DISI - University of Trento
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Security Master Symbol Description a AGILENT TECHNOLOGIES INC AA
*The information contained herein is believed to Security Master be reliable but is neither guaranteed by EQIS Capital Management, Inc. its principles nor any affiliated EQIS companies. This information is Symbol Description intended for the exclusive use of investment Adviser Representative. This list is subject to A AGILENT TECHNOLOGIES INC change. AA ALCOA CORP COM Advisor Services are offered through EQIS AAAAX DEUTSCHE ALTERNATIVE ASSET ALLOCATION FU Capital Management, Inc. an SEC Registered AAAP ADVANCED ACCELERATOR APPLIC SPONSORED AD Investment Adviser. For information purposes AAASX DEUTSCHE ALTERNATIVE ASSET ALLOCATION F only, not for public distribution. AABPX AMERICAN BEACON BALANCED INVESTOR AAC AAC HLDGS INC COM AACFX AIM CHINA A AADAX AIM GROWTH ALLOCATION CLASS A AADEX AMERICAN BEACON LARGE CAP VALUE INSTL AADR ADVISORSHARES WCM/BNY MLNFCSD GR ADR ETF AAGIY AIA GROUP LTD SPONS ADR AAGPX AMERICAN BEACON LARGE CAP VALUE INVESTOR AAIFX CROW POINT ALTERNATIVE INCOME FUND AAIPX AMERICAN BEACON INTERNATIONAL EQUITY INV AAL AMERICAN AIRLS GROUP INC COM AAMC ALTISOURCE ASSET MGMT CORP COM AAME ATLANTIC AMERN CORP AAN AARONS, INC. CL A AAOI APPLIED OPTOELECTRONICS INC COM AAON AAON INC PAR $0.004 AAP ADVANCED AUTO PARTS INC AAPC ATLANTIC ALLIANCE PARTNER CORP SHS AAPL APPLE INC COM AAT AMERICAN ASSETS TR INC COM AAU ALMADEN MINERALS LTD AAV ADVANTAGE OIL & GAS LTD AAWW ATLAS AIR WORLDWIDE HLDGS INC COM NEW AAXJ ISHARES MSCI ALL COUNTRY ASIA EX JAPAN I AB ALLIANCEBERNSTEIN HOLDING LP UNIT LTD PA ABAC AOXIN TIANLI GROUP INC NEW -

2019 Stateof the Software Supply Chain
2019 State of the Software Supply Chain The 5th annual report on global open source software development presented by in partnership with supported by Table of Contents Introduction................................................................................. 3 CHAPTER 4: Exemplary Dev Teams .................................26 4.1 The Enterprise Continues to Accelerate ...........................27 Infographic .................................................................................. 4 4.2 Analysis of 12,000 Large Enterprises ................................27 CHAPTER 1: Global Supply of Open Source .................5 4.3 Component Releases Make Up 85% of a Modern Application......................................... 28 1.1 Supply of Open Source is Massive ...........................................6 4.4 Characteristics of Exemplary 1.2 Supply of Open Source is Expanding Rapidly ..................7 Development Teams ................................................................... 29 1.3 Suppliers, Components and Releases ..................................7 4.5 Rewards for Exemplary Development Teams ..............34 CHAPTER 2: Global Demand for Open Source ..........8 CHAPTER 5: The Changing Landscape .......................35 2.1 Accelerating Demand for 5.1 Deming Emphasizes Building Quality In ...........................36 Open Source Libraries .....................................................................9 5.2 Tracing Vulnerable Component Release 2.2 Automated Pipelines and Downloads Across Software Supply Chains -

The TYPO3 Neos 1.0 Compendium
