FASTLY, INC. (Exact Name of Registrant As Specified in Its Charter) ______
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-
Global Glitch: Swaths of Internet Go Down After Cloud Outage 8 June 2021, by Kelvin Chan
Global glitch: Swaths of internet go down after cloud outage 8 June 2021, by Kelvin Chan The company said in an emailed statement that it was a "technical issue" and "not related to a cyber attack." Still, major futures markets in the U.S. dipped sharply minutes after the outage, which came a month after hackers forced the shutdown of the biggest fuel pipeline in the U.S. Fastly is a content-delivery network, or CDN. It provides vital but behind-the-scenes cloud computing "edge servers" to many of the web's popular sites. These servers store, or "cache," content such as images and video in places around the world so that it is closer to users, allowing them to fetch it more quickly and smoothly. This Jan. 17, 2001 file photo shows people entering CNN Center, the headquarters for CNN, in downtown Atlanta. Numerous websites were unavailable on Fastly says its services mean that a European user Tuesday June 8, 2021, after an apparent widespread going to an American website can get the content outage at cloud service company Fastly. Dozens of high- 200 to 500 milliseconds faster. traffic websites including the New York Times, CNN, Twitch and the U.K. government's home page, could not be reached. Credit: AP Photo/Ric Feld, File Dozens of websites went down briefly around the globe Tuesday, including CNN, The New York Times and Britain's government home page, after an outage at the cloud computing service Fastly, illustrating how vital a small number of behind-the- scenes companies have become to running the internet. -

Annual Report 2018 2 Annual Report 2018
ANNUAL REPORT 2018 2 ANNUAL REPORT 2018 ACCELERATING GROWTH PLAYING BY THE NEW RULES: IN THE DIRECT BRAND DATA GOVERNANCE, ECONOMY REVOLUTION ETHICS, AND LEGISLATION et’s not mince words: 2018 was a year of We see no reason to believe this direct brand ata is to the 21st century what capital massive disruption by any measure—and all economy will slow down, let alone go into reverse. This was to the 20th century. If you doubt that, Lsigns point to this disruption accelerating in “stack-your-own supply chain” is now so advanced and Dconsider this: In 2018, American companies 2019 and beyond. so embedded in the economy that the trends we’ve spent nearly $19.2 billion on the acquisition of For over a century, dominant consumer-facing seen for the past decade will only accelerate. audience data and on solutions to manage, process, companies created value through their ownership and and analyze digital audience data—a figure that operation of high-barrier-to-entry, capital-intensive It also represents an incredible represents a staggering 17.5 percent increase supply chains. The most successful companies owned opportunity for those who understand from the prior year (State of Data 2018 Report, outright or had significant control over every major the power of interactive media in this Winterberry Group, IAB). function within their supply chain, from the sourcing of new world order. This is the current data landscape—and the raw materials to the ownership of their factories and elephant in the room. warehouses, to the railway cars and trucks that got Digital advertising—whether display, search, or Our industry is at the center of a seismic change If you don’t have consumers’ trust, their goods to market. -

Public Company Analysis 6
MOBILE SMART FUNDAMENTALS MMA MEMBERS EDITION NOVEMBER 2014 messaging . advertising . apps . mcommerce www.mmaglobal.com NEW YORK • LONDON • SINGAPORE • SÃO PAULO MOBILE MARKETING ASSOCIATION NOVEMBER 2014 REPORT Measurement & Creativity Thoughts for 2015 Very simply, mobile marketing will continue to present the highest growth opportunities for marketers faced with increasing profitability as well as reaching and engaging customers around the world. Widely acknowledged to be the channel that gets you the closest to your consumers, those marketers that leverage this uniqueness of mobile will gain competitive footholds in their vertical markets, as well as use mobile to transform their marketing and their business. The MMA will be focused on two cores issues which we believe will present the biggest opportunities and challenges for marketers and the mobile industry in 2015: Measurement and Creativity. On the measurement side, understanding the effectiveness of mobile: the ROI of a dollar spent and the optimized level for mobile in the marketing mix will become more and more critical as increased budgets are being allocated towards mobile. MMA’s SMoX (cross media optimization research) will provide the first-ever look into this. Additionally, attribution and understanding which mobile execution (apps, video, messaging, location etc…) is working for which mobile objective will be critical as marketers expand their mobile strategies. On the Creative side, gaining a deeper understanding of creative effectiveness cross-screen and having access to case studies from marketers that are executing some beautiful campaigns will help inspire innovation and further concentration on creating an enhanced consumer experience specific to screen size. We hope you’ve had a successful 2014 and we look forward to being a valuable resource to you again in 2015. -

