Hello Everyone and Welcome to This Month's TXDPS Cyber Newsletter
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Review of Rogue One: a Star Wars Story
DVD reviews Rogue One: A Star Wars Story (Gareth Edwards US 2016). Walt Disney Studios 2017. Region 1. 2.39:1 widescreen. US$23. Sean Guynes-Vishniac After the release of Revenge of the Sith (Lucas US 2005), the third film in the Star Wars prequel trilogy in 2005, George Lucas and Lucasfilm had no plans to add further feature films to the multi-billion-dollar franchise. This was in part because fans of the original Star Wars trilogy (1977–83) hated the prequels, and because Lucas was now interested in television, starting with the animated series The Clone Wars (2008–14, 2019). When Disney bought Lucasfilm, they announced a new trilogy extending the saga of the Skywalker family, and several standalone non-saga ‘anthology’ films to fill narrative gaps in the universe; Rogue One: A Star Wars Story is the first of these anthology films. Its position raises important questions about the contemporary state of the transmedia sf franchise, while its narrative looks at the limits and possibilities of sf blockbusters’ political work. To provide an easy entry into the franchise’s storyworld, Rogue One offers a cast of new characters that fit (and slightly modify) well-known franchise types: protagonist Jyn Erso (Felicity Jones), for example, pairs the scruffiness of Han Solo with the paternal drama of Luke Skywalker; Chirrut Îmwe (Donnie Yen) takes on the Jedi mystique and mentor role of Obi-Wan Kenobi; K-2SO (Alan Tudyk) is the non-human, comedy-relief sidekick, a cynical update of C-3PO. Cassian Andor (Diego Luna), however, stands out thematically, mixing the scoundrel qualities of Solo with the risky charm of Lando Calrissian, and bringing a moral ambiguity to the normally black-and-white world of Jedi and Sith; perhaps these qualities have led to Andor’s being named as the protagonist of one of the upcoming Star Wars series on the new streaming service Disney+. -

Women, Sf Spectacle and the Mise-En-Scene of Adventure in the Star Wars Franchise
This is a repository copy of Women, sf spectacle and the mise-en-scene of adventure in the Star Wars franchise. White Rose Research Online URL for this paper: http://eprints.whiterose.ac.uk/142547/ Version: Accepted Version Article: Tasker, Y orcid.org/0000-0001-8130-2251 (2019) Women, sf spectacle and the mise-en- scene of adventure in the Star Wars franchise. Science Fiction Film and Television, 12 (1). pp. 9-28. ISSN 1754-3770 https://doi.org/10.3828/sfftv.2019.02 Reuse Items deposited in White Rose Research Online are protected by copyright, with all rights reserved unless indicated otherwise. They may be downloaded and/or printed for private study, or other acts as permitted by national copyright laws. The publisher or other rights holders may allow further reproduction and re-use of the full text version. This is indicated by the licence information on the White Rose Research Online record for the item. Takedown If you consider content in White Rose Research Online to be in breach of UK law, please notify us by emailing [email protected] including the URL of the record and the reason for the withdrawal request. [email protected] https://eprints.whiterose.ac.uk/ Women, science fiction spectacle and the mise-en-scène of space adventure in the Star Wars franchise American science fiction cinema has long provided a fantasy space in which some variation in gender conventions is not only possible but even expected. Departure from normative gender scripts signals visually and thematically that we have been transported to another space or time, suggesting that female agency and female heroism in particular is a by-product of elsewhere, or more precisely what we can term elsewhen. -

Movies in the Park
Movies in the Park Movies shown at the Park in the Square, except July. RC Juggles begins at 7:00 PM. Friday, June 23, 8:30 PM Fantastic Beasts and Where to Find Them Thursday, July 13, 8:00 PM Rogue One, A Star Wars Story Friday, August 11, 8:00 PM Emricson Park, under the Big Tent Grease – a Sing-a-Long * Costume Contest* Questions? Contact 815-338-4301 City of Office of the City Manager phone 815.338.4301 Roscoe C. Stelford III, City Manager fax 815.334.2269 121 W. Calhoun Street [email protected] Woodstock, Illinois 60098 www.woodstockil.gov PRESS RELEASE For Immediate Release Contact: Jane Howie 815-338-4301 [email protected] COME OUT TO MOVIES IN THE PARK! This tradition is moving venues so bring your lawn chairs or blankets and come out to the Park in the Square to enjoy movies under the stars as the City of Woodstock’s 12th season of Movies in the Park gets underway. Movies in the Park remains free of charge and will begin as close to 8:00 as darkness will allow. Of course, we will again be joined by RC Juggles who will provide pre-movie fun for kids of all ages. This summer’s movies premiere on Friday, June 23rd in Park in the Square with the showing of Fantastic Beasts and Where to Find Them. This movie is a prequel to the Harry Potter series about the magical creatures in the Harry Potter universe. Fantastic Beasts… purports to be a reproduction of a textbook owned by Harry Potter and written by Newt Scamander in New York’s secret community of witches and wizards 70 years before Harry Potter reads his book in school. -

