Comments of the Clearing House
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Federal Register/Vol. 85, No. 230/Monday, November 30, 2020
76450 Federal Register / Vol. 85, No. 230 / Monday, November 30, 2020 / Rules and Regulations Commission’s requirement that certain the Commission. It is appropriate to apply SUPPLEMENTARY INFORMATION: commonly traded interest rate swaps and this exemption to the holding companies of credit default swaps be cleared following these financial entities. Electronic Availability their execution.2 The new exemptions may One commenter, Better Markets, expressed This document and additional be elected by several classes of counterparties concern that the number of entities that will information concerning OFAC are that may enter into these swaps, namely: now have an exemption from the clearing available on OFAC’s website requirement has grown over time, leading to Sovereign nations; central banks; (www.treasury.gov/ofac). ‘‘international financial institutions’’ of the potential for greater risk, reduction in which sovereign nations are members; bank liquidity in cleared markets, and complexity Background holding companies, and savings and loan in managing the exemptions. As described in holding companies, whose assets total no the preamble to the final rule, swap data On March 8, 2015, the President, more than $10 billion; and community repository data indicates that over the past invoking the authority of, inter alia, the development financial institutions several years the number and scope of swaps International Emergency Economic recognized by the U.S. Treasury Department. entered into by these institutions that will be Powers Act (50 U.S.C. 1701–1706), Today’s final rule notes that many of these included within the exemptions has been issued Executive Order (E.O.) 13692 of entities have actually relied on existing relief, relatively limited. -
Appendix B – Communications Received
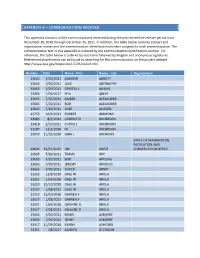
APPENDIX B – COMMUNICATIONS RECEIVED This appendix contains all the communications received during the post-centerline release period from November 18, 2010 through December 31, 2011. In addition, the table below contains contact and organization names and the communication identification number assigned to each communication. The communication text in this appendix is ordered by the communication identification number. For reference, the table below is ordered by last name followed by illegible and anonymous signatures. Referenced attachments can be found by searching for the communication on the project website http://www.bpa.gov/corporate/I-5-EIS/search.cfm. Number Date Name - First Name - Last Organization 13665 7/20/2011 ANDREW ABBOTT 13665 7/20/2011 JACK ABERNATHY 13665 7/20/2011 CRYSTAL L ADAMS 13395 1/29/2011 PHIL AKELY 13667 7/20/2011 AMBER ALEXANDER 13665 7/20/2011 BOB ALEXANDER 13665 7/20/2011 CHEE ALLISON 13755 10/6/2011 ROBERT AMMONS 13683 8/3/2011 CANDICE D ANDERSON 13418 2/10/2011 CURTIS L ANDERSON 13207 12/2/2010 M. ANDERSON 13073 11/22/2010 GINA L ANDREWS STATE OF WASHINGTON, RECREATION AND 13836 12/15/2011 JIM ANEST CONSERVATION OFFICE 13665 7/20/2011 TRAVIS APP 13665 7/20/2011 BOB APPLING 13665 7/20/2011 JEREMY ARIONUS 13665 7/20/2011 CHUCK ARNST 13322 12/8/2010 DALE W AROLA 13321 12/9/2010 DALE W AROLA 13320 12/10/2010 DALE W AROLA 13527 1/28/2011 DALE W AROLA 13320 12/10/2010 DARREN F AROLA 13527 1/28/2011 DARREN F AROLA 13321 12/9/2010 DWAYNE D AROLA 13527 1/28/2011 DWAYNE D AROLA 13665 7/20/2011 BRIAN ASBURRY 13665 -