2014-04-26 TYPO3 Neos 1.0.2 The Compendium translated into english LOBACHER . Patrick Lobacher Roland Schenke Head of Web Development TYPO3 Neos - the Compendium Feedback LOBACHER. Feedback requested ! • Dear Neos Enthusiast! I try to keep the TYPO3 Neos Compendium on an up-to-date Level. To achieve this I need your Input! If you have ideas regarding Code Examples, FAQ Entries or just want to praise or criticize please do not hesitate to contact me at the following address: patrick [AT] lobacher.de Have fun with the Compendium! Patrick Lobacher & Roland Schenke (c) 2014 - Patrick Lobacher | TYPO3 Neos 1.0.2 - the Compendium | 2014-03-07 | www.lobacher.de 2 TYPO3 Neos - the Compendium Changelog LOBACHER. Changelog Date Changes 2013-08-08 Initial Version / Thanks to Christian Schwerdt for domainFACTORY specific Input 2013-08-09 included proof corrections by Roland Schenke and Michael Oehlhof - Thanks! 2013-08-10 added Nginx-Config - Thanks to Christian Kuhn, Christian Müller and Anja Leichsenring 2013-08-10 added Troubleshoot Section 2013-08-18 included proof corrections by Roland Schenke - Thanks! 2013-08-18 translated from german into english by Roland Schenke - Thanks a lot! 2013-12-12 updated to TYPO3 Neos 1.0 final 2013-12-15 updated to TYPO3 Neos 1.0.1 2014-01-07 Link for the installation under Shared Hosting and proof corrections (Thanks to Christian Glass!) 2014-03-03 migrated to „LOBACHER.“ CI 2014-03-05 updated to TYPO3 Neos 1.0.2 2014-03-07 added installation on a all-inkl.com Server. Thanks to Mario Janetzko! (c) 2014 - Patrick Lobacher | TYPO3 Neos 1.0.2 - the Compendium | 2014-03-07 | www.lobacher.de 3 TYPO3 Neos - the Compendium Changelog LOBACHER. -

Challenges and Limits of an Open Source Approach to Artificial Intelligence
STUDY Requested by the AIDA committee Challenges and limits of an open source approach to Artificial Intelligence Policy Department for Economic, Scientific and Quality of Life Policies Directorate-General for Internal Policies Authors: Alexandra THEBEN, Laura GUNDERSON, Laura LÓPEZ-FORÉS, Gianluca MISURACA and Francisco LUPIÁÑEZ-VILLANUEVA. EN PE 662.908 - May 2021 Challenges and limits of an open source approach to Artificial Intelligence Abstract Coupled with the numerous opportunities emerging from the use of artificial intelligence (AI), open source comes with the potential for innovation capacity in both the public and private sector. Advantages include the ability to enhance transparency, facilitate the auditing of AI and thereby enhance citizen trust, while stimulating economic activities and domain-specific expertise. Disadvantages and limits include legal, technical, data, risk management, societal and ethical challenges. This analysis examines all main open source artificial intelligence pro and cons and proposes seven recommendations to boost its uptake. This document was provided by the Policy Department for Economic, Scientific and Quality of Life Policies at the request of the Special Committee on Artificial Intelligence in a Digital Age (AIDA). This document was requested by the European Parliament's Special Committee on Artificial Intelligence in a Digital Age (AIDA). AUTHORS Alexandra THEBEN, Open Evidence Laura GUNDERSON, Open Evidence Laura LÓPEZ-FORÉS, Open Evidence Gianluca MISURACA, Politecnico di Milano Francisco LUPIÁÑEZ-VILLANUEVA, Open Evidence ADMINISTRATORS RESPONSIBLE Matteo CIUCCI Frédéric GOUARDÈRES EDITORIAL ASSISTANT Catherine NAAS LINGUISTIC VERSIONS Original: EN ABOUT THE EDITOR Policy departments provide in-house and external expertise to support EP committees and other parliamentary bodies in shaping legislation and exercising democratic scrutiny over EU internal policies. -

H:\My Documents\Article.Wpd