Star Wars H and V (Autosaved)
YouGov Results - Star Wars Characters Fieldwork: 6th - 9th December 2019 Sample size: 2,016 GB adults Gender Age Total Male Female 18-24 25-34 35-44 45-54 55+ THX_1. Moving on...For the following question, if you haven't seen any Star Wars films, please select the 'Not applicable' option.Would you, or would you not, describe yourself as a Star Wars film fan? Unweighted base 2016 937 1079 202 310 336 337 831 Base: All GB adults 2016 978 1038 224 311 341 341 800 Yes, I would describe myself as a Star Wars film fan 33% 44% 23% 39% 36% 47% 41% 20% No, I would not describe myself as a Star Wars film fan 37% 34% 39% 32% 35% 34% 40% 38% Don't know 3% 2% 3% 3% 3% 2% 3% 3% Not applicable - I have never seen any Star Wars film 28% 20% 35% 26% 26% 17% 16% 39% © 2019 YouGov plc. All Rights Reserved 3 YouGov.co.uk YouGov Results - Star Wars Characters Fieldwork: 6th - 9th December 2019 Sample size: 2,016 GB adults Gender Age Total Male Female 18-24 25-34 35-44 45-54 55+ THX_1. Moving on...For the following question, if you haven't seen any Star Wars films, please select the 'Not applicable' option.Would you, or would you not, describe yourself as a Star Wars film fan? Unweighted base 2016 937 1079 202 310 336 337 831 THX_2. Thinking about ALL the Star Wars films you have seen… Which ONE, if any, of the following do you think is the BEST villain from the Star Wars films? (Please select the option that best applies. -

Reconstructing the Death Star: Myth and Memory in the Star Wars Franchise
Abilene Christian University Digital Commons @ ACU Electronic Theses and Dissertations Electronic Theses and Dissertations Spring 5-2018 Reconstructing the Death Star: Myth and Memory in the Star Wars Franchise Taylor Hamilton Arthur Katz [email protected] Follow this and additional works at: https://digitalcommons.acu.edu/etd Recommended Citation Katz, Taylor Hamilton Arthur, "Reconstructing the Death Star: Myth and Memory in the Star Wars Franchise" (2018). Digital Commons @ ACU, Electronic Theses and Dissertations. Paper 91. This Thesis is brought to you for free and open access by the Electronic Theses and Dissertations at Digital Commons @ ACU. It has been accepted for inclusion in Electronic Theses and Dissertations by an authorized administrator of Digital Commons @ ACU. ABSTRACT Mythic narratives exert a powerful influence over societies, and few mythic narratives carry as much weight in modern culture as the Star Wars franchise. Disney’s 2012 purchase of Lucasfilm opened the door for new films in the franchise. 2016’s Rogue One: A Star Wars Story, the second of these films, takes place in the fictional hours and minutes leading up to the events portrayed in 1977’s Star Wars: Episode IV – A New Hope. Changes to the fundamental myths underpinning the Star Wars narrative and the unique connection between these film have created important implications for the public memory of the original film. I examine these changes using Campbell’s hero’s journey and Lawrence and Jewett’s American monomyth. In this thesis I argue that Rogue One: A Star Wars Story was likely conceived as a means of updating the public memory of the original 1977 film. -

