Alt-Coin Traceability
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Auditing Wallets in Cryptonote
Auditing wallets in CryptoNote sowle <[email protected]> Zano project, https://zano.org Cryptocurrency wallet auditing is the ability for a third party (the "auditor") to watch the transactions and to be able to calculate the correct balance without an ability to spend a coin. This article explores several possible implementations of expansion cryptocurrency protocol CryptoNote 2.0 [1] with such ability. In the original CryptoNote protocol auditing is only partially possible with the help of the tracking key, namely, an auditor is able to distinguish incoming transactions in the blockchain, but the full set of secret keys is required to filter out outgoing transactions. This article is intended for readers familiar with the general blockchain technology and “classic” cryptocurrencies, as well as with the basics of cryptography on elliptic curves. 1. Introduction What is CryptoNote? Surprisingly, most people interested in blockchain technology have never heard anything about CryptoNote, in spite of the fact that the technology has more than 300 forks, including Monero as the most famous. Back in 2014 in the cryptocurrency community there were mentions [2] about a project, titled Bytecoin. That project did not originate as a Bitcoin or other known project fork, having its own original codebase. It was very unusual at the time. Bytecoin general conception was to be an implementation of a privacy-technology named CryptoNote. There were two main privacy mechanisms: stealth-addresses and inputs` mixing-in with the help of ring signatures (at the time it was called "blockchain mixer"). Since Zcash existed only on paper / in theory at that time, CryptoNote became a competitive technology and has provoked much controversy in the cryptocurrency community. -

On the Relationship of Cryptocurrency Price with US Stock and Gold Price Using Copula Models
mathematics Article On the Relationship of Cryptocurrency Price with US Stock and Gold Price Using Copula Models Jong-Min Kim 1 , Seong-Tae Kim 2 and Sangjin Kim 3,* 1 Statistics Discipline, University of Minnesota at Morris, Morris, MN 56267, USA; [email protected] 2 Department of Mathematics, North Carolina A&T State University, Greensboro, NC 27411, USA; [email protected] 3 Department of Management and Information Systems, Dong-A University, Busan 49236, Korea * Correspondence: [email protected] Received: 15 September 2020; Accepted: 20 October 2020; Published: 23 October 2020 Abstract: This paper examines the relationship of the leading financial assets, Bitcoin, Gold, and S&P 500 with GARCH-Dynamic Conditional Correlation (DCC), Nonlinear Asymmetric GARCH DCC (NA-DCC), Gaussian copula-based GARCH-DCC (GC-DCC), and Gaussian copula-based Nonlinear Asymmetric-DCC (GCNA-DCC). Under the high volatility financial situation such as the COVID-19 pandemic occurrence, there exist a computation difficulty to use the traditional DCC method to the selected cryptocurrencies. To solve this limitation, GC-DCC and GCNA-DCC are applied to investigate the time-varying relationship among Bitcoin, Gold, and S&P 500. In terms of log-likelihood, we show that GC-DCC and GCNA-DCC are better models than DCC and NA-DCC to show relationship of Bitcoin with Gold and S&P 500. We also consider the relationships among time-varying conditional correlation with Bitcoin volatility, and S&P 500 volatility by a Gaussian Copula Marginal Regression (GCMR) model. The empirical findings show that S&P 500 and Gold price are statistically significant to Bitcoin in terms of log-return and volatility. -

