Netbsd, I Would Like Art Director: to Invite You to Read the Article Written by Diego Montalvo
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Reconfigurable Embedded Control Systems: Problems and Solutions
RECONFIGURABLE EMBEDDED CONTROL SYSTEMS: PROBLEMS AND SOLUTIONS By Dr.rer.nat.Habil. Mohamed Khalgui ⃝c Copyright by Dr.rer.nat.Habil. Mohamed Khalgui, 2012 v Martin Luther University, Germany Research Manuscript for Habilitation Diploma in Computer Science 1. Reviewer: Prof.Dr. Hans-Michael Hanisch, Martin Luther University, Germany, 2. Reviewer: Prof.Dr. Georg Frey, Saarland University, Germany, 3. Reviewer: Prof.Dr. Wolf Zimmermann, Martin Luther University, Germany, Day of the defense: Monday January 23rd 2012, Table of Contents Table of Contents vi English Abstract x German Abstract xi English Keywords xii German Keywords xiii Acknowledgements xiv Dedicate xv 1 General Introduction 1 2 Embedded Architectures: Overview on Hardware and Operating Systems 3 2.1 Embedded Hardware Components . 3 2.1.1 Microcontrollers . 3 2.1.2 Digital Signal Processors (DSP): . 4 2.1.3 System on Chip (SoC): . 5 2.1.4 Programmable Logic Controllers (PLC): . 6 2.2 Real-Time Embedded Operating Systems (RTOS) . 8 2.2.1 QNX . 9 2.2.2 RTLinux . 9 2.2.3 VxWorks . 9 2.2.4 Windows CE . 10 2.3 Known Embedded Software Solutions . 11 2.3.1 Simple Control Loop . 12 2.3.2 Interrupt Controlled System . 12 2.3.3 Cooperative Multitasking . 12 2.3.4 Preemptive Multitasking or Multi-Threading . 12 2.3.5 Microkernels . 13 2.3.6 Monolithic Kernels . 13 2.3.7 Additional Software Components: . 13 2.4 Conclusion . 14 3 Embedded Systems: Overview on Software Components 15 3.1 Basic Concepts of Components . 15 3.2 Architecture Description Languages . 17 3.2.1 Acme Language . -

Ethereal Developer's Guide Draft 0.0.2 (15684) for Ethereal 0.10.11
Ethereal Developer's Guide Draft 0.0.2 (15684) for Ethereal 0.10.11 Ulf Lamping, Ethereal Developer's Guide: Draft 0.0.2 (15684) for Ethere- al 0.10.11 by Ulf Lamping Copyright © 2004-2005 Ulf Lamping Permission is granted to copy, distribute and/or modify this document under the terms of the GNU General Public License, Version 2 or any later version published by the Free Software Foundation. All logos and trademarks in this document are property of their respective owner. Table of Contents Preface .............................................................................................................................. vii 1. Foreword ............................................................................................................... vii 2. Who should read this document? ............................................................................... viii 3. Acknowledgements ................................................................................................... ix 4. About this document .................................................................................................. x 5. Where to get the latest copy of this document? ............................................................... xi 6. Providing feedback about this document ...................................................................... xii I. Ethereal Build Environment ................................................................................................14 1. Introduction .............................................................................................................15 -

