SPI Annual Report 2015
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Creating Awareness for the Use of Opensource Systems in the Public Sector in Afghanistan
A Service of Leibniz-Informationszentrum econstor Wirtschaft Leibniz Information Centre Make Your Publications Visible. zbw for Economics Hussini, Sayed Jahed (Ed.); Finke, Wolfgang F. (Ed.) Research Report Creating Awareness for the Use of OpenSource Systems in the Public Sector in Afghanistan. Workshop Proceedings, Sept. 15-17, 2012, Kabul/ Afghanistan Wirtschaftswissenschaftliche Schriften, No. 02/2013 Provided in Cooperation with: Ernst-Abbe-Hochschule Jena – University of Applied Sciences, Department of Business Administration Suggested Citation: Hussini, Sayed Jahed (Ed.); Finke, Wolfgang F. (Ed.) (2013) : Creating Awareness for the Use of OpenSource Systems in the Public Sector in Afghanistan. Workshop Proceedings, Sept. 15-17, 2012, Kabul/Afghanistan, Wirtschaftswissenschaftliche Schriften, No. 02/2013, ISBN 3-939046-32-9, Ernst-Abbe-Fachhochschule, Fachbereich Betriebswirtschaft, Jena, http://nbn-resolving.de/urn:nbn:de:gbv:27-20130408-110626-4 This Version is available at: http://hdl.handle.net/10419/71197 Standard-Nutzungsbedingungen: Terms of use: Die Dokumente auf EconStor dürfen zu eigenen wissenschaftlichen Documents in EconStor may be saved and copied for your Zwecken und zum Privatgebrauch gespeichert und kopiert werden. personal and scholarly purposes. Sie dürfen die Dokumente nicht für öffentliche oder kommerzielle You are not to copy documents for public or commercial Zwecke vervielfältigen, öffentlich ausstellen, öffentlich zugänglich purposes, to exhibit the documents publicly, to make them machen, vertreiben oder anderweitig nutzen. publicly available on the internet, or to distribute or otherwise use the documents in public. Sofern die Verfasser die Dokumente unter Open-Content-Lizenzen (insbesondere CC-Lizenzen) zur Verfügung gestellt haben sollten, If the documents have been made available under an Open gelten abweichend von diesen Nutzungsbedingungen die in der dort Content Licence (especially Creative Commons Licences), you genannten Lizenz gewährten Nutzungsrechte. -

Hacker Public Radio
hpr0001 :: Introduction to HPR hpr0002 :: Customization the Lost Reason hpr0003 :: Lost Haycon Audio Aired on 2007-12-31 and hosted by StankDawg Aired on 2008-01-01 and hosted by deepgeek Aired on 2008-01-02 and hosted by Morgellon StankDawg and Enigma talk about what HPR is and how someone can contribute deepgeek talks about Customization being the lost reason in switching from Morgellon and others traipse around in the woods geocaching at midnight windows to linux Customization docdroppers article hpr0004 :: Firefox Profiles hpr0005 :: Database 101 Part 1 hpr0006 :: Part 15 Broadcasting Aired on 2008-01-03 and hosted by Peter Aired on 2008-01-06 and hosted by StankDawg as part of the Database 101 series. Aired on 2008-01-08 and hosted by dosman Peter explains how to move firefox profiles from machine to machine 1st part of the Database 101 series with Stankdawg dosman and zach from the packetsniffers talk about Part 15 Broadcasting Part 15 broadcasting resources SSTRAN AMT3000 part 15 transmitter hpr0007 :: Orwell Rolled over in his grave hpr0009 :: This old Hack 4 hpr0008 :: Asus EePC Aired on 2008-01-09 and hosted by deepgeek Aired on 2008-01-10 and hosted by fawkesfyre as part of the This Old Hack series. Aired on 2008-01-10 and hosted by Mubix deepgeek reviews a film Part 4 of the series this old hack Mubix and Redanthrax discuss the EEpc hpr0010 :: The Linux Boot Process Part 1 hpr0011 :: dd_rhelp hpr0012 :: Xen Aired on 2008-01-13 and hosted by Dann as part of the The Linux Boot Process series. -

