Towards an Efficient Online Causal-Event-Pattern-Matching Framework
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Efficient Pattern Matching Over Event Streams
Efficient Pattern Matching over Event Streams ∗ Jagrati Agrawal, Yanlei Diao, Daniel Gyllstrom, and Neil Immerman Department of Computer Science University of Massachusetts Amherst Amherst, MA, USA fjagrati, yanlei, dpg, [email protected] ABSTRACT against complex patterns and the events used to match each Pattern matching over event streams is increasingly being pattern are transformed into new events for output. Re- employed in many areas including financial services, RFID- cently, such pattern matching over streams has aroused sig- based inventory management, click stream analysis, and elec- nificant interest in industry [28, 30, 29, 9] due to its wide tronic health systems. While regular expression matching applicability in areas such as financial services [10], RFID- is well studied, pattern matching over streams presents two based inventory management [31], click stream analysis [26], new challenges: Languages for pattern matching over streams and electronic health systems [16]. In financial services, for are significantly richer than languages for regular expression instance, a brokerage customer may be interested in a se- matching. Furthermore, efficient evaluation of these pattern quence of stock trading events that represent a new market queries over streams requires new algorithms and optimiza- trend. In RFID-based tracking and monitoring, applica- tions: the conventional wisdom for stream query processing tions may want to track valid paths of shipments and detect (i.e., using selection-join-aggregation) is inadequate. anomalies such as food contamination in supply chains. In this paper, we present a formal evaluation model that While regular expression matching is a well studied com- offers precise semantics for this new class of queries and a puter science problem [17], pattern matching over streams query evaluation framework permitting optimizations in a presents two new challenges: principled way. -

Cayuga: a General Purpose Event Monitoring System
Cayuga: A General Purpose Event Monitoring System Alan Demers1, Johannes Gehrke1, Biswanath Panda1 ∗ † Mirek Riedewald1, Varun Sharma2 , and Walker White1 1Department of Computer Science, Cornell University 2Computer Science and Engineering, Indian Institute of Technology Delhi ABSTRACT number of concurrent queries registered in the event processing We describe the design and implementation of the Cornell Cayuga system. This is similar to the workload of publish/subscribe sys- System for scalable event processing. We present a query language tems. In comparison, data stream management systems are usually based on Cayuga Algebra for naturally expressing complex event less scalable in the number of queries, capable of supporting only patterns. We also describe several novel system design and im- a small number of concurrent queries. plementation issues, focusing on Cayuga’s query processor, its in- We have designed and built Cayuga, a general-purpose system dexing approach, how Cayuga handles simultaneous events, and its for processing complex events on a large scale [8]. Cayuga supports specialized garbage collector. on-line detection of a large number of complex patterns in event streams. Event patterns are written in a query language based on operators which have well-defined formal semantics. This enables 1. INTRODUCTION Cayuga to perform query-rewrite optimizations. All operators are A large class of both well-established and emerging applications composable, allowing Cayuga to build up complex patterns from can best be described as -

Episodic Memory Representation in a Knowledge Base, with Application to Event Monitoring and Event Detection
Episodic Memory Representation in a Knowledge Base, with Application to Event Monitoring and Event Detection Master’s Thesis Engin C¸ınar S¸ahin Committee Members Scott E. Fahlman Eric Nyberg Stephen F. Smith Language Technologies Institute School of Computer Science Carnegie Mellon University Pittsburgh, PA, 15213 Abstract The thesis explores the use of a knowledge-based AI system to assist people in executing proce- dures and detecting events in an observed world. We extend the Scone knowledge-base system with open-ended facilities for representing time and events. Then we use this episodic knowledge repre- sentation as the foundation for our event monitoring and event detection algorithms. This approach lets us represent and reason about three fundamental aspects of the observed events: 1. their ontological character and what entities take part in these events (e.g. buying is a kind of transaction that involves an agent, a seller, money and goods) 2. how events change the world over time (e.g. after a buy event the agent has the goods rather than the money) 3. how events may be composed of other subevents (i.e. a buy event may be composed of giving money and receiving goods) We illustrate knowledge-based solutions to the event monitoring problem in the conference organization domain and to the event detection problem in the national security domain. i Acknowledgements First, I would like to thank my advisor Scott Fahlman for letting me learn so much from him. His invaluable experience and constant support helped me go through the ups and downs of research. Working with him, his passion and excitement for knowledge representation and reasoning has passed on to me. -

