Information Technology Management
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Information Technology Management 14
Information Technology Management 14 Valerie Bryan Practitioner Consultants Florida Atlantic University Layne Young Business Relationship Manager Indianapolis, IN Donna Goldstein GIS Coordinator Palm Beach County School District Information Technology is a fundamental force in • IT as a management tool; reshaping organizations by applying investment in • understanding IT infrastructure; and computing and communications to promote competi- • ȱǯ tive advantage, customer service, and other strategic ęǯȱǻȱǯȱǰȱŗşşŚǼ ȱȱ ȱ¢ȱȱȱ¢ǰȱȱ¢Ȃȱ not part of the steamroller, you’re part of the road. ǻ ȱǼ ȱ ¢ȱ ȱ ȱ ęȱ ȱ ȱ ¢ǯȱȱȱȱȱ ȱȱ ȱ- ¢ȱȱȱȱȱǯȱ ǰȱ What is IT? because technology changes so rapidly, park and recre- ation managers must stay updated on both technological A goal of management is to provide the right tools for ȱȱȱȱǯ ěȱ ȱ ě¢ȱ ȱ ȱ ȱ ȱ ȱ ȱȱȱȱ ȱȱȱǰȱȱǰȱ ȱȱȱȱȱȱǯȱȱȱȱ ǰȱȱȱȱ ȱȱ¡ȱȱȱȱ recreation organization may be comprised of many of terms crucial for understanding the impact of tech- ȱȱȱȱǯȱȱ ¢ȱ ȱ ȱ ȱ ȱ ǯȱ ȱ ȱ ȱ ȱ ȱ ǯȱ ȱ - ȱȱęȱȱȱ¢ȱȱȱȱ ¢ȱǻ Ǽȱȱȱȱ¢ȱ ȱȱȱȱ ǰȱ ȱ ȱ ȬȬ ȱ ȱ ȱ ȱȱǯȱȱȱȱȱ ¢ȱȱǯȱȱ ȱȱȱȱ ȱȱ¡ȱȱȱȱȱǻǰȱŗşŞśǼǯȱ ȱȱȱȱȱȱĞȱȱȱȱ ǻȱ¡ȱŗŚǯŗȱ Ǽǯ ě¢ȱȱȱȱǯ Information technology is an umbrella term Details concerning the technical terms used in this that covers a vast array of computer disciplines that ȱȱȱȱȱȱȬȬęȱ ȱȱ permit organizations to manage their information ǰȱ ȱ ȱ ȱ Ȭȱ ¢ȱ ǯȱ¢ǰȱȱ¢ȱȱȱ ȱȱ ǯȱȱȱȱȱȬȱ¢ȱ a fundamental force in reshaping organizations by applying ȱȱ ȱȱ ȱ¢ȱȱȱȱ investment in computing and communications to promote ȱȱ¢ǯȱ ȱȱȱȱ ȱȱ competitive advantage, customer service, and other strategic ȱ ǻȱ ȱ ŗŚȬŗȱ ęȱ ȱ DZȱ ęȱǻǰȱŗşşŚǰȱǯȱřǼǯ ȱ Ǽǯ ȱ¢ȱǻ Ǽȱȱȱȱȱ ȱȱȱęȱȱȱ¢ȱȱ ȱ¢ǯȱȱȱȱȱ ȱȱ ȱȱ ȱȱȱȱ ȱ¢ȱ ȱȱǯȱ ȱ¢ǰȱ ȱȱ ȱDZ ȱȱȱȱǯȱ ȱȱȱȱǯȱ It lets people learn things they didn’t think they could • ȱȱȱ¢ǵ ȱǰȱȱǰȱȱȱǰȱȱȱȱȱǯȱ • the manager’s responsibilities; ǻȱǰȱȱ¡ȱĜȱȱĞǰȱȱ • information resources; ǷȱǯȱȱȱřŗǰȱŘŖŖŞǰȱ • disaster recovery and business continuity; ȱĴDZȦȦ ǯ ǯǼ Information Technology Management 305 Exhibit 14. -

Digitalization in Supply Chain Management and Logistics: Smart and Digital Solutions for an Industry 4.0 Environment
A Service of Leibniz-Informationszentrum econstor Wirtschaft Leibniz Information Centre Make Your Publications Visible. zbw for Economics Kersten, Wolfgang (Ed.); Blecker, Thorsten (Ed.); Ringle, Christian M. (Ed.) Proceedings Digitalization in Supply Chain Management and Logistics: Smart and Digital Solutions for an Industry 4.0 Environment Proceedings of the Hamburg International Conference of Logistics (HICL), No. 23 Provided in Cooperation with: Hamburg University of Technology (TUHH), Institute of Business Logistics and General Management Suggested Citation: Kersten, Wolfgang (Ed.); Blecker, Thorsten (Ed.); Ringle, Christian M. (Ed.) (2017) : Digitalization in Supply Chain Management and Logistics: Smart and Digital Solutions for an Industry 4.0 Environment, Proceedings of the Hamburg International Conference of Logistics (HICL), No. 23, ISBN 978-3-7450-4328-0, epubli GmbH, Berlin, http://dx.doi.org/10.15480/882.1442 This Version is available at: http://hdl.handle.net/10419/209192 Standard-Nutzungsbedingungen: Terms of use: Die Dokumente auf EconStor dürfen zu eigenen wissenschaftlichen Documents in EconStor may be saved and copied for your Zwecken und zum Privatgebrauch gespeichert und kopiert werden. personal and scholarly purposes. Sie dürfen die Dokumente nicht für öffentliche oder kommerzielle You are not to copy documents for public or commercial Zwecke vervielfältigen, öffentlich ausstellen, öffentlich zugänglich purposes, to exhibit the documents publicly, to make them machen, vertreiben oder anderweitig nutzen. publicly available on the internet, or to distribute or otherwise use the documents in public. Sofern die Verfasser die Dokumente unter Open-Content-Lizenzen (insbesondere CC-Lizenzen) zur Verfügung gestellt haben sollten, If the documents have been made available under an Open gelten abweichend von diesen Nutzungsbedingungen die in der dort Content Licence (especially Creative Commons Licences), you genannten Lizenz gewährten Nutzungsrechte. -

