Metadata's Shadows in the Courtroom
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

GLAAD Media Institute Began to Track LGBTQ Characters Who Have a Disability
Studio Responsibility IndexDeadline 2021 STUDIO RESPONSIBILITY INDEX 2021 From the desk of the President & CEO, Sarah Kate Ellis In 2013, GLAAD created the Studio Responsibility Index theatrical release windows and studios are testing different (SRI) to track lesbian, gay, bisexual, transgender, and release models and patterns. queer (LGBTQ) inclusion in major studio films and to drive We know for sure the immense power of the theatrical acceptance and meaningful LGBTQ inclusion. To date, experience. Data proves that audiences crave the return we’ve seen and felt the great impact our TV research has to theaters for that communal experience after more than had and its continued impact, driving creators and industry a year of isolation. Nielsen reports that 63 percent of executives to do more and better. After several years of Americans say they are “very or somewhat” eager to go issuing this study, progress presented itself with the release to a movie theater as soon as possible within three months of outstanding movies like Love, Simon, Blockers, and of COVID restrictions being lifted. May polling from movie Rocketman hitting big screens in recent years, and we remain ticket company Fandango found that 96% of 4,000 users hopeful with the announcements of upcoming queer-inclusive surveyed plan to see “multiple movies” in theaters this movies originally set for theatrical distribution in 2020 and summer with 87% listing “going to the movies” as the top beyond. But no one could have predicted the impact of the slot in their summer plans. And, an April poll from Morning COVID-19 global pandemic, and the ways it would uniquely Consult/The Hollywood Reporter found that over 50 percent disrupt and halt the theatrical distribution business these past of respondents would likely purchase a film ticket within a sixteen months. -

'2009 MTV Movie Awards' Honors Ben Stiller with 'MTV Generation Award'
'2009 MTV Movie Awards' Honors Ben Stiller With 'MTV Generation Award' Premiering LIVE Sunday, May 31, 2009 at 9pm ET/8pm CT From The Gibson Amphitheatre in Universal City, CA SANTA MONICA, Calif., May 22 -- The 2009 MTV Movie Awards pays tribute to Ben Stiller with the coveted "MTV Generation Award" for his amazing contribution to Hollywood and for entertaining the MTV audience for years. From generation to generation, Ben Stiller has kept fans rolling with laughter since bursting onto the scene in Reality Bites and his early film roles and cult classics such as There's Something About Mary, Meet the Parents, Dodgeball: A True Underdog Story, Tropic Thunder and now this summer's eagerly anticipated Night at the Museum: Battle at the Smithsonian in theaters May 22, 2009. The "MTV Generation Award" is the MTV Movie Awards' highest honor, acknowledging an actor who has captured the attention of the MTV audience throughout his or her career. Past recipients include Adam Sandler, Mike Myers, Tom Cruise and Jim Carrey. Hosted by Andy Samberg, the 2009 MTV Movie Awards will be broadcast LIVE from the Gibson Amphitheatre in Universal City, CA on Sunday, May 31st at 9p.m. ET/8p.m. CT. "From The Royal Tenenbaums to Zoolander, Ben is a comedic chameleon, able to make the leap between drama and full-out comedy while maintaining his own unique brand of subversive humor," said Van Toffler, President of MTV Networks Music/Logo/Film Group. "That versatility and talent has earned him legions of devoted fans over the years which makes him a perfect recipient for the 'MTV Generation Award.' Whether it's fighting a monkey in a museum or licking a decapitated head, nothing is ever off-limits for him and that's the type of warped creative vision and commitment MTV loves to reward." "I am honored to be getting the 'Generation Award,'" said Ben Stiller. -

2016 Movie Schedule
2016 Free Movie Series June 11 Zoolander, Rated PG-13; 88 minutes; 2001 Sponsored by Plato’s Closet Starring: Ben Stiller, Owen Wilson, Will Ferrell Derek Zoolander is an intellectually challenged but bone structure-blessed male model who's despondent after being eclipsed in popularity by an equally vacuous rival, Hansel. Upon his reluctant retirement, Derek is invited to a day spa by previously standoffish fashion designer Jacobim Mugatu where the befuddled model is brainwashed by the mysterious Katinka into assassinating the prime minister of Malaysia. June 18 RENT, Rated PG-13; 135 minutes; 2005 Sponsored by Pride Week Starring: Rosario Dawson, Adam Pascal, Idina Menzel This rock opera tells the story of one year in the life of a group of bohemians struggling in modern day East Village New York. The story centers around Mark and Roger, two roommates. While a former tragedy has made Roger numb to life, Mark tries to capture it through his attempts to make a film. The group deals with AIDS, poverty, drugs, illness and just trying to pay the rent in the 525,600 minutes that make up a year. June 25 The Wedding Singer, Rated PG-13; 93 minutes; 1998 Sponsored by Garage Mahaul Starring: Adam Sandler, Drew Barrymore, Christine Taylor In 1985, Robbie Hart is a vocalist whose rock band stubbornly refuses to get off the ground. In the meantime, he makes a living playing wedding receptions, where he meets Julia Sullivan when she's working as a waitress. He immediately takes a shine to her, but since she is engaged, he keeps his distance. -