Complex Event Processing As a Service in Multi-Cloud Environments
Western University Scholarship@Western Electronic Thesis and Dissertation Repository August 2016 Complex Event Processing as a Service in Multi-Cloud Environments Wilson A. Higashino The University of Western Ontario Supervisor Dr. Miriam A. M. Capretz The University of Western Ontario Graduate Program in Electrical and Computer Engineering A thesis submitted in partial fulfillment of the equirr ements for the degree in Doctor of Philosophy © Wilson A. Higashino 2016 Follow this and additional works at: https://ir.lib.uwo.ca/etd Part of the Databases and Information Systems Commons Recommended Citation Higashino, Wilson A., "Complex Event Processing as a Service in Multi-Cloud Environments" (2016). Electronic Thesis and Dissertation Repository. 4016. https://ir.lib.uwo.ca/etd/4016 This Dissertation/Thesis is brought to you for free and open access by Scholarship@Western. It has been accepted for inclusion in Electronic Thesis and Dissertation Repository by an authorized administrator of Scholarship@Western. For more information, please contact [email protected]. Abstract The rise of mobile technologies and the Internet of Things, combined with advances in Web technologies, have created a new Big Data world in which the volume and velocity of data gen- eration have achieved an unprecedented scale. As a technology created to process continuous streams of data, Complex Event Processing (CEP) has been often related to Big Data and used as a tool to obtain real-time insights. However, despite this recent surge of interest, the CEP market is still dominated by solutions that are costly and inflexible or too low-level and hard to operate. To address these problems, this research proposes the creation of a CEP system that can be o↵ered as a service and used over the Internet. -

Concepts of Concurrent Programming
C U R R I C U L U M M O D U L E SEI-CM-24 Carnegie Mellon University Software Engineering Institute Concepts of Concurrent Programming . David W. Bustard University of Ulster April 1990 Approved for public release. Distribution unlimited. Preface A concurrent program is one defining actions that may be performed Capsule simultaneously. This module discusses the nature of such programs Description and provides an overview of the means by which they may be constructed and executed. Emphasis is given to the terminology used in this field and the underlying concepts involved. This module is largely concerned with explicit concurrency, where Scope concurrent behavior is specified by the program designer. Particular attention is paid to programs that can be considered inherently concurrent, that is, programs that are constructed to control or model physical systems that involve parallel activity. The module also includes a brief introduction to performance-oriented concurrency, where concurrency is used to improve program performance by taking advantage of hardware support for parallel processing. The module is divided into three sections. The first deals with basic concepts in concurrent programming, covering characteristic attributes, formal properties, standard design problems, and execution details. The second section discusses the steps in constructing concurrent programs from specification to coding. The final section briefly examines concurrency from the point of view of some common application areas. The module gives a foundation for a deeper study of specific topics in concurrent programming. It also provides the preparatory material for a study of the concurrent aspects of application areas such as real-time (embedded) systems, database systems, operating systems, and many simulation systems. -
So Many Performance Events, So Little Time
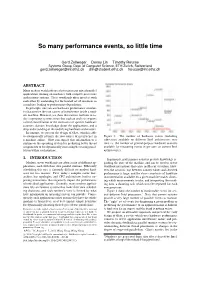
So many performance events, so little time Gerd Zellweger Denny Lin Timothy Roscoe Systems Group, Dept. of Computer Science, ETH Zurich, Switzerland [email protected] [email protected] [email protected] ABSTRACT Many modern workloads are a heterogeneous mix of parallel applications running on machines with complex processors and memory systems. These workloads often interfere with each other by contending for the limited set of resources in a machine, leading to performance degradation. In principle, one can use hardware performance counters to characterize the root causes of interference inside a mod- ern machine. However, we show that current facilities in to- day’s operating systems mean that such an analysis requires careful consideration of the intricacies of specific hardware counters, domain knowledge about the applications, and a deep understanding of the underlying hardware architecture. In contrast, we present the design of Glatt, which is able to automatically identify the root causes of interference in Figure 1: The number of hardware events (including a machine online. Glatt can expose this information to a subevents) available on different Intel architectures over runtime or the operating system for predicting better thread time vs. the number of general-purpose hardware counters assignments or for dynamically increasing/decreasing paral- available for measuring events (8 per core on current Intel lelism within each runtime. architectures). 1. INTRODUCTION In principle, performance counters provide knowledge re- Modern server workloads are often a mix of different ap- garding the state of the machine and can be used to detect plications, each with their own parallel runtime. -