NRECA Electric Cooperative Employee Competencies 1.24.2020
The knowledge, skills, and abilities that support successful performance for ALL cooperative employees, regardless of the individual’s role or expertise. BUSINESS ACUMEN Integrates business, organizational and industry knowledge to one’s own job performance. Electric Cooperative Business Fundamentals Integrates knowledge of internal and external cooperative business and industry principles, structures and processes into daily practice. Technical Credibility Keeps current in area of expertise and demonstrates competency within areas of functional responsibility. Political Savvy Understands the impacts of internal and external political dynamics. Resource Management Uses resources to accomplish objectives and goals. Service and Community Orientation Anticipates and meets the needs of internal and external customers and stakeholders. Technology Management Keeps current on developments and leverages technology to meet goals. PERSONAL EFFECTIVENESS Demonstrates a professional presence and a commitment to effective job performance. Accountability and Dependability Takes personal responsibility for the quality and timeliness of work and achieves results with little oversight. Business Etiquette Maintains a professional presence in business settings. Ethics and Integrity Adheres to professional standards and acts in an honest, fair and trustworthy manner. Safety Focus Adheres to all occupational safety laws, regulations, standards, and practices. Self-Management Manages own time, priorities, and resources to achieve goals. Self-Awareness / Continual Learning Displays an ongoing commitment to learning and self-improvement. INTERACTIONS WITH OTHERS Builds constructive working relationships characterized by a high level of acceptance, cooperation, and mutual respect. 2 NRECA Electric Cooperative Employee Competencies 1.24.2020 Collaboration/Engagement Develops networks and alliances to build strategic relationships and achieve common goals. Interpersonal Skills Treats others with courtesy, sensitivity, and respect. -

The Impact of Information Technology on Supply Chain Performance: a Knowledge Management Perspective
View metadata, citation and similar papers at core.ac.uk brought to you by CORE provided by The University of North Carolina at Greensboro THE IMPACT OF INFORMATION TECHNOLOGY ON SUPPLY CHAIN PERFORMANCE: A KNOWLEDGE MANAGEMENT PERSPECTIVE by Yuan Niu A dissertation submitted to the faculty of The University of North Carolina at Charlotte in partial fulfillment of the requirements for the degree of Doctor of Philosophy in Information Technology Charlotte 2010 Approved by: _______________________________ Dr. Chandrasekar Subramaniam _______________________________ Dr. Antonis Stylianou _______________________________ Dr. Sungjune Park _______________________________ Dr. Arun Rai _______________________________ Dr. Thomas Stevenson ii © 2010 Yuan Niu ALL RIGHTS RESERVED iii ABSTRACT YUAN NIU. The impact of information technology on supply chain performance: a knowledge management perspective (Under direction of DR. CHANDRASEKAR SUBRAMANIAM AND DR. ANTONIS STYLIANOU) Supply chain management has become an increasingly important management tool to help organizations improve their business operations. Although information and communication technologies have been used extensively in supply chains, there is a lack of systematic evidence regarding the mechanisms through which IT creates value. Furthermore, as supply chain objectives are going beyond operational efficiency towards pursuing higher-order goals, such as understanding the market dynamics and discovering new partnering arrangements to provide greater customer value, the capabilities -