Software in the Public Interest, Inc. 2011-2012 Annual Report
Software in the Public Interest, Inc. 2011-2012 Annual Report 1st July 2012 To the membership, board and friends of Software in the Public Interest, Inc: As mandated by Article 8 of the SPI Bylaws, I respectfully submit this annual report on the activities of Software in the Public Interest, Inc. and extend my thanks to all of those who contributed to the mission of SPI in the past year. { Jonathan McDowell, SPI Secretary 1 Contents 1 President's Welcome3 2 Committee Reports4 2.1 Membership Committee.......................4 2.1.1 Statistics...........................4 3 Board Report5 3.1 Board Members............................5 3.2 Board Changes............................6 3.3 Elections................................6 4 Treasurer's Report7 4.1 Income Statement..........................7 4.2 Balance Sheet.............................9 5 Member Project Reports 11 5.1 New Associated Projects....................... 11 5.1.1 Drizzle............................. 11 5.1.2 Arch Linux.......................... 11 5.1.3 FreedomBox......................... 11 5.1.4 Fluxbox............................ 12 5.1.5 Haskell.org.......................... 12 5.1.6 FFmpeg............................ 12 A About SPI 13 2 Chapter 1 President's Welcome { Bdale Garbee, SPI President 3 Chapter 2 Committee Reports 2.1 Membership Committee The membership committee was extended to cover the entire board. 2.1.1 Statistics At the time of writing (July 10th) the current membership status is: NC Applicants Pending Email Approval 94 NC Members 485 Contrib Membership Applications 11 Contrib Members 489 Application Managers 9 On 1st July 2011 we had 445 contributing and 436 non-contributing members. On 1st July 2011 there were 481 contributing members and 452 non-contributing members. -

Praktikum Iz Softverskih Alata U Elektronici 2020/2021
PRAKTIKUM IZ SOFTVERSKIH ALATA U ELEKTRONICI 2020/2021 Predrag Pejović 16.01.2021, 10:00 © 2021 Predrag Pejović, This work is licensed under a Creative Commons Attribution-ShareAlike 4.0 International License. Linkovi na primere: OS 1: http://tnt.etf.bg.ac.rs/~oe4sae/softwareinstall.sh OS 2: http://tnt.etf.bg.ac.rs/~oe4sae/primeri-3-2020.zip LATEX 1: http://tnt.etf.bg.ac.rs/~oe4sae/primeri-4-2020.zip LATEX 2: http://tnt.etf.bg.ac.rs/~oe4sae/primeri-5-2020.zip LATEX 3: http://tnt.etf.bg.ac.rs/~oe4sae/primeri-6-2020.zip LATEX 4: http://tnt.etf.bg.ac.rs/~oe4sae/primeri-7-2020.zip Python 1: http://tnt.etf.bg.ac.rs/~oe4sae/primeri-9-2020.py Python 2: http://tnt.etf.bg.ac.rs/~oe4sae/primeri-10-2020.zip Python 3: http://tnt.etf.bg.ac.rs/~oe4sae/primeri-11-2020.zip GNU Octave: http://tnt.etf.bg.ac.rs/~oe4sae/primeri-12-2020.zip SageMath: http://tnt.etf.bg.ac.rs/~oe4sae/primeri-13-2020.zip Alternativni linkovi na primere: OS 1: http://peja.freedombox.rocks/PSAE/softwareinstall.sh OS 2: http://peja.freedombox.rocks/PSAE/primeri-3-2020.zip LATEX 1: http://peja.freedombox.rocks/PSAE/primeri-4-2020.zip LATEX 2: http://peja.freedombox.rocks/PSAE/primeri-5-2020.zip LATEX 3: http://peja.freedombox.rocks/PSAE/primeri-6-2020.zip LATEX 4: http://peja.freedombox.rocks/PSAE/primeri-7-2020.zip Python 1: http://peja.freedombox.rocks/PSAE/primeri-9-2020.py Python 2: http://peja.freedombox.rocks/PSAE/primeri-10-2020.zip Python 3: http://peja.freedombox.rocks/PSAE/primeri-11-2020.zip GNU Octave: http://peja.freedombox.rocks/PSAE/primeri-12-2020.zip SageMath: http://peja.freedombox.rocks/PSAE/primeri-13-2020.zip PRAKTIKUM IZ SOFTVERSKIH ALATA U ELEKTRONICI 2020 PRAKTIKUM IZ SOFTVERSKIH ALATA U ELEKTRONICI 2020 c Predrag Pejović, Lica (i ostali podaci o predmetu): Lica, dopuna, odakle ja u ovome? I dr Predrag Pejović, red. -