Windows OS Event Correlation
TALLINN UNIVERSITY OF TECHNOLOGY Faculty of Information Technology Department of Computer Science TUT Centre for Digital Forensics and Cyber Security ITC70LT Mina Gerges - 114381IVCMM LOG MONITORING AND EVENT CORRELATION ON MICROSOFT® WINDOWS™ USING SIMPLE EVENT CORRELATOR Master thesis Supervisor: Risto Vaarandi Doctor of Philosophy Senior Researcher Tallinn 2016 TALLINNA TEHNIKAÜLIKOOL Infotehnoloogia teaduskond Arvutiteaduse instituut TTÜ Küberkriminalistika ja Küberjulgeoleku Keskus ITC70LT Mina Gerges - 114381IVCMM LOGIDE MONITOORING JA SÜNDMUSTE KORRELATSIOON MICROSOFT® WINDOWS™ PLATVORMIL SEC KORRELATSIOONIMOOTORI ABIL Magistritöö Juhendaja: Risto Vaarandi Filosoofiadoktor Vanemteadur Tallinn 2016 Declaration I hereby declare that I am the sole author of this thesis. All the used materials, references to the literature and the work of others have been referred to. This thesis has not been presented for examination anywhere else. Author: Mina Gerges ……………………………………. ……………………………… (Date) (Signature) 2 Abstract The aim of this thesis is providing a stable integration solution for Simple Event Correlator (SEC) Perl process to run on Microsoft Windows operating system as a service. The purpose of running SEC on Microsoft Windows is providing a reliable correlation engine to monitor event logs of the operating system and other software for critical alerts, malicious action, attack patterns and other anomalies, then to interact proactively. SEC is coded using Perl. However Microsoft does not provide a native Perl distribution for Windows. A third party Perl distribution from the available shall be selected, based on features and performance comparison. SEC is not capable of loading Microsoft Windows event logs without the aid of a log collection tool. Miscellaneous applications provide different log formats which require normalization to standardize parsing for extracting information from events. -

Monitoring the Behaviour of Distributed Systems
Monitoring the Behaviour of Distributed Systems Scarlet Schwiderski Selwyn College University of Cambridge Adissertationsubmittedforthedegreeof Doctor of Philosophy April 1996 Abstract Monitoring the behaviour of computing systems is an important task. In active database systems, a detected system behaviour leads to the triggering of an ECA (event-condition-action) rule. ECA rules are employed for supporting database man- agement system functions as well as external applications. Although distributed database systems are becoming more commonplace, active database research has to date focussed on centralised systems. In distributed debugging systems, a de- tected system behaviour is compared with the expected system behaviour. Differ- ences illustrate erroneous behaviour. In both application areas, system behaviours are specified in terms of events: primitive events represent elementary occurrences and composite events represent complex occurrence patterns. At system runtime, specified primitive and composite events are monitored and event occurrences are detected. However, in active database systems events are monitored in terms of physical time and in distributed debugging systems events are monitored in terms of logical time. The notion of physical time is difficult in distributed systems because of their special characteristics: no global time, network delays, etc. This dissertation is concerned with monitoring the behaviour of distributed sys- tems in terms of physical time, i.e. the syntax, the semantics, the detection, and the implementation of events are considered. The syntax of primitive and composite events is derived from the work of both active database systems and distributed debugging systems; differences and neces- sities are highlighted. The semantics of primitive and composite events establishes when and where an event occurs; the semantics depends largely on the notion of physical time in distributed systems. -

Cross-Core Event Monitoring for Processor Failure Prediction
Cross-Core Event Monitoring for Processor Failure Prediction Felix Salfner, Peter Tröger, and Steffen Tschirpke Humboldt University Berlin {salfner,troeger,tschirpke}@informatik.hu-berlin.de ABSTRACT With the ever-increasing number of transistors on these chips, hardware reliability is about to become a pressing A recent trend in the design of commodity processors is issue in the upcoming years. AMD already sells triple- the combination of multiple independent execution units core processors that were originally intended as quad-core on one chip. With the resulting increase of complexity and processors, but contain one disabled defective execution transistor count, it becomes more and more likely that a unit. This shows that new paradigms and approaches are single execution unit on a processor gets faulty. In order needed to ensure dependability of modern CMP-based to tackle this situation, we propose an architecture for computer systems. dependable process management in chip-multiprocessing machines. In our approach, execution units survey each One way to improve dependability (meaning performance other to anticipate future hardware failures. The and availability) at run-time in imperfect systems is the prediction relies on the analysis of processor hardware proactive failure management approach. In contrast to performance counters by a statistical rank-sum test. classical fault tolerance techniques, which typically react Initial experiments with the Intel Core processor platform after the problem has occurred, it relies on the short-term proved the feasibility of the approach, but also showed anticipation of upcoming failures. the need for further investigation due to a high prediction quality variation in most of the cases. -