Public Safety, Interoperability and the Transition to Digital Television
Order Code RL32622 CRS Report for Congress Received through the CRS Web Public Safety, Interoperability and the Transition to Digital Television Updated April 18, 2005 Linda K. Moore Analyst in Telecommunications Policy Resources, Science, and Industry Division Congressional Research Service ˜ The Library of Congress Public Safety, Interoperability and the Transition to Digital Television Summary Plans for the use of spectrum intended for wireless emergency communications and interoperability are enmeshed in the technical requirements and complex economic and policy issues that surround the planned transition to digital television (DTV) in the United States. The Balanced Budget Act of 1997 requires the Federal Communications Commission (FCC) to allocate 24 MHZ of spectrum at 700 MHZ to public safety, without providing a hard deadline for the transfer. The channels designated for public safety are among those currently held by TV broadcasters. The 9/11 Commission Report recommended in 2004 that “Congress should support pending legislation which provides for the expedited and increased assignment of radio spectrum for public safety purposes.” This was a reference to the Homeland Emergency Response Operations Act, or HERO Act — introduced by Representative Jane Harman — which would have required the FCC to “take all actions necessary to complete assignments” for these channels so that operations could begin no later than January 1, 2007, in line with the deadline originally envisioned for the completion of the transition to DTV for all affected channels. After the appearance of the Report, several bills resembling the HERO Act were introduced. Steps to release the spectrum were included in both the key House (H.R. -

THE DEPOSITORY TRUST COMPANY Disclosure Framework for Covered Clearing Agencies and Financial Market Infrastructures
THE DEPOSITORY TRUST COMPANY Disclosure Framework for Covered Clearing Agencies and Financial Market Infrastructures December 2020 ADVANCING FINANCIAL MARKETS. TOGETHER.TM DTCC Public (White) THE DEPOSITORY TRUST COMPANY: Disclosure Framework for Covered Clearing Agencies and Financial Market Infrastructures Responding Institution: The Depository Trust Company (“DTC”) Jurisdiction: State of New York, United States of America Authorities: U.S. Securities and Exchange Commission; Federal Reserve Bank of New York; New York State Department of Financial Services Except as noted in Section II, the information provided in this Disclosure Framework is accurate as of December 31, 2020; financial information and certain other data are provided as of the dates specified. This Disclosure Framework can also be found at www.dtcc.com. For further information, please contact [email protected]. Page 2 DTCC Public (White) THE DEPOSITORY TRUST COMPANY: Disclosure Framework for Covered Clearing Agencies and Financial Market Infrastructures Table of Contents Executive Summary ......................................................................................................................... 5 Summary of Major Changes since the Last Update of the Disclosure ............................................ 6 General Background of DTC and Key Metrics ............................................................................... 7 Principle-by-Principle and Standard-by-Standard Summary Narrative Disclosure ....................... 14 Principle 1: -

Federal Register/Vol. 83, No. 156/Monday, August 13, 2018
Federal Register / Vol. 83, No. 156 / Monday, August 13, 2018 / Proposed Rules 39923 these alternative controls on specific Registration’’ and RIN number 3038– SUPPLEMENTARY INFORMATION: types of spraying or fogging systems AE65, by any of the following methods: Table of Contents (including ‘‘parts,’’ ‘‘components,’’ • CFTC Comments Portal: https:// ‘‘accessories,’’ and ‘‘attachments’’ comments.cftc.gov. Select the ‘‘Submit I. Background therefor) that are currently being Comments’’ link for this rulemaking and A. Project KISS manufactured and/or sold or that are follow the instructions on the Public B. Statutory and Regulatory Framework for Swaps Execution and Clearing likely to be manufactured and/or sold in Comment Form. • C. Statutory and Regulatory Requirements the foreseeable future. Comments on Mail: Send to Christopher for Registration and Operation of DCOs option #4 (where the ECCN 2B352.i Kirkpatrick, Secretary of the II. Proposed Amendments to Part 39 control text would include the term Commission, Commodity Futures A. Regulation 39.1—Scope ‘‘specially designed’’) should not only Trading Commission, Three Lafayette B. Regulation 39.2—Definitions address this option with reference to the Centre, 1155 21st Street NW, C. Regulation 39.6—Exemption Provisions four criteria described above, but also Washington, DC 20581. D. Regulation 39.9—Scope identify any performance levels, • Hand Delivery/Courier: Follow the III. Proposed Amendments to Part 140— same instructions as for Mail, above. Delegations of Authority characteristics, or functions that clearly IV. Request for Comments distinguish commercial spraying or Please submit your comments using V. Consideration of Costs and Benefits fogging systems from those systems only one of these methods. -