Steve Burnett Education Employment
Steve Burnett Raleigh NC [email protected] More details and attached recommendations at http://www.linkedin.com/in/steveburnett Education 1992 M.S. Technical Communication, North Carolina State University 1992 Emergency Medical Technician, Wake Technical Community College 1989 B.A. History, B.A. Economics, NCSU Employment Information Developer III, Hewlett-Packard (formerly Opsware) (November 2007 – present) (HP acquired Opsware effective November 2007.) Creating install, user, and administrator guides for HP SAR (Service Automation Reporter, formerly Opsware OMDB) and HP Live Network (formerly TON) on Linux, Solaris, VMware, and Windows platforms. Sole documentation support for OMDB (1.0, had contributing author for the 1.0.2 release), SAR (7.0, 7.50), and HP Live Network (1.0 to 1.30). Provided Web QA for the HP Live Network Portal. Tools: FrameMaker 7, WebWorks, ClearCase, subversion, RapidSVN, Eclipse, Bugzilla, HP Quality Center, Collabnet, BIRT Report Designer, WebEx, MS SharePoint. Senior Technical Writer, Opsware (January – November 2007) Created install, user, and administrator guides for Opsware OMDB (Operational Management Database) and TON (The Opsware Network) on Linux, Solaris, and Windows platforms. Worked with Technical Support on CMS selection. Tools: FrameMaker 7, WebWorks, ClearCase, subversion, Bugzilla, Quality Center, Collabnet, BIRT Report Designer, WebEx. Technical Writer, SAS Institute (contract, Apex Systems) (November 2005 – January 2007) SAS Technical Support: Internal and external documentation. Tools: SAS, SIRIUS, SOS. SAS R&D: Internal and external documentation. Tools: SAS, WebLogic, Xythos, SQL. Systems Administrator, SAS Institute (contract, Apex Systems) (March – September 2005) SAS Solutions: Provided Linux, Windows, Solaris, and HP-UX server system administration, technical support, and internal training for an ASP (application service provider) team. -

Extreme Programming Unit Testing
Programming Tools Lecture Plan for Group Projects ● Unit testing ● Version control ● Building Richard Smith ● Debugging [email protected] – Logging ● Documenting – Code – Reports 1 2 Biased General advice ● Use a Unix based operating system – Solaris in the labs – Mac OS X if you are buying a laptop – Install Linux if you have a PC at home Unit testing ● Learn how to do everything using the command line, then use an IDE! – Xemacs – difficult to learn, but integrates well with command line and has modes for everything – Eclipse – easier to learn, specialised for Java ● Use Java or C++ or 'script' (Python, Ruby, Perl) as appropriate 3 4 Background: Extreme Unit Testing Programming ● Pair programming ● Write tests before code. ● Small releases ● Code not done until tests all run. ● Metaphor ● Re-run tests after any major changes ● Simple design ● Can be confident that nothing has ● Testing broken. ● Refactoring ● Hence not afraid to refactor. www.extremeprogramming.org 5 6 Tools for Testing Installing CPPUnit ● Some functional tests can be manual. ● We use GNU compiler on Unix-like OS (Linux, FreeBSD) ● Possible to automate most tests. ● wget http://aleron.dl.sourceforge.net/sourceforge/cppunit/cppuni ● Tools exist to make this easy and t-1.10.2.tar.gz provide GUI. ● tar xvfz cppunit-1.10.2.tar.gz ● cd cppunit-1.10.2 ● Java – JUnit – www.junit.org ● ./configure; make ● C++ – CPPunit – cppunit.sf.net ● su -c 'make install' ● su -c 'ldconfig' ● Installation of GUI library is a bit more complicated :-( 7 8 Or you can use mine! C++ Example ● bash ● Class diagram ● export LD_LIBRARY_PATH=/cs/research/nets/home/marine/ucacrts /g2/local/lib ● export PATH=/cs/research/nets/home/marine/ucacrts/g2/local/b in:$PATH 9 10 C++ Example C++ Example Cat.h Animal. -
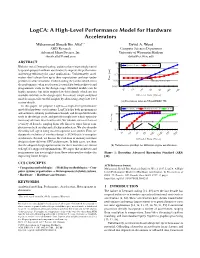
Logca: a High-Level Performance Model for Hardware Accelerators Muhammad Shoaib Bin Altaf ∗ David A
LogCA: A High-Level Performance Model for Hardware Accelerators Muhammad Shoaib Bin Altaf ∗ David A. Wood AMD Research Computer Sciences Department Advanced Micro Devices, Inc. University of Wisconsin-Madison [email protected] [email protected] ABSTRACT 10 With the end of Dennard scaling, architects have increasingly turned Unaccelerated Accelerated 1 to special-purpose hardware accelerators to improve the performance and energy efficiency for some applications. Unfortunately, accel- 0.1 erators don’t always live up to their expectations and may under- perform in some situations. Understanding the factors which effect Time (ms) 0.01 Break-even point the performance of an accelerator is crucial for both architects and 0.001 programmers early in the design stage. Detailed models can be 16 64 highly accurate, but often require low-level details which are not 256 1K 4K 16K 64K available until late in the design cycle. In contrast, simple analytical Offloaded Data (Bytes) models can provide useful insights by abstracting away low-level system details. (a) Execution time on UltraSPARC T2. In this paper, we propose LogCA—a high-level performance 100 model for hardware accelerators. LogCA helps both programmers SPARC T4 UltraSPARC T2 GPU and architects identify performance bounds and design bottlenecks 10 early in the design cycle, and provide insight into which optimiza- tions may alleviate these bottlenecks. We validate our model across Speedup 1 Break-even point a variety of kernels, ranging from sub-linear to super-linear com- plexities on both on-chip and off-chip accelerators. We also describe the utility of LogCA using two retrospective case studies. -

