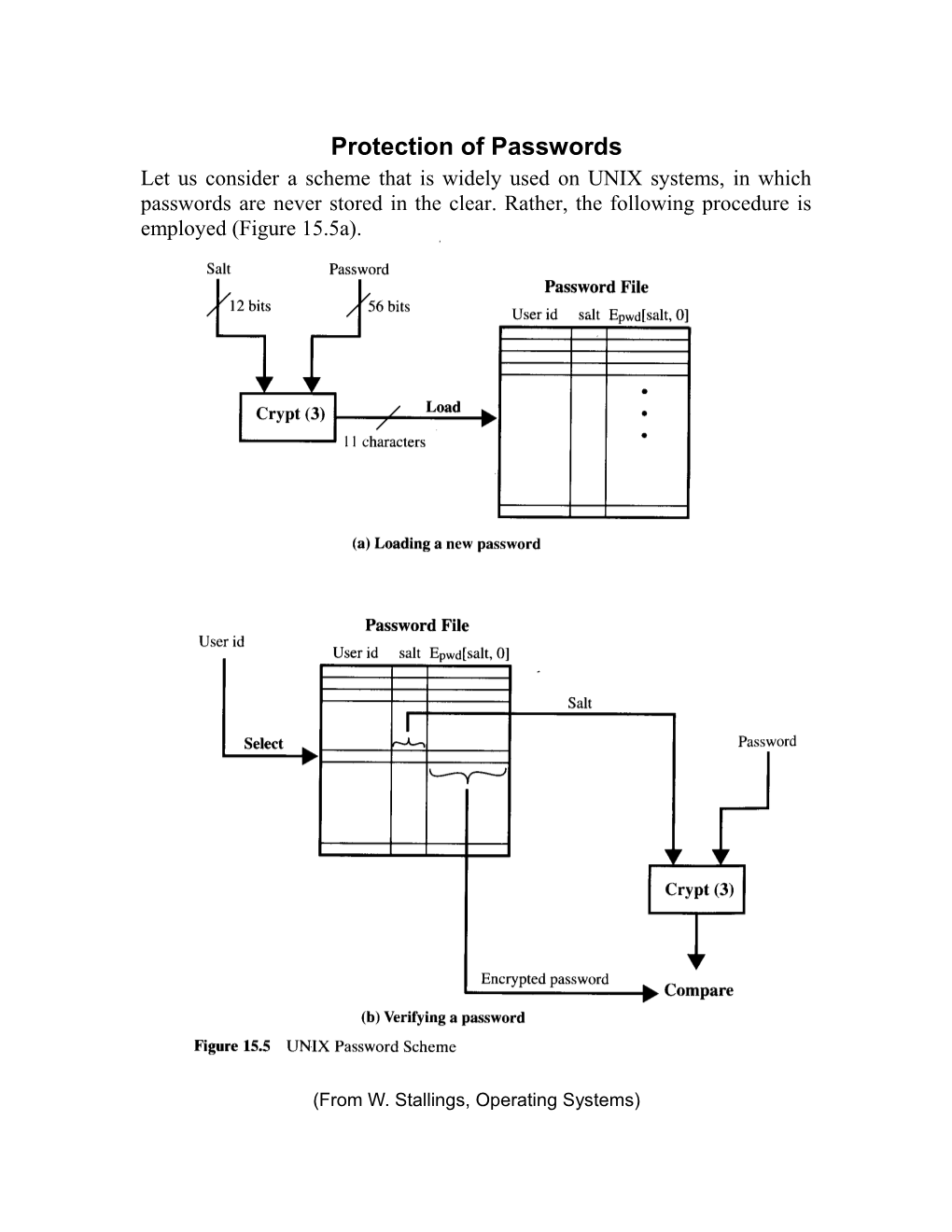
Protection of Passwords Let us consider a scheme that is widely used on UNIX systems, in which passwords are never stored in the clear. Rather, the following procedure is employed (Figure 15.5a).