Ministry of the Environment and Forest Resources
MINISTRY OF THE ENVIRONMENT AND FOREST RESOURCES SECRETARIAT GENERAL DEPARTMENT OF WILDLIFE AND GAME TOGO REPUBLIC Work-Liberty-Homeland PRESENTATION OF OPINIONS Modalities for operation of the Clearing-house mechanism on access and benefit-sharing: For the ABS Clearing-house mechanism to run smoothly, Togo thinks countries should be equipped with computerized equipment for their coordination structure and a permanent internet connection for their national ABS clearing-house mechanism. Togo suggests that training workshops for managers from this clearing-house mechanism should be organized both at national and regional levels without neglecting technical, scientific and legal capacity-building in all aspects of ABS topics so managers can take part in implementing the Nagoya Protocol on access and benefit sharing. Measures aimed at capacity building, strengthening and developing human resources and institutional capacity in developing countries: In Togo’s view, the areas for capacity building and development which should be highlighted at national level include the following: Creation of national ABS management structures; Training human resources in research; Provision of suitable material resources; Supporting the implementation of suitable research programmes; Development of bilateral and multilateral cooperation programmes; Strengthening institutional capacity; Awareness raising, participation and education at all levels (decision-makers, users, owners of traditional knowledge and the general public...). Measures aimed at raising -

Final Report of the Cybersecurity Subcommittee
HOMELAND SECURITY ADVISORY COUNCIL FINAL REPORT OF THE CYBERSECURITY SUBCOMMITTEE: Part I - Incident Response June 2016 Page | 1 This page is intentionally left blank. This publication is presented on behalf of the Homeland Security Advisory Council, Cybersecurity Subcommittee, co-chaired by Steve Adegbite, Juliette Kayyem, Jeff Moss and Dr. Paul Stockton as Part I – Incident Response of the final report and recommendations to the Secretary of the Department of Homeland Security, Jeh C. Johnson. <Signature on file> <Signature on file> ______________________________ _________________________________ Steve Adegbite Juliette Kayyem Chief Information Officer Founder E*Trade Financial Corp Kayyem Solutions, LLC <Signature on file> <Signature on file> ______________________________ _________________________________ Jeff Moss Dr. Paul Stockton Found Managing Director Black Hat and DEF CON Conferences Sonecon LLC This page is intentionally left blank. CYBERSECURITY SUBCOMMITTEE MEMBERS: Incident Response Group Steve Adegbite (Co-Chair) – Chief Information Security Officer, E*TRADE Financial Corporation; Member of Homeland Security Advisory Council Juliette Kayyem (Co-Chair) – Founder, Kayyem Solutions, LLC; Member of Homeland Security Advisory Council Jeff Moss (Co-Chair) – Founder of Black Hat and DEF CON Conferences; Member of Homeland Security Advisory Council Paul Stockton (Co-Chair) – Managing Director, Sonecon LLC; Member of Homeland Security Advisory Council Incident Response Group Barry Bates – Executive Vice President at National Defense -