Foreign Library Interface by Daniel Adler Dia Applications That Can Run on a Multitude of Plat- Forms
30 CONTRIBUTED RESEARCH ARTICLES Foreign Library Interface by Daniel Adler dia applications that can run on a multitude of plat- forms. Abstract We present an improved Foreign Function Interface (FFI) for R to call arbitary na- tive functions without the need for C wrapper Foreign function interfaces code. Further we discuss a dynamic linkage framework for binding standard C libraries to FFIs provide the backbone of a language to inter- R across platforms using a universal type infor- face with foreign code. Depending on the design of mation format. The package rdyncall comprises this service, it can largely unburden developers from the framework and an initial repository of cross- writing additional wrapper code. In this section, we platform bindings for standard libraries such as compare the built-in R FFI with that provided by (legacy and modern) OpenGL, the family of SDL rdyncall. We use a simple example that sketches the libraries and Expat. The package enables system- different work flow paths for making an R binding to level programming using the R language; sam- a function from a foreign C library. ple applications are given in the article. We out- line the underlying automation tool-chain that extracts cross-platform bindings from C headers, FFI of base R making the repository extendable and open for Suppose that we wish to invoke the C function sqrt library developers. of the Standard C Math library. The function is de- clared as follows in C: Introduction double sqrt(double x); We present an improved Foreign Function Interface The .C function from the base R FFI offers a call (FFI) for R that significantly reduces the amount of gate to C code with very strict conversion rules, and C wrapper code needed to interface with C. -

Hardware, Firmware, Devices Disks Kernel, Boot, Swap Files, Volumes
hardware, kernel, boot, firmware, disks files, volumes swap devices software, security, patching, networking references backup tracing, logging TTAASSKK\ OOSS AAIIXX AA//UUXX DDGG//UUXX FFrreeeeBBSSDD HHPP--UUXX IIRRIIXX Derived from By IBM, with Apple 1988- 4.4BSD-Lite input from 1995. Based and 386BSD. System V, BSD, etc. on AT&T Data General This table SysV.2.2 with was aquired does not Hewlett- SGI. SVR4- OS notes Runs mainly extensions by EMC in include Packard based on IBM from V.3, 1999. external RS/6000 and V.4, and BSD packages related 4.2 and 4.3 from hardware. /usr/ports. /usr/sysadm ssmmiitt ssaamm /bin/sysmgr (6.3+) ssmmiittttyy ttoooollcchheesstt administrativ /usr/Cadmin/ wwssmm FFiinnddeerr ssyyssaaddmm ssyyssiinnssttaallll ssmmhh (11.31+) e GUI bin/* /usr/sysadm/ useradd (5+) FFiinnddeerr uusseerraadddd aadddduusseerr uusseerraadddd privbin/ addUserAcco userdell (5+) //eettcc//aadddduusseerr uusseerrddeell cchhppaassss uusseerrddeell unt usermod edit rrmmuusseerr uusseerrmmoodd managing (5+) /etc/passwd users llssuusseerr ppww ggeettpprrppww ppaassssmmggmmtt mmkkuusseerr vviippww mmooddpprrppww /usr/Cadmin/ cchhuusseerr ppwwggeett bin/cpeople rmuser usrck TASK \ OS AAIIXX AA//UUXX DDGG//UUXX FFrreeeeBBSSDD HHPP--UUXX IIRRIIXX pprrttccoonnff uunnaammee iioossccaann hhiinnvv dmesg (if (if llssccffgg ssyyssccttll--aa you're lucky) llssaattttrr ddmmeessgg aaddbb ssyyssiinnffoo--vvvv catcat lsdev /var/run/dm model esg.boot stm (from the llssppaatthh ppcciiccoonnff--ll SupportPlus CDROM) list hardware dg_sysreport - bdf (like -

