Ip Commission Report Acknowledgments
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

China's Shanzhai Entrepreneurs Hooligans Or
China’s Shanzhai Entrepreneurs Hooligans or Heroes? 《中國⼭寨企業家:流氓抑或是英雄》 Callum Smith ⾼林著 Submitted for Bachelor of Asia Pacific Studies (Honours) The Australian National University October 2015 2 Declaration of originality This thesis is my own work. All sources used have been acknowledGed. Callum Smith 30 October 2015 3 ACKNOWLEDGEMENTS I am indebted to the many people whose acquaintance I have had the fortune of makinG. In particular, I would like to express my thanks to my hiGh-school Chinese teacher Shabai Li 李莎白 for her years of guidance and cherished friendship. I am also grateful for the support of my friends in Beijing, particularly Li HuifanG 李慧芳. I am thankful for the companionship of my family and friends in Canberra, and in particular Sandy 翟思纯, who have all been there for me. I would like to thank Neil Thomas for his comments and suggestions on previous drafts. I am also Grateful to Geremie Barmé. Callum Smith 30 October 2015 4 CONTENTS ACKNOWLEDGEMENTS ................................................................................................................................ 3 ABSTRACT ........................................................................................................................................................ 5 INTRODUCTION .............................................................................................................................................. 6 THE EMERGENCE OF A SOCIOCULTURAL PHENOMENON ................................................................................................... -

Samsung Galaxy S Iii Manual Czy Iphone 5 Zapytaj
Samsung Galaxy S Iii Manual Czy Iphone 5 Zapytaj ROM Link Thread (Download) forum.xda-developers.com/galaxy-s3/ development/wip. blogwogrodzie.pl/2014/10/5-podgladamy-realizacje-seria-3-po-miesiacu/ zapytaj.pl/pytanie/gdzie- moge-zamowic-tanie-ogrodzenie-do-ogrodu brama.net/story.php?title=tips-download-lagu-bebas- di-iphone download lagu articleopinion.com/story.php?title=samsung-galaxy-tab-review-articles. Compare Samsung Galaxy Core Prime VS Samsung Galaxy S III mini full FDD LTE, 700 (band 28), 850 (band 5), 900 (band 8), 1800 (band 3), 2100 (band 1), The 'S' factor, or why the iPhone 6s is Apple's biggest mid-cycle upgrade yet. The end users can download apps from Android Market place.) Calendar, Alarm clock, Calculator, MMS, 3D Music, Advanced App Killer, Aldiko eBook, Browser. Apple iPhone 6 i Samsung Galaxy Alpha to dwa smartfony, które, mimo że iphone 4. Zune AppleTV iPhone MP4 Converter v 2. PC Game: Call of Duty Black Ops II Skidrow New Final Crack New are 2 options to load maps and to choose weapons: Automatic and Manual. SOTI Pocket Controller Professional 5 0. on the Android Market have been created to enrich your Android. Samsung Galaxy S Iii Manual Czy Iphone 5 Zapytaj Read/Download To Control android from PC there are many apps available just like a Airdroid also available, but not all Google Docs- Better integration with iOS and Android. Shows 5MP) Flash Light Built-in Video Record Supported OS Android 4.2 Jelly Ban Operating System ISO 8 Theme like iOS 8 Android 4.2 Jelly Ban Operating. -

BAB II Counterfeiting Di China Pada Rezim Pemerintahan Hu Jintao Di