SUSANNE SCHEEL NY Based Casting Director Two-Time CSA Artios Winner, Seven-Time Nominee [email protected] O: 212.941-2001 M: 701.412.6724
SUSANNE SCHEEL NY Based Casting Director Two-time CSA Artios Winner, Seven-time nominee [email protected] O: 212.941-2001 M: 701.412.6724 Feature Films Past Lives (2021) dir. Celine Song, produced by A24 & Scott Rudin Productions, currently casting, Cast: Choi Woo-sik & Jong-seo Jun Love.Wedding.Repeat (2020) dir. Dean Craig – Premiered on Netflix April 12th, has been in the top 3 watched new programs in several countries; Cast: Sam Catlin, Aisling Bea, Eleanor Tomlinson, Frieda Pinto, Tim Key, Joel Frey, Jack Farthing, Olivia Munn Night into Day (2020) dir. Ben Hall; Premiered on Amazon Prime on July 20th, Prods: Elyse Rosenfield and Marjorie Chodorov; Cast: Justin Gaston, Jessica Renee Russell, Christopher Mychael Watson, Ray Corasani The Wife (2017) dir. Bjorn Runge – Sony Classics, premiered at TIFF, Glenn Close nominated for numerous roles for her role "Joan Castleman"; Cast: Glenn Close, Jonathan Pryce, Christian Slater, Max Irons, Annie Starke, Harry Lloyd, Elizabeth McGovern Folk Hero and Funny Guy (2016) dir. Jeff Grace – Premiered at Tribeca Film Festival; Cast: Wyatt Russell, Alex Karpovsky, Meredith Hagner, Melanie Lynskey, David Cross, Hannah Simone, Heather Morris Television Barkskins (2020) NatGeo, Fox 21 – dir. David Slade & various, Prods. Elwood Reid, Scott Rudin & Garret Basch; Cast: David Thewlis, Marcia Gay Harden, David Wilmot, Aneurin Barnard, Thomas M. Wright, Christian Cooke, James Bloor, Lily Sullivan & Tallulah Haddon Scripted Audio Series The Coldest Case (2020) Audible, Broadway Video & James Patterson Entertainment, dir. Matt Luem; Cast: Aaron Paul, Beau Bridges, Krysten Ritter, Nathalie Emmanuel, Kevin Dunn, Alexis Bledel & Karan Soni The Marvels (2020) Marvel & Stitcher Entertainment, dir. -

Suggested Fashion Films and TV
Suggested Fashion Films and TV: • 1800-1850 o Dinner at Eight (1933) o Beau Brumell: This Charming Man (2008) o Letty Lynton (1932) • 1850-1890 o Grand Hotel (1932) o Little Women (1994) o Baby Face (1933) o The Young Victoria (2009) o Atonement (2007, also 1940s) o Mrs. Brown (1997, Netflix) o The Women (1939) o Possession (2002) • 1940s o Gone with the Wind (1939) o Land Girls (Netflix) • 1890s o Home Fires o The Paradise (Netflix) o Mildred Pierce (1945) • 1900s o His Girl Friday (1940, Netflix) Double Indemnity (1944) o Mr. Selfridge o The Big Sleep (1946) o My Fair Lady (1964) o Ball of Fire (1941) o A Room with a View (1986, Netflix) o Key Largo (1948) o Wings of the Dove (1997, Netflx) o Casablanca (1942) o Daughters of the Dust (1991) o o The Philadelphia Story (1940) • 1910s o Now, Voyager (1942) o Downton Abbey (Netflix)-also 1920s o Zoot Suit Riots (documentary, 2002) o Tillie’s Punctured Romance (1914, YouTube) o Malcolm X (1992, also 1950s, 1960s) o The House of Mirth (2000) • 1950s • 1920s o Velvet (Netflix) o Miss. Fisher’s Murder Mysteries (Netflix) o Call the Midwife (Netflix) o Coco Chanel & Igor Stravinsky o How to Marry a Millionaire (1953, Netflix) o Cold Comfort Farm (1995) o An Affair to Remember (1957, Netflix) o The Great Gatsby (2013) o Roman Holiday (1953, Netflix) o The Cat’s Meow (2001) o All that Heaven Allows (1955) o Salome (1923, YouTube) o Far From Heaven (2002) o The House of Elliot o Imitation of Life (1959) o The Wild Party (1929) o Carol (2015) o It (1927) o Funny Face (1957) o Why Change Your Wife (1920, YouTube) o Sabrina (1954) o Our Dancing Daughters (1928) o The Wild One (1953) o Our Modern Maidens (1929) o Rebel Without a Cause (1955) • 1930s o Gentlemen Prefer Blondes (1953) Dancing on the Edge (Netflix) o o All about Eve (1950) o Mildred Pierce (HBO Miniseries, 2011) o Rear Window (1954) o The Divorcee (1930) o Carol (1952) o Madam Satan (1930) • 1960s o Christopher Strong (1933) o Mad Men (Netflix) o Holiday (1938) o The Marvelous Mrs. -

