Database Machines in Support of Very Large Databases
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Oracle Database VLDB and Partitioning Guide, 11G Release 2 (11.2) E25523-01
Oracle® Database VLDB and Partitioning Guide 11g Release 2 (11.2) E25523-01 September 2011 Oracle Database VLDB and Partitioning Guide, 11g Release 2 (11.2) E25523-01 Copyright © 2008, 2011, Oracle and/or its affiliates. All rights reserved. Contributors: Hermann Baer, Eric Belden, Jean-Pierre Dijcks, Steve Fogel, Lilian Hobbs, Paul Lane, Sue K. Lee, Diana Lorentz, Valarie Moore, Tony Morales, Mark Van de Wiel This software and related documentation are provided under a license agreement containing restrictions on use and disclosure and are protected by intellectual property laws. Except as expressly permitted in your license agreement or allowed by law, you may not use, copy, reproduce, translate, broadcast, modify, license, transmit, distribute, exhibit, perform, publish, or display any part, in any form, or by any means. Reverse engineering, disassembly, or decompilation of this software, unless required by law for interoperability, is prohibited. The information contained herein is subject to change without notice and is not warranted to be error-free. If you find any errors, please report them to us in writing. If this is software or related documentation that is delivered to the U.S. Government or anyone licensing it on behalf of the U.S. Government, the following notice is applicable: U.S. GOVERNMENT RIGHTS Programs, software, databases, and related documentation and technical data delivered to U.S. Government customers are "commercial computer software" or "commercial technical data" pursuant to the applicable Federal Acquisition Regulation and agency-specific supplemental regulations. As such, the use, duplication, disclosure, modification, and adaptation shall be subject to the restrictions and license terms set forth in the applicable Government contract, and, to the extent applicable by the terms of the Government contract, the additional rights set forth in FAR 52.227-19, Commercial Computer Software License (December 2007). -
Data Warehouse Fundamentals for Storage Professionals – What You Need to Know EMC Proven Professional Knowledge Sharing 2011
Data Warehouse Fundamentals for Storage Professionals – What You Need To Know EMC Proven Professional Knowledge Sharing 2011 Bruce Yellin Advisory Technology Consultant EMC Corporation [email protected] Table of Contents Introduction ................................................................................................................................ 3 Data Warehouse Background .................................................................................................... 4 What Is a Data Warehouse? ................................................................................................... 4 Data Mart Defined .................................................................................................................. 8 Schemas and Data Models ..................................................................................................... 9 Data Warehouse Design – Top Down or Bottom Up? ............................................................10 Extract, Transformation and Loading (ETL) ...........................................................................11 Why You Build a Data Warehouse: Business Intelligence .....................................................13 Technology to the Rescue?.......................................................................................................19 RASP - Reliability, Availability, Scalability and Performance ..................................................20 Data Warehouse Backups .....................................................................................................26 -

Security on the Mainframe Stay Connected to IBM Redbooks
