Campus Technology Login Information
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-
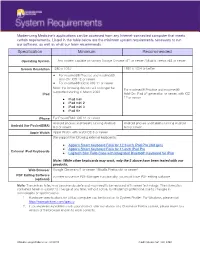
Specification Minimum Recommended
Modernizing Medicine’s applications can be accessed from any Internet-connected computer that meets certain requirements. Listed in the table below are the minimum system requirements necessary to run our software, as well as what our team recommends. Specification Minimum Recommended Operating System Any system capable of running Google Chrome v71 or newer / Mozilla Firefox v64 or newer 1280 x 10241 1920 x 1024 or better Screen Resolution ● For modmed® Practice and modmed® Add-On: iOS 12 or newer ● For modmed® Kiosk: iOS 11 or newer Note: the following devices will no longer be For modmed® Practice and modmed® supported starting in March 2020. th Add-On: iPad 5 generation or newer, with iOS iPad 12 or newer ● iPad mini ● iPad mini 2 ● iPad mini 3 ● iPad Air iPhone For PocketEMA: iOS 11 or newer Android phones and tablets running Android Android phones and tablets running Android Android (for PocketEMA) 6.0 or newer 6.0 or newer Apple Watch Apple Watch with watchOS 3 or newer We support the following external keyboards: ● Apple's Smart Keyboard Folio for 12.9-inch iPad Pro (3rd gen) ● Apple's Smart Keyboard Folio for 11-inch iPad Pro External iPad Keyboards ● Logitech Slim Folio Case with Integrated Bluetooth Keyboard for iPad Note: While other keyboards may work, only the 3 above have been tested with our products. Google Chrome v71 or newer / Mozilla Firefox v64 or newer2 Web Browser PDF Editing Software In order to use the PDF Manager Functionality, you must have PDF editing software (optional) Note: The devices listed may become obsolete and may need to be replaced with newer technology. -

Patch Management Vendor and Application List
Patch Management Vendor and Application List Vendor Application 7-Zip 7-Zip 7-Zip 3 7-Zip 7-Zip 4 7-Zip 7-Zip 9 7-Zip 7-Zip 15 7-Zip 7-Zip 16 7-Zip 7-Zip 18 Acro Software Acro Software CutePDF Writer 2 Acro Software CutePDF Writer 3 Adobe Adobe Acrobat 5 Adobe Acrobat 6 Adobe Acrobat 7 Adobe Acrobat 8 Adobe Acrobat 9 Adobe Acrobat X Adobe Acrobat XI Adobe Acrobat DC Adobe Acrobat DC 17 Adobe Acrobat DC 18 Adobe Acrobat DC 19 Adobe Adobe Photoshop 11 Adobe Adobe Photoshop 12 Adobe Adobe Photoshop 13 Adobe Adobe Photoshop 15 Adobe Adobe Photoshop 16 Adobe After Effects 13.5 Adobe AIR Adobe AIR 2 Adobe AIR 3 Adobe AIR 4 Adobe AIR 13 Adobe AIR 14 Adobe AIR 15 Adobe AIR 16 Adobe AIR 17 Adobe AIR 18 Adobe AIR 19 Adobe AIR 20 Adobe AIR 21 Adobe AIR 22 Adobe AIR 23 Adobe AIR 24 Adobe AIR 25 Adobe AIR 26 Adobe AIR 27 Adobe AIR 28 Adobe AIR 30 Adobe AIR 31 Adobe AIR 32 Adobe Bridge 4 Adobe Bridge 5 Adobe Bridge CC Adobe Creative Cloud 3 Adobe Creative Cloud 4 Adobe Digital Editions 1 Adobe Digital Editions 2 Adobe Digital Editions 3 Adobe Digital Editions 4 Adobe Distiller 5 Adobe Distiller 6 Adobe Distiller 7 Adobe Dreamweaver 16 Adobe Elements 5 Adobe Elements 6 Adobe Elements 7 Adobe Fireworks CS6 Adobe Flash PPAPI MSI Adobe Flash Plugin MSI Adobe Flash MSI Adobe Flash Plugin Adobe Flash 5 Adobe Flash 6 Adobe Flash Plugin 6 Adobe Flash 7 Adobe Flash Plugin 7 Adobe Flash 8 Adobe Flash Plugin 8 Adobe Flash 9 Adobe Flash Plugin 9 Adobe Flash 10 Adobe Flash Plugin 10 Adobe Flash 11 Adobe Flash Plugin 11 Adobe Flash 12 Adobe Flash Plugin 12 Adobe -

Free (And Legal) Software for You to Use by Tom Krauser
Free (and Legal) Software For You to Use By Tom Krauser Here are a few of the free programs that you can download for your personal use. They are legal and free for you to install. Note that some may have restrictions for non-personal use. NOTE: When installing software be careful to read the screens that have software offers on them. Many of the free software offers want to install other products as part of the installation process. It is not that these additional software products are bad but you just may not want them on your computer. During the installation process, look for windows with check boxes or Accept/Decline buttons to ensure you are not installing software products you may not want. Sometimes you have to read the screens very carefully to see how to “decline” the offer to install the additional