FILM REVIEW: Zoolander 2
Page 6 • INDEPENDENT • FEBRUARY 17, 2016 Zoolander (Ben Stiller) and FILM REVIEW: Zoolander 2 Hansel (Owen Wilson) res- Dear Lord, please don’t let to hate on this movie; I’m a I’ll try to relate the story to urrect their characters from there be a “Zoolander 3.” I human that suff ers and don’t you, but please don’t expect 2001. A little long in the didn’t mean to blaspheme, I bleed when cut? Ben and an explanation of the ending tooth with hair and careers es- but I do hope that director three other writers actually as I left before the grand fi na- chew, the bimbos are attempt- and star Ben Stiller makes a sat in a conference room and le. Only fi fteen minutes left, ing to… I’m sorry; I’m not lot of money on this silly slice laughed at this facacta – which but I was not strong enough to sure what they were trying to of diddly boo and then lets is Yiddish for trash/manure or remain in Theatre 23. I tried; do. I did note that Penelope the franchise die. I didn’t see other smelly things. There dat gummit. Cruz is still a fox even in an “Zoolander 1” so who am I was defi nitely an odor. Our male models Derek absurd movie. How dumb NOTICE OF SALE STATE OF TEXAS § BY VIRTUE OF AN ORDER OF SALE § FORT BEND COUNTY § and issued pursuant to judgment decree(s) of the District Court of Fort Bend County, Texas, by the Clerk of said Court on said date, in the hereinafter numbered and styled suit(s) and to me directed and delivered as Sheriff or Constable of said County, I have on January 27, 2016, seized, levied upon, and will, on the first Tuesday in March, 2016, the same being the 1st day of said month, at 301 Jackson Street, William Travis Building, 1st Floor Meeting Room in the City of Richmond, Texas 77469, between the hours of 10 o'clock a.m. -

Loki Production Brief
PRODUCTION BRIEF “I am Loki, and I am burdened with glorious purpose.” —Loki arvel Studios’ “Loki,” an original live-action series created exclusively for Disney+, features the mercurial God of Mischief as he steps out of his brother’s shadow. The series, described as a crime-thriller meets epic-adventure, takes place after the events Mof “Avengers: Endgame.” “‘Loki’ is intriguingly different with a bold creative swing,” says Kevin Feige, President, Marvel Studios and Chief Creative Officer, Marvel. “This series breaks new ground for the Marvel Cinematic Universe before it, and lays the groundwork for things to come.” The starting point of the series is the moment in “Avengers: Endgame” when the 2012 Loki takes the Tesseract—from there Loki lands in the hands of the Time Variance Authority (TVA), which is outside of the timeline, concurrent to the current day Marvel Cinematic Universe. In his cross-timeline journey, Loki finds himself a fish out of water as he tries to navigate—and manipulate—his way through the bureaucratic nightmare that is the Time Variance Authority and its by-the-numbers mentality. This is Loki as you have never seen him. Stripped of his self- proclaimed majesty but with his ego still intact, Loki faces consequences he never thought could happen to such a supreme being as himself. In that, there is a lot of humor as he is taken down a few pegs and struggles to find his footing in the unforgiving bureaucracy of the Time Variance Authority. As the series progresses, we see different sides of Loki as he is drawn into helping to solve a serious crime with an agent 1 of the TVA, Mobius, who needs his “unique Loki perspective” to locate the culprits and mend the timeline. -