How to Cheat at Configuring Open Source Security Tools
436_XSS_FM.qxd 4/20/07 1:18 PM Page ii 441_HTC_OS_FM.qxd 4/12/07 1:32 PM Page i Visit us at www.syngress.com Syngress is committed to publishing high-quality books for IT Professionals and deliv- ering those books in media and formats that fit the demands of our customers. We are also committed to extending the utility of the book you purchase via additional mate- rials available from our Web site. SOLUTIONS WEB SITE To register your book, visit www.syngress.com/solutions. Once registered, you can access our [email protected] Web pages. There you may find an assortment of value- added features such as free e-books related to the topic of this book, URLs of related Web sites, FAQs from the book, corrections, and any updates from the author(s). ULTIMATE CDs Our Ultimate CD product line offers our readers budget-conscious compilations of some of our best-selling backlist titles in Adobe PDF form. These CDs are the perfect way to extend your reference library on key topics pertaining to your area of expertise, including Cisco Engineering, Microsoft Windows System Administration, CyberCrime Investigation, Open Source Security, and Firewall Configuration, to name a few. DOWNLOADABLE E-BOOKS For readers who can’t wait for hard copy, we offer most of our titles in downloadable Adobe PDF form. These e-books are often available weeks before hard copies, and are priced affordably. SYNGRESS OUTLET Our outlet store at syngress.com features overstocked, out-of-print, or slightly hurt books at significant savings. SITE LICENSING Syngress has a well-established program for site licensing our e-books onto servers in corporations, educational institutions, and large organizations. -

Basics of UNIX
Basics of UNIX August 23, 2012 By UNIX, I mean any UNIX-like operating system, including Linux and Mac OS X. On the Mac you can access a UNIX terminal window with the Terminal application (under Applica- tions/Utilities). Most modern scientific computing is done on UNIX-based machines, often by remotely logging in to a UNIX-based server. 1 Connecting to a UNIX machine from {UNIX, Mac, Windows} See the file on bspace on connecting remotely to SCF. In addition, this SCF help page has infor- mation on logging in to remote machines via ssh without having to type your password every time. This can save a lot of time. 2 Getting help from SCF More generally, the department computing FAQs is the place to go for answers to questions about SCF. For questions not answered there, the SCF requests: “please report any problems regarding equipment or system software to the SCF staff by sending mail to ’trouble’ or by reporting the prob- lem directly to room 498/499. For information/questions on the use of application packages (e.g., R, SAS, Matlab), programming languages and libraries send mail to ’consult’. Questions/problems regarding accounts should be sent to ’manager’.” Note that for the purpose of this class, questions about application packages, languages, li- braries, etc. can be directed to me. 1 3 Files and directories 1. Files are stored in directories (aka folders) that are in a (inverted) directory tree, with “/” as the root of the tree 2. Where am I? > pwd 3. What’s in a directory? > ls > ls -a > ls -al 4. -

Version Control with Subversion for Subversion 1.1 (Book Compiled from Revision 1337)
Version Control with Subversion For Subversion 1.1 (book compiled from Revision 1337) Ben Collins-Sussman Brian W. Fitzpatrick C. Michael Pilato Version Control with Subversion: For Subversion 1.1: (book com- piled from Revision 1337) by Ben Collins-Sussman, Brian W. Fitzpatrick, and C. Michael Pilato Published (TBA) Copyright © 2002, 2003, 2004, 2005 Ben Collins-SussmanBrian W. FitzpatrickC. Michael Pilato This work is licensed under the Creative Commons Attribution License. To view a copy of this license, visit http://creativecommons.org/licenses/by/2.0/ or send a letter to Creative Commons, 559 Nathan Abbott Way, Stanford, California 94305, USA. Table of Contents Foreword......................................................................................................................................11 Preface.........................................................................................................................................13 Audience ..............................................................................................................................13 How to Read this Book ........................................................................................................... 13 Conventions Used in This Book ................................................................................................ 14 TypographicConventions ................................................................................................14 Icons ...........................................................................................................................14 -