Front cover Security on the IBM Mainframe Operating system and application security IBM Security Blueprint and Framework IBM mainframe security concepts Karan Singh Lennie Dymoke-Bradshaw Thomas Castiglion Pekka Hanninen Vincente Ranieri Junior Patrick Kappeler ibm.com/redbooks International Technical Support Organization Security on the IBM Mainframe April 2010 SG24-7803-00 Note: Before using this information and the product it supports, read the information in “Notices” on page ix. First Edition (April 2010) This edition applies to the IBM System z10 Enterprise Class server, the IBM System z10 Business Class server, and Version 1, Release 11, Modification 0 of z/OS (product number 5694-A01). © Copyright International Business Machines Corporation 2010. All rights reserved. Note to U.S. Government Users Restricted Rights -- Use, duplication or disclosure restricted by GSA ADP Schedule Contract with IBM Corp. Contents Notices . ix Trademarks . .x Preface . xi The team who wrote this book . xi Now you can become a published author, too! . xii Comments welcome. xii Stay connected to IBM Redbooks . xiii Part 1. Introduction . 1 Chapter 1. Introduction. 3 1.1 IBM Security Framework. 4 1.1.1 People and identity . 5 1.1.2 Data and information. 5 1.1.3 Application and process . 5 1.1.4 Network, server, and endpoint . 5 1.1.5 Physical Infrastructure . 6 1.2 Framework and Blueprint . 7 1.3 IBM Security Blueprint. 7 Chapter 2. Security of the IBM Mainframe: yesterday and today . 13 2.1 Operating systems . 14 2.1.1 z/OS operating system family . 14 2.1.2 z/VM Hypervisor family . -

Mapping out the DBMS Territory
DATA BASE Mapping out the DBMS territory by Dr. George Schussel, stant both in terms of new product environment and should include the COP announcements and users since following: 1975. Of companies already using a • A DBMS offering data indepen Data base and data management DBMS product, 85 percent of these dence products have changed dramatically are not CODASYL, so it seems clear that CODASYL DDL and DML • A data dictionary defining and in the last several years. New hard controlling the data environment ware and software technologies standards will not be adopted by the marketplace, at least in their cur • A query language allowing user have greatly changed the character personnel access to the data base and number of products available. rent form. Just as the oil crisis hit the auto Mainframe DBMS • A report-generating system al makers, the "productivity crisis" The market for full-function trans lowing simplified programming has hit the software suppliers mar action processing DBMS, with their generation of reports ket. required high-level technical data • A screen mapper allowing gener base administration gurus and large ation of data entry screens by a In the 1970s there were no more simple example process than two dozen widely marketed mainframes, is still active but ex DBMS product lines. Non-IBM DP tremely competitive. Successful • A user language that is high -level, easy to use and an alternative to shops, using equipment such as vendors of this type of product have procedural languages such as Univac, Honeywell or Burroughs, COBOL and PL/l. simply took the DBMS offered by the hardware vendor. -
Study Material for B.Sc.Cs Dataware Housing and Mining Semester - Vi, Academic Year 2020-21
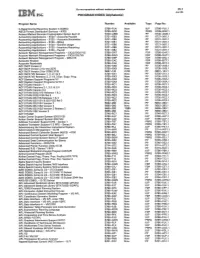
STUDY MATERIAL FOR B.SC.CS DATAWARE HOUSING AND MINING SEMESTER - VI, ACADEMIC YEAR 2020-21 UNIT CONTENT PAGE Nr I DATA WARE HOUSING 03 II BUSINESS ANALYSIS 10 III DATA MINING 18 IV ASSOCIATION RULE MINING AND CLASSIFICATION 35 V CLUSTER ANALYSIS 53 Page 1 of 66 STUDY MATERIAL FOR B.SC.CS DATAWARE HOUSING AND MINING SEMESTER - VI, ACADEMIC YEAR 2020-21 UNIT I: DATA WAREHOUSING Data warehousing Components: ->Overall Architecture Data warehouse architecture is Based on a relational database management system server that functions as the central repository (a central location in which data is stored and managed) for informational data In the data warehouse architecture, operational data and processing is separate and data warehouse processing is separate. Central information repository is surrounded by a number of key components. These key components are designed to make the entire environment- (i) functional, (ii) manageable and (iii) accessible by both the operational systems that source data into warehouse by end-user query and analysis tools. Page 2 of 66 STUDY MATERIAL FOR B.SC.CS DATAWARE HOUSING AND MINING SEMESTER - VI, ACADEMIC YEAR 2020-21 The source data for the warehouse comes from the operational applications As data enters the data warehouse, it is transformed into an integrated structure and format The transformation process may involve conversion, summarization, filtering, and condensation of data Because data within the data warehouse contains a large historical component the data warehouse must b capable of holding and managing large volumes of data and different data structures for the same database over time. ->Data Warehouse Database Central data warehouse database is a foundation for data warehousing environment. -