Vehicle Data Codes as of 1/26/2010 Press CTRL + F to prompt the search field. VEHICLE DATA CODES TABLE OF CONTENTS 1--LICENSE PLATE TYPE (LIT) FIELD CODES 1.1 LIT FIELD CODES FOR REGULAR PASSENGER AUTOMOBILE PLATES 1.2 LIT FIELD CODES FOR AIRCRAFT 1.3 LIT FIELD CODES FOR ALL-TERRAIN VEHICLES AND SNOWMOBILES 1.4 SPECIAL LICENSE PLATES 1.5 LIT FIELD CODES FOR SPECIAL LICENSE PLATES 2--VEHICLE MAKE (VMA) AND BRAND NAME (BRA) FIELD CODES 2.1 VMA AND BRA FIELD CODES 2.2 VMA, BRA, AND VMO FIELD CODES FOR AUTOMOBILES, LIGHT-DUTY VANS, LIGHT- DUTY TRUCKS, AND PARTS 2.3 VMA AND BRA FIELD CODES FOR CONSTRUCTION EQUIPMENT AND CONSTRUCTION EQUIPMENT PARTS 2.4 VMA AND BRA FIELD CODES FOR FARM AND GARDEN EQUIPMENT AND FARM EQUIPMENT PARTS 2.5 VMA AND BRA FIELD CODES FOR MOTORCYCLES AND MOTORCYCLE PARTS 2.6 VMA AND BRA FIELD CODES FOR SNOWMOBILES AND SNOWMOBILE PARTS 2.7 VMA AND BRA FIELD CODES FOR TRAILERS AND TRAILER PARTS 2.8 VMA AND BRA FIELD CODES FOR TRUCKS AND TRUCK PARTS 2.9 VMA AND BRA FIELD CODES ALPHABETICALLY BY CODE 3--VEHICLE MODEL (VMO) FIELD CODES 3.1 VMO FIELD CODES FOR AUTOMOBILES, LIGHT-DUTY VANS, AND LIGHT-DUTY TRUCKS 3.2 VMO FIELD CODES FOR ASSEMBLED VEHICLES 3.3 VMO FIELD CODES FOR AIRCRAFT 3.4 VMO FIELD CODES FOR ALL-TERRAIN VEHICLES 3.5 VMO FIELD CODES FOR CONSTRUCTION EQUIPMENT 3.6 VMO FIELD CODES FOR DUNE BUGGIES 3.7 VMO FIELD CODES FOR FARM AND GARDEN EQUIPMENT 3.8 VMO FIELD CODES FOR GO-CARTS 3.9 VMO FIELD CODES FOR GOLF CARTS 3.10 VMO FIELD CODES FOR MOTORIZED RIDE-ON TOYS 3.11 VMO FIELD CODES FOR MOTORIZED WHEELCHAIRS 3.12 -

Neos CMS Documentation Release 2.3.3
Neos CMS Documentation Release 2.3.3 The Neos Team Jun 16, 2019 Contents 1 Getting Started 3 1.1 Feature List..............................................3 1.2 Installation..............................................5 2 Technical Principles 11 3 User Guide 13 3.1 User Interface Basics......................................... 13 3.2 Workspaces.............................................. 15 4 Creating a Site with Neos 17 4.1 Node Types.............................................. 17 4.2 TypoScript.............................................. 30 4.3 Rendering Custom Markup..................................... 42 4.4 Content Dimensions......................................... 70 4.5 Multi Site Support.......................................... 74 4.6 Content Cache............................................ 74 4.7 Permissions & Access Management................................. 80 5 Extending Neos 89 5.1 Creating a plugin........................................... 89 5.2 Custom Backend Modules...................................... 94 5.3 Custom Edit/Preview-Modes..................................... 95 5.4 Custom Editors............................................ 96 5.5 Custom Eel Helper.......................................... 97 5.6 Custom FlowQuery Operations................................... 98 5.7 Custom TypoScript Objects..................................... 100 5.8 Custom Validators.......................................... 101 5.9 Custom ViewHelpers......................................... 101 5.10 Customizing the Inspector..................................... -

Towards Left Duff S Mdbg Holt Winters Gai Incl Tax Drupal Fapi Icici