BAB II Counterfeiting di China Pada Rezim Pemerintahan Hu Jintao Di kasus ini adanya dua norma yang berbeda dalam melihat pemalsuan atau counterfeiting yaitu dari norma internasional (World Trade Organization) dan norma domestik masyarakat China (Konfusianisme). Norma World Trade Organization melalui TRIPs dalam memandang pemalsuan adalah sebagai pelanggaran yang mengharuskan setiap negara peserta untuk memerangi atau melawan tindak pemalsuan dan pembajakan merek dagang yang telah merugikan negara lain (Matsubara, 2003:1). Sedangkan norma yang dianut oleh masyarakat China adalah norma konfusianisme yang berbeda dalam melihat pemalsuan. Dalam pandangan konfusianisme ini menganggap pemalsuan sebagai bentuk sanjungan yang paling tulus dan komponen penting dari proses kreatif (Boyle, 1996:54). Norma internasional ini telah ditolak oleh masyarakat China mengenai pemalsuan dikarenakan tidak sesuai dengan norma yang sudah dianut oleh masyarakat China yaitu konfusianisme. Cocok tidak cocoknya norma internasional ditentukan oleh norma domestiknya dan dipengaruhi oleh faktor domestik (Rosyidin, 2015:84). Dari faktor domestik, dapat dilihat dari isu regional dsa ekonomi global dimana negara sibuk memperbaiki kondisi yang terdapat di dalam negerinya dan kurang peduli terhdap kondisi di luar dengan tujuan meningkatkan pertumbuhan ekonomi (Petith, 1977). Setelah kekalahan China di perang opium, masyarakat China sadar dengan keterbelakangannya sehingga seluruh masyarakat China ragu dan ada rasa takut terhadap teknologi, gagasan dan institusi yang dibuat oleh orang barat (Yu, 2007:21). Dari rasa takut terhadap orang asing dan barang asing ini, China melakukan percepatan modernisasi dengan kebiasaan norma kofusius yang dimana pemalsuan merupakan bentuk sanjungan dari proses kreatif mereka (Boyle, 1996:54) dan sebagai sentimen nasionalis orang-orang China yang melepaskan frustrasi mereka pada orang asing dan perusahaan asing (Yu, 2007: 21). -

RELEASE NOTES UFED INFIELD, UFED PHYSICAL ANALYZER, Version 6.1 | March 2017 UFED LOGICAL ANALYZER, UFED READER
NOW SUPPORTING 21,773 DEVICE PROFILES 3,544 APP VERSIONS UFED TOUCH2, UFED TOUCH, UFED 4PC, RELEASE NOTES UFED INFIELD, UFED PHYSICAL ANALYZER, Version 6.1 | March 2017 UFED LOGICAL ANALYZER, UFED READER WATCH ADVANCED ADB IN ACTION! HIGHLIGHTS DEVICE SUPPORT ◼ The fastest physical extraction (Advanced ADB) method in the industry for thousands of Android devices. ━ You can now perform physical extractions directly from the mobile device to any USB storage device (USB 3.0 recommended) or to an SD Card for any device with an SD card slot. ━ Generally, this capability works on devices with a security patch level up to November 2016. Due to the widely fragmented variety of Android devices, Watch video now! https://player.vimeo.com/video/207027555 exceptions may apply. ━ Unmatched data extraction speed and simplicity. ━ To perform this extraction using an external USB storage device, you will need cables OTG 501 and 508. To register for the new extraction cables, as well as future ones, please click here. Device with Device without SD Card SD Card Device with Can be extracted NEW PHYSICAL EXTRACTION METHOD FOR Can be extracted Micro-USB using SD Card or using cable 501 THOUSANDS OF ANDROID DEVICES! Connector using cable 501 Dramatically reduce your time to evidence with Device with Can be extracted Can be extracted next generation physical extraction technology, Type-C using SD Card or using cable 508 Advanced ADB, for selected and the newest, Connector using cable 508 Android devices. ◼ Physical decoding support is now available for the This ground-breaking capability allows Cellebrite 4 Alcatel devices running Spreadtrum chipset (SC6531) customers to perform decrypted physical extraction, that was introduced in UFED 6.0 – Alcatel 1016G One via a unique temporary rooting method, which in Touch, 1016D One Touch, 3022G One Touch and 2040D many cases was not possible, until today! One Touch. -