Vulnerability of Blockchain Technologies to Quantum Attacks
Vulnerability of Blockchain Technologies to Quantum Attacks Joseph J. Kearneya, Carlos A. Perez-Delgado a,∗ aSchool of Computing, University of Kent, Canterbury, Kent CT2 7NF United Kingdom Abstract Quantum computation represents a threat to many cryptographic protocols in operation today. It has been estimated that by 2035, there will exist a quantum computer capable of breaking the vital cryptographic scheme RSA2048. Blockchain technologies rely on cryptographic protocols for many of their essential sub- routines. Some of these protocols, but not all, are open to quantum attacks. Here we analyze the major blockchain-based cryptocurrencies deployed today—including Bitcoin, Ethereum, Litecoin and ZCash, and determine their risk exposure to quantum attacks. We finish with a comparative analysis of the studied cryptocurrencies and their underlying blockchain technologies and their relative levels of vulnerability to quantum attacks. Introduction exist to allow the legitimate owner to recover this account. Blockchain systems are unlike other cryptosys- tems in that they are not just meant to protect an By contrast, in a blockchain system, there is no information asset. A blockchain is a ledger, and as central authority to manage users’ access keys. The such it is the asset. owner of a resource is by definition the one hold- A blockchain is secured through the use of cryp- ing the private encryption keys. There are no of- tographic techniques. Notably, asymmetric encryp- fline backups. The blockchain, an always online tion schemes such as RSA or Elliptic Curve (EC) cryptographic system, is considered the resource— cryptography are used to generate private/public or at least the authoritative description of it. -
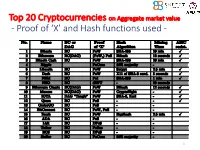
Proof of 'X' and Hash Functions Used
Top 20 Cryptocurrencies on Aggregate market value - Proof of ‘X’ and Hash functions used - 1 ISI Kolkata BlockChain Workshop, Nov 30th, 2017 CRYPTOGRAPHY with BlockChain - Hash Functions, Signatures and Anonymization - Hiroaki ANADA*1, Kouichi SAKURAI*2 *1: University of Nagasaki, *2: Kyushu University Acknowledgements: This work is supported by: Grants-in-Aid for Scientific Research of Japan Society for the Promotion of Science; Research Project Number: JP15H02711 Top 20 Cryptocurrencies on Aggregate market value - Proof of ‘X’ and Hash functions used - 3 Table of Contents 1. Cryptographic Primitives in Blockchains 2. Hash Functions a. Roles b. Various Hash functions used for Proof of ‘X’ 3. Signatures a. Standard Signatures (ECDSA) b. Ring Signatures c. One-Time Signatures (Winternitz) 4. Anonymization Techniques a. Mixing (CoinJoin) b. Zero-Knowledge proofs (zk-SNARK) 5. Conclusion 4 Brief History of Proof of ‘X’ 1992: “Pricing via Processing or Combatting Junk Mail” Dwork, C. and Naor, M., CRYPTO ’92 Pricing Functions 2003: “Moderately Hard Functions: From Complexity to Spam Fighting” Naor, M., Foundations of Soft. Tech. and Theoretical Comp. Sci. 2008: “Bitcoin: A peer-to-peer electronic cash system” Nakamoto, S. Proof of Work 5 Brief History of Proof of ‘X’ 2008: “Bitcoin: A peer-to-peer electronic cash system” Nakamoto, S. Proof of Work 2012: “Peercoin” Proof of Stake (& Proof of Work) ~ : Delegated Proof of Stake, Proof of Storage, Proof of Importance, Proof of Reserves, Proof of Consensus, ... 6 Proofs of ‘X’ 1. Proof of Work 2. Proof of Stake Hash-based Proof of ‘X’ 3. Delegated Proof of Stake 4. Proof of Importance 5. -

Hybrid Public/Anonymous Transactions on Monero, Cryptonote X-Cash
Hybrid public/anonymous transactions on Monero, Cryptonote X-Cash Zach Hildreth October 7, 2019 Abstract This yellow paper details the technical concepts and implementation of hybrid transactions (also known as FlexPrivacy c ), a feature enabling public and private transactions on the X- Cash public blockchain. In the first part, the paper aims at detailing how the hybrid transactions operate from a user’s perspective with some real-world use cases. A parallel is made between the digital money system and the economic behaviors associated with the current FIAT system. Secondly, a deeper understanding of the technology is given, explaining the implication on a blockchain perspective, as well as the edge cases and their approaches. Lastly, the last part consists in an in-depth approach of the mathematical concepts and technical implementation of the hybrid transaction in the X-Cash blockchain. Contents 1 Public transactions in the ringCT 4 2 Privacy in the inputs 4 3 A brief understanding of cryptonote transactions 4 4 Creation of a public address 6 5 How stealth addresses/outputs are decoded 6 6 How public transactions are created 7 1 Summary of the public transaction feature The hybrid transaction feature allows users to send and receive public or private transactions on the X-Network Blockchain X-Cash, which is based on the CryptoNote protocol. This feature is implemented on a per transaction basis where users can directly switch the privacy type by choosing the setting before attempting to send a transaction. In a public transaction, the following additional information is made public: • Sender’s address • Receiver’s address • Amount sent • Change amount sent back to the sender’s address However, the public transaction does not compromise the sender’s or receiver’s wallet full bal- ances nor the real mixin (number of signatures in the ring signature that authorizes the transaction) that provided the X-Cash balance. -