Customer Relationship Management and Technology
Customer Relationship Management and Technology Mohammad Hassan Yousefi , Department of Business Administration and Marketing, Allameh Tabatabayi University/ Market Research Head in Hooshmand Tadbir Research Institute, Tehran, Iran [email protected] Mohammad Hossein Jarrahi , Department of Information Systems, London School of Economics and Political Sciences, London, UK [email protected] Keywords Information Technology, Customer Relationship Management, eCRM Abstract During the last decade, increasing attention has been given to relationship marketing as a way to enhance cooperation between a selling company and its customers and bring benefits to both parties. Globalization and technology improvements have exposed companies to a situation with tough competition. Relationship marketing allows a selling company to better meet competition and exceed their competitors, and hence relationship marketing becomes an important determinator of success in the increasingly competitive business world of today. One method of relationship marketing is Customer Relationship Management (CRM). Nowadays, new technologies have empowered customer relationship management (CRM) to dominate marketing paradigms. However, a large proportion of CRM practices do not yield expected profits. Yet, this phenomenon is attributed to a misconception of CRM and the role of technology in its implementation as there are diverse attitudes toward this issue. Some interpret CRM through a technological framework, and assume software solutions are what the organization mainly needs for leveraging CRM whereas others contend that CRM is more than a technology, and underscore some required considerations including formulating customer-focused strategy, user involvement, and process alignment before CRM execution. Here, these different perspectives are organized into two main groups of technological and non-technological perspectives, and consequently the position they appreciate for technology in CRM will be pondered and compared. -

Introduction to Technology Management
ering & ine M g a n n E a l g a i e r Industrial Engineering & m t s e u n d t n Namdeo et al., Ind Eng Manage 2016, 5:3 I Management 10.4172/2169-0316.1000195 ISSN: 2169-0316 DOI: Perspective Open Access Introduction to Technology Management Punit Namdeo, Musheer Ahmed Ansarie and Ashutosh Bhatnagar* Institute of Technology-Management, DRDO, Ministry of Defence, Mussoorie, Uttrarakhand, India *Corresponding author: Bhatnagar A, Institute of Technology-Management, DRDO, Ministry of Defence, Mussoorie, Uttrarakhand, India, Tel: +8827949313; E-mail: [email protected] Received date: July 28, 2015, Accepted date: July 02, 2016, Published date: July 08, 2016 Copyright: © 2016 Namdeo P, et al. This is an open-access article distributed under the terms of the Creative Commons Attribution License, which permits unrestricted use, distribution, and reproduction in any medium, provided the original author and source are credited. Abstract Management of Technology is interdisciplinary fields that integrate science, engineering and management knowledge also with practice. Technology Management is set of management disciplines that allow organizations to manage their technological fundamentals to create competitive advantage. The main focus on technology part for manager is to create wealth. Technology management requires deep understanding of life cycles of technology, product, process and system. Technology management is also a tool to catalyze R&D. By providing R&D team in R&D organization to an increased extent, it can generate more science from existing science and more technology from existing technology. Technology management involve technological tool for national defense, national development and economic growth by resolving to make country a self-reliant, strong and technology developed country. -