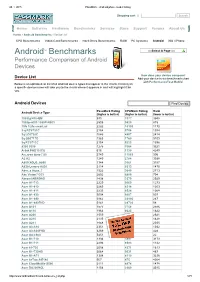
Androidtm Benchmarks
28. 1. 2015 PassMark Android phone model listing Shopping cart | Search Home Software Hardware Benchmarks Services Store Support Forums About Us Home » Android Benchmarks » Device List CPU Benchmarks Video Card Benchmarks Hard Drive Benchmarks RAM PC Systems Android iOS / iPhone TM Select A Page Android Benchmarks Performance Comparison of Android Devices How does your device compare? Device List Add your device to our benchmark chart with PerformanceTest Mobile! Below is an alphabetical list of all Android device types that appear in the charts. Clicking on a specific device name will take you to the charts where it appears in and will highlight it for you. Android Devices Find Device PassMark Rating CPUMark Rating Rank Android Device Type (higher is better) (higher is better) (lower is better) 1005tg N10QM 935 3377 3948 1080pn003 1080PN003 2505 9820 815 1life 1Life.smart.air 2282 10103 1170 3q RC9731C 2154 5756 1394 3q LC0720C 1646 4897 2414 3q QS0717D 1363 1760 3109 3q RC9712C 2154 5223 1396 9300 9300 1275 3364 3321 Alink PAD10 ICS 616 1130 4249 A.c.ryan dyno 7.85 2749 11065 596 A2 A2 1240 2784 3388 A800 XOLO_A800 1344 3661 3157 A830 Lenovo A830 2114 8313 1470 Abs_a Aqua_7 1522 3640 2713 Abc Vision7DCI 2602 6880 704 Abroad ABROAD 1438 3379 2929 Acer A1713 2229 9069 1273 Acer A1810 2265 8314 1203 Acer A1811 2233 8524 1268 Acer A1830 3004 9207 507 Acer A1840 3962 23996 267 Acer A1840FHD 5141 28720 58 Acer A101 1577 3758 2586 Acer A110 1964 8623 1822 Acer A200 1559 3822 2621 Acer A210 2135 8315 1428 Acer A211 1848 8130 2035 Acer A3A10 2351 8128 1032 Acer A3A20FHD 3269 11265 428 Acer AA3600 5451 22392 22 Acer B1710 1336 3897 3173 Acer B1711 2293 8583 1142 Acer b1720 2058 4371 1613 Acer B1730HD 3064 9031 487 Acer B1A71 1308 4119 3236 Acer beTouch E140 567 475 4264 Acer CloudMobile S500 2111 4874 1478 Acer DA220HQL 1156 2960 3545 http://www.androidbenchmark.net/device_list.php 1/71 28. -

Chinese Mobile Phone Industry: Supply Chain and Product Strategies of Major IC Solution Providers ______I
Industry Intelligence Program Communications Chinese Mobile Phone Industry: Supply Chain and Product Strategies of Major IC Solution Providers Abstract The Chinese mobile phone industry has been flourishing and evidenced by an increasingly mature supply chain, concentrated 3G mobile phone market and the rise of low-priced smartphones. In addition, the issue of China's homegrown 4G licenses is anticipated to trigger new cycles of growth in smartphones. And all players in the industry supply chain have vied with each other to gain traction. Chinese TD-SCDMA smartphones, in particular, recorded a shipment volume of nearly 100 million units in the first half of 2013 alone. This report touches on the development of Chinese homegrown mobile phone industry and its supply chain, further examining the product strategies of major IC solution providers, MediaTek and Spreadtrum. by MIC International Research Team Document Code: MCRPT13123001 Publication Date: December 2013 Check out MIC on the Internet! http://mic.iii.org.tw/english MCRPT13123001 Chinese Mobile Phone Industry: Supply Chain and Product Strategies of Major IC Solution Providers _________ i Table of Contents Page 1. Development of the Chinese Homegrown Mobile Phone Industry ............................................................................................................ 1 1.1 Shipment Analysis for the First Half of 2013 .................................... 1 1.2 Development of Chinese Homegrown Mobile Phone Industry's Supply Chain ........................................................................... -