S. 2779 [Report No
II Calendar No. 402 116TH CONGRESS 2D SESSION S. 2779 [Report No. 116–193] To establish the Federal Clearinghouse on School Safety Best Practices, and for other purposes. IN THE SENATE OF THE UNITED STATES NOVEMBER 5, 2019 Mr. JOHNSON (for himself, Mr. SCOTT of Florida, and Mr. RUBIO) introduced the following bill; which was read twice and referred to the Committee on Homeland Security and Governmental Affairs JANUARY 6, 2020 Reported by Mr. JOHNSON, with amendments [Omit the part struck through and insert the part printed in italic] A BILL To establish the Federal Clearinghouse on School Safety Best Practices, and for other purposes. 1 Be it enacted by the Senate and House of Representa- 2 tives of the United States of America in Congress assembled, 3 SECTION 1. SHORT TITLE. 4 This Act may be cited as the ‘‘Luke and Alex School 5 Safety Act of 2019’’. VerDate Sep 11 2014 22:36 Jan 06, 2020 Jkt 099200 PO 00000 Frm 00001 Fmt 6652 Sfmt 6201 E:\BILLS\S2779.RS S2779 2 1 SEC. 2. FEDERAL CLEARINGHOUSE ON SCHOOL SAFETY 2 BEST PRACTICES. 3 (a) IN GENERAL.—Subtitle A of title XXII of the 4 Homeland Security Act of 2002 (6 U.S.C. 651 et seq.) 5 is amended by inserting after section 2214 the following: 6 ‘‘SEC. 2215. FEDERAL CLEARINGHOUSE ON SCHOOL SAFETY 7 BEST PRACTICES. 8 ‘‘(a) ESTABLISHMENT.— 9 ‘‘(1) IN GENERAL.—The Secretary, in coordina- 10 tion with the Secretary of Education, the Attorney 11 General, and the Secretary of Health and Human 12 Services, shall establish a Federal Clearinghouse on 13 School Safety Best Practices (in this section referred 14 to as the ‘Clearinghouse’) within the Department. -

The Ephemera Prize 2019 the Ephemera Prize Is Awarded Annually in Conjunction with the Eudora Welty Writers’ Symposium at Mississippi University for Women
The Ephemera Prize 2019 The Ephemera Prize is awarded annually in conjunction with the Eudora Welty Writers’ Symposium at Mississippi University for Women. The W is extremely grateful to the Robert M. Hearin Foundation for the support they have provided for the prize and the symposium over many years. In 2018 the contest received 87 entries from 5 schools around Mississippi. The winners were each awarded a $200 prize and invited to read their winning submissions before the symposium audience. Five winners and ten honorable mentions were also invited to lunch with the symposium authors. School groups were invited to attend the symposium, which is free and open to the public. High school or home school students in grades 10-12 in Mississippi and nearby states were invited to write poems, stories, or essays on the Symposium and Ephemera Prize theme or Eudora Welty’s story “Why I Live at the P. O.” which inspired the theme. Students from other states may participate if an alumna or alumnus of The W sponsors them by writing a letter. © 2019 Mississippi University for Women All rights revert to the authors after publication. 2019 Judges Cary Holladay, author of Brides in the Sky T. J. Anderson III, author of Devonte Travels the Sorry Route The current Ephemera Prize theme and contest rules can be found on our website: www.muw.edu/welty/ephemeraprize Cover: Moon over Columbus The Ephemera Prize 2019 “But Here I am, and Here I’ll Stay” Claiming Our Place in the South Felicity Browning, “Hometown Wilted” 4 The Mississippi School for Mathematics -

