Chapter 2 Booting
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Boot Mode Considerations: BIOS Vs UEFI
Boot Mode Considerations: BIOS vs. UEFI An overview of differences between UEFI Boot Mode and traditional BIOS Boot Mode Dell Engineering June 2018 Revisions Date Description October 2017 Initial release June 2018 Added DHCP Server PXE configuration details. The information in this publication is provided “as is.” Dell Inc. makes no representations or warranties of any kind with respect to the information in this publication, and specifically disclaims implied warranties of merchantability or fitness for a particular purpose. Use, copying, and distribution of any software described in this publication requires an applicable software license. Copyright © 2017 Dell Inc. or its subsidiaries. All Rights Reserved. Dell, EMC, and other trademarks are trademarks of Dell Inc. or its subsidiaries. Other trademarks may be the property of their respective owners. Published in the USA [1/15/2020] [Deployment and Configuration Guide] [Document ID] Dell believes the information in this document is accurate as of its publication date. The information is subject to change without notice. 2 : BIOS vs. UEFI | Doc ID 20444677 | June 2018 Table of contents Revisions............................................................................................................................................................................. 2 Executive Summary ............................................................................................................................................................ 4 1 Introduction .................................................................................................................................................................. -

Active@ UNDELETE Documentation
Active @ UNDELETE Users Guide | Contents | 2 Contents Legal Statement.........................................................................................................5 Active@ UNDELETE Overview............................................................................. 6 Getting Started with Active@ UNDELETE.......................................................... 7 Active@ UNDELETE Views And Windows...................................................................................................... 7 Recovery Explorer View.......................................................................................................................... 8 Logical Drive Scan Result View..............................................................................................................9 Physical Device Scan View......................................................................................................................9 Search Results View...............................................................................................................................11 File Organizer view................................................................................................................................ 12 Application Log...................................................................................................................................... 13 Welcome View........................................................................................................................................14 Using -

Chapter 3. Booting Operating Systems
Chapter 3. Booting Operating Systems Abstract: Chapter 3 provides a complete coverage on operating systems booting. It explains the booting principle and the booting sequence of various kinds of bootable devices. These include booting from floppy disk, hard disk, CDROM and USB drives. Instead of writing a customized booter to boot up only MTX, it shows how to develop booter programs to boot up real operating systems, such as Linux, from a variety of bootable devices. In particular, it shows how to boot up generic Linux bzImage kernels with initial ramdisk support. It is shown that the hard disk and CDROM booters developed in this book are comparable to GRUB and isolinux in performance. In addition, it demonstrates the booter programs by sample systems. 3.1. Booting Booting, which is short for bootstrap, refers to the process of loading an operating system image into computer memory and starting up the operating system. As such, it is the first step to run an operating system. Despite its importance and widespread interests among computer users, the subject of booting is rarely discussed in operating system books. Information on booting are usually scattered and, in most cases, incomplete. A systematic treatment of the booting process has been lacking. The purpose of this chapter is to try to fill this void. In this chapter, we shall discuss the booting principle and show how to write booter programs to boot up real operating systems. As one might expect, the booting process is highly machine dependent. To be more specific, we shall only consider the booting process of Intel x86 based PCs. -