jimportneoneo_clienterrorentitynotfoundrelatedtonoeneo_j_sdn neo_j_traversalcyperneo_jclientpy_neo_neo_jneo_jphpgraphesrelsjshelltraverserwritebatchtransactioneventhandlerbatchinsertereverymangraphenedbgraphdatabaseserviceneo_j_communityjconfigurationjserverstartnodenotintransactionexceptionrest_graphdbneographytransactionfailureexceptionrelationshipentityneo_j_ogmsdnwrappingneoserverbootstrappergraphrepositoryneo_j_graphdbnodeentityembeddedgraphdatabaseneo_jtemplate neo_j_spatialcypher_neo_jneo_j_cyphercypher_querynoe_jcypherneo_jrestclientpy_neoallshortestpathscypher_querieslinkuriousneoclipseexecutionresultbatch_importerwebadmingraphdatabasetimetreegraphawarerelatedtoviacypherqueryrecorelationshiptypespringrestgraphdatabaseflockdbneomodelneo_j_rbshortpathpersistable withindistancegraphdbneo_jneo_j_webadminmiddle_ground_betweenanormcypher materialised handaling hinted finds_nothingbulbsbulbflowrexprorexster cayleygremlintitandborient_dbaurelius tinkerpoptitan_cassandratitan_graph_dbtitan_graphorientdbtitan rexter enough_ram arangotinkerpop_gremlinpyorientlinkset arangodb_graphfoxxodocumentarangodborientjssails_orientdborientgraphexectedbaasbox spark_javarddrddsunpersist asigned aql fetchplanoriento bsonobjectpyspark_rddrddmatrixfactorizationmodelresultiterablemlibpushdownlineage transforamtionspark_rddpairrddreducebykeymappartitionstakeorderedrowmatrixpair_rddblockmanagerlinearregressionwithsgddstreamsencouter fieldtypes spark_dataframejavarddgroupbykeyorg_apache_spark_rddlabeledpointdatabricksaggregatebykeyjavasparkcontextsaveastextfilejavapairdstreamcombinebykeysparkcontext_textfilejavadstreammappartitionswithindexupdatestatebykeyreducebykeyandwindowrepartitioning -

A Periodic Table of the Elements at Los Alamos National Laboratory Los Alamos National Laboratory's Chemistry Division Presents Periodic Table of the Elements
A Periodic Table of the Elements at Los Alamos National Laboratory Los Alamos National Laboratory's Chemistry Division Presents Periodic Table of the Elements A Resource for Elementary, Middle School, and High School Students Click an element for more information: Group** Period 1 18 IA VIIIA 1A 8A 1 2 13 14 15 16 17 2 1 H IIA IIIA IVA VA VIA VIIA He 1.008 2A 3A 4A 5A 6A 7A 4.003 3 4 5 6 7 8 9 10 2 Li Be B C N O F Ne 6.941 9.012 10.81 12.01 14.0116.00 19.00 20.18 11 12 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 3 Na Mg IIIB IVB VB VIB VIIB------- VIII ------ IB IIB Al Si P S Cl Ar 22.99 24.31 3B 4B 5B 6B 7B - 1B 2B 26.98 28.09 30.9732.07 35.45 39.95 ------- 8 ------- 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 4 K Ca Sc Ti V Cr Mn Fe Co Ni Cu Zn Ga Ge As Se Br Kr 39.10 40.08 44.96 47.8850.94 52.00 54.94 55.85 58.47 58.6963.5565.39 69.72 72.59 74.9278.96 79.90 83.80 37 38 39 40 41 42 43 44 45 46 47 48 49 50 51 52 53 54 5 Rb Sr Y Zr NbMo Tc Ru Rh Pd AgCd In Sn Sb Te I Xe 85.47 87.62 88.91 91.2292.91 95.94 (98) 101.1 102.9 106.4107.9112.4 114.8 118.7 121.8127.6 126.9 131.3 55 56 57 72 73 74 75 76 77 78 79 80 81 82 83 84 85 86 6 Cs Ba La* Hf Ta W Re Os Ir Pt AuHg Tl Pb Bi Po At Rn 132.9 137.3 138.9 178.5180.9 183.9 186.2 190.2 190.2 195.1197.0200.5 204.4 207.2 209.0 (210) (210) (222) 87 88 89 104 105 106 107 108 109 110 111 112 114 116 118 7 Fr Ra Ac~ Rf Db Sg Bh Hs Mt --- --- --- --- --- --- (223) (226) (227) (257) (260) (263) (262) (265) (266) () () () () () () http://periodic.lanl.gov/default.htm (1 of 3) [10/24/2001 5:40:02 PM] A Periodic Table of the Elements at Los Alamos National Laboratory 58 59 60 61 62 63 64 65 66 67 68 69 70 71 Lanthanide Series* Ce Pr NdPmSm Eu Gd Tb DyHo Er Tm Yb Lu 140.1 140.9144.2 (147) 150.4 152.0 157.3 158.9162.5164.9 167.3 168.9 173.0175.0 90 91 92 93 94 95 96 97 98 99 100 101 102 103 Actinide Series~ Th Pa U Np Pu AmCmBk Cf Es FmMdNo Lr 232.0 (231) (238) (237) (242) (243) (247) (247) (249) (254) (253) (256) (254) (257) ** Groups are noted by 3 notation conventions. -