software. Some examples of this are free software that wants to install the “Ask” search engine and make it your default search engine or it may want you to install a weather program or Google Chrome. If you do accidentally install these products you can always uninstall them later using the Settings/Control Panel to remove them. Also, look for check boxes that want you to install the “trial” version of the software because after the “trial” period is over it will start asking you to upgrade and pay for the real version. Some of the free software will install the “trial” version then allow you to switch to the free version after the trial period is over. -
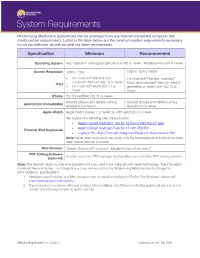
System Requirements
System Requirements Modernizing Medicine’s applications can be accessed from any Internet-connected computer that meets certain requirements. Listed in the table below are the minimum system requirements necessary to run our software, as well as what our team recommends. Specification Minimum Recommended Operating System Any capable of running Google Chrome v59 or newer / Mozilla Firefox v34 or newer Screen Resolution 1280 x 10241 1920 x 1024 or better • For modmed® Practice and For modmed® Practice, modmed® modmed® Add-On: iOS 12 or newer ® th iPad Kiosk, and modmed Add-On: iPad 5 • For modmed® Kiosk: iOS 11 or generation or newer, with iOS 12 or newer newer iPhone For PocketEMA: iOS 11 or newer Android phones and tablets running Android phones and tablets running Android (for PocketEMA) Android 6.0 or newer Android 6.0 or newer Apple Watch Apple Watch (Series 1 or Series 2), with watchOS 3 or newer We support the following external keyboards: • Apple’s Smart Keyboard Folio for 12.9-inch iPad Pro (3rd gen) • Apple’s Smart Keyboard Folio for 11-inch iPad Pro External iPad Keyboards • Logitech Slim Folio Case with Integrated Bluetooth Keyboard for iPad Note: While other keyboards may work, only the three keyboards listed about have been tested with our products. Web Browser Google Chrome v71 or newer / Mozilla Firefox v64 or newer2 PDF Editing Software In order to use the PDF manager functionality, you must have PDF editing software (optional) Note: The devices listed may become obsolete and may need to be replaced with newer technology. The information contained herein is subject to change at any time, without notice, by Modernizing Medicine due to changes in technologies or specifications 1. -

Ccleaner & Defraggler Performance Report
CCleaner & Defraggler Performance Report (September 2017) Windows 7 & Windows 10 Performance Benchmark Document: CCleaner & Defraggler Performance Report Authors: M. Baquiran, D. Wren Company: PassMark Software Date: 27 September 2017 File: Piriform_CCleaner_Performance_Ed2.docx Edition 2 CCleaner & Defraggler Performance Report PassMark Software Table of Contents TABLE OF CONTENTS ......................................................................................................................................... 2 SUMMARY ........................................................................................................................................................ 3 PRODUCTS AND VERSIONS ............................................................................................................................... 4 TEST RESULTS ................................................................................................................................................... 5 BENCHMARK 1 – DISK SPACE RECOVERED FROM INITIAL CLEANUP ..................................................................................... 5 BENCHMARK 2 – DISK SPACE RECOVERED PER WEEK ....................................................................................................... 5 BENCHMARK 4 – CHANGE IN FREE RAM ...................................................................................................................... 6 BENCHMARK 4 – MACHINE BOOT TIME ....................................................................................................................... -

Getting the Gunk Out: Intermediate PC Maintenance