Lecture Notes in Assembly Language
Lecture Notes in Assembly Language Short introduction to low-level programming Piotr Fulmański Łódź, 12 czerwca 2015 Spis treści Spis treści iii 1 Before we begin1 1.1 Simple assembler.................................... 1 1.1.1 Excercise 1 ................................... 2 1.1.2 Excercise 2 ................................... 3 1.1.3 Excercise 3 ................................... 3 1.1.4 Excercise 4 ................................... 5 1.1.5 Excercise 5 ................................... 6 1.2 Improvements, part I: addressing........................... 8 1.2.1 Excercise 6 ................................... 11 1.3 Improvements, part II: indirect addressing...................... 11 1.4 Improvements, part III: labels............................. 18 1.4.1 Excercise 7: find substring in a string .................... 19 1.4.2 Excercise 8: improved polynomial....................... 21 1.5 Improvements, part IV: flag register ......................... 23 1.6 Improvements, part V: the stack ........................... 24 1.6.1 Excercise 12................................... 26 1.7 Improvements, part VI – function stack frame.................... 29 1.8 Finall excercises..................................... 34 1.8.1 Excercise 13................................... 34 1.8.2 Excercise 14................................... 34 1.8.3 Excercise 15................................... 34 1.8.4 Excercise 16................................... 34 iii iv SPIS TREŚCI 1.8.5 Excercise 17................................... 34 2 First program 37 2.1 Compiling, -
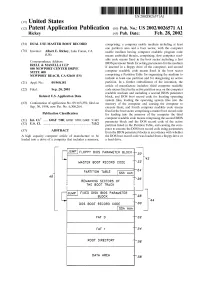
[JUMP FLOPPY Bios PARAMETER BLOCK—\20
US 20020026571A1 (19) United States (12) Patent Application Publication (10) Pub. No.: US 2002/0026571 A1 Rickey (43) Pub. Date: Feb. 28, 2002 (54) DUAL USE MASTER BOOT RECORD comprising: a computer usable medium including at least one partition area and a boot sector, With the computer (76) Inventor: Albert E. Rickey, Lake Forest, CA usable medium having computer readable program code (Us) means embodied therein, comprising: ?rst computer read able code means ?xed in the boot sector including a ?rst Correspondence Address: BIOS parameter block for setting parameters for the medium IRELL & MANELLA LLP if inserted in a ?oppy drive of the computer; and second 840 NEWPORT CENTER DRIVE SUITE 400 computer readable code means ?xed in the boot sector NEWPORT BEACH, CA 92660 (US) comprising a Partition Table for organizing the medium to include at least one partition and for designating an active (21) Appl. No.: 09/960,181 partition. In a further embodiment of the invention, the article of manufacture includes: third computer readable (22) Filed: Sep. 20, 2001 code means ?xed in the active partition area on the computer readable medium and including a second BIOS parameter Related US. Application Data block, and DOS boot record code for locating operating system ?les, loading the operating system ?les into the (63) Continuation of application No. 09/163,359, ?led on memory of the computer and causing the computer to Sep. 30, 1998, noW Pat. No. 6,308,264. execute them; and fourth computer readable code means ?xed in the boot sector comprising a master boot record code Publication Classi?cation for loading into the memory of the computer the third computer readable code means comprising the second BIOS (51) Int. -

DOS Technical Reference
-------- - ---- Personal Computer - ---- - --- ------ - . - Programming Family DOS Technical Reference 6138536 Preliminary First Edition (February 1985) The following paragraph does not apply to the United Kingdom or any country where such provisions are inconsistent ~ith local law: INTERNATIONAL BUSINESS MACHINES CORPORATION PROVIDES TIllS PUBLICATION "AS IS" wrrnom WARRANTY OF ANY KIND, EmlER EXPRESS OR IMPLIED, INCLUDING, BUT NOT LIMITED TO, 1HE IMPLIED WARRANTIES OF MERCHANTABILITY OR FITNESS FOR A PARTICULAR PURPOSE. Some states do not allow disclaimer of express or implied warranties in certain transactions, therefore, this statement may not apply to you. lbis publication could include technical inaccuracies or typographical errors. Changes are periodically made to the information herein; these changes will be incorporated in new editions of the publication. IBM may make improvements and!or changes in the product(s) and/or the program(s) described in this pUblication at any time. It is possible that this publication may contain reference to, or information about, IBM products (machines and programs), programming, or services that are not announced in your country. Such references or information must not be construed to mean that IBM intends to announce such IBM products, programming, or services in your country. Products are not stocked at the address below. Requests for copies of this publication and for technical information about IBM Personal Computer products should be made to your authorized IBM Personal Computer dealer, IBM Product Center, or your IBM Marketing Representative. The following paragraph applies only to the United States and Puerto Rico: A Reader's Comment Form is provided at the back of this publication. If the form has been removed. -

Unit V Algorithm for Booting the UNIX System
Unit V Algorithm for booting the UNIX system : As we’ve noted, the boot process begins when the instructions stored in the computer’s permanent, nonvolatile memory (referred to colloquially as the BIOS, ROM,NVRAM, and so on) are executed. This storage location for the initial boot instructions is generically referred to as firmware (in contrast to “software,” but reflecting the fact that the instructions constitute a program[2]). These instructions are executed automatically when the power is turned on or the system is reset, although the exact sequence of events may vary according to the values of stored parameters.[3] The firmware instructions may also begin executing in response to a command entered on the system console (as we’ll see in a bit). However they are initiated, these instructions are used to locate and start up the system’s boot program , which in turn starts the Unix operating system. The boot program is stored in a standard location on a bootable device. For a normal boot from disk, for example, the boot program might be located in block 0 of the root disk or, less commonly, in a special partition on the root disk. In the same way, the boot program may be the second file on a bootable tape or in a designated location on a remote file server in the case of a network boot of a diskless workstation. There is usually more than one bootable device on a system. The firmware program may include logic for selecting the device to boot from, often in the form of a list of potential devices to examine. -