Coinbase Explores Crypto ETF (9/6) Coinbase Spoke to Asset Manager Blackrock About Creating a Crypto ETF, Business Insider Reports
Crypto Week in Review (9/1-9/7) Goldman Sachs CFO Denies Crypto Strategy Shift (9/6) GS CFO Marty Chavez addressed claims from an unsubstantiated report earlier this week that the firm may be delaying previous plans to open a crypto trading desk, calling the report “fake news”. Coinbase Explores Crypto ETF (9/6) Coinbase spoke to asset manager BlackRock about creating a crypto ETF, Business Insider reports. While the current status of the discussions is unclear, BlackRock is said to have “no interest in being a crypto fund issuer,” and SEC approval in the near term remains uncertain. Looking ahead, the Wednesday confirmation of Trump nominee Elad Roisman has the potential to tip the scales towards a more favorable cryptoasset approach. Twitter CEO Comments on Blockchain (9/5) Twitter CEO Jack Dorsey, speaking in a congressional hearing, indicated that blockchain technology could prove useful for “distributed trust and distributed enforcement.” The platform, given its struggles with how best to address fraud, harassment, and other misuse, could be a prime testing ground for decentralized identity solutions. Ripio Facilitates Peer-to-Peer Loans (9/5) Ripio began to facilitate blockchain powered peer-to-peer loans, available to wallet users in Argentina, Mexico, and Brazil. The loans, which utilize the Ripple Credit Network (RCN) token, are funded in RCN and dispensed to users in fiat through a network of local partners. Since all details of the loan and payments are recorded on the Ethereum blockchain, the solution could contribute to wider access to credit for the unbanked. IBM’s Payment Protocol Out of Beta (9/4) Blockchain World Wire, a global blockchain based payments network by IBM, is out of beta, CoinDesk reports. -

A Survey on Volatility Fluctuations in the Decentralized Cryptocurrency Financial Assets
Journal of Risk and Financial Management Review A Survey on Volatility Fluctuations in the Decentralized Cryptocurrency Financial Assets Nikolaos A. Kyriazis Department of Economics, University of Thessaly, 38333 Volos, Greece; [email protected] Abstract: This study is an integrated survey of GARCH methodologies applications on 67 empirical papers that focus on cryptocurrencies. More sophisticated GARCH models are found to better explain the fluctuations in the volatility of cryptocurrencies. The main characteristics and the optimal approaches for modeling returns and volatility of cryptocurrencies are under scrutiny. Moreover, emphasis is placed on interconnectedness and hedging and/or diversifying abilities, measurement of profit-making and risk, efficiency and herding behavior. This leads to fruitful results and sheds light on a broad spectrum of aspects. In-depth analysis is provided of the speculative character of digital currencies and the possibility of improvement of the risk–return trade-off in investors’ portfolios. Overall, it is found that the inclusion of Bitcoin in portfolios with conventional assets could significantly improve the risk–return trade-off of investors’ decisions. Results on whether Bitcoin resembles gold are split. The same is true about whether Bitcoins volatility presents larger reactions to positive or negative shocks. Cryptocurrency markets are found not to be efficient. This study provides a roadmap for researchers and investors as well as authorities. Keywords: decentralized cryptocurrency; Bitcoin; survey; volatility modelling Citation: Kyriazis, Nikolaos A. 2021. A Survey on Volatility Fluctuations in the Decentralized Cryptocurrency Financial Assets. Journal of Risk and 1. Introduction Financial Management 14: 293. The continuing evolution of cryptocurrency markets and exchanges during the last few https://doi.org/10.3390/jrfm years has aroused sparkling interest amid academic researchers, monetary policymakers, 14070293 regulators, investors and the financial press. -