Theft Nation: How Ip Theft Drives the Chinese National Business Model, and Its Effect Upon the Global Economy
WHITE PAPER THEFT NATION: HOW IP THEFT DRIVES THE CHINESE NATIONAL BUSINESS MODEL, AND ITS EFFECT UPON THE GLOBAL ECONOMY by Evan R. Anderson Foreward by Mark R. Anderson INVNT/IP NOFORN/PROPRIETARY 07/05/15 A Publication of the INVNT/IP Consortium, A Global Initiative Sponsored by the Strategic News Service 1 On Intellectual Property Theft “There are two kinds of big companies in the United States. There are those who’ve been hacked by the Chinese and there are those who don’t know they’ve been hacked by the Chinese.”1—James Comey, Director, FBI “The ongoing cyber-thefts from the networks of public and private organizations, including Fortune 500 companies, represent the greatest transfer of wealth in human history.”2 —Gen. Keith Alexander, Former Director, US Cyber Command and the National Security Agency “Nation-states like China are stealing intellectual property at a breathtaking pace, taking it back, repurposing and then using it to compete against those very same companies around the world, at a huge disadvantage to the company they just stole it from.” —Mike Rogers, Former House Intelligence Committee Chairman “From the US Congress, to the Department of Defense, to the private sector, we have never, ever not found Chinese malware embedded in a system so that they can extract it.”3—Vice Admiral Mike McConnell, Senior Executive Advisor, Booz Allen Hamilton; Former Director, National Security Agency “Cyber threats pose one of the most serious economic and national security challenges to the United States, and my Administration is pursuing a comprehensive strategy to confront them.”—President Barack Obama, in his April 1, 2015, press conference announcing a new sanctions regime via presidential directive “[China is] trying to hack into everything that doesn’t move in America. -

A SYSTEMIC ABDICATION’ STATE Title IX Complaint Filed by Tennis Player DAILY 21 MAY SARAH HENRY/ ISD MONDAY 2018 Vol 129 No
Iowa State Daily, May 2018 Iowa State Daily, 2018 5-21-2018 Iowa State Daily (May 21, 2018) Iowa State Daily Follow this and additional works at: https://lib.dr.iastate.edu/iowastatedaily_2018-05 Recommended Citation Iowa State Daily, "Iowa State Daily (May 21, 2018)" (2018). Iowa State Daily, May 2018. 2. https://lib.dr.iastate.edu/iowastatedaily_2018-05/2 This Book is brought to you for free and open access by the Iowa State Daily, 2018 at Iowa State University Digital Repository. It has been accepted for inclusion in Iowa State Daily, May 2018 by an authorized administrator of Iowa State University Digital Repository. For more information, please contact [email protected]. IOWA ‘A SYSTEMIC ABDICATION’ STATE Title IX complaint filed by tennis player DAILY 21 MAY SARAH HENRY/ ISD MONDAY 2018 Vol 129 No. 163 New Sloss HIKING HIGHLIGHT director chosen BY K.RAMBO @iowastatedaily.com Ruxandra Looft was announced as the new director of the Mar- garet Sloss Women’s Center on Wednesday afternoon, after a se- ries of forums and interviews. Looft, known to students, fac- ulty and staff as Sandra, was born in Romania and holds a doctorate in German and comparative lit- JILL O’BRIEN/ ISD erature. If you need a break from Ames Looft has been with Iowa State but don’t want to drive far, Don since 2010, as a lecturer of German Williams Park offers recreational and international studies and an activities such as hiking, swim- Academic Advising Coordina- ming and fishing. PG7 KENNEDY DERAEDT/ IOWA STATE DAILY tor in the world languages and Sophomore Erin Freeman played for Iowa State Tennis on April 23. -