Objex, Inc. Product Overview April 2015
WHERE COMMON SENSE MEETS UNCOMMON INGENUITY ObjEx, Inc. Product Overview April 2015 ObjEx INC PO Box 25608 Scottsdale, AZ 85255-5608 Tel: (480) 588-7776 http://www.obj-ex.com ObjEx, Inc. Product Overview Table of Contents Contents TABLE OF CONTENTS I OVERVIEW 1 PACKAGED SOFTWARE 1 SERVICES 2 OBJEX XMLQUERY 4 OBJEX XMLPUBLISHER 5 OBJEX PROGRAM CALL 6 ABOUT OBJEX 7 2015 ObjEx, Inc. Page i ObjEx, Inc. Product Overview Overview ObjEx was founded in 1996 by former Cullinet and CA executives and employees who have more than 65 years of IDMS experience and 20 years as IDMS Integrators. We provide software and services to our clients which include many large organizations. Packaged Software Our packaged software is conceived and developed as a result of our integration experiences related to Service Oriented Architecture, cloud computing calls to and from IDMS, trigger- based data publishing, and replication. ObjEx products are focused on Service Oriented Architecture (SOA) and are designed to participate within the latest n-tier architectures. ObjEx has been used to: Extend existing IDMS systems with new modern application components either direct client/server or through SOA, all in one database. Allow existing IDMS applications to call out to internal and external web services. Provide modern applications the ability to use existing IDMS DC-Cobol and ADSO programs as web services. This allows the reuse of business rules without the hassles of screen scraping. Push IDMS data to non-mainframe applications without altering IDMS programs. The products are useful for ERP and warehouse integration, data replication to operational data stores, and data warehousing feeds. -
- -:§';'§: ISG PROGRAM INDEX (Alphabetic)
--- - Do not reproduce without written permission PI.1 ------ ---- Jan 84 :: - -:§';'§: ISG PROGRAM INDEX (Alphabetic) Program Name Number Available Type Page No. A Departmental Reporting System II (ADRS) 5796-PLN Now IUP 5796-PLK.1 A8CS Format Distribution Services - 4700 5799-8QZ Now PRPQ 5799-8QZ.1 Access Method Services Cryptographic Option Re1.1.0 5740-AM8 Now PP 5740-AM8.1 Accounting Applications - 5120 - Accounts Payable 5721-X83 Now PP 5721-X81.1 Accounting Applications - 5120 - Accounts Receivable 5721-X84 Now PP 5721-XB1.1 Accounting Applications - 5120 - Billing 5721-XB1 Now PP 5721-XB1.1 Accounting Applications - 5120 - General Ledger 5721-XB6 Now PP 5721-XB1.1 Accounting Applications - 5120 - Inventory Reporting 5721-XB5 Now PP 5721-XB1.1 Accounting Applications - 5120 - Payroll 5721-XB2 Now PP 5721-XB1.1 Account Network Management Programs - CICS/DOS/VS 5798-DAT Now FDP 5798-DAP.1 Account Network Management Programs - CICS/OS/VS 5798-DAQ Now FDP 5798-DAP.1 Account Network Management Program - IMS/VS 5798-DBP Now FDP 5798-DBJ.1 Accounts Payable 5798-CAC Now FDP 5798-BCT.1 Accounts Receivable 5798-CAE Now FDP 5798-BCT.1 ACF/NCP Version 2 5735-XX9 Now PP 5735-XX9.1 ACF/NCP Version 2 for the 3275 5735-XX9 Now PP 5735-XX9.1 ACF/NCP Version 3 for 3705/3725 5667-124 4/84 PP 5667-124.1 ACF/NCP/VS Releases 1, 2, 2.1 & 3 5735-XX1 Now PP 5735-XX1.1 ACF/NCP/VS Releases 2,2.1 & 3 Sys. Supp. Prog. 5735-XX3 Now PP 5735-XX3.1 ACF/System Support Programs V2 5735-XXA Now PP 5735-XXA.1 ACF /System Support Programs V2 R1.1 5735-XXA Now PP 5735-XXA.1 -

Public 1 Agenda
© 2013 SAP AG. All rights reserved. Public 1 Agenda Welcome Agenda • Introduction to Dobler Consulting • SAP IQ Roadmap – What to Expect • Q&A Presenters • Courtney Claussen - SAP IQ Product Management • Peter Dobler - CEO Dobler Consulting Closing © 2013 SAP AG. All rights reserved. Public 2 Introduction to Dobler Consulting Dobler Consulting is a leading information technology and database services company, offering a broad spectrum of services to their clients; acting as your Trusted Adviser, Provide License Sales, Architectural Review and Design Consulting, Optimization Services, High Availability review and enablement, Training and Cross Training, and lastly ongoing support and preventative maintenance. Founded in 2000, the Tampa consulting firm specializes in