A View from the Edge: a Stub-AS Perspective of Traffic Localization
A View From the Edge: A Stub-AS Perspective of Traffic Localization and its Implications Bahador Yeganeh Reza Rejaie Walter Willinger University of Oregon University of Oregon NIKSUN, Inc. [email protected] [email protected] [email protected] Abstract—Serving user requests from near-by caches or servers to implement their business model for getting content closer has been a powerful technique for localizing Internet traffic with to the end users. For example, while Akamai [1] operates and the intent of providing lower delay and higher throughput to maintains a global infrastructure consisting of more then 200K end users while also lowering the cost for network operators. This basic concept has led to the deployment of different types of servers located in more than 1.5K different ASes to bring the infrastructures of varying degrees of complexity that large CDNs, requested content by its customers closer to the edge of the ISPs, and content providers operate to localize their user traffic. network where this content is consumed, other CDNs such Prior measurement studies in this area have focused mainly on as Limelight or EdgeCast rely on existing infrastructure in revealing these deployed infrastructures, reverse-engineering the the form of large IXPs to achieve this task [2]. Similar to techniques used by these companies to map end users to close- by caches or servers, or evaluating the performance benefits that Akamai but smaller in scale, major CPs such as Google and “typical” end users experience from well-localized traffic. Netflix negotiate with third-party networks to deploy their own To our knowledge, there has been no empirical study that caches or servers that are then used to serve exclusively the assesses the nature and implications of traffic localization as CP’s own content. -

Annual Report 2017 Iab Annual Report 2017
ANNUAL REPORT 2017 IAB ANNUAL REPORT 2017 dynamic creative powerhouses apply their storytelling expertise to build marketers’ brands. Similarly, the 2017 IAB Leadership Dialogues were a first-ever Building 21st Century Brands: series of discussions with transformative leaders in business, politics, economics, and technology to gain The Race to the New Economy insights from and debate critical industry, political, and economic issues with each other. A cross-screen economy requires new standards and ife in America in 2017 was lived inside a series a time. These direct brands—as well as the incumbents guidelines to grow the marketplace, and IAB and the of paradoxes, all of them balanced on one side that join their club—are the growth engine of the new L IAB Tech Lab introduced the completely revamped by the ongoing economic boom, characterized by brand economy. IAB Standard Ad Unit Portfolio, featuring dynamic a bull market now in its 10th year. We had political more than 14,800 digital media professionals Adapting to this new landscape is not optional either: ads that allow for flexible creative on a multitude turmoil … and economic boom. Populist revolt … have advanced through the IAB Certification Two-thirds of consumers now expect direct brand of screen sizes and resolution capabilities and that and economic boom. Immigration mania … and Programs and Professional Development initiatives. connectivity. puts user experience front and center. Another major economic boom. Media disruption … and economic accelerator for growth is a trustworthy supply chain. An emerging economy and fast-changing media boom. Retail apocalypse … and economic boom. THE WORLD HAS SHIFTED FROM AN A major initiative for the Tech Lab in this area was INDIRECT BRAND ECONOMY TO A landscape also requires an active eye on policy, and In the digital media and marketing industries, we DIRECT BRAND ECONOMY. -

Domain Shadowing: Leveraging Content Delivery Networks for Robust Blocking-Resistant Communications
Domain Shadowing: Leveraging Content Delivery Networks for Robust Blocking-Resistant Communications Mingkui Wei Cybersecurity Engineering George Mason University, Fairfax, VA, 22030 Abstract according to the Host header but have the TLS connection still appear to belong to the allowed domain. The blocking- We debut domain shadowing, a novel censorship evasion resistance of domain fronting derives from the significant technique leveraging content delivery networks (CDNs). Do- “collateral damage”, i.e., to disable domain fronting, the censor main shadowing exploits the fact that CDNs allow their cus- needs to block users from accessing the entire CDN, resulting tomers to claim arbitrary domains as the back-end. By set- in all domains on the CDN inaccessible. Because today’s ting the front-end of a CDN service as an allowed domain Internet relies heavily on web caches and many high-profile and the back-end a blocked one, a censored user can access websites also use CDNs to distribute their content, completely resources of the blocked domain with all “indicators”, includ- blocking access to a particular CDN may not be a feasible ing the connecting URL, the SNI of the TLS connection, and option for the censor. Because of its strong blocking-resistant the Host header of the HTTP(S) request, appear to belong power, domain fronting has been adopted by many censorship to the allowed domain. Furthermore, we demonstrate that evasion systems since it has been proposed [24, 28, 34, 36]. domain shadowing can be proliferated by domain fronting, In the last two years, however, many CDNs began to disable a censorship evasion technique popularly used a few years domain fronting by enforcing the match between the SNI and ago, making it even more difficult to block. -

