Answer Sheet
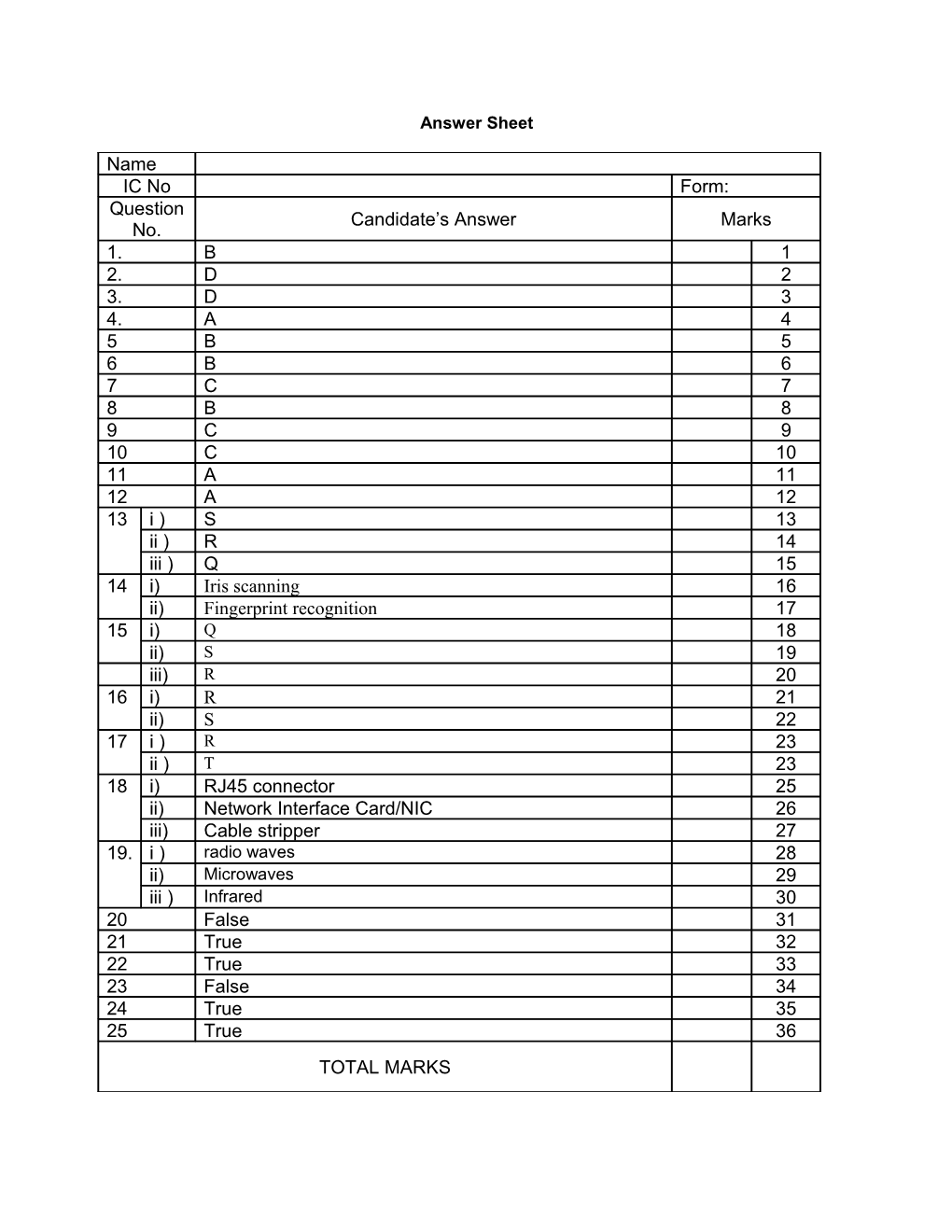
Name IC No Form: Question Candidate’s Answer Marks No. 1. B 1 2. D 2 3. D 3 4. A 4 5 B 5 6 B 6 7 C 7 8 B 8 9 C 9 10 C 10 11 A 11 12 A 12 13 i ) S 13 ii ) R 14 iii ) Q 15 14 i) Iris scanning 16 ii) Fingerprint recognition 17 15 i) Q 18 ii) S 19 iii) R 20 16 i) R 21 ii) S 22 17 i ) R 23 ii ) T 23 18 i) RJ45 connector 25 ii) Network Interface Card/NIC 26 iii) Cable stripper 27 19. i ) radio waves 28 ii) Microwaves 29 iii ) Infrared 30 20 False 31 21 True 32 22 True 33 23 False 34 24 True 35 25 True 36 TOTAL MARKS Scheme Section B 1. a) Copyright infringement is defined as a violation of the rights secured by Copyright Act. Pelanggaran hakcipta bermaksud pencabulan ke atas hak-hak yang dilindungi oleh Akta Hakcipta..
