Data Deployed Model Jin Chi He Feng Li Ke Zhu Kevin Yu IBM is the 2nd Largest Contributor IBM is the 2nd Largest Contributor IBMers contributing across projects in Kubeflow Kubeflow Services kubectl apply -f tfjob High Level Kubernetes API Server Services Notebooks Low Level APIs / Services Pipelines TFJob PyTorchJob Pipelines CR KFServing Argo Jupyter CR MPIJob Katib Seldon CR Study Job Spark Job Istio Mesh and Gateway Kubebench TFX Developed By Kubeflow Developed Outside Kubeflow Adapted from Kubeflow Contributor Summit 2019 talk: Kubeflow and ML Landscape (Not all components are shown) Community is growing! 8 Multi-User Isolation ML Lifecycle: Build: Development, Training and HPO Untrained Model Prepared Preparedand Trained