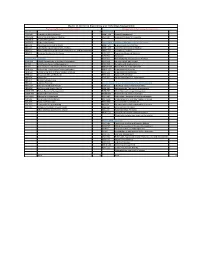
M.S. Engineering and Technology Management Curriculum
Master of Science in Engineering and Technology Management Engineering Management Concentration Management of Technology Concentration Core Courses 24 Core Courses 6 EMGT 507 Engineering Administration EMGT 518 Project Management EMGT 509 Economics and Decision Making INEN 514 Statistical Analysis for Six Sigma EMGT 518 Project Management EMGT 525 Engineering Finance Quantitative Analysis and Management (Pick 3 Courses) 9 INEN 502 Operations Research Methods EMGT 507 Engineering Administration INEN 505 Manufacturing and Operations Analysis EMGT 509 Economics and Decision Making INEN 511 Theory and Application of Lean Manufacturing and Management EMGT 525 Engineering Finance INEN 514 Statistical Analysis for Six Sigma INEN 502 Operations Research Methods INEN 504 Simulation Electives (Pick 3 Courses) 9 INEN 505 Manufacturing and Operations Analysis BUSN 501 Global Perspectives in Business Management INEN 520 Six Sigma Black Belt Project CIS 510 Information Resource Management INEN 566 Six Sigma and Quality Control CIS 521 Introduction to Information System Assurance MGMT 537 Human Resource Management ENTR 501 Technology Transfer and Commercialization MGMT 571 Organizational Behavior ENTR 510 Entrepreneurship and New Venture Creation PSYC 513 Organizational Psychology ENTR 560 Innovative Venture Research PSYC 516 Industrial Psychology INEN 504 Simulation STAT 507 Design and Analysis of Experiments INEN 512 Reliability Engineering INEN 515 Logistics Planning Science, Engineering, and Entrepreneurship (Pick 3 Courses) 9 INEN 520 Six Sigma -

Technology and Innovation Management 1674
TECHNOLOGY AND INNOVATION MANAGEMENT 1674 SUSTAINABLE TECHNOLOGY MANAGEMENT AND DEVELOPMENT - STATE UNIVERSITY AND INDUSTRY PERFORMANCE MODEL 1675 Levi Jakšić Maja, Jovanović Milica, Petković Jasna GOVERNMENT PERFORMANCE IN TECHNOLOGY AND INNOVATION MANAGEMENT – THE CASE OF SERBIA 1684 Marinković Sanja, Rakićević Jovana, Levi Jakšić Maja MECHANISMS FOR STIMULATING INNOVATION CAPABILITIES IN W ESTERN BALKAN COUNTRIES 1693 Štrbac Dijana, Kutlača Đuro, Ţivković Lazar POSSIBILITIES OF OPENING UP THE STAGE-GATE MODEL 1700 Stošić Biljana, Milutinović Radul THE EVOLUTION OF MOBILE TECHNOLOGY IN RETAIL MARKETING CHANNELS IN THE REPUBLIC OF SERBIA 1708 Končar Jelena, Vukmirović Goran, Leković Sonja ADVANCE REAL ESTATE MANAGEMENT SYSTEM 1713 Jovanović Verka, Vukelić ĐorĎe CLOUD COMPUTING INFRASTRUCTURE APPLICATIONS IN COMPUTER SIMULATION 1721 Marinković Mihailo, Čavoški Sava, Marković Aleksandar TECHNOLOGY AND INNOVATION MANAGEMENT 1674 SUSTAINABLE TECHNOLOGY MANAGEMENT AND DEVELOPMENT - STATE, UNIVERSITY AND INDUSTRY PERFORMANCE MODEL Maja Levi Jakšić1, Milica Jovanović2 Jasna Petković3 1University of Belgrade, Faculty of Organizational Sciences [email protected] 2University of Belgrade, Faculty of Organizational Sciences [email protected] 3University of Belgrade, Faculty of Organizational Sciences [email protected] Abstract: In this paper a general model is created for measuring the performance of Technology and Innovation Management (TIM) related to the crucial dimensions/elements of the Triple Helix (TH) model. More precisely, the Triple Helix Model (high education – government - industry) is analysed in relation to its fulfilling the three main functions of TIM: planning, organizing and control (POC). The general model – TMD- TH (Technology Management and Development – Triple Helix) represents the framework for further more specific research into the relations of the observed dimensions. -