(From W. Stallings, Operating Systems) Protection of Passwords (Cont 1)
Each user selects a password of up to eight printable characters in length. This is converted into a 56-bit value (using 7-bit ASCII) that serves as the key input to an encryption routine. The encryption routine, known as crypt(3), is based on DES. crypt(1) is a Unix utility command while crypt(3) is an unrelated standard library function. The (1) and (3) suffixes to these reflect a documentation convention among Unix writers, system administrators, programmers, and users which disambiguate some terms based on whether they are commands (documented in chapter (1) of the Unix man pages) or library functions (documented in chapter (3), traditionally). The DES algorithm is modified using a 12-bit “salt” value. DES algorithm is represented by the following schema: Protection of Passwords (Cont 2)
(From W. Stallings, Cryptography and Network Security) Protection of Passwords (Cont 3)
Typically, the value of “salt” is related to the time at which the password is assigned to the user. The modified DES algorithm is exercised with a data input consisting of a 64-bit block of zeros. The output of the algorithm permuted with the help of the salt then serves as input for a second encryption. This process is repeated for a total of 25 encryptions. The resulting 64-bit output is then translated into a 11-character sequence. The ciphertext password is then stored, together with a plaintext copy of the salt, in the password file for the corresponding user ID. The salt serves three purposes: It prevents duplicate passwords from being visible in the password file. Even if two users choose the same password, those passwords will be assigned at different times. Hence, the “extended” passwords of the two users will differ. It effectively increases the length of the password without requiring the user to remember two additional characters. Hence, the number of possible passwords is increased by a factor of 4096, increasing the difficulty of guessing a password. There are two threats to the UNIX password scheme. First, a user can gain access on a machine using a guest account or by some other means and then run a password-guessing program, called a password cracker, on that machine. The attacker should be able to check hundreds and perhaps thousands of possible passwords with little resource consumption. Second, if opponent is able to obtain a copy of the password file, then a cracker program can be run on another machine at leisure. This enables the opponent to run through many thousands of possible passwords in a reasonable period. Protection of Passwords (Cont 4)
Even high rates do not make it feasible for an attacker to use a dumb brute- force technique of trying all possible combinations of characters to discover a password. Instead, password crackers rely on the fact that some people choose easily guessable passwords. Some users use absurdly short passwords: among 7000 user accounts almost 3% were three characters or fewer in length. A simple remedy is for the system to reject any password choice of fewer than eight characters in length. Password length is only part of the problem. Many people choose password as their own name, their street name, a common dictionary word, and so forth. It is reported about a study, in which nearly 14,000 encrypted passwords were analyzed, and nearly one-fourth of the passwords were guessed. The following strategy was used: 1. Try the user’s name, initials, account name, and all other relevant information (130 variants for each user). 2. Try words from various dictionaries (60,000 words were tried). 3. Try various permutations on the words from step 2. This included making the first letter uppercase or a control character, making the entire word uppercase, reversing the word, changing the letter “o” to the digit “zero”, and so on (1 million words were added). 4. Try various capitalization permutations on the words from step 2 that were not considered in step 3 (2 million words were added). Thus, the test involved about 3 million words. And it had a success rate of about 25%, whereas even a single hit may be enough to gain a wide range of privileges on a system. Password Selection Strategies Four basic techniques are in use: User education – is unlikely to succeed because many users will simply ignore the guidelines, other may not be good judges of what is a strong password. Many users believe that reversing a word or capitalizing the last letter makes a password un-guessable Computer-generated passwords – if the passwords are quite random in nature, users will not be able to remember them Reactive password checking – a system periodically runs its own password cracker to find guessable passwords, cancels them and notifies the user. Existing passwords remain vulnerable until the reactive password cracker finds them Proactive password checking – a user is allowed to select a password, however, at the time of selection, the system checks to see if the password is allowable and, if not, rejects it. If the system rejects too many passwords, users will complain. If the system uses