P38-39 Layout 1
lifestyle TUESDAY, JANUARY 19, 2016 FASHION Fashion Week Fashion Milan Discreet detailing Bottega Veneta creative director Tomas Maier gave some rock ‘n’ roll edge to a decidedly wintery wardrobe. Amid the tweeds and wools, plaids and checks, the German designer incorporated stage-worthy statements, from velvet double-breasted suits that catch the light in burgundy and a deep peacock blue, to leather trousers with eye-catching zippers all the way down the front of the leg, silken Henley shirts with tuxedo ruffle details and long scarves, silken and woolen both, that added drama with every step. Maier joined other Milan designers in tipping his hat to music and fashion icon David Bowie with the occa- sional felt brimmed chapeau to create an aura of mystery. The overall silhouette of the collection was long and lean, something Bowie could have worn well, with pants that gently flair at the square-toed boot and elegant coat lengths below the knee. Details set the pieces apart, including diagonal buckle to close the collar on cash- mere overcoats to the coated tweed wool coat that had an eye-catching sheen. Maier said in his notes that the collection has “no tricks, nothing ostentatious. It is very discreet.” Save Venice Models present creations for fash- British designer Vivienne Westwood is imploring the ion house Bottega Veneta. world to “be specific.” By that she means to be specific about what needs to be changed, part of her runway activism. For her latest menswear preview show, Westwood added a plea to save Venice from cruise ships. To drive the point home, the invitation featured a repro- duction of a painting of the canal city’s historic canals with an enormous cruise ship hulking in the background. -

Surprise and Seduction: Theorising Fashion Via the Sociology of Wit Dita
Surprise and seduction: Theorising fashion via the sociology of wit Dita Svelte A thesis in fulfilment of the requirements for the degree of Doctor of Philosophy School of Social Sciences Faculty of Arts and Social Sciences UNSW Sydney 12 September 2019 THE UNIVERSITY OF NEW SOUTH WALES Thesis/Dissertation Sheet Surname or Family name: SVELTE First name: DITA Other name/s: ISHTAR ARTEMIS Abbreviation for degree as given in the University calendar: Doctor of Philosophy (PhD) School: School of Social Sciences Faculty: Arts and Social Sciences Title: Surprise and seduction: Theorising fashion via the sociology of wit Abstract 350 words maximum: What insights might a sociology of wit as applied to the phenomenon of fashion generate? This thesis applies the sociology of humour to fashion to develop a concept of wit that contributes to further understanding fashion. The thesis argues that this concept of wit is characterised by qualities of surprise and seduction. Surprise is defined as the experience of an unexpected, creative intellectual insight expressed in a pithy manner; seduction is the experience of being led astray, and also the desire of the subject to be led astray. The thesis demonstrates the presence of empirical sites of wit within fashion in the form of the dandy and glamour. It utilises Thomas Carlyle’s Sartor Resartus [2000] (1836) to further conceptualise the wit of fashion at the intersection of theories of humour and theories of fashion. The contribution of the wit of fashion to classical texts in the sociology of fashion -
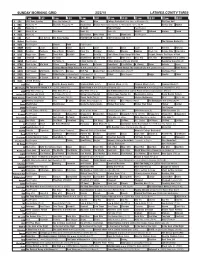
Sunday Morning Grid 2/22/15 Latimes.Com/Tv Times
SUNDAY MORNING GRID 2/22/15 LATIMES.COM/TV TIMES 7 am 7:30 8 am 8:30 9 am 9:30 10 am 10:30 11 am 11:30 12 pm 12:30 2 CBS CBS News Sunday Face the Nation (N) Men Men College Basketball Ohio State at Michigan. (N) PGA Tour Golf 4 NBC News (N) Å Meet the Press (N) Å Hockey Day Hockey Washington Capitals at Philadelphia Flyers. (N) Å Hockey Day Hockey 5 CW News (N) Å In Touch Hour Of Power Paid Program 7 ABC News (N) Å This Week News (N) News (N) Wildlife Outback Explore Award 9 KCAL News (N) Joel Osteen Mike Webb Paid Woodlands Paid Program 11 FOX Paid Joel Osteen Fox News Sunday FOX NASCAR Sunday (N) 2015 Daytona 500 (N) Å 13 MyNet Paid Program The Princess Bride (PG) 18 KSCI Paid Program Church Faith Paid Program 22 KWHY Como Local Local Local Local Local Local Local Local Local Transfor. Transfor. 24 KVCR Painting Dewberry Joy of Paint Wyland’s Paint This Painting Kitchen Mexico Cooking Chefs Life Simply Ming Ciao Italia 28 KCET Raggs Rain. Space Travel-Kids Biz Kid$ News Asia Biz Don’t Worry, Retire Happy With Tom Deepak Chopra: The Future of God 30 ION Jeremiah Youssef In Touch Bucket-Dino Bucket-Dino Doki Doki (TVY7) Dive, Olly Dive, Olly Parenthood ››› (1989) 34 KMEX Paid Program Al Punto (N) Fútbol Central (N) Fútbol Mexicano Primera División República Deportiva (N) 40 KTBN Walk in the Win Walk Prince Carpenter Liberate In Touch PowerPoint It Is Written B. -