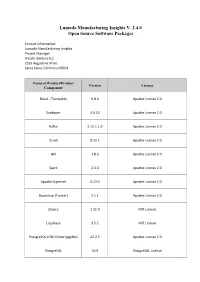
Lumada Manufacturing Insights V. 2.4.0 Open Source Software Packages
Lumada Manufacturing Insights V. 2.4.0 Open Source Software Packages Contact Information: Lumada Manufacturing Insights Project Manager Hitachi Vantara LLC 2535 Augustine Drive Santa Clara, California 95054 Name of Product/Product Version License Component Druid - Tranquility 0.8.0 Apache License 2.0 Zookeper 3.4.10 Apache License 2.0 Kafka 2.11-1.1.0 Apache License 2.0 Druid 0.12.1 Apache License 2.0 Nifi 1.8.0 Apache License 2.0 Spark 2.3.0 Apache License 2.0 Apache Superset 0.23.0 Apache License 2.0 Bootstrap (Twitter) 3.1.1 Apache License 2.0 jQuery 1.11.0 MIT License LiquiBase 3.5.2 MIT License PostgreSQL JDBC Driver (pgjdbc) 42.2.5 Apache License 2.0 PostgreSQL 10.9 PostgreSQL License Name of Product/Product Version License Component Mosquitto 1.4.15 EPL/EDL licensed https://raw.githubusercontent.com/nodejs/node NodeJS 9.11.2 /master/LICENSE https://www.npmjs.com/policies/open-source- NPM 5.6.0 terms Yarn 1.17.3 BSD License Yui 2.8.2r1 BSD License Java OpenJDK 1.8 GPL v2 1.5.10. Spring Boot Tomcat Starter Apache License, Version 2.0 RELEASE @babel/code-frame 7.0.0-beta.44 The MIT License @babel/code-frame 7.0.0-beta.51 The MIT License @babel/generator 7.0.0-beta.44 The MIT License @babel/generator 7.0.0-beta.51 The MIT License @babel/helper-function-name 7.0.0-beta.44 The MIT License @babel/helper-function-name 7.0.0-beta.51 The MIT License @babel/helper-get-function-arity 7.0.0-beta.44 The MIT License @babel/helper-get-function-arity 7.0.0-beta.51 The MIT License Name of Product/Product Version License Component @babel/helper-module-imports -

EXO User Manual ADVANCED WATER QUALITY MONITORING PLATFORM TM
USER MANUAL ITEM# 603789REF REVISION K EXO User Manual ADVANCED WATER QUALITY MONITORING PLATFORM TM The information contained in this manual is subject to change without notice. Effort has been made to make the information in this manual complete, accurate, and current. The manufacturer shall not be held responsible for errors or omissions in this manual. Consult YSI.com/EXO for the most up-to-date version of this manual. THIS IS AN INTERACTIVE DOCUMENT When viewing this document as an AdobeTM PDF, hovering your cursor over certain phrases will bring up the finger-point icon. Clicking elements of the Table of Contents, website URLs, or references to certain sections will take you automatically to those locations. Product Components Carefully unpack the instrument and accessories and inspect for damage. If any parts or materials are damaged, contact YSI Customer Service at 800-897-4151 (+1 937 767-7241) or the authorized YSI distributor from whom the instrument was purchased. Technical Support Telephone: 800 897 4151 (USA), +1 937 767 7241 (Globally) Monday through Friday, 8:00 AM to 5:00 ET Fax: +1 937 767 9353 (orders) Email: [email protected] YSI.com Safety Information Please read this entire manual before unpacking, setting up or operating this equipment. Pay attention to all precautionary statements. Failure to do so could result in serious injury to the operator or damage to the equipment. Make sure that the protection provided by this equipment is not impaired. Do not use or install this equipment in any manner other than that specified in this manual. -

ON the DESIGN, SYNTHESIS, and RADIATION EFFECT PREVENTION of a 6U DEEP SPACE CUBESAT by Michael Cullen Halvorson a Thesis Submi