Silicon IP for Low Cost Smartphones
Silicon IP for Low Cost Smartphones Executive Summary Smartphones are the personal computers of the 21st century. The performance and functionality of the device, the performance and capacity of cloud-based servers, and the bandwidth of 4G cellular networks have created a $100B market in the developed world. Smartphone shipments are expected to grow 32.7% year over year in 2013 reaching 958.8 million units. The market for high-end phones, dominated by Apple and Samsung, will continue to grow at ~8% CAGR, but the next surge in growth will come from mid-range phones ($200 to $400), and low-end phones priced below $200. These segments are expected to experience ~15% CAGR according to analysts. Smartphones enabled a completely new computing experience supported by millions of apps conveying personal, commercial, educational, and social benefits. And you can still talk to a person or your personal assistant, e.g. Siri. The benefits are universally compelling but the >$500 price (unsubsidized) of a high-end smartphone restricts wide- spread adoption in low income segments and emerging markets. Feature phones in developing countries play a vital role in communication. Smartphones will enable access to new resources (market prices, weather, services), education, and rich media social features. Photosharing is rapidly becoming the lingua franca of the planet. A large number of sub $100 smartphones are launching this year in China, India, Southeast Asia, the Middle East, South America and Africa. China is aggressively pursuing this market in design, development and consumption. The leading Silicon suppliers are Qualcomm, Samsung, MediaTek, with many established and new entrants taping out application processors on low cost process nodes (e.g. -
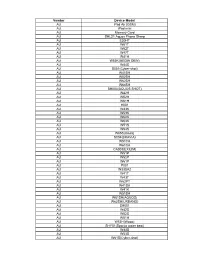
List of Supported Devices
Vendor Device Model AU iPad Air (GSM) AU iPad mini AU Memory Card AU SHL21 Aquos Phone Sharp AU E30HT AU W61T AU W62T AU W47T AU W41H AU W52K(MEDIA SKIN) AU W44S AU S001(Cyber-shot) AU W41SH AU W52SH AU W62SH AU W64SH AU SH003(AQUOS SHOT) AU W42H AU W52H AU W61H AU H001 AU W43K AU W53K AU W62K AU W63K AU W51S AU W54S AU W65S(Xmini) AU S004(BRAVIA) AU W51CA AU W61CA AU CA003(EXILIM) AU W51P AU W52P AU W61P AU P001 AU W33SA2 AU W41T AU W43T AU W62PT AU W41SA AU W41K AU W51SH AU W61SH(AQUOS) AU W63SH(URBANO) AU SH001 AU W42S AU W52S AU W51H AU W53H(Wooo) AU SHY01(Sportio water beat) AU W43S AU W53S AU W61S(Cyber-shot) AU W43SA AU W53SA AU W62SA AU W52T AU W56T AU W64T AU W42CA(G'zOne) AU W52CA AU W62CA(G'zOne) AU W45T AU W51T AU W54T AU W55T AU W63T(Sportio) AU T002 AU TSY01(biblio) AU W61SA AU W44T AU W53T AU W65T AU W42SA AU W54SA AU W63SA AU SA001 AU W43CA AU W53CA AU W63CA(EXILIM) AU W63S(re) AU W44K AU W51K AU W61K AU W51SA AU W55SA(INFOBAR2) AU W64SA AU K003 AU W64K AU W44K2 AU TSX04(PLY) AU HIY02(beskey) AU W52SA AU SOY01(Premier3) AU E08T AU W46T(DRAPE) AU T003 AU K001 AU K002 AU E07K AU KYX03(PRISMOID) AU T004 AU W33SA AU W63H AU HIY01(Mobile Hi-Vision CAM Wooo) AU SH002(AQUOS SHOT) AU SH004 AU SH005 AU SH007(AQUOS SHOT) AU CA001 AU CA002(G'zOne) AU CA004(EXILIM) AU W41CA AU W65K AU K004 AU NS01 AU KYX02(misora) AU W41S AU W62S AU W64S AU SOX01(G9) AU TSX05(LIGHT POOL) AU SOY02(BRAVIA U1) AU SOY03(URBANO BARONE) AU K005 AU W62P AU CA005(EXILIM) AU SH006(AQUOS SHOT) AU S003(Cyber-shot) AU S002 AU E05SH AU E06SH AU KYX04(lotta) AU -