Impossibility of Full Decentralization in Permissionless Blockchains
Impossibility of Full Decentralization in Permissionless Blockchains Yujin Kwon*, Jian Liuy, Minjeong Kim*, Dawn Songy, Yongdae Kim* *KAIST {dbwls8724,mjkim9394,yongdaek}@kaist.ac.kr yUC Berkeley [email protected],[email protected] ABSTRACT between achieving good decentralization in the consensus protocol Bitcoin uses the proof-of-work (PoW) mechanism where nodes earn and not relying on a TTP exists. rewards in return for the use of their computing resources. Although this incentive system has attracted many participants, power has, CCS CONCEPTS at the same time, been significantly biased towards a few nodes, • Security and privacy → Economics of security and privacy; called mining pools. In addition, poor decentralization appears not Distributed systems security; only in PoW-based coins but also in coins that adopt proof-of-stake (PoS) and delegated proof-of-stake (DPoS) mechanisms. KEYWORDS In this paper, we address the issue of centralization in the consen- Blockchain; Consensus Protocol; Decentralization sus protocol. To this end, we first define ¹m; ε; δº-decentralization as a state satisfying that 1) there are at least m participants running 1 INTRODUCTION a node, and 2) the ratio between the total resource power of nodes Traditional currencies have a centralized structure, and thus there run by the richest and the δ-th percentile participants is less than exist several problems such as a single point of failure and corrup- or equal to 1 + ε. Therefore, when m is sufficiently large, and ε and tion. For example, the global financial crisis in 2008 was aggravated δ are 0, ¹m; ε; δº-decentralization represents full decentralization, by the flawed policies of banks that eventually led to many bank which is an ideal state. -

Exploring the Interconnectedness of Cryptocurrencies Using Correlation Networks
Exploring the Interconnectedness of Cryptocurrencies using Correlation Networks Andrew Burnie UCL Computer Science Doctoral Student at The Alan Turing Institute [email protected] Conference Paper presented at The Cryptocurrency Research Conference 2018, 24 May 2018, Anglia Ruskin University Lord Ashcroft International Business School Centre for Financial Research, Cambridge, UK. Abstract Correlation networks were used to detect characteristics which, although fixed over time, have an important influence on the evolution of prices over time. Potentially important features were identified using the websites and whitepapers of cryptocurrencies with the largest userbases. These were assessed using two datasets to enhance robustness: one with fourteen cryptocurrencies beginning from 9 November 2017, and a subset with nine cryptocurrencies starting 9 September 2016, both ending 6 March 2018. Separately analysing the subset of cryptocurrencies raised the number of data points from 115 to 537, and improved robustness to changes in relationships over time. Excluding USD Tether, the results showed a positive association between different cryptocurrencies that was statistically significant. Robust, strong positive associations were observed for six cryptocurrencies where one was a fork of the other; Bitcoin / Bitcoin Cash was an exception. There was evidence for the existence of a group of cryptocurrencies particularly associated with Cardano, and a separate group correlated with Ethereum. The data was not consistent with a token’s functionality or creation mechanism being the dominant determinants of the evolution of prices over time but did suggest that factors other than speculation contributed to the price. Keywords: Correlation Networks; Interconnectedness; Contagion; Speculation 1 1. Introduction The year 2017 saw the start of a rapid diversification in cryptocurrencies. -