ON THE DESIGN, SYNTHESIS, AND RADIATION EFFECT PREVENTION OF A 6U DEEP SPACE CUBESAT by Michael Cullen Halvorson A thesis submitted to the Graduate Faculty of Auburn University in partial fulfillment of the requirements for the Degree of Master of Science Auburn, AL December 12, 2020 Keywords: Deep Space CubeSat, Orbit Thermal Modeling, Electric Propulsion Optimization, Radiation Tolerance Copyright 2020 by Michael Cullen Halvorson Approved by Dr. David G. Beale, Chair, Professor of Mechanical Engineering Dr. Daniel K. Harris, Associate Professor of Mechanical Engineering Dr. Thaddeus H. Roppel, Associate Professor of Electrical Engineering Dr. Michael Fogle Jr., Associate Professor of Physics Except where reference is made to the work of others, the work described in this thesis is my own or was done in collaboration of my advisory committee. This thesis does not include proprietary or classified information except where permission was given. _________________________________________________ Michael Cullen Halvorson Certificate of Approval: _________________________________ David G. Beale, Chair Professor Mechanical Engineering _________________________________ ________________________________ Thaddeus H. Roppel Daniel K. Harris Associate Professor Associate Professor Electrical Engineering Mechanical Engineering _________________________________ _________________________________ Michael Fogle Jr Jeffrey Suhling Associate Professor Department Chair Physics Mechanical Engineering ii Permission is granted to Auburn University to make copies of this thesis at its discretion, upon request of individuals or institutions and at their expense. The author reserves all publication rights. _____________________________ Signature of Author _____________________________ Date iii VITA Michael Halvorson is an Aeromechanical Engineer from Montgomery, AL. His mother, Melanie, is an internal medicine nephrologist, and his father, David, is an otolaryngological surgeon. With five generations of medical doctors in his immediate ancestry, academia was always the plan. -

Neos CMS Documentation Release 4.2.X-Dev
Neos CMS Documentation Release 4.2.x-dev The Neos Team Dec 02, 2020 Contents 1 Getting Started 3 1.1 Installation..............................................3 2 Technical Principles 9 3 Creating a Site with Neos 11 3.1 Node Types.............................................. 11 3.2 Fusion................................................ 28 3.3 Rendering Custom Markup..................................... 42 3.4 Content Dimensions......................................... 72 3.5 Multi Site Support.......................................... 76 3.6 Content Cache............................................ 77 3.7 Permissions & Access Management................................. 83 4 Extending Neos 95 4.1 Creating a plugin........................................... 95 4.2 Custom Backend Modules...................................... 100 4.3 Custom Edit/Preview-Modes..................................... 101 4.4 Custom Editors............................................ 103 4.5 Custom Eel Helper.......................................... 105 4.6 Custom FlowQuery Operations................................... 106 4.7 Custom Fusion Objects........................................ 108 4.8 Custom Validators.......................................... 109 4.9 Custom ViewHelpers......................................... 109 4.10 Customizing the Inspector...................................... 112 4.11 Data sources............................................. 115 4.12 Interaction with the Neos backend.................................. 116 4.13 Rendering special