Your Best Source for Local Entertainment Information
Page 6 THE NORTON TELEGRAM Tuesday, December 16, 2003 Monday Evening December 22, 2003 7:00 7:30 8:00 8:30 9:00 9:30 10:00 10:30 11:00 11:30 KHGI/ABC Threat Matrix NFL Football Local Local KBSH/CBS Yes, Dear Standing Raymond Two Half CSI: Miami Local Late Show Late Late KSNK/NBC Fear Factor Las Vegas Las Vegas Local Tonight Show Conan FOX Simpsons King Hill Malcolm Arrested Local Local Local Local Local Local Cable Channels A&E Biography Cold Case Files City Confidential Third Watch Biography AMC The Horse Whisperer Hud ANIM King Of The Jungle Cell dogs Animal Precinct King Of The Jungle Cell dogs CNN Paula Zahn Now Larry King Live Newsnight Lou Dobbs Larry King Norton TV DISC Monster House Monster Garage American Chopper Monster House Monster Garage DISN Full- Court Miracle Sis,Sis Boy Meets Kim Poss Proud Fa Evn Stvns Sis, Sis E! THS Lisa Marie Presley E!OS Love Chai Howard Howard Wild On Panama ESPN Tangerine Bowl World Seri Sportscenter ESPN2 Monday Night Countdown Brian Boitano's Skating Spectacul World Gymnastics Fast Brea Streetball FAM Three Days Whose Lin Whose Lin The 700 Club Funniest Funniest FX Big Cops Cops Married.... Big HGTV Drm Hous Divine CurbAppe Dsgn Chal Dsgn Dim Dsgn Dme Hunters Ground Drm Hous Divine HIST Mail Call In Search Of Christmas The Christmas Truce Mail Call LIFE Take Me Home Nanny Nanny Golden Gr Golden Gr Any day Now MTV Newlywed Newlywed Newlywed Newlywed Newlywed Newlywed Crtvsy MTV Cribs Punk'D Viva La Listings: NICK Fairly Odd Rocket Pr Full Hous Full Hous Cosby Cosby Roseanne Roseanne Cosby Cosby -
“ Crossing the Border
PUNK ICON A WOW Hall concert will honor Joe Strummer and raise money to build a new skate park PAGE 5 OREG O N WWW.DAILYEMERALD.COM DAILYTHURSDAY | AuGUST 14, 2008 EMERALThe independent student newspaper at the University of Oregon | Since 1900D Volume 110, Issue 24 University gets go-ahead for alley vacation The city will allow the UO with a 5-3 vote after discussing the issue Bonny Bettman said. “My motivation constructing a sidewalk. which may be granted after it receives to purchase the alley and for over an hour. To approve a property here is to make the alley vacation be in However, after several councilors a Conditional Use Permit, before it can vacation, the council must rule that it is the public interest.” pointed out that it would be difficult to begin construction. a neighboring plot of land in the public interest to sell the land. Bettman began the work session assign another value to the properties “The UO manufactured this sense of University spokesperson Phil Wei- yesterday with a motion to increase the without postponing the decision to re- JESSIE HIGGINS | NEWS REPORTER urgency to get us to prematurely grant ler said the University requested the purchase price of the parcels by nearly negotiate the price with the University, them this alley vacation so that they can The Eugene City Council approved vacation because it already owns $1 million. Bettman withdrew the amendment, get this part under their belt, but they’re the vacation of an alley way and another property on three sides of the Vil- The University had already depos- opting to instead table the decision and going to really sit on this for several small area of land near the site of the lard Alley from East 13th Avenue to ited $482,950 with the city as payment re-negotiate the cost of the properties.