BIOS Boot Specification
Compaq Computer Corporation Phoenix Technologies Ltd. Intel Corporation BIOS Boot Specification Version 1.01 January 11, 1996 This specification has been made available to the public. You are hereby granted the right to use, implement, reproduce, and distribute this specification with the foregoing rights at no charge. This specification is, and shall remain, the property of Compaq Computer Corporation (“Compaq”), Phoenix Technologies Ltd (“Phoenix”), and Intel Corporation (“Intel”). NEITHER COMPAQ, PHOENIX NOR INTEL MAKE ANY REPRESENTATION OR WARRANTY REGARDING THIS SPECIFICATION OR ANY PRODUCT OR ITEM DEVELOPED BASED ON THIS SPECIFICATION. USE OF THIS SPECIFICATION FOR ANY PURPOSE IS AT THE RISK OF THE PERSON OR ENTITY USING IT. COMPAQ, PHOENIX AND INTEL DISCLAIM ALL EXPRESS AND IMPLIED WARRANTIES, INCLUDING BUT NOT LIMITED TO THE IMPLIED WARRANTIES OF MERCHANTABILITY, FITNESS FOR A PARTICULAR PURPOSE AND FREEDOM FROM INFRINGEMENT. WITHOUT LIMITING THE GENERALITY OF THE FOREGOING, NEITHER COMPAQ, PHOENIX NOR INTEL MAKE ANY WARRANTY OF ANY KIND THAT ANY ITEM DEVELOPED BASED ON THIS SPECIFICATION, OR ANY PORTION OF IT, WILL NOT INFRINGE ANY COPYRIGHT, PATENT, TRADE SECRET OR OTHER INTELLECTUAL PROPERTY RIGHT OF ANY PERSON OR ENTITY IN ANY COUNTRY. Table of Contents 1.0 INTRODUCTION 5 1.1 REVISION HISTORY 5 1.2 RELATED DOCUMENTS 5 1.3 PURPOSE 5 1.4 TERMS 6 2.0 OVERVIEW 9 2.1 DESCRIPTION 9 3.0 IPL DEVICES 10 3.1 REQUIREMENTS FOR IPL DEVICES 10 3.1.1 IPL TABLE 10 3.1.2 PRODUCT NAME STRING 11 3.2 BAIDS 11 3.3 DEVICES WITH PNP EXPANSION HEADERS -

Bootloader and Startup Feature Overview and Configuratoin Guide
TechnicalTTechnicalechnical GuideGuidGuidee Bootloader and Startup Feature Overview and Configuration Guide The AlliedWare Plus™ Bootloader Every switch has a startup process. The end result of the startup is that the unit is running a specific version of the operating system software, with the features configured according to a specific startup configuration file. The startup process goes through two main phases: First, the switch boots up off a dedicated bootloader software image, which initializes core functionality of the unit. Then, the bootloader launches the main operating software image, and passes control over to this operating system. The bootloader is the executable code responsible for setting up the system and loading the operating system software. The bootloader is the software that runs the unit when it first powers up, performing basic initialization and executing the product software release. As part of the startup process of the switch, the bootloader allows you various options before running the product operating system software. C613-22004-00 x REV A alliedtelesis.com Products and software version that apply to this guide This guide applies to all AlliedWare Plus products, running version 5.4.4 or later. However, not all features in this guide are supported on all products. To see whether a product supports a particular feature or command, see the following documents: The product’s Datasheet The AlliedWare Plus Datasheet The product’s Command Reference These documents are available from the above links on our website at alliedtelesis.com. Feature support may change in later versions. For the latest information, see the above documents. Content The AlliedWare Plus™ Bootloader .................................................................................... -