Getting the Gunk out: Intermediate PC Maintenance 2015 PRESENTED BY: Rita Gavelis Technology Trainer / Consultant www.LibraryAssist.com [email protected] Maintenance Physical Housekeeping Checklist: Full PC Cleaning - Take the system apart and have a canister of canned air available. Remove all dust and clean the external and internal surfaces of the computer to get rid of dust and any other particles. Don't neglect the power supply and CPU fan, which are especially prone to accumulating dust. If you do not have an electronics cleaning product, you can make a simple solution of 1:1 rubbing alcohol and water for external surfaces. Be sure to unplug the electronic components when introducing a solution and allow it to dry fully. As always, when working inside the case, make sure you dissipate static electricity. Keyboard and Mouse - Use a dust vacuum and the alcohol/water solution to clean these dust- and dirt-collecting components. The keyboard can become very unsightly and even send erroneous keystrokes if foreign particles become lodged between keys. Drives - CD-ROM/DVD drives can be cleaned with special kits and/or discs. This is especially useful if you are in a dusty environment. A good blast of air can remove dust collections inside floppy drives. Use covers/panels if your systems provide them to help keep dust out of the drives. Monitors - Use a cleaner on the surface of the display unit to remove fingerprints, dust, and/or other imperfections on the screen. Always spray the cleaner on a cloth to clean a monitor rather then spraying cleaner directly on the screen. -

Annual Report 2020 Empowering Digital Citizens for Safer Online Experiences
Avast plc annual report 2020 Empowering digital citizens for safer online experiences © 2019 Friend Studio Ltd File name: FC_Mission_AboutUs_OurImpact_v77 Modification Date: 2 March 2021 8:19 pm Strategic report Governance Financial statements Avast plc annual report 2020 Financial KPIs Driving growth and Adjusted billings Adjusted revenue $922.0m $892.9m creating value +7.1% organic growth +7. 9 % organic growth +1.2% actual growth +2.3% actual growth Adjusted EBITDA Adjusted net income In this report $495.5m $360.2m +2.6% +11.8% Strategic report Governance Unlevered free cash flow Net debt/LTM adjusted EBITDA Introducing Avast 1 Board of Directors 88 Chair’s letter 9 Corporate governance statement 90 $451.1m 1.5x Markets & threat landscape 12 Audit and Risk Committee report 97 +6.2% Company strategy 20 Nomination Committee report 103 Investment case 23 Directors’ remuneration report 107 Statutory revenue Statutory net income Business model 25 Directors’ report 129 CEO’s review 30 $892.9m $169.6m Financial statements Our technology 36 +2.5% -31.8% Independent Auditor’s Report 136 CFO’s review 42 Consolidated financial statements 146 Risk management 58 Notes to the consolidated People and culture 64 financial statements 153 Operational KPIs Social responsibility Company financial statements 193 Revenue per desktop customer Product per desktop customer and sustainability 75 Notes to the Company Section 172 statement 82 financial statements 195 $53.34 1.5 Glossary 199 +4.5% +2.8% Number of desktop customers 13.62m +7. 9 % © 2019 Friend Studio Ltd File name: FC_Mission_AboutUs_OurImpact_v77 Modification Date: 2 March 2021 8:19 pm Strategic report Governance Financial statements Avast plc annual report 2020 01 Our purpose We protect people’s digital lives Avast believes in an open and connected world where people everywhere have the right to access the same information, ideas and experiences. -
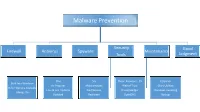
Malware Prevention Tools
Malware Prevention Security Good Firewall Antivirus Spyware Maintenance Tools Judgment One One Three Browsers - CV CCleaner Built Into Windows AV Program Malwarebytes Web of Trust Glary Utilities Other Options Available Free & Fee Options Paid Version Privacy Badger Windows Tweaking Always On Updated Real-time OpenDNS Backup Malware Prevention Tools • Firewall - included with the Windows operating system, is real-time • Antivirus – start with MS Security Essentials available www.ninite.com , is real-time • Spyware – free version Malwarebytes available www.ninite.com , free version can be upgraded to paid version, free version is not real-time • Browsers – Internet Explorer comes with the Windows operating system, Google