Exploring the Interplay Between CDN Caching and Video Streaming Performance
Exploring the interplay between CDN caching and video streaming performance Ehab Ghabashneh and Sanjay Rao Purdue University Abstract—Content Delivery Networks (CDNs) are critical for our goal of understanding performance implications for such optimizing Internet video delivery. In this paper, we characterize videos. For each chunk in a video session, our measurements how CDNs serve video content, and the implications for video characterize where in the CDN hierarchy (or origin) the chunk performance, especially emerging 4K video streaming. Our work is based on measurements of multiple well known video pub- is served from, the application-perceived throughput, the chunk lishers served by top CDNs. Our results show that (i) video size, and the latency incurred before each chunk is received. chunks in a session often see heterogeneous behavior in terms of Our results show that it is common for chunks in a video whether they hit in the CDN, and which layer they are served session to be served from different layers in the CDN hierarchy from; and (ii) application throughput can vary significantly even or the origin. Further, while there is a higher tendency for across chunks in a session based on where they are served from. The differences while sensitive to client location and CDN can chunks at the start of a session to be served from edge locations, sometimes be significant enough to impact the viability of 4K even chunks later in the session may be served from multiple streaming. We consider the implications for Adaptive bit rate locations. Interestingly, some sessions may exhibit significant (ABR) algorithms given they rely on throughput prediction, and switching in terms of the location from which consecutive are agnostic to whether objects hit in the CDN and where. -

3000 Applications
Uila Supported Applications and Protocols updated March 2021 Application Protocol Name Description 01net.com 05001net plus website, is a Japanese a French embedded high-tech smartphonenews site. application dedicated to audio- 050 plus conferencing. 0zz0.com 0zz0 is an online solution to store, send and share files 10050.net China Railcom group web portal. This protocol plug-in classifies the http traffic to the host 10086.cn. It also classifies 10086.cn the ssl traffic to the Common Name 10086.cn. 104.com Web site dedicated to job research. 1111.com.tw Website dedicated to job research in Taiwan. 114la.com Chinese cloudweb portal storing operated system byof theYLMF 115 Computer website. TechnologyIt is operated Co. by YLMF Computer 115.com Technology Co. 118114.cn Chinese booking and reservation portal. 11st.co.kr ThisKorean protocol shopping plug-in website classifies 11st. the It ishttp operated traffic toby the SK hostPlanet 123people.com. Co. 123people.com Deprecated. 1337x.org Bittorrent tracker search engine 139mail 139mail is a chinese webmail powered by China Mobile. 15min.lt ChineseLithuanian web news portal portal 163. It is operated by NetEase, a company which pioneered the 163.com development of Internet in China. 17173.com Website distributing Chinese games. 17u.com 20Chinese minutes online is a travelfree, daily booking newspaper website. available in France, Spain and Switzerland. 20minutes This plugin classifies websites. 24h.com.vn Vietnamese news portal 24ora.com Aruban news portal 24sata.hr Croatian news portal 24SevenOffice 24SevenOffice is a web-based Enterprise resource planning (ERP) systems. 24ur.com Slovenian news portal 2ch.net Japanese adult videos web site 2Checkout (acquired by Verifone) provides global e-commerce, online payments 2Checkout and subscription billing solutions. -

1 Navigating Advertising's New World Order
President’s Report November 4, 2016 Navigating Advertising’s New World Order By Randall Rothenberg As we head into the last weeks of 2016, it has become abundantly clear that user experience is the grand opportunity that stands in front of us—and it is also the great crisis of our time in the marketing and media industries. Our unbridled infatuation with new technologies and our desire to drive costs as low as possible—regardless of the consequences—have contributed to a form of consumer abuse in digital advertising. By neglecting a founding mantra of the internet—“the consumer is in control”—we have contributed to making the very concept of advertising a pariah among the consumers we serve. Frustrated consumers have responded by adopting ad-blocking software at alarming rates. Nowhere was this new tension more on display than at this year’s IAB MIXX conference which featured some of the most powerful digital content we’ve seen in years—and highlighted the challenges and opportunities our industry faces. The theme of the MIXX event was “Advertising’s New World Order,” acknowledging both the innovation and chaos seen on every platform, as well as consumers’ demand for more original, personal, and provocative experiences. We’re confident there is a way forward that will keep us on the path toward opportunity. At IAB, our efforts on our members’ behalf are all in support of navigating this new world order. Among the biggest efforts underway, we announced and released for public comment a complete overhaul of the IAB Standard Ad Unit Portfolio. -