Give TWO examples of copyright infringement Berikan DUA contoh pelanggaran hakcipta
i. Copying movie, software or CD’s illegally
ii. Selling pirate software
(any releven answers)
Mark (1 mark for each correct answer)
b) i. Hand geometry scanning ii. Iris scanning Mark (1 mark for each correct answer)
2. Computer theft is defined as the unauthorised use of another person’s property with the intention to deny the owner the rightful possession of that property or its use. Examples of computer theft include: transfer of payments to the wrong accounts tap into data transmission lines on database at no cost divert goods to the wrong destination
Mark (Define – 1 mark, Example – 1 mark) b. Hacking is a source of threat to security in computer. It is defined as unauthorised access to the computer system by a hacker. Examples of computer hacking include: virus, Trojan horse logic door trapdoor and backdoor worm many others.
Mark (Define – 1 mark, Example – 1 mark) 3. a. X = Network Card , Y = Hub/Switch/Router Mark (1 mark for each correct answer)
b. Function of X is provides connection between the computer and the network’s communications media OR supplies the basic addressing system used to get data from PC to PC across a network. Function of Y is control the flow of data on a network. Mark (1 mark for each correct answer)
4. i) Two differences of user interfaces applied for both software H
Command-line Interface Dimensio Graphical-User n Interface
User type commands or A way to User interact with presses special keys on the enter data menus and visual keyboard images such as buttons and other graphical objects to issue commands
Not user-friendly User- User friendly Difficult to use because friendly Easy to use – user they require exact spelling, can choose the grammar command by clicking a mouse
Mark (1 mark for each correct answer) ii) One type of software I and its function Software I is Application Software o One type of Software I is … (either one – refer table)
- Function of any Software I Application Function Software Type Word - Enables user to create, edit, format and print textual Processing documents
Spreadsheet - Help users to produce information in the form of grid of columns and rows
Presentation - Enables user to create transparencies, slides and handouts for presentation - Allows user to create visual aids for presentation to communicate ideas messages and other information to a group
Graphic - Enables user to edit digital representation or non-text information such as drawings, charts or photographs.
Mark (1 mark for the software name and any one type of it, 1 mark for the function of the software type stated)
5. a) Reason: PC1 and PC2 have the same IP address, 192.168.1.5 and therefore the network has IP conflict. All the computers in a network must have different IP addresses so that they are able to communicate with each other. OR The subnet masks for both PCs have been configured incorrectly. The subnet mask used for both PCs is invalid. It should be 255.255.255.0 Mark (2 mark for correct answer)
b) Computer IP address Subnet Mask (any 192.168.1.x except 192.168.1.1) PC1 192.168.1.2 255.255.255.0 PC2 192.168.1.3 255.255.255.0 Mark (1 mark for each correct answer) Scheme Section C Question 31 (a)
(b) - Interprets and carries out basic instructions that operate a computer - Control unit directs and coordinates operations in computer - Arithmetic logic unit (ALU) performs arithmetic, comparison and logical operations (c)
Component B Component C Any machine that feeds data into a A piece of hardware uses to present computer. information to the user. Examples : keyboard, webcam, mouse Example : monitor, speaker, printer. Allow user to enter raw data into a Capable of delivering or showing computer information to user. Provides communication between the user Serves as an interface between the and the computer computer and the user Capable of converting data into a form Takes machine coded output results from which can be recognized by the computer the processor and convert them into a form that can be used by human beings. (d) - Speaker - Liquid Crystal Display (LCD) Projector
Question 32 (a) i . Ring Topology ii. Star Topology iii. Bus Topology
(b) - A star network generally requires more cable - If the hub fails, the entire network also fails - Bottlenecks can occur because all data must pass through the hub - Expensive to install - Network speed decreases when the number of nodes fails. - Troubleshooting is difficult when one of the nodes fails - A host must be installed to control the network.
(c) Types Topology A (Ring) Topology C (Bus) Structure All computer and other Consist a single central devices are connected in a cable (backbone) and all circle. computers and other devices connect it Connection between nodes Yes No Host failure Network will fail Network can still run Nodes Failure Network will fail Network can still run Ease of troubleshooting Depends on backbones Difficult Ease of adding or removing Difficult Easy nodes Number of nodes when Limited Many extending network
Question 33 (a) Application software is a computer program or a suite of computer programs that performs a particular function for the user. Example: Word star, Dbase, Microsoft Excel, Microsoft Access.
(b) System Software Application Software Enables the computer to function properly Enables users to work efficiently with documentation such as letters, accounting reports and presentations Compulsory – each computer must have a Optional – depends on usage and needs. system software to function Without an application software, the computer is still able to function. Each computer only needs one system Each computer can have more than one software application software Independent – system software can Dependent – application software cannot function without an application software work without system software Provides the environment in which the Provides the environment to enable users to application run accomplish specific tasks.
(c) - The AVG Antivirus in Computer X is an antivirus program, will protects computer X against viruses by identifying and removing any computer viruses found in the computer memory, on storage media or incoming e-mail files.