Defining a Technology Management Framework Within a Defense Enterprise
Journal of Management, Marketing and Logistics – (JMML), ISSN: 2148-6670, http://www.pressacademia.org/journals/jmml Journal of Management, Marketing and Logistics -JMML (2017), Vol.4(3),p.301-309 Kaya, Erol, Ozbilgin Year: 2017 Volume: 4 Issue: 3 DEFINING A TECHNOLOGY MANAGEMENT FRAMEWORK WITHIN A DEFENSE ENTERPRISE DOI: 10.17261/Pressacademia.2017.492 JMML- V.4-ISS.3-2017(12)-p.301-309 Pınar Kaya1, Tolga Erol2 and I. Gokhan Ozbilgin3 1 HAVELSAN Technology and Academia Directoriate, [email protected] 2 HAVELSAN Technology and Academia Directoriate, [email protected] 3 HAVELSAN Technology and Academia Directoriate, [email protected] To cite this document Kaya, P., T. Erol and İ. G. Ozbilgin (2017). Defining a technology management framework within a defense enterprise. Journal of Management, Marketing and Logistics (JMML), V.4, Iss.3, p.301-309. Permemant link to this document: http://doi.org/10.17261/Pressacademia.2017.492 Copyright: Published by PressAcademia and limited licenced re-use rights only. ABSTRACT Purpose- In this paper, the methodology of definition a tailored Technology Management (TM) Framework for a large scale enterprise defense company (HAVELSAN) will be explained briefly, and selected subset of TMF components in the company will be further discussed. The method of managing technologies in enterprises depends primarily on the size of the company and its organizational structure. Methodology- The main purpose of this paper is the identification and analysis of the factors influencing the manner in which technologies are managed in big enterprise companies especially focused on defense industry. Findings- The concepts that are investigated and the methodologies that are developed in this study are primarily based on the case of technology management framework within a defence technology enterprise. -

Impact of Customer Relationship Management on Product Innovation Process
Impact of Customer Relationship Management on Product Innovation Process Supervisor Dr. Ossi Pesämaa Authors Yelin Li and Nguyen Thi Thu Sang Dec 2011 Abstracts In marketing, the common view is that customer relationships enhance innovativeness. Regularly it involves doing something new or different in response to market conditions. However, previous studies have not addressed how customer relationship management (CRM) plays its role in product innovation process. This thesis proposes and tests how key CRM activities influence and relate to each stage in product innovation process. The objective of this study is to test how customer relations management activities influence four basic stages of product innovation process. Five practices of CRM is found in the literature (i.e., information sharing, customer involvement, long-term partnership, joint problem-solving and technology-based CRM). Furthermore, our literature review suggests four stages of innovation process (i.e., innovation initiation, input, thoroughput and output). The one-to-one relationship between CRM activities and innovation stages are established in four models. These associations are tested and some are verified in a survey-based study. Specifically data from 83 respondents were collected. All respondents represent a strategic business unit and work closely with R&D, product development or marketing. Regression analysis is conducted to examine the impacts of CRM on innovation process. The statistical results indicate that not all CRM activities make contributions to each stage within innovation process. It is found that 1) information sharing effectively enhances both innovation throughput and innovation output. 2) Customer involvement and joint problem-solving exert positive influence on innovation throughput stage, while long-term partnership has significant effects on innovation output. -