Telstra Ventures in the Digital Age 2
Connecting the dots Telstra Ventures in the Digital Age 2. Backing Winners Telstra Ventures Telstra Ventures is a strategic growth investor in lighthouse technology companies that are commencing scale. We provide venture capital investment via a “Strategic Growth Investment” approach. This approach offers entrepreneurs access to genuine revenue growth beyond the investment itself and shortens the time to reach global scale. We support this growth through investment capital and leadership. Our heritage combined with our association with Telstra and its capabilities help accelerate growth for the entrepreneurs in our portfolio. In almost a decade we have invested over $250 million in over 60 companies, generated more than $150+ million in revenue for our portfolio companies and managed 13 liquidity events. We are backed by our strategic investors Telstra, one of the 20 largest telecommunications providers globally and HarbourVest, one of the world’s largest private equity funds. Back 2 Next 3.2. OurBackingVentures Winners What we look for We focus on high-growth opportunities that are strategically aligned to Telstra customers and partners Based in SiliconValley, Led by proven entrepreneurs Australia and the Asia who have successfully built Pacific region and sold companiesbefore Offer world-class Are later stage innovation with bestof venture capital /growth breed technologies / equity investments products / services Back 3 Next 3.2. OurBackingVentures Winners Where we invest Reflecting our customers’ priorities and our existing solution suite, areas of interest at the moment include cloud,mobile and media. We typically invest between $5M and $50M in established business that have already won millions of dollars in existing revenue. -

Protecting Web Applications and Apis from Exploits and Abuse
This research note is restricted to the personal use of [email protected]. Protecting Web Applications and APIs From Exploits and Abuse Published: 24 April 2019 ID: G00383318 Analyst(s): Frank Catucci, Michael Isbitski, Ramon Krikken Web applications, mobile applications and web APIs are subject to increasing volumes and complexity of attacks. Security and risk management technical professionals responsible for application security architecture must use an appropriate mix of mitigating technologies to secure applications. Key Findings ■ Automated attack and abuse patterns have evolved, making firewalls and intrusion detection and prevention systems ineffective. Web application firewalls and API gateways only provide a partial solution. Bot mitigation capabilities can help by addressing the growing number of abuse scenarios. ■ Product categories, such as runtime application self-protection and application shielding, are emerging to fill gaps in application and API security. They can provide exploit mitigation, abuse mitigation and access control capabilities at different layers of an overall system implementation. ■ Modern application design and architectures affect edge and inner architecture defenses. A subset of protections and respective placement closer to workloads are beneficial, if not necessary, in protecting these modern architectures from attacks. Recommendations Security and risk management technical professionals focusing on security of applications should: ■ Identify integrated capabilities in existing solutions, emphasizing a cloud-first approach for flexibility and favoring security as a service over virtual appliances. Use strong exploit prevention and access control capabilities — security SDKs, WAFs or RASP for exploit prevention, and API gateways — for API access control and management. ■ Deploy integrated capabilities or dedicated solutions, DDoS protection, and bot mitigation based on expected levels of application and API abuse, as well as desired level of configurability. -
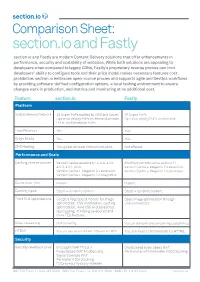
Section.Io and Fastly
Comparison Sheet: section.io and Fastly section.io and Fastly are modern Content Delivery solutions that offer enhancements in performance, security and scalability of websites. While both solutions are appealing to developers when compared to legacy CDNs, Fastly’s proprietary reverse proxies can limit developers’ ability to configure tools and their price model makes necessary features cost prohibitive. section.io embraces open-source proxies and supports agile and DevOps workflows by providing software-defined configuration options, a local testing environment to ensure changes work in production, and metrics and monitoring at no additional cost. Feature section.io Fastly Platform Global Delivery Network 29 Super PoPs backed by AWS and Azure. 35 Super PoPs. Option to deploy PoPs on demand, private Option to deploy PoPs on demand. PoPs, and Developer PoPs. Load Balancer Yes. Yes. Origin Shield Yes. Yes. DNS Hosting Yes, global Anycast network included. Not offered. PerformancePerformance + Scale and Scale Caching reverse proxies Varnish Cache versions 5.1.2, 5.0, 4.1.5, Modified Varnish Cache version 2.1 4.0.3, 4.0.1, 3.0.5 .Varnish Cache + Magento 2.x extension Varnish Cache + Magento 2.x extension Varnish Cache + Magento 1.x extension Varnish Cache + Magento 1.x integration Cache clear time Instant. Instant. Caching types Static + dynamic content. Static + dynamic content. Front End Optimizations Google’s PageSpeed module for image Basic image optimization through optimization, CSS minification, caching undisclosed tool. optimization, Inine CSS and JavaScript, lazy loading, minifying JavaScript and more FEO features. Video streaming Not currently. Yes, on demand and streaming capabilities. HTTP/2 Yes, no extra cost for HTTPS and HTTP/2.