Star Wars Pop! List Popvinyls.Com
Star Wars Pop! LIst PopVinyls.com Updated January 2, 2017 STAR WARS SERIES 32: DROIDS Boba Fett (CELEBRATION 01: Darth Vader Europe 13) 01 Chrome Darth Vader (HT) 33: GITD Holographic Darth Vader (TOY 02: Yoda Matrix Dallas CC 14) 02 GITD Yoda (Walgreens) 33: GITD Holographic Darth Vader 03: Han Solo (PARIS Expo Exclusive) 03: Vault Edition Han Solo 34: Hoth Luke Skywaker 04: Princess Leia 35: Bossk 05: Stormtrooper 36: The Emperor 05 RED Stormtrooper (Target) 37: Hammerhead 06:Chewbacca 38: Biker Scout 06: Flocked Chewbacca (SDCC 11) 39 Wampa 6” 06: Hoth Chewbacca 39: Flocked Wampa (Hot Topic) 07: Greedo 40: Holographic Emperor (TOYWARS) 07: Vault Greedo 41: R2-Q5 (SW Celebration) 08: Boba Fett 42: Shock Trooper (SW Celebration) 08 Prototype Boba Fett (Walgreens) 43: Unmasked Vader 09: Darth Maul 44: R2 R9 (SW Celebration) 10: Obi Wan Kenobi 45: R2-B1 10: Vault Obi Wan Kenobi 46: E-3P0 (SW Celebration) 11: Jedi Luke Skywalker 47: Hoth Han Solo 11: Vault Jedi Luke Skywalker 48: Figrin D’an 12: Gammorrean Guard 49: Tattoine Luke Skywalker 12: Vault Gammorean Guard 50: Boushh Princess Leia 13: C3P0 51: TIE Fighter Pilot 13 Gold Chrome C3P0 (SDCC 15) 51 Metallic TIE Fighter (NYCC 15) 14: Shadow Trooper (SDCC 2011) 52: Nalan Cheel 15: Stormtrooper Han (ECCC 11) 53: Bib Fortuna 16: Stormtrooper Luke (ECCC 11) 54 Unmasked Princess Leia as Boushh 17: X-Wing Luke Skywalker (SDCC 15) 18: Slave Leia 55 K-3P0 18: Vault Slave Leia 56 Snowtrooper (Walgreens) 19: Tusken Raider 57 Imperial Gurrd (Walgreens) 19: Vault Tusken Raider 58 Rey 20: Jawa 59 -

Catalyst: a Rogue One Novel Free
FREE CATALYST: A ROGUE ONE NOVEL PDF James Luceno | 330 pages | 18 Nov 2016 | Del Rey Books | 9780345511492 | English | United States Star Wars Catalyst: A Rogue One Novel synopsis! | Making Star Wars Nov 27 In over 30 years of filmmaking, Lucas Film has never released a stand-alone movie, Ewoks adventure and holiday film notwithstanding. We know a group of stormtroopers, led by Orson Krennic, orphaned Jyn Erso when they absconded with her father, Catalyst: A Rogue One Novel. Catalyst is the story that sets up the events in Rogue One. It takes place a few years after the start of the Galactic Civil war and ends roughly five years after the rise of the Empire. In the beginning, we are introduced to Galen, his wife Lyra, and his Catalyst: A Rogue One Novel with synthetic kyber crystals. Galen has been trying to harness the power of the crystals in an attempt to provide inexpensive energy to developing worlds. But through a series of events, Galen and his wife, who is expecting their first child, Catalyst: A Rogue One Novel imprisoned on Catalyst: A Rogue One Novel Separatist planet. Orson rescued the Ersos in an attempt to persuade Galen to use his research in an attempt to help the Republic and eventually the Empire. Since Galen is a pacifist, he is unwilling to let his research be weaponized by any government, be it Separatist, Republic, or Empire. To a greater degree, it shows how the Empire is willing to use and desecrate all that is good in the universe for their own means. -

Star Wars Pop! List Popvinyls.Com
Star Wars Pop! LIst PopVinyls.com Updated December 2016 STAR WARS SERIES 32: DROIDS Boba Fett (CELEBRATION 01: Darth Vader Europe 13) 01 Chrome Darth Vader (HT) 33: GITD Holographic Darth Vader (TOY 02: Yoda Matrix Dallas CC 14) 02 GITD Yoda (Walgreens) 33: GITD Holographic Darth Vader 03: Han Solo (PARIS Expo Exclusive) 03: Vault Edition Han Solo 34: Hoth Luke Skywaker 04: Princess Leia 35: Bossk 05: Stormtrooper 36: The Emperor 06:Chewbacca 37: Hammerhead 06: Flocked Chewbacca (SDCC 11) 38: Biker Scout 06: Hoth Chewbacca 39 Wampa 6” 07: Greedo 39: Flocked Wampa (Hot Topic) 07: Vault Greedo 40: Holographic Emperor (TOYWARS) 08: Boba Fett 41: R2-Q5 (SW Celebration) 08 Prototype Boba Fett (Walgreens) 42: Shock Trooper (SW Celebration) 09: Darth Maul 43: Unmasked Vader 10: Obi Wan Kenobi 44: R2 R9 (SW Celebration) 10: Vault Obi Wan Kenobi 45: R2-B1 11: Jedi Luke Skywalker 46: E-3P0 (SW Celebration) 11: Vault Jedi Luke Skywalker 47: Hoth Han Solo 12: Gammorrean Guard 48: Figrin D’an 12: Vault Gammorean Guard 49: Tattoine Luke Skywalker 13: C3P0 50: Boushh Princess Leia 13 Gold Chrome C3P0 (SDCC 15) 51: TIE Fighter Pilot 14: Shadow Trooper (SDCC 2011) 51 Metallic TIE Fighter (NYCC 15) 15: Stormtrooper Han (ECCC 11) 52: Nalan CHeel 16: Stormtrooper Luke (ECCC 11) 53: Bib Fortuna 17: X-Wing Luke Skywalker 54 Unmasked Princess Leia as Boushh 18: Slave Leia (SDCC 15) 18: Vault Slave Leia 55 K-3P0 19: Tusken Raider 56 Snowtrooper (Walgreens) 19: Vault Tusken Raider 57 Imperial Gurrd (Walgreens) 20: Jawa 58 Rey 20: Vault Jawa 59 Finn 21: Clone -