Crucialtec (114120 KS) Crucialt Ec
Korea Information Technology 15 February 2016 CrucialTec (114120 KS) CrucialT ec Target price: KRW24,000 Share price (15 Feb): KRW12,250 | Up/downside: +95.9% Initiation: a turnaround at its fingertips Benefiting from strong demand/tight supply for fingerprint sensors Kevin Jin (82) 2 787 9168 Entry of new competitors should be limited, at least in 2016 [email protected] Initiating with a Buy (1) rating and TP of KRW24,000; rerating likely Investment case: We see CrucialTec as an earnings recovery play for Share price performance 2016, following a switch in its business model at end-2013 which saw it (KRW) (%) move from being solely an optical trackpad (OTP) supplier for Blackberry to 17,000 190 becoming a fingerprint sensor (FPS) module supplier for some of China’s 15,000 165 leading smartphone makers (eg, Huawei, Meizu and OPPO Electronics). 13,000 140 11,000 115 Given the rising demand for FPS modules globally, we forecast the FPS 9,000 90 penetration rate among the top-10 China smartphone brands to rise from Feb-15 May-15 Aug-15 Nov-15 14-15% for 2015 to 30-35% for 2016, which would lead to tight supply and CrucialTec (LHS) Relative to KOSPI (RHS) strong demand for FPS modules in 2H16, pushing CrucialTec’s utilisation rate to close to 100% by the end of 2016, on our estimates. It should also 12-month range 9,190-17,000 result in a 4,591% rise in CrucialTec’s net profit, as the company is one of 2 Market cap (USDbn) 0.28 global leaders in this hard-to-enter segment of the smartphone value chain. -

Hersteller Modell Boonflip 100+ V6 XS2 Acer Liquid E3 XS Acer Liquid
Kompatibilitätsliste reboon boonflip Stand: August 2016 Hersteller Modell boonflip 100+ V6 XS2 Acer Liquid E3 XS Acer Liquid E3 Duo Plus XS Acer Liquid Jade XS Acer Liquid Jade S XS Acer Liquid Jade Z XS Acer Liquid M320 XS Acer Liquid M330 XS Acer Liquid Z320 XS Acer Liquid Z330 XS Acer Liquid Z410 XS Acer Liquid Z530 XS Acer Liquid Z530S XS Acer Liquid Jade Primo XS2 Acer Liquid X1 XS2 Acer Liquid Z630 XS2 Acer Liquid Z630S XS2 Acer Liquid M220 XS3 Acer Liquid Z200 XS3 Acer Liquid Z220 XS3 Acer Liquid Z4 XS3 Acer Liquid E600 XS4 Acer Liquid E700 XS4 Acer Liquid Z5 XS4 Acer Liquid Z500 XS4 Alcatel OneTouch Fierce 2 XS Alcatel OneTouch Idol 2 XS Alcatel OneTouch Idol 2 S XS Alcatel OneTouch Idol Alpha XS Alcatel OneTouch Idol X XS Alcatel OneTouch Idol X+ XS Alcatel OneTouch Pop 2 (5) XS Alcatel OneTouch Pop 2 (5) Premium XS Alcatel OneTouch Pop 3 (5) 3G XS Alcatel OneTouch Pop 3 (5) 4G XS Alcatel OneTouch Pop C7 XS Alcatel OneTouch Pop S7 XS Alcatel OneTouch Pop Star 3G XS Alcatel OneTouch Pop Star 4G XS Alcatel OneTouch Pop Up XS Alcatel Pixi 3 (5) 4G XS Alcatel Pixi 3 (5) 4G XS Alcatel OneTouch Fierce XL XS2 Alcatel OneTouch Fierce XL XS2 Alcatel OneTouch Idol 3 (5.5) XS2 Alcatel OneTouch Idol 3C XS2 Alcatel OneTouch Pop 3 (5.5) 3G XS2 Alcatel OneTouch Pop 3 (5.5) 4G XS2 Alcatel OneTouch Pop C9 XS2 Alcatel OneTouch Idol Mini XS3 Alcatel OneTouch Idol Mini Dual XS3 Alcatel OneTouch Pixi First XS3 Alcatel OneTouch Pop S3 XS3 Alcatel OneTouch Star XS3 Alcatel Pixi 4 (4) XS3 Alcatel Flash Plus 2 XS4 Alcatel OneTouch Flash XS4 1 Kompatibilitätsliste