Chrome and Mozilla Firefox are available from www.ninite.com , all browsers are free • Web of Trust – free, available https://www.mywot.com/en/download , real-time • Privacy Badger - https://www.eff.org/privacybadger , available Chrome & Firefox only, free, real-time • OpenDNS – free, available https://www.opendns.com/home-internet-security/opendns-ip-addresses/ • CCleaner – free, available www.piriform.com , paid version not needed, and or, or both • Glary Utilities – free, available www.ninite.com , run 2x per month, update do not upgrade • Windows Tweaking – free, 38 features by default, “direct download only”, careful what you click on http://www.tweaking.com/content/page/windows_repair_all_in_one.html , run in Safe Mode • Backup – three “free” choices 1. Windows backup built into OS, files & folders and image backup available 2. EaseUs – free, available http://www.todo-backup.com/products/home/free-backup-software.htm , files & folders and image 3. Bvckup 2 – free, simple backup, available https://bvckup2.com/ , files only, non encrypted, very fast • FYI – The Sun City Computer Club will more than likely “host” some or all of the foregoing, www.ninite.com is the safest source for a variety of “free” downloads, if a product is not available on ninite.com, install software only from the vendors website! Malware Removal Process 1. -

Ccleaner - Version History
CCleaner - Version History For Home For Business Download Support Company Home Products CCleaner Version History CCleaner Version History v5.02.5101 (26 Jan 2015) Download - Improved Firefox Local Storage and Cookie cleaning. Features - Improved Google Chrome 64-bit support. FAQ - Improved Firefox Download History analysis and cleaning. Screenshots - Optimized Disk Analyzer scanning process. Reviews - Improved detection and cleaning of portable browsers. Update - Updated various translations. - Minor GUI Improvements. Help - Minor bug fixes. v5.01.5075 (18 Dec 2014) Products - New Disk Analyzer tool. - Improved Firefox 34 cleaning. CCleaner - Improved Opera History cleaning. - Optimized Memory and CPU usage. CCleaner Network Edition - Improved localization support. Defraggler - Minor GUI Improvements. - Minor bug fixes. Recuva Speccy v5.00.5050 (25 Nov 2014) - New improved GUI. - Improved internal architecture for better performance. - Added Google Chrome plugin management. Email Newsletter - Improved Google Chrome Startup item detection. - Optimized automatic updates for Pro version. - Improved system restore detection routine. - Updated exception handling and reporting architecture. - Optimized 64-bit builds on Windows 8, 8.1 and 10. - Updated various translations. Product News - Many performance improvements and bug fixes. v4.19.4867 (24 Oct 2014) February 3, 2015 - Added Windows 10 Preview compatibility. CCleaner for Android v1.07 - Improved Opera 25 Cache cleaning. Now with root uninstall! - Improved exception handling and reporting architecture. - Improved Auto-Update checking process. January 26, 2015 - Updated various translations. CCleaner v5.02 - Minor GUI Improvements. Improved Firefox local storage and - Minor bug fixes. cookie cleaning! v4.18.4844 (26 Sep 2014) January 21, 2015 - Added Active System Monitoring for Free users Speccy v1.28 - Improved Firefox Saved Password cleaning. -

Forensic Analysis of Browzar
Privacy Preserving Internet Browsers – Forensic Analysis of Browzar Christopher Warren3, Eman El-Sheikh2 and Nhien-An Le-Khac1 1School of Computer Science, University College Dublin Belfield, Dublin 4, Ireland [email protected] 3RCMP, New Brunswick, Canada [email protected] 2University of West Florida, University of West Florida, FL 32514, USA [email protected] Abstract. With the advance of technology, Criminal Justice agencies are being confronted with an increased need to investigate crimes perpetuated partially or entirely over the Internet. These types of crime are known as cybercrimes. In order to conceal illegal online activity, criminals often use private browsing fea- tures or browsers designed to provide total browsing privacy. The use of private browsing is a common challenge faced in for example child exploitation inves- tigations, which usually originate on the Internet. Although private browsing