Does the Rebel Alliance's Suspicious Procurement of the Death Star
young SOUTH CAROLINA lawyer younglawyer ySOUTHou CAROLINAnglawyer APRIL 2019 VOL. 11, ISSUE 3 A REPORT TO MEMBERS OF Does the Rebel Alliance’s Suspicious THE SOUTH CAROLINA BAR Procurement of the Death Star Plans YOUNG LAWYERS DIVISION YRenderou Itn Liableg Under La Southw Carolina’syer Trade Secrets Act? By Jeremy R. Summerlin As a young lawyer, you’ve probably always asked yourself, “Why doesn’t the Galac- tic Employer just sue the Rebel Alliance, LLC for misappropriation of trade secrets (i.e., the plans to the Death Star) instead of trying to blow the Alliance to bits with the Death Star?” That’s a compelling and entirely necessary and relevant question, and I’ll do my best to answer it. [Full dis- closure: I represented the estates of several Alderaanian individuals killed during the YOEmpire’s Uinitial operationalN Gtest of the firstL AWYER Death Star.] The entirely reasonable question of jurisdiction probably jumps to your mind immediately, just like it did to mine: Where does the Galactic Employer bring its law- suit? For purposes of this wholly education- al article, I will assume that Emperor Palpa- tine’s attorney decides to bring the lawsuit in South Carolina. As you may already know because you high ground, morally speaking, and you typically discuss it on all your first dates, should never challenge someone who has the key personnel of the Rebel Alliance the high ground. were former employees and agents of the As covered by the recent documentary, Galactic Employer, but after some internal Rogue One: A Star Wars Story, the Galactic disputes (and, well, the Clone Wars), these Employer spent significant time, effort, employees left the employ of their Galactic and resources to design and construct the Employer and started their own competing Death Star. -
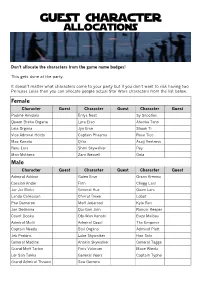
Guest Character Allocations
Guest Character allocations Don’t allocate the characters from the game name badges! This gets done at the party. It doesn’t matter what characters come to your party but if you don’t want to risk having two Princess Leias then you can allocate people actual Star Wars characters from the list below. Female Character Guest Character Guest Character Guest Padmé Amidala Enfys Nest Sy Snootles Queen Breha Organa Lyra Erso Ahsoka Tano Leia Organa Jyn Erso Shaak Ti Vice Admiral Holdo Captain Phasma Rose Tico Maz Kanata Qi'ra Asajj Ventress Beru Lars Shmi Skywalker Rey Mon Mothma Zam Wessell Oola Male Character Guest Character Guest Character Guest Admiral Ackbar Galen Erso Orson Krennic Cassian Andor Finn Cliegg Lars Jar Jar Binks General Hux Owen Lars Lando Calrissian Chirrut Îmwe Lobot Poe Dameron Moff Jerjerrod Kylo Ren Jan Dodonna Qui-Gon Jinn Rancor Keeper Count Dooku Obi-Wan Kenobi Baze Malbus Admiral Motti Admiral Ozzel The Emperor Captain Needa Bail Organa Admiral Piett Jek Porkins Luke Skywalker Han Solo General Madine Anakin Skywalker General Tagge Grand Moff Tarkin Finis Valorum Mace Windu Lor San Tekka General Veers Captain Typho Grand Admiral Thrawn Saw Gerrera Generic Character Guest Character Guest Character Guest Jedi AT-ST Pilot Monster Padawan Imperial Officer Rebel Clone Trooper Pilot Villager Stormtrooper Generic Alien Sand Person Snow Trooper Generic Droid Bounty Hunter Tie Fighter Pilot Wookie Politician AT-AT Pilot Ewok Royalty Biker Scout Ugnaught Cantina Band Jawa Dianoga Anything Star Wars e.g. the Death Star Not Specifically Male or Female Character Guest Character Guest Character Guest Darth Maul Droopy McCool Yak Face 2-1B Chewbacca Greedo 4-LOM Chief Chirpa Max Rebo Ponda Baba Salacious Crumb Nute Gunray BB-8 Dengar IG-88 Bossk Imperial Guard Jabba the Hutt C-3PO Boba Fett K-2SO General Grievous Jango Fett Ki-Adi-Mundi Wicket W. -