SAP/Sybase, Microsoft SQL Server, and Oracle. Visit us online at www.doblerconsulting.com, or contact us at 813 322 3240, or [email protected]. © 2013 SAP AG. All rights reserved. Public 3 Your Data is Your DNA, Dobler Consulting Focus Areas Strategic Database Consulting SAP VAR D&T DBA Database Managed Training Services Programs Cross-Platform Expertise SAP Sybase® SQL Server® Oracle® © 2013 SAP AG. All rights reserved. Public 4 What’s Ahead ISUG-TECH Annual Conference April 14-17, Atlanta • Register at http://my.isug.com/conference/registration • Early Bird ending 2/28/14 (free hotel room with registration) SAPPHIRENOW Annual Conference June 3-5, Orlando • Come visit our kiosk in the exhibition hall © 2013 SAP AG. All rights reserved. Public 5 SAP IQ Roadmap Dobler Events Webinar Courtney Claussen / SAP IQ Product Management February 27, 2014 Disclaimer This presentation outlines our general product direction and should not be relied on in making a purchase decision. -

Requirements for XML Document Database Systems Airi Salminen Frank Wm
Requirements for XML Document Database Systems Airi Salminen Frank Wm. Tompa Dept. of Computer Science and Information Systems Department of Computer Science University of Jyväskylä University of Waterloo Jyväskylä, Finland Waterloo, ON, Canada +358-14-2603031 +1-519-888-4567 ext. 4675 [email protected] [email protected] ABSTRACT On the other hand, XML will also be used in ways SGML and The shift from SGML to XML has created new demands for HTML were not, most notably as the data exchange format managing structured documents. Many XML documents will be between different applications. As was the situation with transient representations for the purpose of data exchange dynamically created HTML documents, in the new areas there is between different types of applications, but there will also be a not necessarily a need for persistent storage of XML documents. need for effective means to manage persistent XML data as a Often, however, document storage and the capability to present database. In this paper we explore requirements for an XML documents to a human reader as they are or were transmitted is database management system. The purpose of the paper is not to important to preserve the communications among different parties suggest a single type of system covering all necessary features. in the form understood and agreed to by them. Instead the purpose is to initiate discussion of the requirements Effective means for the management of persistent XML data as a arising from document collections, to offer a context in which to database are needed. We define an XML document database (or evaluate current and future solutions, and to encourage the more generally an XML database, since every XML database development of proper models and systems for XML database must manage documents) to be a collection of XML documents management. -

A Methodology for Evaluating Relational and Nosql Databases for Small-Scale Storage and Retrieval
Air Force Institute of Technology AFIT Scholar Theses and Dissertations Student Graduate Works 9-1-2018 A Methodology for Evaluating Relational and NoSQL Databases for Small-Scale Storage and Retrieval Ryan D. Engle Follow this and additional works at: https://scholar.afit.edu/etd Part of the Databases and Information Systems Commons Recommended Citation Engle, Ryan D., "A Methodology for Evaluating Relational and NoSQL Databases for Small-Scale Storage and Retrieval" (2018). Theses and Dissertations. 1947. https://scholar.afit.edu/etd/1947 This Dissertation is brought to you for free and open access by the Student Graduate Works at AFIT Scholar. It has been accepted for inclusion in Theses and Dissertations by an authorized administrator of AFIT Scholar. For more information, please contact [email protected]. A METHODOLOGY FOR EVALUATING RELATIONAL AND NOSQL DATABASES FOR SMALL-SCALE STORAGE AND RETRIEVAL DISSERTATION Ryan D. L. Engle, Major, USAF AFIT-ENV-DS-18-S-047 DEPARTMENT OF THE AIR FORCE AIR UNIVERSITY AIR FORCE INSTITUTE OF TECHNOLOGY Wright-Patterson Air Force Base, Ohio DISTRIBUTION STATEMENT A. Approved for public release: distribution unlimited. AFIT-ENV-DS-18-S-047 The views expressed in this paper are those of the author and do not reflect official policy or position of the United States Air Force, Department of Defense, or the U.S. Government. This material is declared a work of the U.S. Government and is not subject to copyright protection in the United States. i AFIT-ENV-DS-18-S-047 A METHODOLOGY FOR EVALUATING RELATIONAL AND NOSQL DATABASES FOR SMALL-SCALE STORAGE AND RETRIEVAL DISSERTATION Presented to the Faculty Department of Systems and Engineering Management Graduate School of Engineering and Management Air Force Institute of Technology Air University Air Education and Training Command In Partial Fulfillment of the Requirements for the Degree of Doctor of Philosophy Ryan D. -