some simple algorithms to define what is acceptable, this provides guidance to password crackers to refine their guessing technique. For proactive password checking, the following simple rules could be enforced: All passwords must be at least eight characters long In the first eight characters, the passwords must include at least one each of uppercase, lowercase, numeric digits, and punctuation marks. Another possible strategy is to compile a large dictionary of possible “bad” passwords. When a user selects a password, the system checks that it is not on the disapproved list. But this approach suffers from the large resource consumption: both space and time. Intrusion Detection Inevitably, the best intrusion prevention system will fail. A system’s second line of defense is intrusion detection. Intrusion detection is based on the assumption that the behavior of the intruder differs from that of a legitimate user in ways that can be quantified. Of course, there is no crisp distinction between an attack by intruder and the normal use of resources by an authorized user. Rather, we must expect some overlap. Hence, legitimate user can be recognized as intruders, and vice versa. The following approaches to intrusion detection can be considered: 1. Statistical anomaly detection: Involves the collection of data relating to the behavior of legitimate user over a period of time. Then statistical tests are applied to observed behavior to determine with a high level of confidence whether that behavior is not legitimate user behavior. 1.1. Threshold detection: This approach involves defining thresholds, independent of user, for the frequency of various events 1.2. Profile based: A profile of the activity of each user is developed and used to detect changes in the behavior of individual accounts 2. Rule-based detection: Involves an attempt to define a set of rules that can be used to decide that a given behavior is that of an intruder 2.1. Anomaly detection: Rules are developed to detect deviation from previous usage patterns 2.2. Penetration identification: An expert system approach that searches for suspicious behavior In a nutshell, statistical approaches attempt to define normal, or expected, behavior, whereas rule-based approaches attempt to define proper behavior. Statistical anomaly detection is effective against masqueraders, who are unlikely mimic the behavior patterns of the accounts they appropriate. On the other hand, such techniques may be unable to deal with misfeasors. Combination of the both approaches may be effective against a broad range of attacks. Audit A fundamental tool for intrusion detection is the audit record. Basically, two plans are used: Native audit records: All multi-user operating systems include accounting software that collects information on user activity. The disadvantage is that it may not contain the needed information or contain it in not convenient form Detection-specific audit records: It records only information necessary to intrusion detection system. The disadvantage is extra overhead (two accounting packages run together) Audit record can contain: Subject: Initiator of actions Action: Operation performed Object: Receptors of actions Exception Condition: Denotes which, if any, exception condition is raised on return Resource Usage: A list of resources and quantitative measure of their use (lines printed, processor time, I/O units used, session elapsed time) Time Stamp: Unique time and date stamp identifying when the action took place Malicious Software Malware is software designed to cause damage to or use up of the resources of a target computer: Trap Doors (usually used in debugging process), Logic Bombs (makes its harmful action on condition fulfillment), Trojan Horses (make some not expected normally, e.g. compiler inserts malicious code into being compiled program), Viruses (spread by exchange of programs and disks between users), Worms (spread using network connections by electronic mail, remote execution capability, or remote login capability), Zombie (a program that secretly takes over another Internet-attached computer and then uses that computer to launch attacks that are difficult to trace to the zombie’s creator). During its lifetime, a typical virus goes through the following four stages: 1. Dormant phase: The virus is idle. 2. Propagation phase: The virus places an identical copy of itself into other programs 3. Triggering phase: The virus is activated to perform the function for which it was intended 4. Execution phase: The function is performed The most significant types of viruses are: Parasitic Memory-resident Boot sector Stealth Polymorphic Macro One example of a stealth virus is one that uses compression so that the infected program is exactly the same length as an uninfected program. One of the most widely spread since 1999 macro viruses is Melissa. Information about it can be found in http://www.securiteam.com/exploits/2XUQ1QAQMQ.html. Its structure and behavior is explained in the file /IEEESpectrumVirusDefOnePage.pdf, reference to which is given in my site http://cmpe.emu.edu.tr/chefranov/cmpe552-06/index.htm.