Cryptonote Coin
CryptoNote Coin Michael Davis University of Miami April 2019 Proof of Work \scrypt" (used by Litecoin) has a uniform distribution of dependent lookups. Given a fast enough processor, it can be faster to only keep a small scratch-pad in memory and compute other dependencies on the fly. CryptoNight ensures that new blocks depend on all previous blocks, so CPU speed trades off with memory exponentially. Terminology I l = 2252 + 27742317777372353535851937790883648493 4 I A base point G = (x; − 5 ) I Hs a cryptographic hash function I Hp a deterministic hash function I Private keys are numbers a 2 [1; l − 1] I Public keys are points A = aG. I Private user keys are pairs (a; b) of private ec-keys I A standard address is a pair (A; B) derived from the private user key (a; b) Table of Contents Unlinkability Untraceability Alice ! Bob: Step 1 Alice reads Bob's public address (A; B). Alice ! Bob: Step 2 Alice generates r 2 [1; l − 1] and then computes P = Hs (rA)G + B. Alice ! Bob: Step 3 Alice generates the transaction. The transaction contains: I The transaction public key R = rG I The amount being transferred I The destination key P = Hs (rA)G + B Alice ! Bob: Step 4 Alice sends the transaction. Alice ! Bob: Step 5 Bob is listening on the stream of transactions. For each transaction, using R, the public key of the transaction, and a, one 0 of Bob's private ec-keys, Bob computes P = Hs (aR)G + B. If P0 = P (the destination key), then aR = arG = rA. -

Blockchain and The
NOTES ACKNOWLEDGMENTS INDEX Notes Introduction 1. The manifesto dates back to 1988. See Timothy May, “The Crypto Anarchist Manifesto” (1992), https:// www . activism . net / cypherpunk / crypto - anarchy . html. 2. Ibid. 3. Ibid. 4. Ibid. 5. Ibid. 6. Timothy May, “Crypto Anarchy and Virtual Communities” (1994), http:// groups . csail . mit . edu / mac / classes / 6 . 805 / articles / crypto / cypherpunks / may - virtual - comm . html. 7. Ibid. 8. For example, as we wi ll describe in more detail in Chapter 1, the Bitcoin blockchain is currently stored on over 6,000 computers in eighty- nine jurisdictions. See “Global Bitcoin Node Distribution,” Bitnodes, 21 . co, https:// bitnodes . 21 . co / . Another large blockchain- based network, Ethereum, has over 12,000 nodes, also scattered across the globe. See Ethernodes, https:// www . ethernodes . org / network / 1. 9. See note 8. 10. Some blockchains are not publicly accessible (for more on this, see Chapter 1). These blockchains are referred to as “private blockchains” and are not the focus of this book. 11. See Chapter 1. 12. The Eu ro pean Securities and Market Authority, “Discussion Paper: The Dis- tributed Ledger Technology Applied to Securities Markets,” ESMA / 2016 / 773, June 2, 2016: at 17, https:// www . esma . europa . eu / sites / default / files / library / 2016 - 773 _ dp _ dlt . pdf. 213 214 NOTES TO PAGES 5–13 13. The phenomena of order without law also has been described in other con- texts, most notably by Robert Ellickson in his seminal work Order without Law (Cambridge, MA: Harvard University Press, 1994). 14. Joel Reidenberg has used the term “lex informatica” to describe rules imple- mented by centralized operators online. -

Cryptonote V 2.0 1 Introduction 2 Bitcoin Drawbacks and Some
CryptoNote v 2.0 Nicolas van Saberhagen October 17, 2013 1 Introduction \Bitcoin" [1] has been a successful implementation of the concept of p2p electronic cash. Both professionals and the general public have come to appreciate the convenient combination of public transactions and proof-of-work as a trust model. Today, the user base of electronic cash is growing at a steady pace; customers are attracted to low fees and the anonymity provided by electronic cash and merchants value its predicted and decentralized emission. Bitcoin has effectively proved that electronic cash can be as simple as paper money and as convenient as credit cards. Unfortunately, Bitcoin suffers from several deficiencies. For example, the system's distributed nature is inflexible, preventing the implementation of new features until almost all of the net- work users update their clients. Some critical flaws that cannot be fixed rapidly deter Bitcoin's widespread propagation. In such inflexible models, it is more efficient to roll-out a new project rather than perpetually fix the original project. In this paper, we study and propose solutions to the main deficiencies of Bitcoin. We believe that a system taking into account the solutions we propose will lead to a healthy competition among different electronic cash systems. We also propose our own electronic cash, \CryptoNote", a name emphasizing the next breakthrough in electronic cash. 2 Bitcoin drawbacks and some possible solutions 2.1 Traceability of transactions Privacy and anonymity are the most important aspects of electronic cash. Peer-to-peer payments seek to be concealed from third party's view, a distinct difference when compared with traditional banking.