The Impact of Converging Information Technologies. Proceedings of the CAUSE National Conference (Monterey, California, December 9-12, 1986)
DOCUMENT RESUME ED 283 430 HE 020 404 TITLE The Impact of Converging Information Technologies. Proceedings of the CAUSE National Conference (Monterey, California, December 9-12, 1986). INSTITUTION CAUSE, Boulder, Colo. PUB DATE Dec 86 NOTE 586p.; Photographs may not reproduce well. PUB TYFE Collected Works - Conference Proceedings (021) Viewpoints (120) EDRS PRICE MF03/PC24 Plus Postage. DESCRIPTORS *College Administration; College Planning; *Computer Oriented Programs; *Data Processing; Higher Education; Information Networks; *Information Technology; *Management Information Systems; *Microcomputers; Telecommunications; Users (Information) ABSTRACT Proceedings of a 1986 CAUSE conference on the impact of converging information technologies are presented. Topics of conferenco papers include: policy issues in higher education, planning and information technology, people issues in information technology, telecommunications/networking, special environments, microcomputer_issues and applications, and managing academic computing. Some of the papers (with the authors) are: "Distributed Access to Central Data: A Policy Issue" (Eugene W. Carson) "Distributed Access to Central Data: The Cons" (Katherine P. Hall);_ "Overselling Technology: Suppose You Gave a Computer Revolution and Nobody Came?" (Linda Fleit); "Selling the President on the Computing Plan: Strategic Funds Programming" (John L. Green); "A Preliminary Report of Institutional Experieace_with MIS Software" (Paul J. Plourde); "Policy Issues Surrounding Decisions to Use Mainframe or Micros" (Phyllis A. Sholtysi; "Alternative Models for the Delivery of Computing and Communications Services" (E. Michael Staman) "Converging Technologies Require Flexible Organizations" (Carole Barone); "Student Computing and Policy Issues" (Gerald McLaughlin, John A. Muffo, Ralph O. Mueller, Alan R. Sack); "Strategic Planning for Information Resources Management: Putting the Building Blocks Together" (James I. Penrod, Michael G. Dolence); "Planning for Administrative Computing in a Networked Environment" (Cynthia S. -

ICL Technical Journal Volume 6 Issue 3
TECHNICAL JOURNAL Volume 6 Issue 3 May 1989 Published by INTERNATIONAL COMPUTERS LIMITED at OXFORD UNIVERSITY PRESS ICL TCPU M IPA I The ICL Technical Journal is published twice a year by ' . International Computers Limited at Oxford University JOURNAL Press Editor J. Howlett ICL House, Putney, London SW15 ISW, UK Editorial Board J. Howlett (Editor) F.F. Land H.M. Cropper (F International) (London Business School) D.W. Davies, FRS K.H. Macdonald G.E. Felton M.R. Miller M.D. Godfrey (British Telecom Research (Imperial College, London Laboratories) University) J.M.M. Pinkerton C.H.L. Goodman E.C.P. Portman (STCTechnology Ltd B.C. Warboys (University and King’s College,) of Manchester) London) All correspondence and papers to be considered for publication should be addressed to the Editor. The views expressed in the papers are those of the authors and do not necessarily represent ICL policy. 1989 subscription rates: annual subscription £35 UK, £44 rest of world, US $88 N. America; single issues £17 UK, £22 rest of world, US $38 N. America. Orders with remittances should be sent to the Journals Subscriptions Department, Oxford University Press, Walton Street, Oxford 0X2 6DP, UK. This publication is copyright under the Berne Convention and the Inter national Copyright Convention. All rights reserved. Apart from any copying under the UK Copyright Act 1956, part 1, section 7, whereby a single copy of an article may be supplied, under certain conditions, for the purposes of research or private study, by a library of a class prescribed by the UK Board of Trade Regulations (Statutory Instruments 1957, No.