Lares: an Architecture for Secure Active Monitoring Using Virtualization
Lares: An Architecture for Secure Active Monitoring Using Virtualization Bryan D. Payne Martim Carbone Monirul Sharif Wenke Lee School of Computer Science Georgia Institute of Technology Atlanta, Georgia 30332–0765 bdpayne,mcarbone,msharif,wenke @cc.gatech.edu { } Abstract ing a full-featured anti-virus, intrusion detection, or intru- sion prevention system. Previous efforts to implement these Host-based security tools such as anti-virus and intru- types of systems within a protected VM have resorted to im- sion detection systems are not adequately protected on to- plementing the systems with crippled functionality. What day’s computers. Malware is often designed to immedi- was missing in these systems was the ability to do active ately disable any security tools upon installation, render- monitoring. Active monitoring is when the security tool ing them useless. While current research has focused on places a hook inside the system being monitored. When moving these vulnerable security tools into an isolated vir- execution reaches the hook, it will interrupt execution and tual machine, this approach cripples security tools by pre- pass control to the security tool. Active monitoring can also venting them from doing active monitoring. This paper de- be done outside of the system being monitored (e.g., net- scribes an architecture that takes a hybrid approach, giving work and disk monitoring), however these monitors are re- security tools the ability to do active monitoring while still stricted to the semantic level provided by the disk and net- benefiting from the increased security of an isolated virtual work device abstractions. In this work, we focus on systems machine. -

Active Complex Event Processing Over Event Streams∗
Active Complex Event Processing over Event Streams∗ Di Wang Elke A. Rundensteiner Richard T. Ellison III Worcester Polytechnic Institute Worcester Polytechnic Institute UMass Medical School Worcester, MA, USA Worcester, MA, USA Worcester, MA, USA [email protected] [email protected] [email protected] ABSTRACT Motivating Application. Healthcare-associated infec- State-of-the-art Complex Event Processing technology (CEP), tions hit 1.7 million people a year in the United States, caus- while effective for pattern query execution, is limited in its ing an estimated 99,000 deaths [18]. The HyReminder sys- capability of reacting to opportunities and risks detected by tem is a hospital infection control system developed by WPI pattern queries. Especially reactions that affect the query and UMass Medical School to continuously track healthcare results in turn have not been addressed in the literature. workers (HCWs) for hygiene compliance (for example sani- We propose to tackle these unsolved problems by embed- tizing hands and wearing masks), and to remind HCWs to ding active rule support within the CEP engine, hence- perform hygiene precautions - thus preventing the spread of forth called Active CEP (ACEP). Active rules in ACEP al- infections [11]. As shown in Figure 1, every HCW wears low us to specify a pattern query's dynamic condition and a RFID badge which has a three-color light for indicating real-time actions. The technical challenge is to handle in- his (hygiene) status: \safe", \warning" or \violation". Pat- teractions between queries and reactions to queries in the tern queries continuously monitor each HCW's behaviors high-volume stream execution. -

On Synchronous and Asynchronous Monitor Instrumentation for Actor-Based Systems
On Synchronous and Asynchronous Monitor Instrumentation for Actor-based systems Ian Cassar∗ Adrian Francalanza Computer Science, ICT, University of Malta. Computer Science, ICT, University of Malta. [email protected] [email protected] We study the impact of synchronous and asynchronous monitoring instrumentation on runtime over- heads in the context of a runtime verification framework for actor-based systems. We show that, in such a context, asynchronous monitoring incurs substantially lower overhead costs. We also show how, for certain properties that require synchronous monitoring, a hybrid approach can be used that ensures timely violation detections for the important events while, at the same time, incurring lower overhead costs that are closer to those of an asynchronous instrumentation. 1 Introduction Formally ensuring the correctness of component-based, concurrent systems is an arduous task, mainly because exhaustive methods such as model-checking quickly run into state-explosion problems; this is typically caused by the multiple thread interleavings of the system being analysed, and the range of data the system can input and react to. Runtime Verification (RV) [33] is an appealing compromise towards ensuring correctness, as it circumvents such scalability issues by verifying only the current system execu- tion. Runtime Enforcement (RE) [21] builds on RV by automating recovery procedures once a violation is detected so as to mitigate or rectify the effects of the violation. Together, these runtime techniques can be used as a disciplined methodology for augmenting systems with self-adaptation functionality. Most RV and RE frameworks work by synthesising monitors from properties specified in terms of a formal language, and then execute these monitors in tandem with the system.