Oracle1® VM Virtualbox1® User Manual
Oracle R VM VirtualBox R User Manual Version 6.1.0_RC1 c 2004-2019 Oracle Corporation http://www.virtualbox.org Contents Preface i 1 First Steps 1 1.1 Why is Virtualization Useful?.............................2 1.2 Some Terminology..................................2 1.3 Features Overview..................................3 1.4 Supported Host Operating Systems.........................5 1.5 Host CPU Requirements...............................6 1.6 Installing Oracle VM VirtualBox and Extension Packs...............6 1.7 Starting Oracle VM VirtualBox............................7 1.8 Creating Your First Virtual Machine.........................8 1.9 Running Your Virtual Machine............................ 11 1.9.1 Starting a New VM for the First Time................... 12 1.9.2 Capturing and Releasing Keyboard and Mouse.............. 12 1.9.3 Typing Special Characters.......................... 13 1.9.4 Changing Removable Media........................ 14 1.9.5 Resizing the Machine’s Window...................... 14 1.9.6 Saving the State of the Machine...................... 15 1.10 Using VM Groups................................... 16 1.11 Snapshots....................................... 17 1.11.1 Taking, Restoring, and Deleting Snapshots................ 17 1.11.2 Snapshot Contents............................. 18 1.12 Virtual Machine Configuration............................ 19 1.13 Removing and Moving Virtual Machines...................... 19 1.14 Cloning Virtual Machines............................... 20 1.15 Importing and Exporting Virtual Machines.................... -

Symbian Os � 925
CONTENTS PREFACE xxiv 1 INTRODUCTION 1 1.1 WHAT IS AN OPERATING SYSTEM? 3 1.1.1 The Operating System as an Extended Machine 4 1.1.2 The Operating System as a Resource Manager 6 1.2 HISTORY OF OPERATING SYSTEMS 7 1.2.1 The First Generation (1945-55) Vacuum Tubes 7 1.2.2 The Second Generation (1955-65) Transistors and Batch Systems 8 1.2.3 The Third Generation (1965-1980) ICs and Multiprogramming 10 1.2.4 The Fourth Generation (1980—Present) Personal Computers 13 1.3 COMPUTER HARDWARE REVIEW 17 1.3.1 Processors 17 1.3.2 Memory 21 1.3.3 Disks 24 1.3.4 Tapes 25 1.3.5 1/0 Devices 25 1.3.6 Buses 28 1.3.7 Booting the Computer 31 vii Viii CONTENTS 1.4 THE OPERATING SYSTEM ZOO 31 1.4.1 Mainframe Operating Systems 32 1.4.2 Server Operating Systems 32 1.4.3 Multiprocessor Operating Systems 32 1.4.4 Personal Computer Operating Systems 33 1.4.5 Handheld Computer Operating Systems 33 1.4.6 Embedded Operating Systems. 33 1.4.7 Sensor Node Operating Systems 34 1.4.8 Real-Time Operating Systems 34 1.4.9 Smart Card Operating Systems 35 1.5 OPERATING SYSTEM CONCEPTS 35 1.5.1 Processes 36 1.5.2 Address Spaces 38 1.5.3 Files 38 1.5.4 Input/Output 41 1.5.5 Protection 42 1.5.6 The Shell 42 1.5.7 Ontogeny Recapitulates Phylogeny 44 1.6 SYSTEM CALLS 47 1.6.1 System Calls for Process Management 50 1.6.2 System Calls for File Management 54 1.6.3 System Calls for Directory Management 55 1.6.4 Miscellaneous System Calls 56 1.6.5 The Windows Win32 API 57 1.7 OPERATING SYSTEM STRUCTURE 60 1.7.1 Monolithic Systems 60 1.7.2 Layered Systems 61 1.7.3 Microkernels 62 1.7.4