Star Wars Checklist Updated 6/12/19
Star Wars Checklist Updated 6/12/19 STAR WARS SERIES 32: DROIDS Boba Fett (CELEBRATION 01: Darth Vader Europe 13) 01 Chrome Darth Vader (HT) 33: GITD Holographic Darth Vader (TOY 02: Yoda Matrix Dallas CC 14) 02 GITD Yoda (Walgreens) 33: GITD Holographic Darth Vader 03: Han Solo (PARIS Expo Exclusive) 03: Vault Edition Han Solo 34: Hoth Luke Skywaker 04: Princess Leia 35: Bossk 05: Stormtrooper 36: The Emperor 05 RED Stormtrooper (Target) 37: Hammerhead 06:Chewbacca 38: Biker Scout 06: Flocked Chewbacca (SDCC 11) 39 Wampa 6” 06: Hoth Chewbacca 39: Flocked Wampa (Hot Topic) 07: Greedo 40: Holographic Emperor (TOYWARS) 07: Vault Greedo 41: R2-Q5 (SW Celebration) 08: Boba Fett 42: Shock Trooper (SW Celebration) 08 Prototype Boba Fett (Walgreens) 43: Unmasked Vader 09: Darth Maul 44: R2 R9 (SW Celebration) 10: Obi Wan Kenobi 45: R2-B1 10: Vault Obi Wan Kenobi 46: E-3P0 (SW Celebration) 11: Jedi Luke Skywalker 47: Hoth Han Solo 11: Vault Jedi Luke Skywalker 48: Figrin D’an 12: Gammorrean Guard 49: Tattoine Luke Skywalker 12: Vault Gammorean Guard 50: Boushh Princess Leia 13: C3P0 51: TIE Fighter Pilot 13 Gold Chrome C3P0 (SDCC 15) 51 Metallic TIE Fighter (NYCC 15) 14: Shadow Trooper (SDCC 2011) 52: Nalan Cheel 15: Stormtrooper Han (ECCC 11) 53: Bib Fortuna 16: Stormtrooper Luke (ECCC 11) 54 Unmasked Princess Leia as Boushh 17: X-Wing Luke Skywalker (SDCC 15) 18: Slave Leia 55 K-3P0 18: Vault Slave Leia 56 Snowtrooper (Walgreens) 19: Tusken Raider 57 Imperial Gurrd (Walgreens) 19: Vault Tusken Raider 58 Rey 20: Jawa 59 Finn 20: Vault Jawa 60 -

Saint Ignatius College Prep Saint Ignatius Model United Nations
! Saint Ignatius College Prep SIMUN XVI Saint Ignatius Model United Nations ! Chicago, IL November 4, 2017 ! JCC STAR WARS: IMPERIALS SIMUN XVI - November 4, 2017 Letter From the Chair Dear Delegates, My name is Christopher Mitchell and I will be your chair for this awesome committee. I am a member of the SIMUN exec-board and I have previously served as vice chair for the Irish War for Independence Committee and Chair of the House of Cards Cabinet. Myself and the chair of JCC: Rebels, Maggie Doyle, have been working hard these past few months to create the best model UN committee you will ever participate in. This will be my final year in SIMUN since I am a senior so I wanted to create the most memorable committee possible. I've loved Star Wars since I was three years old. After seeing rogue one I knew I had to chair a Star Wars committee. I hope that you will have close to as much fun as I will in this committee. Please contact me with any questions. You can email me at [email protected]. JCC STAR WARS - REBELS !1 About This Committee Imperial Security Bureau Warning: Disclosure of materials included in this briefing to unauthorized individuals is prohibited and will be considered treason under the imperial state security act. (Just don't tell anyone in jcc rebels) This is a military joint crisis committee. The sole goal is to win a war against the rebel alliance. Every action taken by this committee will affect the rebel committee that works against us.