Vulnerability Scanners and Penetration Testing
Vulnerability Scanners and Penetration Testing Introduction OBJECTIVE: CompTIA Security+ Domain: Domain 3: Threats and Vulnerabilities CompTIA Security+ Objective Mapping: Objective 3.8: Explain the proper use of penetration testing versus vulnerability scanning. OVERVIEW: In this lab, you will scan a host to discover security holes. Discovering vulnerabilities is critical so they can be patched before attackers compromise your system. Key Term Description OpenVAS an open source vulnerability scanner gaining a higher level of access (possible administrative access) from account with less Privilege escalation permissions and rights Zenmap a GUI front end for nmap, will allow you to scan for open ports and services Metasploit a framework that contains exploits for various information systems nmap a port scanner which will indicate whether ports are open or closed on a remote system Nmap and OpenVAS 1. Click on the External Kali 2 Linux icon on the topology. Type root for the username, and click the Next button. TOPOLOGY MACHINES If the Kali Linux is displaying the time, and not the logon box, press the Enter Key. EXTERNAL KALI 2 USERNAME 2. For the password, type toor (root spelled backwards), and click the Sign In button. EXTERNAL KALI 2 PASSWORD 3. Click the terminal icon (second from the top) to launch the Linux terminal. OPENING THE KALI 2 TERMINAL 4. Type the following command to scan the firewall for open ports, then press Enter. root@kali2:~# nmap 203.0.113.100 NMAP 5. Type the following command, then press Enter to open Zenmap. After Zenmap opens, type 203.0.113.100 in the Target box and then click the Scan button to launch an intense scan. -

Cygwin User's Guide
Cygwin User’s Guide Cygwin User’s Guide ii Copyright © Cygwin authors Permission is granted to make and distribute verbatim copies of this documentation provided the copyright notice and this per- mission notice are preserved on all copies. Permission is granted to copy and distribute modified versions of this documentation under the conditions for verbatim copying, provided that the entire resulting derived work is distributed under the terms of a permission notice identical to this one. Permission is granted to copy and distribute translations of this documentation into another language, under the above conditions for modified versions, except that this permission notice may be stated in a translation approved by the Free Software Foundation. Cygwin User’s Guide iii Contents 1 Cygwin Overview 1 1.1 What is it? . .1 1.2 Quick Start Guide for those more experienced with Windows . .1 1.3 Quick Start Guide for those more experienced with UNIX . .1 1.4 Are the Cygwin tools free software? . .2 1.5 A brief history of the Cygwin project . .2 1.6 Highlights of Cygwin Functionality . .3 1.6.1 Introduction . .3 1.6.2 Permissions and Security . .3 1.6.3 File Access . .3 1.6.4 Text Mode vs. Binary Mode . .4 1.6.5 ANSI C Library . .4 1.6.6 Process Creation . .5 1.6.6.1 Problems with process creation . .5 1.6.7 Signals . .6 1.6.8 Sockets . .6 1.6.9 Select . .7 1.7 What’s new and what changed in Cygwin . .7 1.7.1 What’s new and what changed in 3.2 . -

Legislators of Cyberspace: an Analysis of the Role Of
SHAPING CODE Jay P. Kesan* & Rajiv C. Shah** I. INTRODUCTION ............................................................................................................................ 4 II. THE CASE STUDIES: THE DEVELOPMENT OF CODE WITHIN INSTITUTIONS.............................. 13 A. World Wide Web......................................................................................................... 14 1. Libwww............................................................................................................ 14 2. NCSA Mosaic .................................................................................................. 16 B. Cookies ........................................................................................................................ 21 1. Netscape’s Cookies .......................................................................................... 21 2. The IETF’s Standard for Cookies .................................................................... 24 C. Platform for Internet Content Selection....................................................................... 28 D. Apache......................................................................................................................... 34 III. LEGISLATIVE BODIES: SOCIETAL INSTITUTIONS THAT DEVELOP CODE ................................. 37 A. Universities.................................................................................................................. 38 B. Firms........................................................................................................................... -