Lecture 5: Feb 4Th, 2020 5.1 OS Boot Process
CMPSCI 577 Operating Systems Design and Implementation Spring 2020 Lecture 5: Feb 4th, 2020 Lecturer: Prashant Shenoy Scribe: Serena Chan 5.1 OS Boot Process While seemingly mundane and not directly relevant to the modifications we will be making in this course, understanding the OS boot process is important for modifying the kernel. There are six steps that take the machine to a running state from when it is first turned on. 5.1.1 Step 1: BIOS (Basic Input/Output System) The BIOS is a small piece of code that lives in the firmware and is the first software that runs upon boot. When the computer is turned on, the BIOS runs the Power-on Self Test, where the RAM is initialized and hardware such as disks and peripherals are identified and checked. Once the disk is found, the BIOSwill start the boot process from the disk (‘bootstrapping’). The BIOS is often stored on EEPROM/ROM (read-only memory); because of its hardware-specific nature, it is not designed to be easily user modifiable. In addition, since the BIOS is the lowest level of softwarein the PC, it also acts as an interface for the OS to perform I/O and communicate with hardware. 5.1.2 Step 2: MBR (Master Boot Record) The MDR is the first 512 bytes of memory and consists of three components. In particular, thefirst440 bytes contain the bootstrap code that is used to continue the boot process, or the 1st stage boot loader; this is executed by the BIOS. The functionality of the code is to simply search through the partition table and find the root partition, where is where the OS resides. -

Wikipedia: Design of the FAT File System
Design of the FAT file system A FAT file system is a specific type of computer file system architecture and FAT a family of industry-standard file systems utilizing it. Developer(s) Microsoft, SCP, IBM, [3] The FAT file system is a legacy file system which is simple and robust. It Compaq, Digital offers good performance even in very light-weight implementations, but Research, Novell, cannot deliver the same performance, reliability and scalability as some Caldera modern file systems. It is, however, supported for compatibility reasons by Full name File Allocation Table: nearly all currently developed operating systems for personal computers and FAT12 (12- many home computers, mobile devices and embedded systems, and thus is a bit version), well suited format for data exchange between computers and devices of almost FAT16 (16- any type and age from 1981 through the present. bit versions), Originally designed in 1977 for use on floppy disks, FAT was soon adapted and FAT32 (32-bit version used almost universally on hard disks throughout the DOS and Windows 9x with 28 bits used), eras for two decades. Today, FAT file systems are still commonly found on exFAT (64- floppy disks, USB sticks, flash and other solid-state memory cards and bit versions) modules, and many portable and embedded devices. DCF implements FAT as Introduced 1977 (Standalone the standard file system for digital cameras since 1998.[4] FAT is also utilized Disk BASIC-80) for the EFI system partition (partition type 0xEF) in the boot stage of EFI- FAT12: August 1980 compliant computers. (SCP QDOS) FAT16: August 1984 For floppy disks, FAT has been standardized as ECMA-107[5] and (IBM PC DOS 3.0) ISO/IEC 9293:1994[6] (superseding ISO 9293:1987[7]). -

Virus Infection Techniques: Boot Record Viruses
Virus Infection Techniques: Boot Record Viruses Bill Harrison CS4440/7440 Malware Analysis and Defense Reading } Start reading Chapter 4 of Szor 2 Virus Infection Techniques } We will survey common locations of virus infections: MBR (Master Boot Record) Boot sector Executable files (*.EXE, *.COM, *.BAT, etc.) } Most of the examples of these viruses, especially the first two types, are from the DOS and floppy disk era 3 Why Study Older Viruses? } Vulnerabilities remain very similar over time, along with the means to exploit them and defend against them } Modern Internet worms differ mainly in the use of the internet for transport, and are otherwise similar to older viruses } Older viruses illustrate the virus vs. antivirus battle over many generations 4 Boot-up Infections and the PC Boot-up Sequence } PC boot-up sequence: 1. BIOS searches for boot device (might be a diskette, hard disk, or CD-ROM) 2. MBR (Master Boot Record) is read into memory from the beginning of the first disk partition; execution proceeds from memory 5 Master Boot Record Structure Boot-up Sequence cont’d. 3. Beginning of MBR has tiny code called the boot- strap loader 4. Data area within MBR has the disk PT (partition table) 5. Boot-strap loader reads PT and finds the active boot partition 6. Boot-strap loader loads the first sector of the active partition into memory and jumps to it; this is called the boot sector 7 Boot-up Sequence cont’d. } MBR is always at BIOS the very first sector of the hard MBR: Expanded View MBR Boot-strap loader code (446 disk (first 512