Information Technology and Customer Relationship Management (CRM) in Some Selected Insurance Firms in Nigeria
Journal of Economics and International Finance Vol. 3(7), pp. 452-461, July 2011 Available online at http://www.academicjournals.org/JEIF ISSN 2006-9812 ©2011 Academic Journals Full Length Research Paper Information technology and customer relationship management (CRM) in some selected insurance firms in Nigeria B. E. A. Oghojafor, S. A. Aduloju* and F. F. Olowokudejo Actuarial Science and Insurance Department, Faculty of Business Administration, University of Lagos, Lagos, Nigeria. Accepted 31 May, 2011 In this study, we explore the question of how IT could enhance firm performance in the areas of customer’s service and organization’s profitability in the Nigerian insurance industry. To draw our sample size of 90, 30 insurance companies were randomly selected from the 49-member insurance umbrella body, the Nigerian Insurers Association. Each company received 3 copies of the questionnaire meant for the IT manager, marketing manager and underwriting manager, respectively, making a total of 90. We proposed 3 hypotheses which were tested with the aid of Komolgorov-Smirnov test. Our findings show that while most companies have a comprehensive data base of their customers, not all make provisions for their customers to make major transactions online because they have not fully integrated their customer relationship management with information technology. We also find out that effective combination of customer relationship management with information technology leads to improved customer service and organization’s profitability. Key words: Information technology, customer relationship management (CRM), firm performance, insurance. INTRODUCTION Today, electronic commerce is breaking the traditional whether banking, insurance, engineering, entertainment, concept and rules of operations, transforming the way etc, there has to be a conscious effort by the enterprises do business and making them confront a new management towards making it customer oriented. -

Evolution of EVM and the Future
Evolution of EVM and the Future NSF Large Facilities Workshop Baton Rouge, LA May 1, 2017 Wayne Abba President, CPM [email protected] Agenda • College of Performance Management (CPM) • Earned Value Management (EVM) – the Foundation of Integrated Program Management (IPM) • Evolution of IPM – Past (Cost/Schedule Control Systems Criteria) – Present (Earned Value Management) – Future (Integrated Program Management) • War Story – A Tale of Two Aircraft • Summary and Q&A 2 THE COLLEGE OF PERFORMANCE MANAGEMENT (CPM) WWW.MYCPM.ORG/ 3 About CPM • The College of Performance Management (CPM) is a global, non-profit, professional organization dedicated to developing and disseminating the principles and practices of earned value management and other project performance management techniques. • We assist the project control professional and project manager in professional growth and promote the application of earned value management. We are a growing body of professionals dedicated to managing projects on time and on budget. 4 2017 CPM Events • EVM World 2017 • IPM Workshop – May 31 – June 2, 2017 – Oct 30 – Nov 1, 2017 – New Orleans, Louisiana – Bethesda, Maryland – Hyatt Regency New – Bethesda North Marriott Orleans Hotel & Conference – Science & PM Track Center 50 www.mycpm.org/news-events/events/ 5 EARNED VALUE MANAGEMENT (EVM) 6 What is EVM? • Earned Value Management (EVM) is a project management technique for measuring project performance and progress. In a single integrated system, Earned Value Management (EVM) is able to provide accurate