Buildsystems and What the Heck for We Actually Use the Autotools
Buildsystems and what the heck for we actually use the autotools Tom´aˇsChv´atal SUSE Packagers team 2013/07/19 Introduction Who the hell is Tom´aˇsChv´atal • SUSE Employee since 2011 - Team lead of packagers team • Packager of Libreoffice and various other stuff for openSUSE • openSUSE promoter and volunteer • Gentoo developer since fall 2008 3 of 37 Autotools process Complete autotools process 5 of 37 Make Why not just a sh script? Always recompiling everything is a waste of time and CPU power 7 of 37 Plain makefile example CC ?= @CC@ CFLAGS ?= @CFLAGS@ PROGRAM = examplebinary OBJ = main.o parser.o output.o $ (PROGRRAM) : $ (OBJ) $ (CC) $ (LDFLAGS) −o $@ $^ main.o: main.c common.h parser.o: parser.c common.h output.o: output.c common.h setup.h i n s t a l l : $ (PROGRAM) # You have to use tabs here $(INSTALL) $(PROGRAM) $(BINDIR) c l e a n : $ (RM) $ (OBJ) 8 of 37 Variables in Makefiles • Variables expanded using $(), ie $(VAR) • Variables are assigned like in sh, ie VAR=value • $@ current target • $<the first dependent file • $^all dependent files 9 of 37 Well nice, but why autotools then • Makefiles can get complex fast (really unreadable) • Lots of details to keep in mind when writing, small mistakes happen fast • Does not make dependencies between targets really easier • Automake gives you automatic tarball creation (make distcheck) 10 of 37 Autotools Simplified autotools process 12 of 37 Autoconf/configure sample AC INIT(example , 0.1, [email protected]) AC CONFIG HEADER([ config .h]) AC PROG C AC PROG CPP AC PROG INSTALL AC HEADER STDC AC CHECK HEADERS([string.h unistd.h limits.h]) AC CONFIG FILES([ Makefile doc/Makefile src/Makefile]) AC OUTPUT 13 of 37 Autoconf syntax • The M4 syntax is quite weird on the first read • It is not interpreted, it is text substitution machine • Lots of quoting is needed, if in doubt add more [] • Everything that does or might contain whitespace or commas has to be quoted • Custom autoconf M4 macros are almost unreadable 14 of 37 Automake bin PROGRAMS = examplebinary examplebinary SOURCES = n s r c /main . -

Vol.11, No. 2, 2011
Applied Computing Review 2 SIGAPP FY’11 Semi-Annual Report July 2010- February 2011 Sung Y. Shin Mission To further the interests of the computing professionals engaged in the development of new computing applications and to transfer the capabilities of computing technology to new problem domains. Officers Chair – Sung Y. Shin South Dakota State University, USA Vice Chair – Richard Chbeir Bourgogne University, Dijon, France Secretary – W. Eric Wong University of Texas, USA Treasurer – Lorie Liebrock New Mexico Institute of Mining and Technology, USA Web Master – Hisham Haddad Kennesaw State University, USA ACM Program Coordinator – Irene Frawley ACM HQ Applied Computing Review 3 Notice to Contributing Authors to SIG Newsletters By submitting your article for distribution in this Special Interest Group publication, you hereby grant to ACM the following non-exclusive, perpetual, worldwide rights. • To publish in print on condition of acceptance by the editor • To digitize and post your article in the electronic version of this publication • To include the article in the ACM Digital Library • To allow users to copy and distribute the article for noncommercial, educational, or research purposes. However, as a contributing author, you retain copyright to your article and ACM will make every effort to refer requests for commercial use directly to you. Status Update SIGAPP's main event for this year will be the Symposium on Applied Computing (SAC) 2011 in Taichung, Taiwan from March 21-24 which will carry the tradition from Switzerland's SAC 2010. This year's SAC preparation has been very successful. More details about incoming SAC 2011 will follow in the next section. -
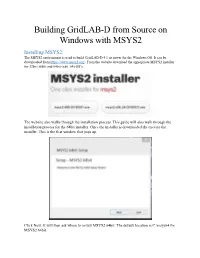
Building Gridlab-D from Source on Windows with MSYS2 Installing MSYS2: the MSYS2 Environment Is Used to Build Gridlab-D 4.1 Or Newer for the Windows OS
Building GridLAB-D from Source on Windows with MSYS2 Installing MSYS2: The MSYS2 environment is used to build GridLAB-D 4.1 or newer for the Windows OS. It can be downloaded from https://www.msys2.org/. From the website download the appropriate MSYS2 installer for 32bit (i686) and 64bit (x86_64) OS’s. The website also walks through the installation process. This guide will also walk through the installation process for the 64bit installer. Once the installer is downloaded the execute the installer. This is the first window that pops up. Click Next. It will then ask where to install MSYS2 64bit. The default location is C:\msys64 for MSYS2 64bit. Once the location has been specified click Next. Then it will ask where to create the program’s shortcuts. Use an existing one or create a new name. Once a destination is chosen click Next. At this point the installer begins to install MSYS2 onto the computer. Once installation is complete click Next. Then click Finish and installation is successful. Setting Up the MSYS2 Environment: To start the MSYS2 environment start msys2.exe. A window like below should pop up. As can be seen MSYS2 provides a Linux-like command terminal and environment for building GNU compliant C/C++ executables for Windows OS’s. When Running the MSYS2 environment for the first time updates will need to be performed. To perform update run $ pacman -Syuu Type “y” and hit enter to continue. If you get a line like the following: Simply close the MSYS2 window and restart the MSYS2 executable. -