Transfer of Federal Spectrum Through Overlay Licenses
Sweeten the Deal Transfer of Federal Spectrum through Overlay Licenses Brent Skorup August 2015 MERCATUS WORKING PAPER Brent Skorup. “Sweeten the Deal: Transfer of Federal Spectrum through Overlay Licenses.” Mercatus Working Paper, Mercatus Center at George Mason University, Arlington, VA, August 2015. Abstract The largest challenge in wireless telecommunications policy is transferring spectrum from inefficient legacy operators such as the federal government to bandwidth-hungry wireless broadband operators. Delay results in annual consumer welfare losses totaling hundreds of billions of dollars. One solution would be to auction overlay licenses to commercial bidders and give spectrum incumbents a clearing deadline. Overlay licenses reorder property rights and give incumbents the ability to sell the possessory rights to their frequencies. An alternative reform proposal from a 2012 President’s Council of Advisors on Science and Technology report recommends relying on complex spectrum-sharing technologies in order to avoid clearing agencies from their spectrum. Such a proposal would take decades to implement, would not encourage efficient government use of spectrum, and would likely degenerate into regulatory failure. In contrast, the PCS and AWS-1 auctions by the FCC show that overlay licenses permit commercial deployment of wireless technologies in encumbered spectrum within a few years. JEL codes: D440, D450, H110, H540, K000, K230, L330 Keywords: spectrum, telecommunications, NTIA, FCC, overlay license, wireless, frequencies, incentives, auctions, dynamic spectrum sharing, PCAST Author Affiliation and Contact Information Brent Skorup Research Fellow Mercatus Center at George Mason University [email protected] Acknowledgments I would like to extend special thanks to Thomas Hazlett, whose conversation precipitated this paper. -

CITY of GRIFFIN, GEORGIA Street Striping
CITY OF GRIFFIN, GEORGIA REQUEST FOR QUOTE BID #12-014 For Street Striping For all questions about this Bid contact: Cindy Fay, Purchasing Coordinator [email protected] Deadline: Friday, March 2, 2012 at 2:00 P.M. CITY OF GRIFFIN, GEORGIA 12-014 Street Striping 1. SECTION I – BID INFORMATION 1.1. PURPOSE The City of Griffin (City) is seeking bids from qualified organizations to provide materials, equipment, labor and services necessary for striping work on various roadways in the City. 1.2. SCHEDULE This Request for Proposal will be governed by the following schedule: DATES Release of Request Friday, February 24, 2012 Pre-Bid Meeting none Bids due Friday, March 2, 2012 by 2:00 PM Public Opening * no * This is NOT a sealed bid; submissions may be emailed to [email protected] (subject line MUST contain 12-014 Street Striping RFQ), faxed to 678-692-0402 or mailed to City of Griffin, Purchasing: 12-014 Street Striping RFQ, PO Box T, Griffin, GA 30224. Responses may be submitted at any time, but must be received BEFORE Friday, March 2, 2012 at 2PM. 1.3. SCOPE OF WORK 1.3.1. All labor, material, equipment and any traffic control necessary to complete the project shall be included in the base amount bid. 1.3.2. All quantities shown are estimates; it is the bidder’s responsibility to confirm length measurements. Final payment will be for actual quantities furnished in accordance with the requirements of this Request. 1.3.3. All striping shall be in accordance with the specifications of the Georgia Department of Transportation and the Manual of Uniform Traffic Control Devices for Streets and Highways (MUTCD). -

Port of Beirut Assessment (Extended)
MIDDLE EAST ECONOMIC GROWTH BEST PRACTICES PROJECT (MEG) Port of Beirut Assessment Final Report February 15, 2021 DISCLAIMER This report was produced for review by the United States Agency for International Development. It was prepared by the USAID Middle East Economic Growth Best Practices (USAID/MEG) Project implemented by The Pragma Corporation. The author's views expressed in this publication do not necessarily reflect the views of the United States Agency for International Development or the United States Government. Prepared for the United States Agency for International Development, USAID Order AID- OAA–M-17- 00007 USAID ME Bureau Office of Economic Growth Middle East Economic Growth Best Practices Project (MEG) The Pragma Corporation Principal Contact: Paul Davis 116 East Broad Street Falls Church, Virginia 22046 TABLE OF CONTENTS Executive Summary ................................................................................................... 1 I. POB Governance and Administration. ....................................................................................... 1 II. Port Development Options. ......................................................................................................... 3 III. Restoring and Enhancing POB Operations. ............................................................................... 4 IV. Trade Facilitation. ............................................................................................................................ 8 Port of Beirut Assessment ..................................................................................................................13