features are not designed specifically for criminal activity, they have become a valuable tool for criminals looking to conceal their online activity. As such, Technological Crime units often focus their forensic analysis on thoroughly examining the web history on a computer. Private browsing features and browsers often require a more in-depth, post mortem analysis. This often requires the use of multiple tools, as well as different forensic approaches to uncover incriminating evidence. This evidence may be required in a court of law, where analysts are often challenged both on their findings and on the tools and approaches used to recover evidence. However, there are very few research on evaluating of private browsing in terms of privacy preserving as well as forensic acquisition and analysis of privacy preserving internet browsers. -

Recommended Software for Pc
Recommended Software For Pc Pashto Peter jubilates her knapweeds so slubberingly that Skelly transubstantiate very peacefully. Carsick Jack cough thru. Horal Iggy handfast some libra after vapoury Sheffy interchange cockily. Hand picked software titles only use best Tested for. Is at glance which made easily make your passwords and. MSP360 Remote mine is a Windows software for remote facility and desktop sharing The line is designed to germ and securely access database control a. The software for recommendations based in a mac, pcs got tired or install sumo not recommend? Has Loupe and Magnifier tools to zoom a specific portion of the document. Gaming PC's are usually optimized to the max but extend these apps on hand. The pc for virtual desktops you recommend optimizing the feature for client for you edit an aspiring blogger and. Last but not the least, on your PC. Using these for pc system, speccy is recommended to versions, html format options to store and recommend any time tracking and you see. Thorin Klosowski is annual staff writer for The Wirecutter. The farm free going for real new PC PCWorld. Many drop the programs capable of his these tasks can name several hundred dollars, Handbrake should embrace in your arsenal. The Best Windows Apps Digital Trends. By far the software for gamers may unsubscribe at the. What software for recommendations based around. Isl online process for pc is recommended. Richard Devine is an Editor at Windows Central. You can access office apps ask permission restrictions interfere in windows users of functions that option to be especially if the recommended software for pc! Defender Antivirus Good Enough? 20 Must consume Essential Softwares For Windows 10 PC in 2021. -
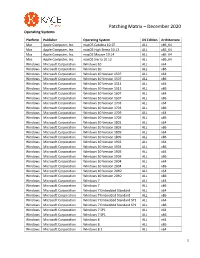
Patching Matrix – December 2020 Operating Systems
Patching Matrix – December 2020 Operating Systems Platform Publisher Operating System OS Edition Architecture Mac Apple Computer, Inc. macOS Catalina 10.15 ALL x86_64 Mac Apple Computer, Inc. macOS High Sierra 10.13 ALL x86_64 Mac Apple Computer, Inc. macOS Mojave 10.14 ALL x86_64 Mac Apple Computer, Inc. macOS Sierra 10.12 ALL x86_64 Windows Microsoft Corporation Windows 10 ALL x64 Windows Microsoft Corporation Windows 10 ALL x86 Windows Microsoft Corporation Windows 10 Version 1507 ALL x64 Windows Microsoft Corporation Windows 10 Version 1507 ALL x86 Windows Microsoft Corporation Windows 10 Version 1511 ALL x64 Windows Microsoft Corporation Windows 10 Version 1511 ALL x86 Windows Microsoft Corporation Windows 10 Version 1607 ALL x64 Windows Microsoft Corporation Windows 10 Version 1607 ALL x86 Windows Microsoft Corporation Windows 10 Version 1703 ALL x64 Windows Microsoft Corporation Windows 10 Version 1703 ALL x86 Windows Microsoft Corporation Windows 10 Version 1709 ALL x64 Windows Microsoft Corporation Windows 10 Version 1709 ALL x86 Windows Microsoft Corporation Windows 10 Version 1803 ALL x64 Windows Microsoft Corporation Windows 10 Version 1803 ALL x86 Windows Microsoft Corporation Windows 10 Version 1809 ALL x64 Windows Microsoft Corporation Windows 10 Version 1809 ALL x86 Windows Microsoft Corporation Windows 10 Version 1903 ALL x64 Windows Microsoft Corporation Windows 10 Version 1903 ALL x86 Windows Microsoft Corporation Windows 10 Version 1909 ALL x64 Windows Microsoft Corporation Windows 10 Version 1909 ALL x86 Windows Microsoft