Sql Server to Aurora Postgresql Migration Playbook
Microsoft SQL Server To Amazon Aurora with Post- greSQL Compatibility Migration Playbook 1.0 Preliminary September 2018 © 2018 Amazon Web Services, Inc. or its affiliates. All rights reserved. Notices This document is provided for informational purposes only. It represents AWS’s current product offer- ings and practices as of the date of issue of this document, which are subject to change without notice. Customers are responsible for making their own independent assessment of the information in this document and any use of AWS’s products or services, each of which is provided “as is” without war- ranty of any kind, whether express or implied. This document does not create any warranties, rep- resentations, contractual commitments, conditions or assurances from AWS, its affiliates, suppliers or licensors. The responsibilities and liabilities of AWS to its customers are controlled by AWS agree- ments, and this document is not part of, nor does it modify, any agreement between AWS and its cus- tomers. - 2 - Table of Contents Introduction 9 Tables of Feature Compatibility 12 AWS Schema and Data Migration Tools 20 AWS Schema Conversion Tool (SCT) 21 Overview 21 Migrating a Database 21 SCT Action Code Index 31 Creating Tables 32 Data Types 32 Collations 33 PIVOT and UNPIVOT 33 TOP and FETCH 34 Cursors 34 Flow Control 35 Transaction Isolation 35 Stored Procedures 36 Triggers 36 MERGE 37 Query hints and plan guides 37 Full Text Search 38 Indexes 38 Partitioning 39 Backup 40 SQL Server Mail 40 SQL Server Agent 41 Service Broker 41 XML 42 Constraints -

List of NMAP Scripts Use with the Nmap –Script Option
List of NMAP Scripts Use with the nmap –script option Retrieves information from a listening acarsd daemon. Acarsd decodes ACARS (Aircraft Communication Addressing and Reporting System) data in real time. The information retrieved acarsd-info by this script includes the daemon version, API version, administrator e-mail address and listening frequency. Shows extra information about IPv6 addresses, such as address-info embedded MAC or IPv4 addresses when available. Performs password guessing against Apple Filing Protocol afp-brute (AFP). Attempts to get useful information about files from AFP afp-ls volumes. The output is intended to resemble the output of ls. Detects the Mac OS X AFP directory traversal vulnerability, afp-path-vuln CVE-2010-0533. Shows AFP server information. This information includes the server's hostname, IPv4 and IPv6 addresses, and hardware type afp-serverinfo (for example Macmini or MacBookPro). Shows AFP shares and ACLs. afp-showmount Retrieves the authentication scheme and realm of an AJP service ajp-auth (Apache JServ Protocol) that requires authentication. Performs brute force passwords auditing against the Apache JServ protocol. The Apache JServ Protocol is commonly used by ajp-brute web servers to communicate with back-end Java application server containers. Performs a HEAD or GET request against either the root directory or any optional directory of an Apache JServ Protocol ajp-headers server and returns the server response headers. Discovers which options are supported by the AJP (Apache JServ Protocol) server by sending an OPTIONS request and lists ajp-methods potentially risky methods. ajp-request Requests a URI over the Apache JServ Protocol and displays the result (or stores it in a file).